What Is Information Assurance?
Information assurance (IA) is the practice of managing IT risks related to the storage, transportation, creation, and handling of information. The concept of IA originated in the U.S. government, specifically the military and intelligence infrastructure. Information assurance and information security share the common goals of confidentiality, integrity, and availability. Unlike information security, information assurance is also concerned with some bigger-picture items, including privacy, compliance, governance, and strategic risk management.
 NOTE
NOTE
Every IA plan must consider three factors: the protection of information, the detection of breaches, and the reaction to a breach.
Information assurance is all about risk assessment and mitigation. You can never make something 100% secure. The goal of IA is to make information as secure as reasonably possible using efficient methods. Risk assessment and information classification play a large role in IA. Understanding what information needs to be secured, and how much time, energy, and money to spend securing a given piece of information, is at the heart of IA.
There are three main models of information assurance. These models help an organization define risk and assist in all aspects of IA for the organization:
- The confidentiality, integrity, and availability (C-I-A) triad
- The five pillars of IA
- The Parkerian hexad
 NOTE
NOTE
The C-I-A triad is also known as the A-I-C triad, which stands for availability, integrity, and confidentiality.
The following sections examine each of these models in detail.
C-I-A Triad
The C-I-A triad is one of the oldest and most widely known IA models. Most people in the IT security field are familiar with it, and it is still utilized heavily in teaching information assurance concepts. The C-I-A triad comprises three criteria for maintaining secure information: confidentiality, integrity, and availability. The C-I-A triad is shown in FIGURE 13-1.
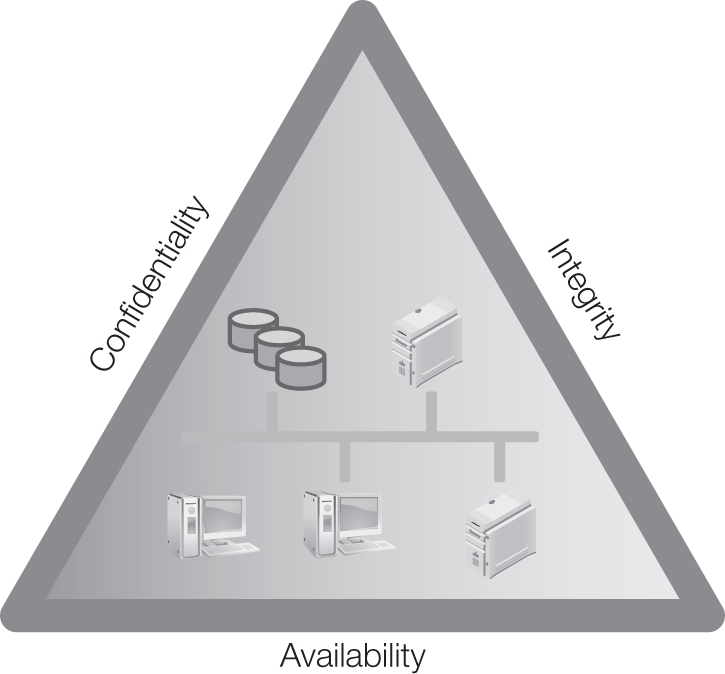
FIGURE 13-1 The C-I-A triad represents three criteria for maintaining secure information.
The model was created to help organizations think about the important aspects of information assurance, develop security policies, and identify problem areas. The next sections cover each aspect.
Confidentiality
According to the Committee on National Security Systems Instruction No. 4009 (CNSSI-4009), confidentiality is “The property that information is not disclosed to system entities (users, processes, devices) unless they have been authorized to access the information.” In other words, information must be viewed, used, or copied only by individuals who have the proper level of access as well as a legitimate need to access the information. A confidentiality breach occurs when an unauthorized individual gains access to sensitive information.
If someone watched over your shoulder while you were entering your automated teller machine (ATM) PIN, a confidentiality breach occurred. Confidentiality breaches can also happen when hardware containing sensitive information is lost or stolen. Any time an unauthorized user can access confidential information, a breach has occurred.
Confidentiality is maintained through proper use of access controls such as limiting access to information to a need-to-know basis and properly assigning security levels to information.
Integrity
CNSSI-4009 defines integrity as “The property whereby an entity has not been modified in an unauthorized manner.” Data integrity refers to the principle that information cannot be changed, created, or deleted without proper authorization; however, integrity in the C-I-A triad goes beyond that. It is also the requirement that the path on which the information travels and the location where it rests are also secure.
Information integrity refers to the ability to trust that the information received is the same as the information originally created. It is also the ability to trust that a document stored in multiple locations contains the exact same information.
Data integrity isn’t just concerned with information security. Accidental data loss and data corruption through transmission are also major causes of integrity failure. Coping with accidental loss and corruption is one of the areas where IA moves beyond information security into information verification.
Availability
CNSSI-4009 defines availability as “The property of being accessible and useable upon demand by an authorized entity.” In other words, information is accessible when it is needed. This requires that the network and systems used to store the information are working correctly. Availability can be compromised by accidents and system failure as well as malicious attacks. A hard drive or network card failure can cause a breach of availability, as can denial of service (DoS) attacks.
