Definitions and Concepts
Risk is a fact of life. There is no such thing as risk-free activity. Even the most common activities, such as walking across your living room, could be risky if, for example, you trip and fall. It isn’t possible to completely eliminate risk, as risk-taking is an important part of any organization’s business strategy. By taking risks, we introduce the potential to innovate and grow as an organization. However, in IT, we attempt to manage all of the risks we face by making informed decisions to mitigate, avoid, transfer, and accept risks.
Before continuing, let’s define some of the key terms you’ll see in this chapter:
- Risk—Risks occur when there is the potential that a particular threat will exploit a vulnerability, causing harm to an organization; risk is measured in terms of probability and impact.
- Asset value—Asset value is the relative value, either in monetary terms or in qualitative value, of the resource being protected by the access control system.
- Threat—A threat is an adverse event that may jeopardize the security of the organization, its information systems, and/or its data.
- Vulnerability—A vulnerability is a known or unknown weakness in a system’s design. A vulnerability may make it possible for an attacker to take control of a system, access resources to which he or she is not authorized, or damage the system in some way.
- Probability of occurrence—The likelihood that a threat will exploit a vulnerability.
- Impact—The impact on an organization if a risk materializes.
- Control—A technical, physical, or administrative process designed to reduce risk.
Risk assessment is the crucial first step in designing any access control system. In a risk assessment, you determine which risks exist in your environment or may occur in the future. You can measure the level of any risk by calculating the probability of occurrence and the potential impact on your environment. The following standard equation determines the level of each risk:
Risk = Probability × Impact
Knowing the level of risk helps you take appropriate steps to prevent the risk or mitigate it. For example, in most cases, it is probably not necessary to design a highly secure, three-stage access control system to protect a desktop printer. The probability that a desktop printer would be exploited is fairly low, and the overall impact of such an exploitation is similarly low. By the same logic, a simple username and password-based access control system would be inadequate to protect top-secret military documents, as the control is not commensurate with the level of risk.
 NOTE
NOTE
You’ll learn about types of risk assessments later in this chapter.
Risk is not a single problem that can be solved once and then ignored. It is also not just an IT problem. Risk is a multifaceted issue that affects every part of the organization. A user can create a highly secure password, but the system protected by that password is not considered secure if user passwords are not stored in a secure manner, or if numerous operating systems or application-level vulnerabilities allow an attacker to go around the access control system.
FYI
The most effective way to determine which threats are relevant to a given situation is to draw on a combination of research, experience, and brainstorming. Case studies are a good way to understand best practices and missteps to avoid for a given topic. The case studies in this chapter illustrate real-world examples of systems that have been attacked, which could have been avoided with the proper security measures in place.
Threats can take many forms, depending on the nature of the system under attack. Some systems, such as web servers, are most vulnerable to denial of service (DoS) attacks. Servers that contain sensitive data are more susceptible to data theft and user impersonation attacks. Networks and individual workstations are most often threatened by attackers who gain access to them as a stepping stone to other, more valuable resources such as servers and databases.
 TIP
TIP
Case studies and background experience can help you identify threats. However, thinking like an attacker is a highly useful way to perceive potential vulnerabilities. If you can look at your infrastructure from the point of view of an attacker, you may be able to see possible weaknesses and strengthen those areas before an attacker finds them.
Vulnerabilities are the weaknesses in a system that allow an attacker to gain access. Vulnerabilities are often obscure bugs in application or operating system code that allow attackers to gain access to low levels of the file system, but they can also take more obvious forms. Weak passwords and lax physical security measures are also vulnerabilities because they allow attackers to gain access to a system.
Probability of occurrence is a crucial aspect of risk assessments. In an ideal world, organizations would mitigate every possible vulnerability, but time and resources can be limited. It does not make sense to devote excessive resources to mitigating a vulnerability that has a very low probability of occurrence, while ignoring a vulnerability with a much higher probability. For example, if a security alert is issued concerning a certain virus that’s spreading across the Internet, the probability is high that your systems may be compromised. It makes sense to devote time and resources to scanning your systems for that virus and taking appropriate measures to eliminate it.
Impact describes the potential consequences of an attack. A scenario with a high probability but a low impact is a lower priority risk than one with a high probability and high impact.
