Access Control for Data
A major concern for any IT department is the security and integrity of data, or information. The major method of securing that information is through access controls. Let’s take a look at some methods for securing information in its various forms.
Information can exist in one of two states: at rest or in motion. Data at rest is data that is in a storage system. Data in motion is data that is in transit, such as on a network. To truly protect data, you need to consider both of these states.
Data at Rest
Data at rest (DAR) is simply stored data. The data may be in archival form on tape or optical disc, on a hard disk, or even in memory. Depending on where the data are resting, they can be at very high risk. Some devices such as web servers are accessible from outside an organization’s network and are open to attack. Portable devices like smartphones, tablets, flash memory devices, and laptops are prone to physical theft and inadvertent loss. Unless properly secured, data at rest are vulnerable to theft. For this reason, it is critical to use appropriate access controls on this information.
Securing DAR
Administrators designing access controls for data at rest have a variety of models at their disposal. In high-security environments, they may choose to use a mandatory access control (MAC) model, where only the administrator grants access. Those seeking more flexibility will likely adopt the more common discretionary access control (DAC) model that allows users to delegate permissions. Users of both MAC and DAC models may also choose to implement role-based access control (RBAC) to simplify administration through the use of permissions based on individuals’ role(s) within the organization.
Let’s look at an example of file server access and DAR. A large corporation is establishing network storage for archival purposes for all of its employees. Each user’s local Documents directory is mapped to a folder on a network file server. The users are told that any document that needs to be backed up should be stored in the Documents folder. For ease of management and organization, each user’s folder on the file server is named with his or her logon. These folders are then organized by department, so each user folder is within his or her departmental folder.
Although documents are more easily backed up, end users raised concerns, especially users in the human resources (HR) and accounting departments. Some documents contain sensitive information that should not be accessible to all employees. This is where access controls come in. Each user is granted full rights to his or her network folder and limited rights to the departmental folder. For document-sharing purposes, users have rights to read and modify files in other user folders in their department; however, those rights may be altered by the owner of the document. Users do not have any access rights to any other department’s folders. Using access controls, the company is able to guarantee the privacy of sensitive data on the file share.
Access controls alone are not enough to secure DAR. Portable devices can be stolen and access controls can be circumvented. When a malicious user has access to the medium on which information is at rest, the user can circumvent standard access controls. A malicious user could mount a stolen laptop hard drive, for example, on another system on which he or she has administrative rights. The user could then take ownership of files and folders, modifying the access rights at will. This is where disk encryption becomes vital.
Disk encryption, especially whole disk encryption, is essential to securing data at rest, especially on a portable device. It’s difficult for an unauthorized user to extract data from an encrypted disk. Although a malicious user could attempt to decrypt the disk, it would take months or even years.
You must also consider physical security when dealing with DAR. If an organization uses backup tapes or optical media for archival purposes, how and where are those tapes stored and transported? How does the organization decommission and dispose of obsolete systems? Some organizations have discovered that improper data and device disposal can lead to information leaks. Here are some examples of data leaks due to poor data disposal practices:
- In 2018, SSM Health St. Mary’s Hospital in Jefferson City, Missouri, reported that improper storage of paper records led to a data breach affecting 301,000 individuals.
- In 2017, ShopRite Supermarkets reported that they improperly disposed of a pharmacy signature capture device that had stored the health records of as many as 12,172 individuals.
- At the end of the 2008 U.S. Presidential campaign, the McCain campaign sold off smartphones that were no longer needed. They neglected, however, to clear the devices’ memory before the sale and exposed the personal phone numbers of high-end donors and campaign officials.
- In 2006, a U.S. defense contractor sold obsolete hard drives on eBay. Information found on these drives included Top Secret documents on a new U.S. missile defense program.
- In 2005, a German police department sold a hard drive containing detailed plans on the department’s alarm systems as well as sensitive police procedural documentation.
There are countless other examples. A study by British Telecom found that 34% of the hard drives the company bought on eBay contained sensitive information. This included personal data, financial information, and even classified documents belonging to various nations.
Data in Motion
Data in motion (DIM) is the term used to describe data any time they travel from one place to another. For example, webpage files are considered in motion while they are sent from a web server through the Internet to a web browser (see FIGURE 8-1). DIM is vulnerable to improper disclosure and theft. DIM is vulnerable as it travels over the network, whether the network is wired or wireless. During transit, standard access controls applied by the operating system are irrelevant. Data packets on a network do not carry ownership information and are not modified by access controls that protect data at rest. Therefore, anyone with access to the network could access the data. The data are vulnerable at any point in transit.