The Five Pillars
The five pillars of IA were developed by the National Security Telecommunications and Information Systems Security Committee (NSTISSC). Detailed in CNSSI-4009, it is an expansion of the C-I-A model.
The three tenets of the C-I-A model make up the foundation of the five pillars of IA. Two further tenets were added to better model the situation that complex organizations face when dealing with IA. CNSSI-4009 defines IA as “Measures that protect and defend information and information systems by ensuring their availability, integrity, authentication, confidentiality, and nonrepudiation. These measures include providing for restoration of information systems by incorporating protection, detection, and reaction capabilities.” Authentication and nonrepudiation are the two factors added to the traditional C-I-A framework.
The McCumber Cube
In the early 1990s, the C-I-A triad model was expanded by John McCumber into a cube to look deeper at IA. McCumber took the C-I-A framework and added two more triads to it, forming a multidimensional cube as shown in FIGURE 13-2. The concept behind the cube was to allow an organization to look at all aspects of IA fully, without overemphasizing any one aspect. McCumber proposed three dimensions of IA:
- Goals—These are represented by the C-I-A triad.
- Information states—These describe where data are located at any given moment.
- Safeguards—These refer to what is being done to secure data.
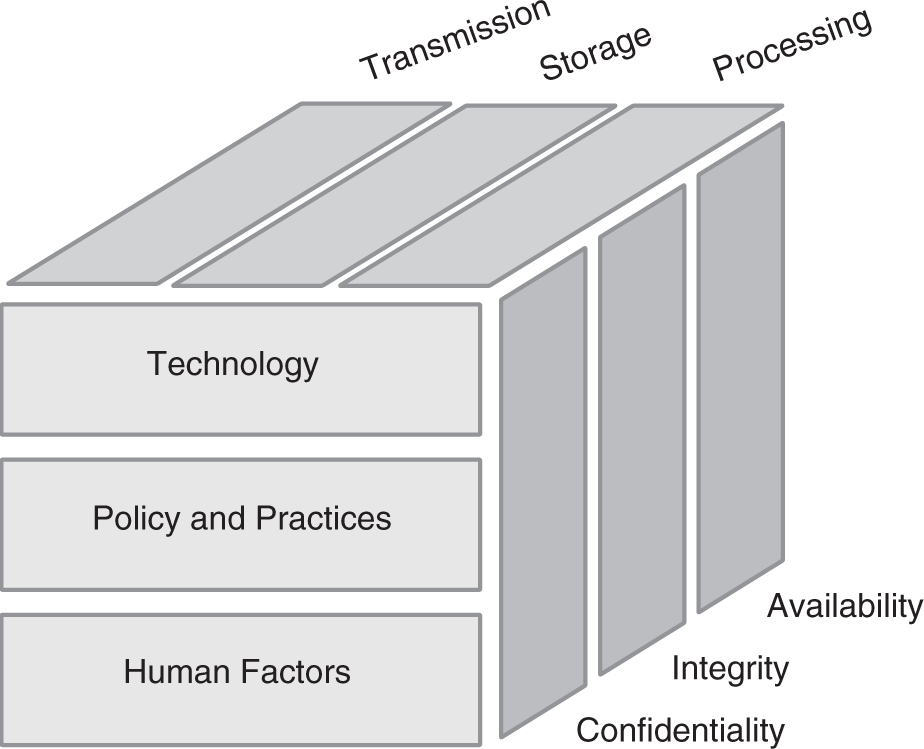
FIGURE 13-2 The McCumber cube, by Munawar Hafiz, illustrates a deeper understanding of information assurance.
There are three information states in the cube: transmission, storage, and processing. Storage and transmission are just other terms for data at rest and data in motion. The processing state refers to the time when data are being acted upon by a system. This is a data state that is often overlooked.
Another dimension of the cube includes safeguards. These include the policies and practices in place to secure information. Human factors such as information security training, and technological safeguards like antivirus software, intrusion detection systems, and firewall systems are included in the concept of safeguards.
In addition to the three triads, there is a fourth dimension: time. According to the cube framework, all three triads must be addressed in connection with each other over time. Understanding the interdependencies of these factors over time is essential to IA.
Some organizations use an expanded McCumber cube model that replaces the C-I-A triad with the five pillars of IA on the goals dimension of the cube.
Authentication
CNSSI-4009 defines authentication as “The process of verifying the identity or other attributes claimed by or assumed of an entity (user, process, or device), or to verify the source and integrity of data.” This entails knowing that those who access the information are who they say they are. Authentication can be achieved through the three tests of what you know, what you have, and what you are. An example of an authentication breach is if an unauthorized user accesses a system using an authorized username and password obtained through illegitimate means.
Nonrepudiation
Nonrepudiation is defined in CNSSI-4009 as “Assurance that the sender of information is provided with proof of delivery and the recipient is provided with proof of the sender’s identity, so neither can later deny having processed the information.” With this concept, both the sender and the receiver are accountable for the information. To implement nonrepudiation, there must be a way for the sender to verify that the receiver got the information and for the receiver to verify the sender’s identity. With nonrepudiation in place, neither side can deny actions they took on the data.
