Access Controls for Employees, Remote Employees, Customers, and Business Partners
Companies have many types of identity groups that need access to the network. The identity groups include employees, remote employees, customers, and business partners. Managing the access controls of various identity groups can be cumbersome. An administrator must understand how they will access the network, when they will access the network, and the amount of access that is required by role.
For example, a business partner of a software development company may need full access to documentation and software but not to the source code. The business partner may be treated like an employee, but the partner cannot receive access to everything an employee in a similar role would have. For example, a business partner should not have access to internal distribution lists, the HR site, or IT sites that are provided specifically for employees. Business partners are important to an organization, but they still work for another company, and data need to remain separate. Careful consideration must be given to every role as well as every group they are a part of. Customers may have access to product A documentation, but this does not mean that the customer should have access to documentation for products B and C as well. There are multiple tools available for providing access to employees, remote employees, customers, and business partners, which are discussed in the following sections.
Remote Virtual Private Network (VPN) Access—Remote Employees and Workers
Remote access virtual private networks (VPNs) are established to allow remote employees access to an organization’s internal network. The idea is to provide the same capabilities off site that you have on site. A remote VPN provides a secure connection by creating an encrypted tunnel from point A to point B, usually across the Internet. If point B is an organization’s internal network, point A is a computer system or mobile device that can be located anywhere, such as a coffee shop, a house, an airport, or any place that provides Internet access. FIGURE 7-6 provides an overview of VPN communications.
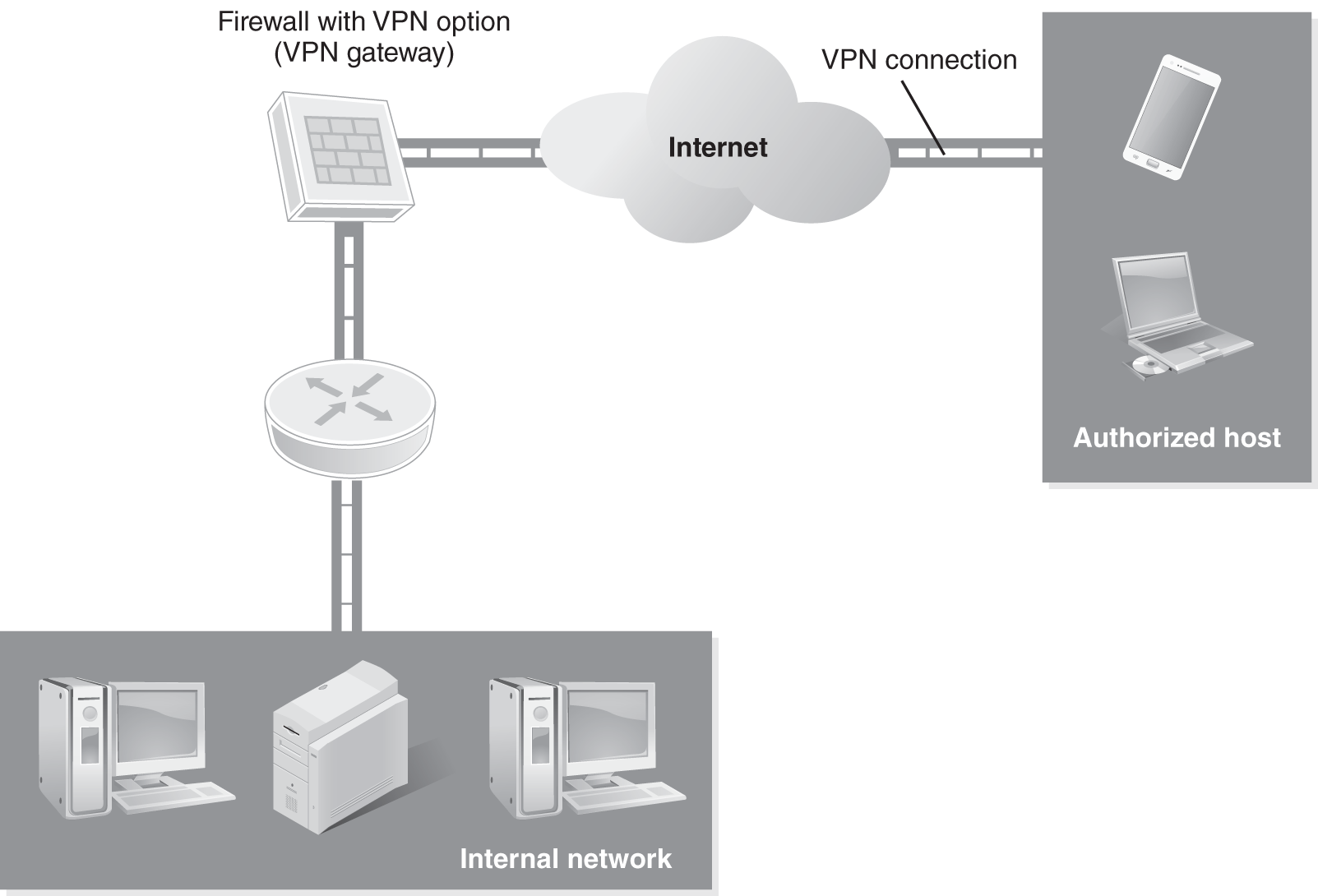
FIGURE 7-6 VPN communications.
