Access Control Process
There are three steps to the access control process:
- Identification—The process by which a subject identifies itself to the access control system
- Authentication—Verification of the subject’s identity
- Authorization—The decision to allow or deny access to an object
The second step usually happens behind the scenes, so the subject is really only aware of two stages: He or she enters credentials and is either given or denied access to a resource. FIGURE 1-1 illustrates the access control process using human interaction as an example.
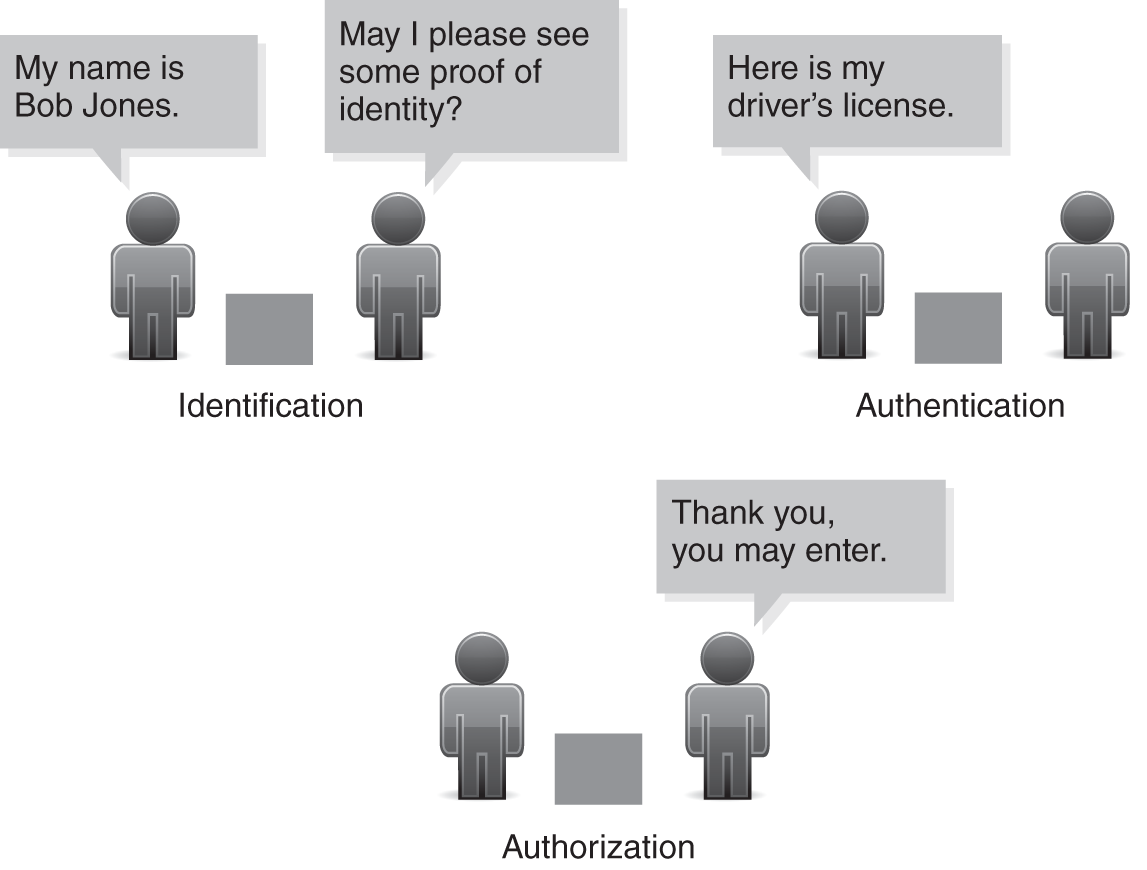
FIGURE 1-1 The access control process.
Identification
The first step in any access control process is identification. The system must be able to apply labels to the two parts of the access equation: the subject and the object. In this case, a label is a purely logical description that is easy for the computer to understand. A human might easily recognize that “Beth” and “Elizabeth” are the same individual, but a computer cannot necessarily make that logical connection.