For example, a virus that has already infected computers in hundreds of other organizations, costing them millions of dollars in lost productivity and lost data, has a high probability (because it is actively spreading) and a high impact (lost productivity and data). This virus would have a high-risk rating. On the other hand, a badly crafted phishing email that asks the reader to click a link that downloads a 10-year-old virus has a low probability (because most people will recognize it as a fake and delete it) and a low impact (the antivirus software installed on a computer will stop a virus that old). Most risks fall somewhere in between, as shown in FIGURE 4-1. Using a visualization, such as the one shown here, is a great way to help management understand risks. This simplifies the risk management process down to, “Start in the upper-right corner and begin addressing each risk, working your way down to the lower-left corner.”
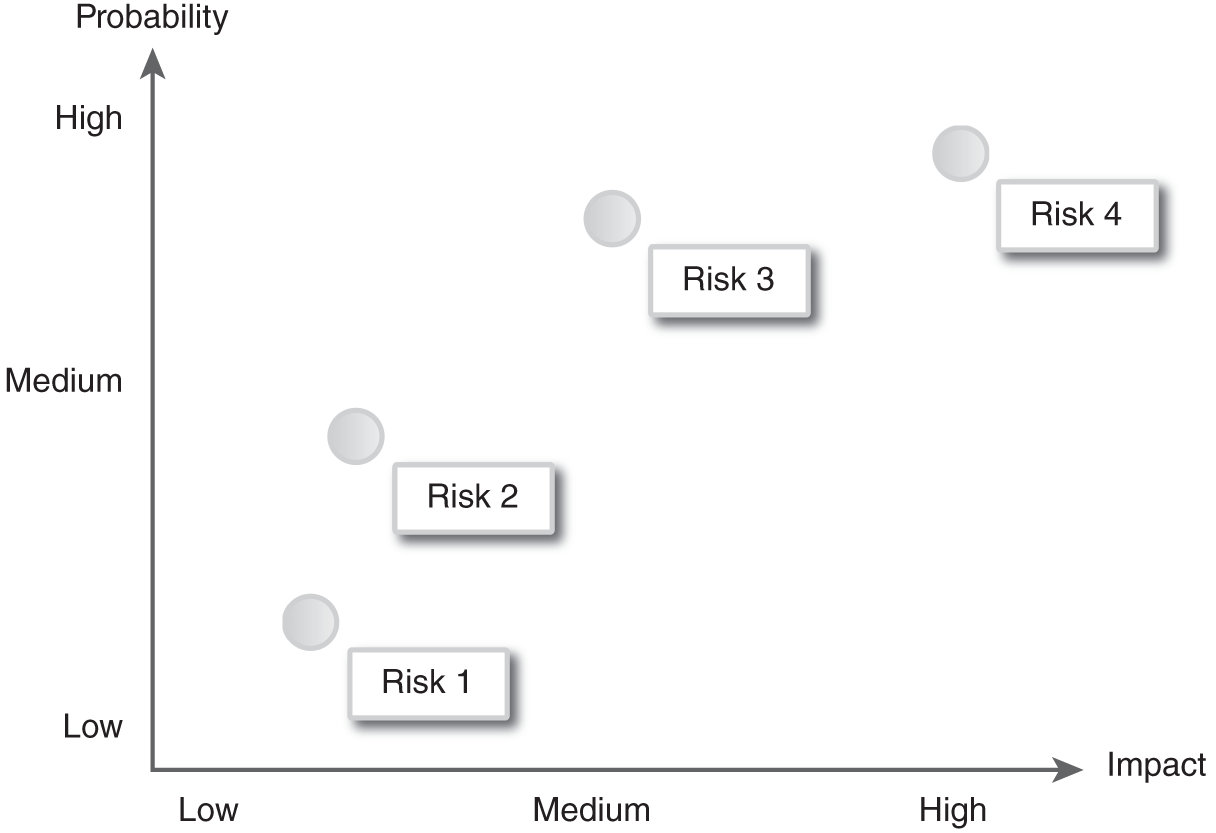
FIGURE 4-1 Risk = Probability × Impact matrix.
IT professionals put controls in place to lower both the probability and impact of a risk. A control, as you just read, is a technical, physical, or administrative process designed to reduce risk. The most useful controls strike a balance between the cost of implementing the control—in terms of actual financial cost and in lost productivity—and the value of the asset being protected. A firewall, for example, adds maintenance and configuration costs to your organization. If the assets behind the firewall are valuable, such as a file server or database storing sensitive data, the cost may be justified.
Controls do not have to be technology-based. Training employees on handling sensitive data is another valuable control because it could lessen the risk of a social engineering ploy. Although employee training is a strategic initiative that takes time and resources to execute, it is an effective method to reduce security breaches and is often well worth the investment.
