Threats and Vulnerabilities
In this section, you will learn about access control threats and vulnerabilities and how to assess their impact. Access control threats cannot be 100% eliminated because new ones are constantly being devised. Instead, security professionals try to minimize their probability and impact by eliminating as much vulnerability as possible. In order to correctly prioritize efforts at mitigating threats and vulnerabilities, we perform risk assessments to accurately decide which threats represent the biggest impact to resources and data.
Access Control Threats
There are three primary threats to any access control system:
- Password cracking—Guessing or deciphering passwords
- Heightened access—The ability of an attacker to log into a system under one level of access and exploit a vulnerability to gain a higher level of access
- Social engineering—The use of manipulation or trickery to convince authorized users to perform actions or divulge sensitive information to the attacker
Password Cracking
Password cracking is a constant game of cat and mouse within IT security. Security administrators set password rules to guarantee that users create secure passwords, and attackers use a combination of brute force and sophisticated algorithms to break those passwords. Security administrators respond by modifying their password policies, and the cycle begins again. Security administrators are hampered by the users’ need for convenience, while attackers are limited only by time and computing cycles.
For example, suppose the security administrator at XYZ, Inc., implements a typical password security policy. The policy states that passwords must be a minimum of eight characters long and may contain uppercase letters, lowercase letters, and numeric characters. This policy ensures that there are at least 628 or 2.18340106 × 1014 possible combinations, as shown in TABLE 4-1.
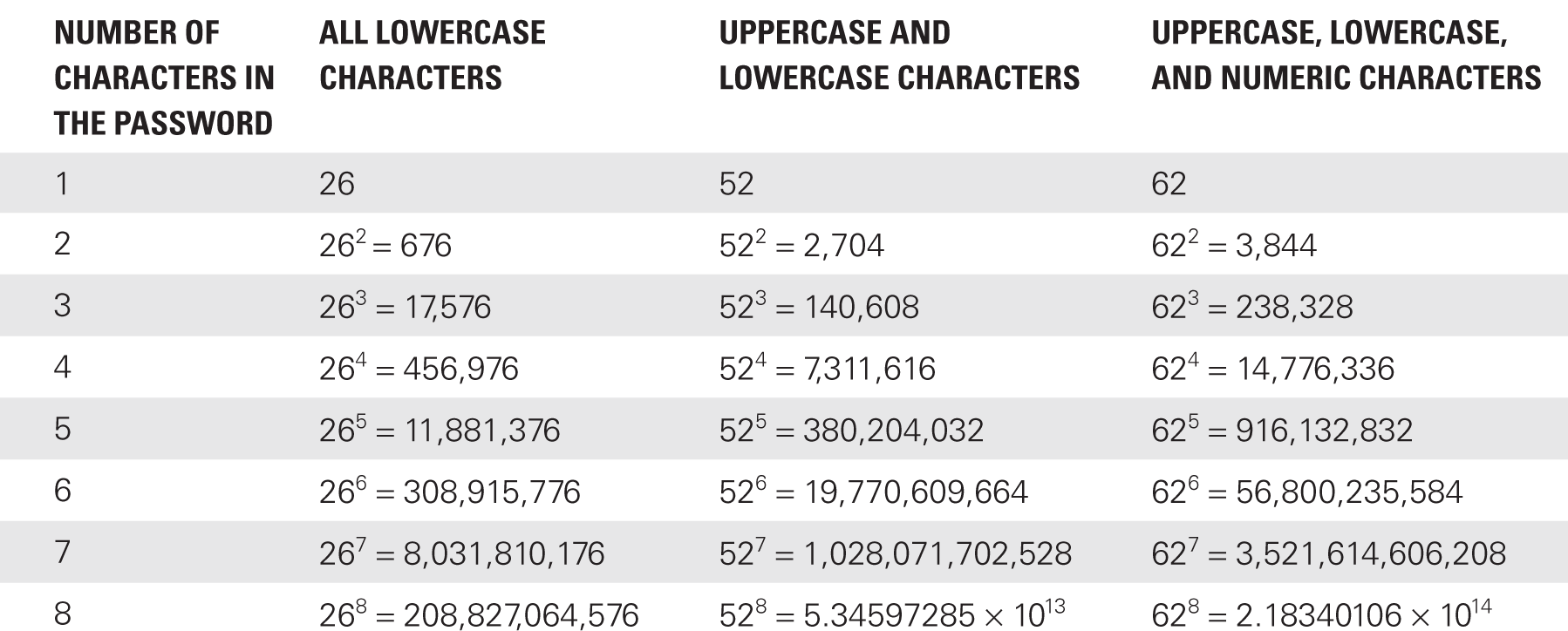
All these permutations are designed to increase the time it takes for an attacker to crack a password. An attacker uses an application designed to generate all possible permutations of case-sensitive alphanumeric characters and a simple script that inputs a known (or guessed) username with these generated passwords to the access control system. If an attacker’s password guessing application can try 100,000 passwords per second, it will take a matter of days to break a very simple password, or thousands of years to break a complex one, as shown in TABLE 4-2.
