IT Security Policy Framework
Organizations have policies and procedures in place for various business units such as accounting and human resources. They also have essential policies for information security and access. The challenge for IT departments is to establish and continually update access control policies in an evolving technology and business environment. Creating and documenting standards for logical and physical security of the organization is essential in the protection of the organization’s infrastructure as shown in FIGURE 14-1.
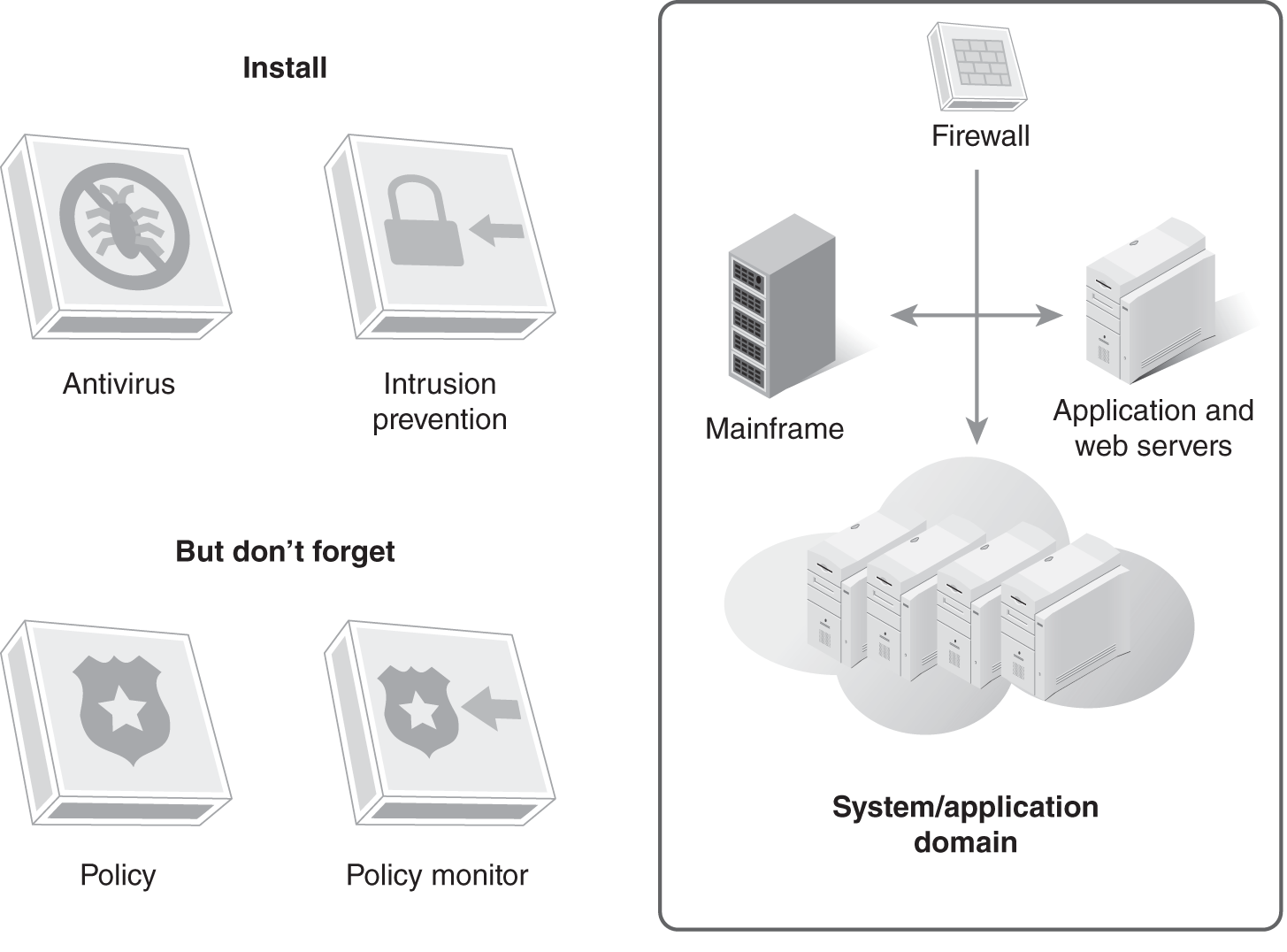
FIGURE 14-1 Protecting the infrastructure through logical and physical security policies and procedures.
The size of the organization, the types of information used, and the industry in which the company exists are all factors to consider when building an IT security policy framework. This framework must address both logical and physical security. The human aspect of security is vital as well. Without training and awareness programs, the best defense can fail. At the heart of these systems is a strong access control policy.
Before discussing security policy frameworks, it is helpful to define a few terms that are often used interchangeably:
- Policy—A policy is a document that describes specific requirements or rules that must be met in a given area. An organization’s acceptable use policy typically describes what is and is not acceptable use of the organization’s computing resources.
- Standard—A standard is a collection of requirements that must be met by anyone who performs a given task or works on a specific system. An organization might have a standard that describes the specific tests that must be performed before an application can be released to the production environment.