A good example of nonrepudiation can be seen in a banking wire transfer. When a wire transfer is sent, the sender verifies its credentials with the Federal Reserve Bank. The Federal Reserve then moves the wire transfer to the receiver. The recipient of the wire verifies receipt of the transfer, and the amount received, back to the sender. This way, the banking system can mitigate the risk of fraud.
Since their creation in 2001, the five pillars of IA have become the standard IA framework for U.S. governmental organizations. Inside the government, these pillars are utilized based on sensitivity, threat, and other risk management decisions. They form the core of any governmental IA operation.
The Parkerian Hexad
The Parkerian hexad, shown in FIGURE 13-3, is an IA framework developed by Donn B. Parker in 2002. It was developed to expand the C-I-A model and uses the C-I-A triad as a base. This was developed in response to the limitations of the C-I-A framework. Parker described these elements as fundamental and nonoverlapping. Most security breaches compromise more than one element at a time.
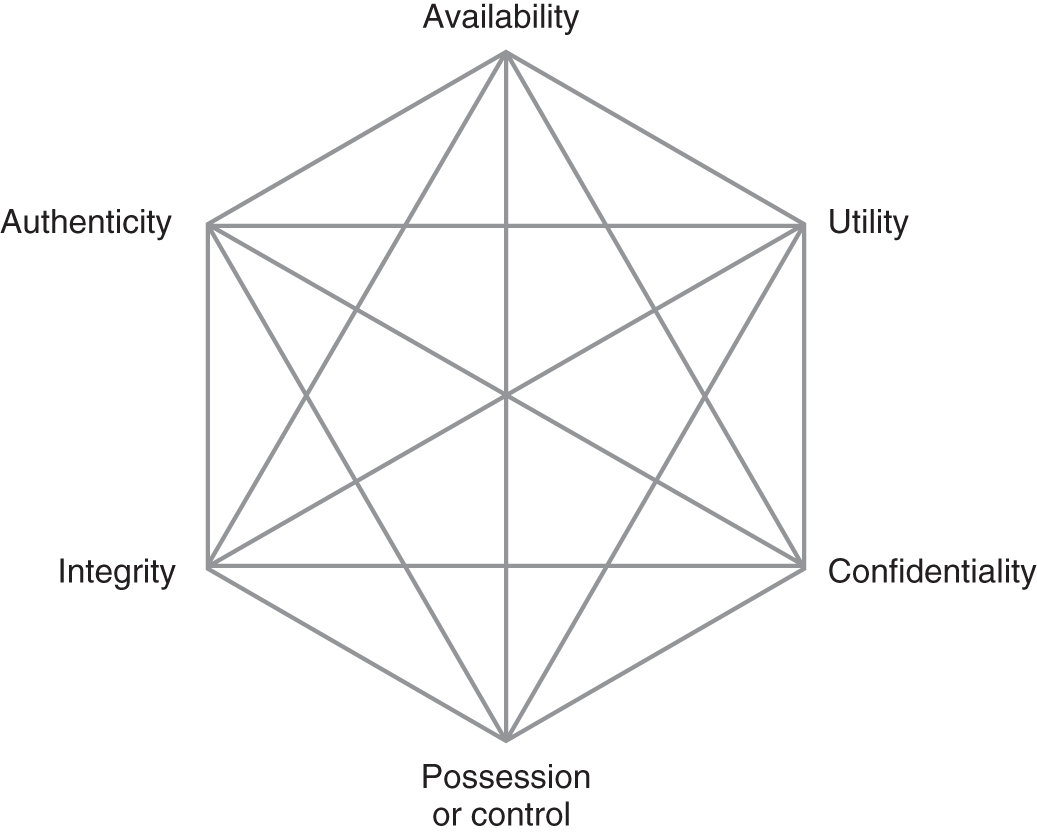
FIGURE 13-3 The Parkerian hexad.
The three additional elements of the hexad are possession or control, authenticity, and utility. Next, you will look at each of these aspects.
Possession or Control
Possession or control is related to confidentiality. It is the concept that control of the information can be breached without a confidentiality breach. For example, suppose a flash drive containing the master copy of sensitive data is lost. The possession of those data is now breached, but until they are accessed, they are still confidential. The basis of control is preventing contact with confidential information by unauthorized users. This idea also covers unauthorized copying of or use of intellectual property. An example of a breach of possession is the piracy of copyrighted music files.
Authenticity
Authenticity is the appropriateness of the labeling of information. Does the information correspond correctly to its intended meaning? The idea behind this element is to avoid garbled data and fraud. A breach may be caused by an incorrect address in an email database.
Utility
Utility describes the usefulness of data. Information that is stored in an obsolete format that can no longer be read would be a breach of utility. Encrypted information with a lost encryption key is also an example of a utility breach.
The hexad and the five pillars of IA both expand upon the C-I-A model. It is important to remember that these are just frameworks or guidelines. Even the C-I-A model, which is the simplest of the three, is a useful guideline for IA. These frameworks give an organization a starting point for developing a robust IA infrastructure. These models are not to be taken literally but used as a tool to craft your own organization’s IA policies and procedures.