The benefits associated with remote access VPNs are:
- It reduces costs by allowing the user to work at locations other than an employer site. This may reduce facility costs for electricity and floor space.
- It improves flexibility by giving users the ability to work whenever and wherever. For example, an employee may be given access to employer resources after hours. The employee may also work at a coffee shop before a customer meeting.
- It provides secure communications through encryption and access rights based on the user.
Before remote access VPNs were available, many organizations used expensive leased lines. This technology was not considered a secure option because these lines can easily be tapped and the communications monitored. With the advent of VPNs with encryption and access controls, security was enabled by protecting the data and controlling who has access to which resources within an organization’s domain. Remote access VPNs provide secure communications for laptops, mobile devices such as smartphones and tablets, and even external servers.
Remote access VPN access controls are managed through authentication of the user, VPN firewalls, VPN routers, and applications. Access controls can be based on user IDs or mandatory access control limitations. The ability for remote access VPNs to provide security and access controls establishes an optimal solution for remote employees as well as customers and business partners. This solution gives the administrator a more granulated access control by limiting or allowing access based on:
- Authentication methods—Incorporating a multifactor authentication method adds the extra level of security for gaining access to the corporate network. For example, when Scott goes into the office, he may use a user ID and password. If Scott is at home and accessing the corporate network remotely, he will still use his user ID and password, but another layer of authentication will be required with the VPN server.
- Membership in groups—Creating groups based on a user’s role within the organization ensures that customers and business partners have access only to specific files and applications and limited access to others.
Intranets—Internal Business Operations and Communications
An intranet is an internal private network. Intranets generally consist of web applications or portals and provide a system for internal employees to collaborate securely. Intranets limit outside communications by allowing only systems and users that have been authenticated on the corporate network. Intranets may be set up to allow a group of people such as a software development team to collaborate, or it can be a tool available to all employees. Some common items stored on an intranet are:
- Company directory
- Company locations and directions to them
- Organizational charts
- Corporate announcements
- Search capabilities for additional corporate resources
Intranets have been set up as a single repository for all employer-focused information. An intranet can update employees regarding holiday dates, building closures due to inclement weather, and changes to 401(k) or benefits information. It can also be a tool for employees to provide thoughts or opinions about the organization. Portals can also be developed for products. These portals can have software updates, roadmaps, documentation, and a section where questions can be asked and answered about a particular product.
Securing the intranet can be done using the same tools that are used for protecting any web application that is maintained by the employer. Authentication, access controls, and tools such as single sign-on or identity and access management, will ensure the information is accessed only by people with the proper credentials.
Extranets—External Supply Chains, Business Partners, Distributors, and Resellers
Extranets extend an intranet in a limited fashion, providing access to business partners, distributors, and resellers. For example, an organization might have a product site for its partners and distributors that contains software downloads and updates, documentation, and questions and answers regarding a specific product.
Extranets expand the usage and availability of intranets. Extending access to your external supply chain, business partners, distributors, and resellers lets these parties know that your relationship with them is important. Giving them the same access to materials and accessibility to resources that customer service and engineering have helps build the relationship and the trust between your organizations.
Security for extranets is provided via isolation, access controls, authentication, and encryption, if communication between the user and web portal is needed. Isolation of the network into a private and public network ensures that only certain users have access to certain networks. Extranets provide remote access to only the limited portions of a company’s infrastructure that are approved for third-party use. Extranets also limit access to specific resources on the extranet. Limiting access to specific applications, services, files and folders, and data ensures that confidential information does not get into the wrong hands. As previously discussed, authentication factors verify that users are who they say they are. Employing a stronger authentication method ensures this. Encryption secures the communication paths between the systems so that no one can access the data while on the network.
Secure E-Commerce Sites with Encryption
Many businesses sell goods and services online using e-commerce websites in a business to business (B2B) and/or business to consumer (B2C) fashion. Customers often provide sensitive information, such as passwords and credit card numbers, on these websites. This sensitive information must be protected against eavesdropping through the use of encryption technology, such as that provided by Transport Layer Security (TLS). This protocol supports a number of different cryptographic algorithms, relying on digital certificates (such as the one shown in FIGURE 7-7) and public key encryption, and works as follows:
- The web server sends its digital certificate to the web browser. The web browser extracts the web server’s public key from the digital certificate.
