Network Authentication Protocols
Modern networks typically require that users authenticate before gaining access via both wired and wireless connections. The 802.1x protocol provides a framework for implementing authentication on a network. In 802.1x networks, there are three different roles held by components:
- The supplicant is the software running on the client that wishes to connect to the network.
- The authenticator is the network device that the client wishes to connect to, typically an Ethernet switch or a wireless access point.
- The authentication server is the server that validates requests for network access, using the RADIUS or EAP protocols.
We’ve already discussed RADIUS in this chapter, so let’s move on and discuss EAP.
Extensible Authentication Protocol (EAP) is a framework that enables multiple authentication mechanisms over a wireless network or PPP connection. Standardization of EAP occurred in 1998 and is defined in RFC 2284. EAP sits inside a PPP authentication protocol such as RADIUS and provides the framework for the authentication method. Unlike PAP and CHAP, EAP specifies the authentication mechanism at the authentication phase. The authenticator can specify the use of additional authentication methods such as Kerberos, one-time passwords, biometrics, and other authentication tools.
In an EAP over the RADIUS environment, the RADIUS client communicates with the system requesting authentication using EAP and with the RADIUS server using RADIUS. This communication is shown in FIGURE 10-2 and works as follows:
- The client computer initiates a connection to the RADIUS client, and the two systems agree on the use of EAP.
- The RADIUS client asks the client computer to identify itself by sending an EAP-Request/Identity message, and the client computer responds with an EAP-Response/Identity message.
- The RADIUS client creates an Access-Request message containing the client computer’s identity and sends it to the RADIUS server.
- The RADIUS server responds with an Access-Challenge message that contains an EAP-Message requesting the client computer to authenticate.
- The RADIUS client removes the RADIUS details from the Access-Challenge message and passes the EAP-Message to the client computer.
- The client computer responds to the authentication request by passing an EAP-Message through the RADIUS client to the RADIUS server in a similar fashion.
- The RADIUS server replies with either an Access-Accept or an Access-Reject message, allowing or denying the connection.

FIGURE 10-2 EAP over RADIUS.
EAP over LAN (EAPOL) is the encapsulation of EAP over wired and wireless LANs and is defined in IEEE 802.1X. EAPOL as a delivery mechanism for authentication types. Therefore, when used for authentication, EAP works in conjunction with a specific authentication technology. There are many EAP types, including:
- EAP with Message Digest 5 (EAP-MD5) uses the outdated MD5 hash protocol and is no longer recommended for use. EAP-MD5 uses one-way authentication, meaning that the client authenticates to the network but the network does not authenticate to the client.
- EAP with Transport Layer Security (EAP-TLS) uses certificate-based authentication in conjunction with the standard TLS protocol and is a strong, secure authentication choice. EAP-TLS provides mutual authentication, meaning that the client authenticates to the server and the server also authenticates to the client. In EAP-TLS, both the client and the server require certificates.
- EAP with Tunneled Transport Layer Security (EAP-TTLS) also uses TLS to provide network authentication. EAP-TTLS also provides mutual authentication but only requires that the server have a certificate.
- Protected EAP (PEAP) is quite similar to EAP-TTLS, differing only in technical implementation details.
- EAP with Flexible Authentication via Secure Tunneling (EAP-FAST) is a proprietary Cisco implementation of EAP authentication that provides mutual authentication but does not use certificates.
- Lightweight EAP (LEAP) is a Cisco proprietary protocol used primarily on wireless networks. It does not require the use of certificates.
TABLE 10-3 compares the EAP authentication types.

The encapsulation of EAP messages is often used in a wireless LAN. The following are the steps used during this process and shown in FIGURE 10-3:
- A new wireless client attempts to associate with a wireless access point (AP). Another option is when a wireless client associates with a new wireless AP and an EAP-Start message is transmitted.
- If the wireless AP detects a new client associating with it, the wireless AP transmits an EAP-Request/Identity message to the wireless client.
- The client replies to this identity request with an EAP-Response/Identity message containing the wireless client’s username.
- The wireless AP sends the authentication request to the RADIUS server in the form of a RADIUS Access-Request message.
- The RADIUS server sends the AP a RADIUS Access-Challenge message containing a request that the user authenticate.
- The wireless AP then sends the client an EAP-Challenge Request requesting authentication.
- The wireless client replies to the challenge with an EAP-Challenge Response containing the requested authentication details.
- The wireless AP sends a RADIUS Access-Request message to the RADIUS server containing the user’s authentication information.
- The RADIUS server verifies the user’s identity and sends a RADIUS Access-Accept message if the user is authenticated or an Access-Reject message otherwise.