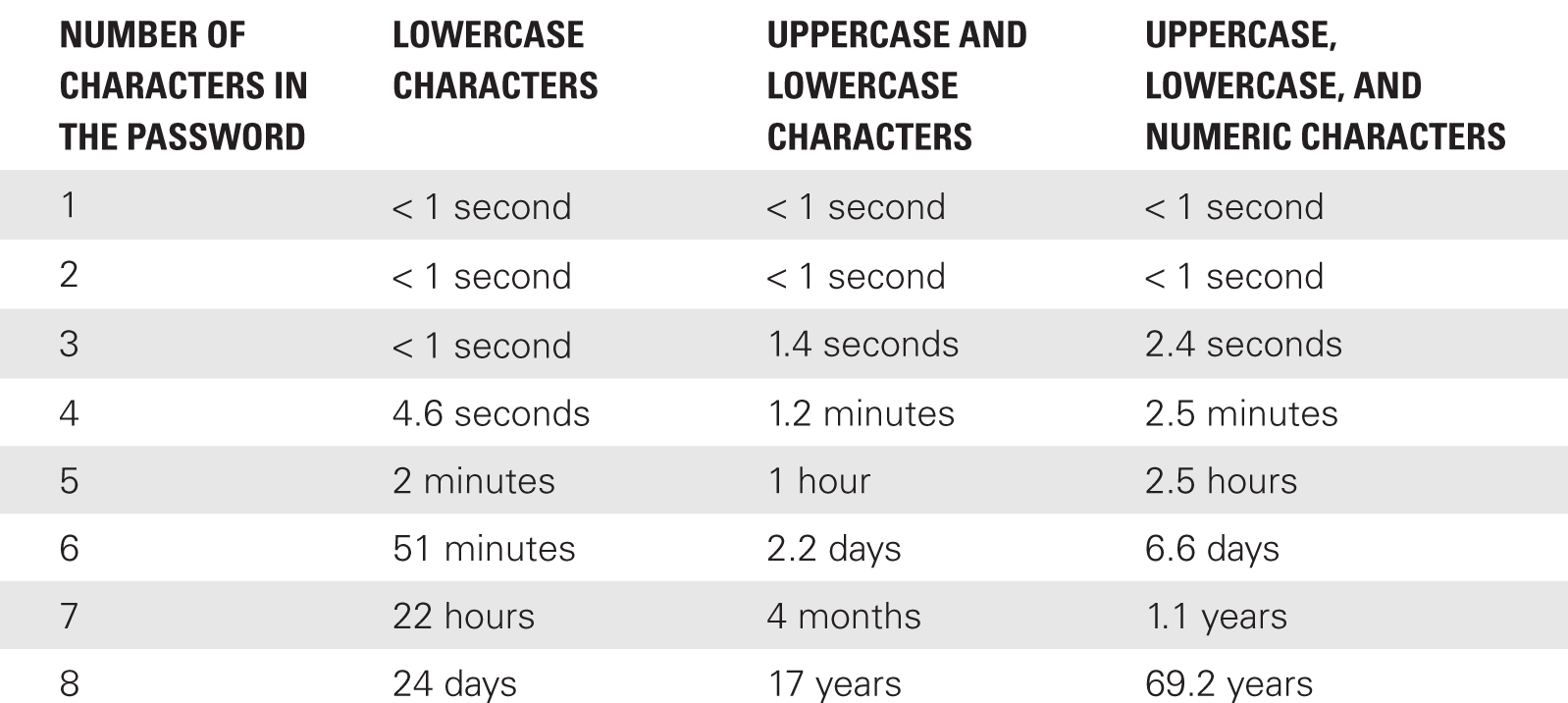
Given enough time, the attacker will eventually find a valid username and password combination, thus breaking into the system. The role of a security administrator is to identify this vulnerability and modify the password creation policy to require a longer minimum length and the use of at least one non-alphanumeric character. This does not necessarily make it more difficult for the attacker to break in—the attack is not really difficult to begin with because the cracking software does all the work behind the scenes. However, the longer, more secure password policy simply makes the process take longer. The goal is to push the time frame beyond one of two limits:
- The time it takes for the security administrator to realize the attack is occurring and disable the account under attack
- The expected lifespan—or at least the attention span—of the attacker
Even with the most sophisticated computing equipment available, it can take years or decades to crack a strong password. However, computer manufacturers are constantly developing more powerful systems, so a password that takes an average of 10 years to crack today may only take a few months to crack five years from now.