- The web browser verifies the web server’s certificate by comparing the certificate authority with the trusted authority list that the web browser was shipped with. The web browser computes a hash of the certificate and compares it with the hash in the certificate. The hash is decrypted using the trusted authority’s public key. If the hash matches, the certificate has not been tampered with. The web browser checks the validity date to ensure the certificate has not expired. The browser also checks to verify that the system that sent the certificate has the same uniform resource locator (URL) that was encoded into the identification information. After these checks match, the public key of the server is extracted from the server’s certificate.
- The web browser generates a random symmetric encryption key. This key will be used to encrypt the conversation between the web browser and the web server. The symmetric encryption key is encrypted with the web server’s public key—in other words, the symmetric encryption key has been “wrapped.” Remember that the web server’s public key was extracted from the web server’s digital certificate.
- The web browser sends the wrapped key to the web server. The web server decrypts the wrapped key with its private key. At this time, the web browser and the web server have the same symmetric encryption key. This encryption key will be used to start an encrypted conversation. The symmetric key will be used to encrypt and decrypt the messages.
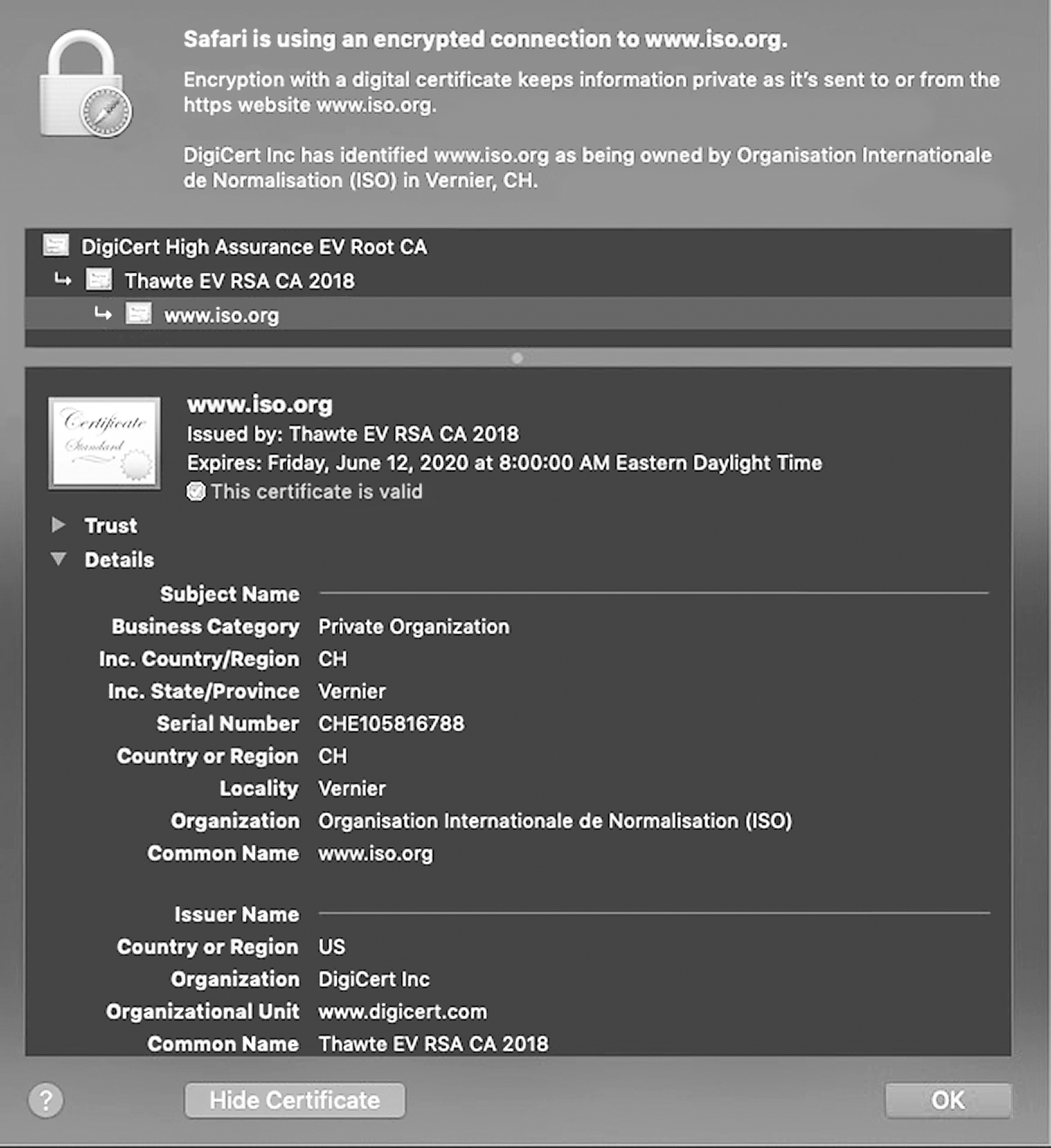
FIGURE 7-7 Example of a certificate.