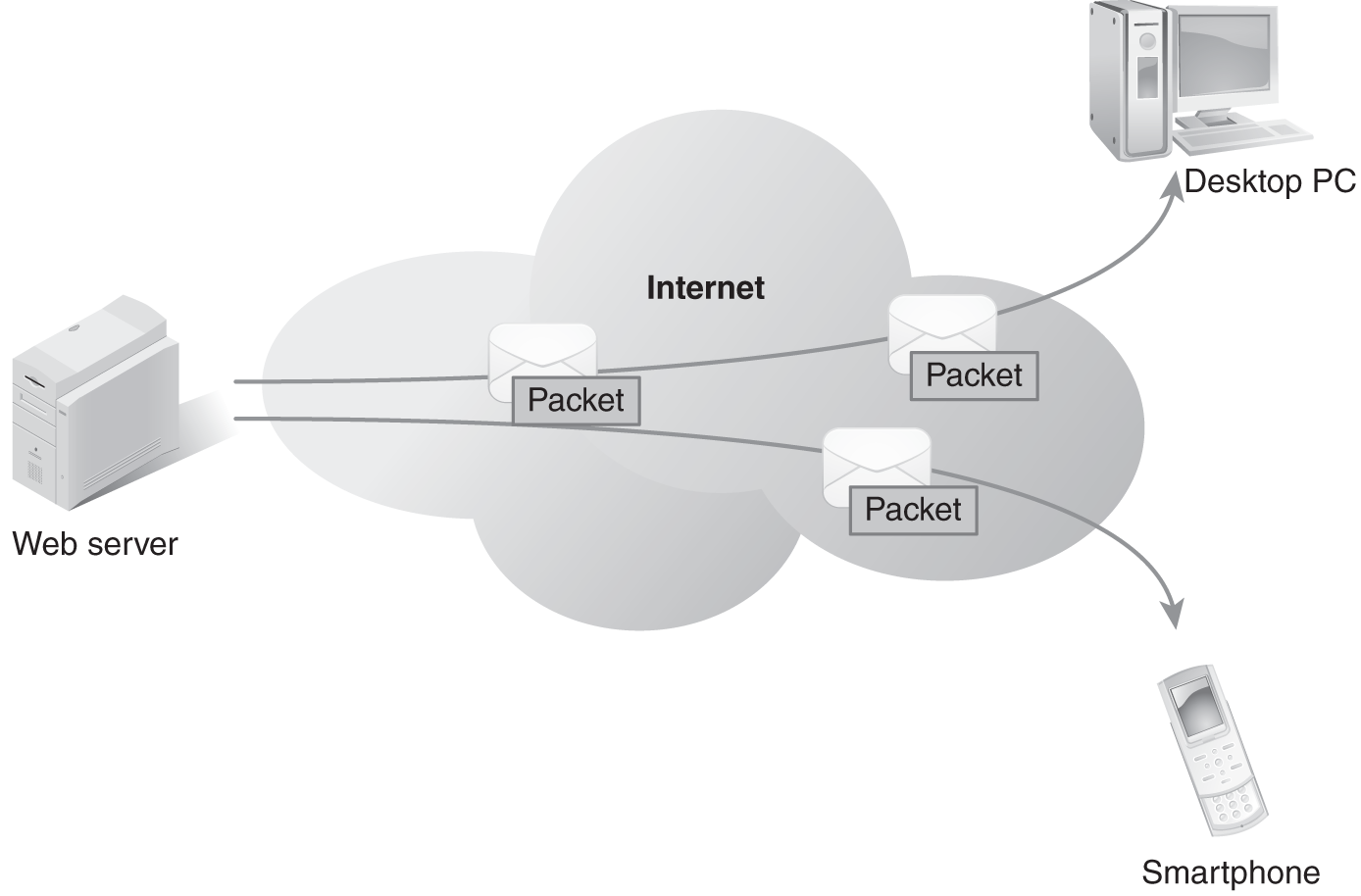
FIGURE 8-1 Data in motion.
DIM can also be at less risk than DAR, which seems counterintuitive. In a modern switched network, data travels from point to point. For an attacker to gain access to the DIM, she would have to know the path the data take while in transit. She also needs access to the physical wires or routers to insert her packet-sniffing equipment inside that path. This also applies to sending data over the Internet. The data travel a distinct path and are not shared with systems that are not on that path. An attacker could use various techniques to trick the switch or router into acting like a hub, which would broadcast the packets to multiple points, including her packet sniffer. However, the attacker would still need undetected access to that device for a significant period of time. At that point, an attacker would have access to an organization’s network and be able to compromise routers and switches. This represents a significant security breach, meaning that DAR will be at risk as well. If a switch can be compromised, any system on the network can be compromised.
Standard network security includes intrusion detection systems (IDSs), intrusion prevention systems (IPSs), and border protections like firewalls. These systems can effectively secure most DIM that doesn’t leave the local area network (LAN). An organization should further secure high impact data. There are two methods for securing DIM, encrypting data, and securing the communications channel.
Securing DIM
One way to secure DIM is to encrypt data. This is especially common with email. The information sender and receiver agree on an encryption technique and then share the appropriate keys. The sender then encrypts the information and the receiver decrypts it. Anyone who intercepts the data packets in transit is left with meaningless bits of data.
Another method is to secure the communications channel. You can use protocols such as Transport Layer Security (TLS) to accomplish this. TLS creates encrypted two-way communications at the Application Layer of networking. You’ll see this most commonly with Hypertext Transfer Protocol Secure (HTTPS) communications. You can also secure the path with a virtual private network (VPN) to provide a secure encrypted tunnel through a public network such as the Internet.
 NOTE
NOTE
You may see references to HTTPS using an older protocol, the Secure Sockets Layer (SSL), to encrypt data. SSL is outdated and insecure and is no longer appropriate for use. There are several known attacks that make it possible for a malicious individual to defeat the encryption used by SSL and gain unauthorized access to communications.
Object-Level Security
An object is an item or a distinct group of information in a data storage system, usually a relational database (RDB), but it can be any grouping of information. By grouping information as an object, applying access controls can be significantly more efficient. You can set controls at the object level. This allows you to manage groups of related data instead of managing individual items. Not only does applying security at the object level help with DAR security, it can also help with DIM security. If the network security device is object-aware, you can apply security rules to objects. This can be used to control how and where data can get transmitted. Application Layer firewalls and web content filters use object-level security to protect DIM.