- The AP passes an EAP-Success message to the user and the connection is authorized.
- The AP and client may then agree to a set of encryption tools to use to protect the remainder of the session.
- Communication continues until the client or AP chooses to close the session.
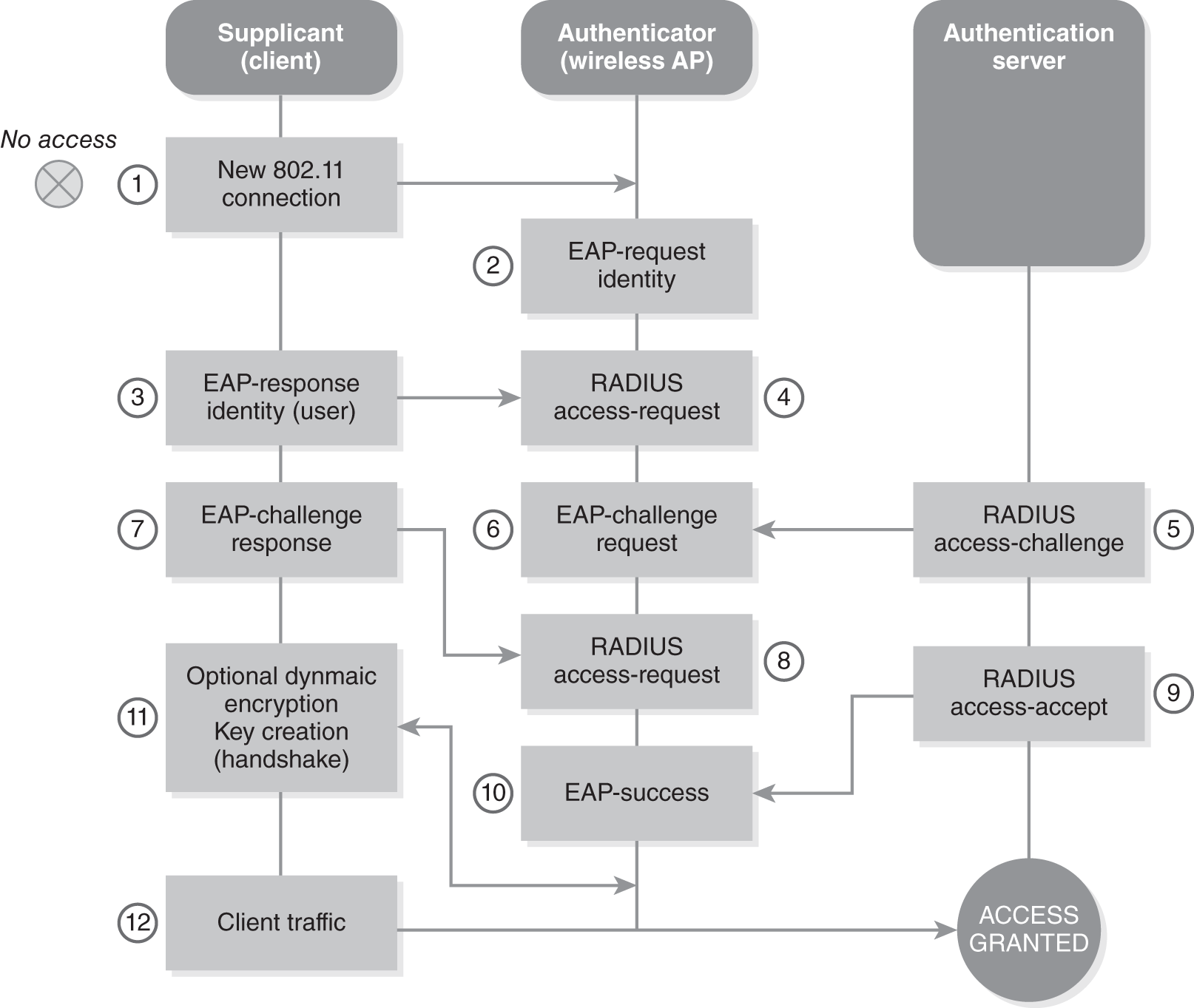
FIGURE 10-3 Process of EAP message encapsulation in a wireless LAN.
Courtesy of Ubiquiti Inc.
During the handshake process over PPP, both systems determine the authentication protocol to use. Other factors are also determined, such as connection parameters and the speed of data. Authentication occurs using the most secure protocol. If one of the systems does not have EAP capabilities, CHAP is attempted. If one of the systems does not have CHAP capabilities, PAP is used unless otherwise specified by the administrator. The administrator may choose to use PAP but because of the security risk, it is not advisable to use PAP.