- Guideline—A guideline is a set of suggestions and best practices for meeting standards and policies. An organization might have strong password guidelines that describe the use of mnemonic devices or passphrases for creating strong passwords. Guidelines are strongly recommended practices but do not carry the weight of a mandatory requirement. An employee could use a random password generator to create a strong password, and thus meet the organization’s strong password policy without following the guidelines laid out for choosing passwords.
- Procedure—A procedure is a set of specific steps to be taken to achieve a desired result. Procedures are often written to ensure that tasks are completed in the same way each time, preventing unexpected problems. For example, an IT department might have a procedure for changing a password on a workstation. That procedure will include a step-by-step workflow with enough detail that anyone in the IT department could follow and expect the password to be changed correctly. Well-written procedures eliminate the problem of critical information being stored in one individual’s mind. If that individual leaves the organization, the information is lost.
A policy is a general-purpose document that describes high-level organizational rules and requirements. A standard is a more specific implementation of a policy. Guidelines are strong suggestions for implementing policies and standards. Procedures are step-by-step outlines for completing a specific task as outlined in the guidelines and standards.
 NOTE
NOTE
Failure to require strong access controls in a company’s security policy framework will contribute to vulnerabilities and breaches in the system. These breaches may result in the disclosure and loss of valuable information and assets and can expose the organization to civil and legal penalties.
Which Policies Are Needed for Access Controls?
The specific policies needed for access controls vary by organization, but in general, organizations should have policies that describe which users have access to sensitive systems and data, for what purpose, and for how long.
The following are common organization policies:
- Acceptable use policy (AUP): Describes what tasks can and cannot be performed using the organization’s computing resources
- Password policy: Describes the organization’s requirements for strong password creation and maintenance
- Account management policy: Describes how new accounts are to be created and secured, and old accounts deleted
- Remote access policy: Defines standards for connecting to the organization’s network offsite
These policies provide a basis for an organization’s access control systems. You should base them on the organization’s business needs and risk assessment.
What Standards Are Needed to Support These Policies?
A standard is a set of detailed processes or methods for implementing technology, hardware, or software solutions. Access control standards are the rules that an organization uses to control access to its IT assets. You need these standards for all points in access control from creation of the users, to granting and revoking rights, to user removal. Standards are important guides for evaluating an organization’s compliance with regulation.
Standards documents, established by collective agreement and approved by management, provide for common repeatable rules. This helps to safeguard access controls and policies. This allows an organization better control in protecting its infrastructure and assets. Some common standards documents that many organizations use are:
- User account standard: Describes the various types of user accounts on specific systems and networks
- Identification standard: Describes how user IDs will be defined based on the individual’s name, job function, or other identifying information
- Remote access standard: Describes the specific tools to be used to implement the organization’s remote access policy
- Application development standard: Describes the security precautions that must be designed into any application developed in-house
Every organization will have a unique set of standards based on business needs. These are the most common standards that most organizations use.
Which Procedures Are Needed to Implement These Policies?
You must establish access control procedures by outlining the steps needed to access organizational IT assets. Procedures should be included that detail authentication, account management, password management, and remote access. Additionally, you will need access determination policies and systems to restrict unauthorized access.
Procedures outlining specific steps for each process should be developed and used. The following is an example of an access request change procedure:
- User fills out an access request form.
- IT receives the form and passes it to the correct authority for approval.
- The form is reviewed and authorization is granted or denied.
- IT implements the access rights modification.
- After signoff, IT files the request in the user’s file to verify access and to provide information to an audit, if required.
This is a simple example of a procedure. Having explicit procedures is vital for the efficient and consistent application of an access control policy. Without written procedures, the risk of mistakes and errors in an organization’s access controls grows dangerously high.
What Guidelines Are Needed for Departments and End Users?
Guidelines are a collection of suggestions and best practices relating to a standard or procedure. A guideline doesn’t necessarily need to be met but compliance is strongly encouraged. Any access control policy in an organization will make reference to guidelines that are in existence in the organization. Although these actions are strongly encouraged, it is important to remember that these are not fixed rules. Guidelines are best viewed as recommendations.
An organization can have various guidelines for department and end users relating to access control policies. All of the information pertaining to the guideline should be included within a policy or procedure that a department or end user is required to follow. Inclusions into these official documents will lend weight to the guideline and allow a system to easily get them to the end users.
Some examples of departmental guidelines are:
- Department heads and managers should review access control systems periodically but not less than annually.
- User accounts should be disabled after 30 days of inactivity.
Some examples of individual guidelines are:
- Individuals should periodically review access control policies, standards, procedures, and guidelines.
- Individuals should not store critical information in their email accounts. Rather, critical information should be stored as documents on the file server.
- Users should not write down their passwords or base them on personally identifiable information. Instead, they should use a mnemonic to create a strong password that is also easy to remember.
Both individual and departmental guidelines should be written as helpful guidance for compliance with more official documents such as policies, standards, and procedures.