Screen shot(s) reprinted with permission from Apple Inc.
 TIP
TIP
How do you know if a website is encrypted? If the web address starts with “https” and displays an icon that looks like a padlock, the website is secure.
Secure Online Banking Access Control Implementations
Online banking is another web portal access that implements encryption capabilities. The user and the bank want to ensure that the credentials entered are not retrieved through a separate entity such as an attacker. Banks that provide online access will also limit the amount of access available. If one user is able to see the accounts of a separate user, a security risk has occurred. Limiting the access for each user ID is a component on online banking.
Online banking sites require specific controls not only to protect the user’s access but to protect the bank’s as well. The Federal Financial Institutions Examination Council (FFIEC) is a body of the U.S. government that provides standards for financial institutions. The FFIEC has stated that an information security strategy should be based on the following:
- Consideration for prevention, detection, and response mechanisms
- Implementation of least privilege and the least permissive controls
- Layered controls between threats and organization assets
- Policies that guide employees and officers in implementing a security program
The FFIEC has established best practices for administering access rights. These access controls are:
- Assigning users and devices only the required access to perform their necessary functions
- Updating access controls based on personnel or system changes
- Periodically reviewing users’ access rights based on the risk associated with the application or system
- Designing the acceptable use policies and having the users agree to them
Formal access control administration consists of the following processes:
- An enrollment for all new users.
- An authentication process to identify the specific users. The appropriate authentication process should match the risk associated with the user. These authentication methods can include multifactor authentication as well as challenge and response mechanisms.
- An authorization process for authorized users. This process will employ controls around a user’s ability to add, delete, or modify applications, files, and specific information pertaining to that user.
- Monitoring and managing the access rights of specific users.
- Encrypting the transmission of user IDs and passwords.
The FFIEC has also established best practices for financial institutions to ensure secure access over multiple layers to protect against unauthorized access. These actions are:
- Grouping network servers, applications, data, and users into security domains
- Establishing the appropriate access requirements within and between the security domains
- Implementing the appropriate technical controls to ensure the access requirements
- Monitoring cross-domain access for security policy violations and anomalous activity
Implementing access controls for applications used by financial institutions is done via:
- Using authentication and authorization controls based on the risk of the application
- Monitoring the access rights to ensure that only the minimum access controls are granted to the users
- Using time-of-day access controls
- Logging of access and security events
- Using software that enables analysis of users’ activities
Best practices for remote access to financial institutions are identified by the FFIEC as:
- Disabling remote access if no business exists
- Controlling access through approval by management and audits
- Implementing controls on both ends of the communication in order to avoid malicious activities
- Logging and monitoring all remote access communications
- Securing remote access devices
- Using strong authentication and encryption to secure communications
Logon/Password Access
Online banking sites require multiple modes of authentication. Users should be comfortable sending this information if the site uses secure communications. Online banking portals may require users to follow strict password polices, ensuring they have a strong password. This authentication information will identify a user’s separate accounts and ensure that he or she is the only person who can access them. Users want to ensure that others cannot see their accounts and account number, and they do not want access to accounts they should not have access to. Using access controls reduces the security risks for both users and their banks.
As identified by the FFIEC, accessing an Internet banking environment with only single-factor authentication is not adequate for high-risk transactions that include access to customer information and movement of funds. The FFIEC recommends that if a financial institution provides an Internet-based service to customers, the appropriate multifactor authentication should be used. Providing the appropriate authentication method for users is necessary for protecting customer information. Not employing these mechanisms can result in credentials being compromised; therefore, identity theft, money laundering, and fraud can occur. The level of authentication should match the level of risk that a financial institution is willing to undertake.
Identification Imaging and Authorization
Online banking portals may provide secondary tactics for users to verify that their communications have not been hijacked. If a session were to be hijacked, a user would be providing his or her credentials to an attacker, and the account would most likely be compromised. Using a second authorization and identification provides a second layer of security. Identification that the website is a valid website protects the user.
Some online banking portals enable you to choose a custom image when you first set up your account. This image often appears before you enter your password. If the image you see is not the same image you originally selected, you know you should not continue logging on. Some banking portals even allow customers to create custom phrases, further enhancing the security of the financial information. You are likely required to enter a PIN as well to gain access to your accounts. Online banking portals aim to provide multiple layers of security to ensure that both the user’s information and the banking information is secure.