 NOTE
NOTE
Trust is a two-way street. The system must trust that a subject has not falsified his or her credentials, but at the same time, the subject must be confident that the system will store those credentials securely. If a system stores usernames and passwords insecurely, they can be stolen and used to impersonate legitimate users. This destroys the integrity of the entire access control system.
To make things simpler, you can assign a universal label to each subject and object. That label remains with that individual or resource throughout the life cycle of the privileged interaction with the object. The object also has a label to distinguish it from other resources. For example, a network might have six printers available, labeled “printer1,” “printer2,” and so on. A person’s label might be a user ID, his or her email address, his or her employee ID, or some other unique identifier.
The key is that each label must be unique, because it also provides accountability. When combined with the authentication system (which correlates the identified subject with the resources he or she is allowed to use) and system logging facilities, unique labels correlate subjects with their actions. This becomes especially important when trying to track down the cause of a system failure. This correlation relies on the trust between the subject and the access control system. If you do not trust that subjects are who they say they are (and this trust is predicated on proof), the use of a uniquely identifying label is pointless.
Authentication
Authentication builds upon identification by requiring that the subject provide proof of identity. There are many ways to authenticate a subject. The most common ones are:
- Password—A secret word or combination of characters that is known only to the subject. A good password is difficult to guess but easy for the subject to remember.
- Token—Something the subject has that no one else does, such as a smart card or a challenge-response device.
- Fingerprint scan—Optical analysis of a person’s fingerprint compared with a recorded sample to verify identity.
The key to both a password and a shared secret is secrecy. If the subject shares its password or shared secret information with someone else, the authentication system becomes less secure and the ability to correlate an action to a subject becomes less precise. Many companies regulate this problem with a policy that an employee is personally responsible for anything done under his or her credentials. If an employee shares his credentials with a friend, for example, he is personally responsible for anything the friend might do.
Most authentication systems require only a single authentication factor, but those protecting highly sensitive assets might use multiple factors. The three most common factors are:
- Something you know—Generally a password or shared secret
- Something you have—A token or smart card ID badge
- Something you are—Fingerprints or other biometric factors
The last two factors are often used to provide or restrict physical access to secure buildings or rooms within buildings, although they can be used in access control systems protecting data as well. You will learn more about all three authentication factors later in the chapter.
Confidence in any authentication system can be measured by two components: the confidence in the accuracy of the authentication mechanisms and the number of authentication factors. An iris scan, such as the one shown in FIGURE 1-2, is a biometric authentication technique that is inherently more secure than a simple password because it is much more difficult to copy or steal an eyeball than it is to guess or steal a password. Using more than one authentication factor increases the security of the system, because if one stage of the authentication system is compromised, the second can still restrict access to those who do not have the proper credentials. This is referred to as “two-factor authentication.”

FIGURE 1-2 Iris scanning as an authentication technique.
© United States Department of Defense
Authorization
Once a subject has identified him- or herself and the access control system authenticates the subject’s identity, the access control system must determine whether the subject is authorized to access the requested resources. Authorization is a set of rights defined for a subject and an object. They are based on the subject’s identity. For example, a manager in the human resources department might be authorized to view personnel records but not authorized to edit the year-end financial report.
Authorization rules can be simple. For example, a corporate e-mail directory might allow access to any employee with a valid user account. Authorization rules can also be complex, depending on the value of the resources being protected and the number of people needing access. For example, a file server might limit folder access by an employee’s role and membership in a particular department.
In a small organization with a high level of trust among the users and resources that are not sensitive, a simple authorization system is reasonable. An enterprise system with a mixture of highly sensitive data and open printers on the same network needs a more complex authorization system. In this case, you might design a system with multiple levels of authorization—a low-level employee might be given rights to the printers, while a manager would have rights to the printers and some areas of the file system. High-level executives might have all the rights of a manager, as well as rights to view sensitive information. How you define your authorization rules depends on business needs and the sensitivity of the resources.
The bottom line is that organizations must perform a balancing act when designing their authorization systems. The more complex the approach to authorization, the more secure the environment. However, more complex authorization may cause user inconvenience and require more administrative work by IT staff.