Heightened Access
Continuing with the example in the last section, once the attacker cracks a user’s password and can log into the system, the next step is to obtain heightened access. Chances are the really valuable assets on a system—sensitive data, for example—are protected by file and group permissions that do not allow every user on a system to read or write to them. However, attackers can exploit vulnerabilities in the operating system as well as within application code to achieve access levels normally denied to the user they are logged in as. You’ll learn about these vulnerabilities in more detail later in this chapter.
Social Engineering
Social engineering is the single most common strategy that attackers use to compromise secure systems. Social engineering is any strategy that tricks a user into giving up information that is helpful toward gaining access, or ultimately, the user’s credentials.
Not all social engineering tactics are technological. In fact, some of the most effective tactics are the simplest and exploit people’s general sense of trust and helpfulness. How many times have you held the door open for someone following you into a building? It is simply the polite, helpful thing to do. In a public place, such as the local mall, there is no security threat from such a simple act. But in a corporate environment where access to buildings or floors is limited to authorized personnel, simply holding the door open for someone could be a serious security breach.
Consider the following scenario: It is 8 a.m. on a typical Tuesday morning. Hundreds of people are filtering into the office to begin their work day. To enter the building, you must swipe your smart card ID badge. The person behind you has his hands full with his briefcase, coffee cup, keys, and a box of doughnuts. He smiles and asks you to hold the door. “Sure, no problem,” you answer as you hold open the door for him, assuming he is a fellow employee. He nods his head, smiles again, and thanks you as he heads confidently into another area of the building. This particular threat, where one person uses the successful authentication of another to gain access to a facility, is known as tailgating or piggybacking.
 NOTE
NOTE
Phishing is a very common social engineering tactic in which the attacker creates an authentic-looking email or webpage that convinces users to enter their confidential information or install software on their computer that secretly records information and sends it back to the attacker. Phishing attack attempts have become significantly more common and successful since 2019.
As you turn on your computer and check your morning email, the person who followed you into the building roams the hallways looking for unlocked offices and unsecured workstations. Often, employees keep sensitive information on their desks, which could help an attacker obtain access to assets stored on the corporate network.
Access Control Vulnerabilities
Vulnerabilities are the weaknesses in any security system that make a threat threatening. Without a vulnerability, a threat is simply a theoretical danger. For example, you live with the risk of electrocution every time you turn on the lights. The threat in this scenario is the electrical current running through the wires in your home. The vulnerability here is potentially bad wiring. If the wiring is bad, you could get a shock when you turn on the lights. However, if you were to build a home without that vulnerability—without wiring—you would face virtually no chance of electrocution. Yes, in theory, you could still be electrocuted if lightning were to strike you while sitting in your electricity-free home, but the probability of that occurring is low enough to be insignificant.
The primary vulnerabilities you need to mitigate to avoid a password-cracking attack are insecure passwords and insecure storage. Users want passwords that are easy to type and easy to remember. Unfortunately, these parameters do not usually lead to passwords that are difficult to guess or crack.
 NOTE
NOTE
Microsoft Windows XP, now no longer supported, used a weak hashing algorithm to store passwords up to 15 characters in length. The algorithm converted the password to all uppercase, then divided it into two fields, which were encoded separately. This allowed attackers to crack each half of the password separately using lookup tables.
Even the most secure password is worthless from a security standpoint if it is stored insecurely. Some applications store user passwords as plain text, either in a database or a flat file. This is becoming less common, but you may still run into this situation with legacy code. The more common problem is insecure password hashes. Most passwords are stored in an encrypted form. To decide whether the password entered by the user matches what the system has stored, the user-entered password is passed through a hashing algorithm. If this hashing algorithm is weak, an attacker can steal even the most secure password.
The most common vulnerabilities that allow an attacker to obtain heightened access are insecure applications that are run at too high of a privilege level. A common example of this problem is a web server where the web service, or daemon, is run as the administrative or root user. Often, when installing an application, a system administrator may be tempted to run the application under a privileged user account. This prevents problems when the application tries to write to the file system or access the network, but it also makes that privileged user account vulnerable to attack.
Ultimately, the biggest vulnerability in any access control system is its users. As discussed earlier in this chapter, people generally want to be helpful and trusting, which makes them perfect targets for social engineering. Thorough and repeated training is the best defense against social engineering.
