Designing a Comprehensive Plan
Perimeter security is any method that restricts access to a defined area, such as a military base, corporate campus, infrastructure facility, or office building. It is the first layer of defense in a physical security strategy. A backyard fence is a common example of perimeter security. It surrounds an area—a parcel of land that is designated for use by a homeowner—and restricts access to that area. Not only does it keep others out of a homeowner’s yard but it also keeps the homeowner’s pets inside the perimeter. In this way, a fence serves two purposes. It restricts access both to the yard and to the outside world.
Landscape design is an important aspect of perimeter security. From a purely aesthetic point of view, it may seem natural to improve the look of a fence by planting trees or bushes around it. Unfortunately, these natural elements can also provide a way for an intruder to climb over the fence. They can also provide cover for an intruder. This is not to say that every fence must be surrounded by 50 feet of bare ground. Landscape elements can also double as perimeter security devices. Thorny or spiky bushes can be planted below windows and other potential vulnerable spots in the perimeter of a facility. A well-placed bush will not stop a determined intruder, but it will encourage the intruder to look for another entry point.
Lighting is another key point in both landscape design and perimeter security. You should design lighting to illuminate official entry points and those areas that an intruder may use to break in. However, landscape lighting design should also avoid creating large areas of shadow that could provide cover for an intruder.
Security guards and closed-captioned video play an important role in perimeter security as well. Prior to the development of closed-captioned video systems, security guards could only patrol the area they could physically see from any given location. Therefore, to provide full perimeter coverage, a facility needed enough guards that each one could maintain line of sight with the guards on either side. Video cameras placed in such a way that their fields of vision overlap slightly, as shown in FIGURE 9-1, provide the same level of coverage with fewer guards. If they view suspicious activity on the monitors, one can investigate while the other continues to monitor the video system for additional activity in other areas of the facility.
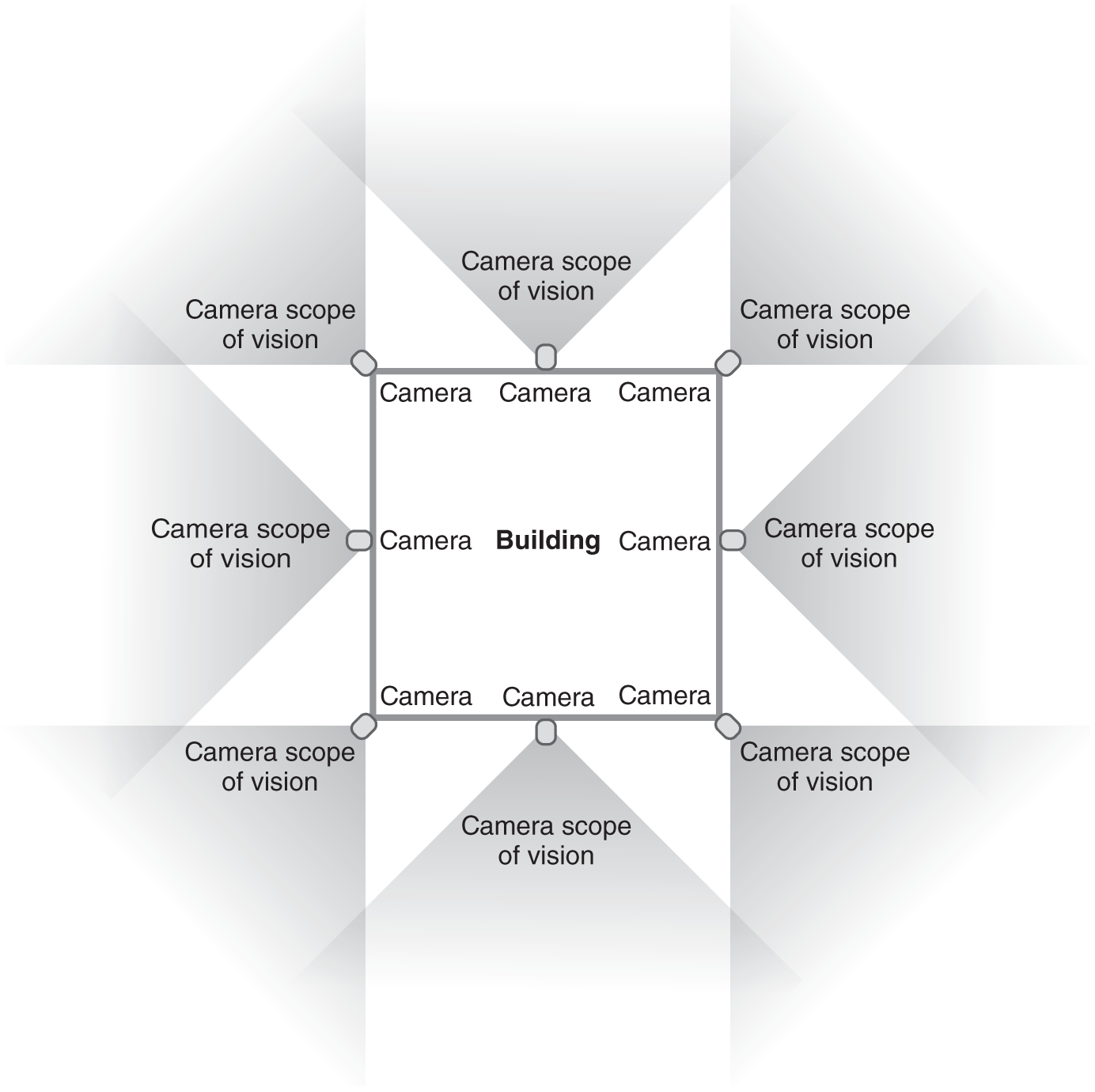
FIGURE 9-1 Video cameras provide perimeter coverage.
Although fences, landscaping, and guards are all designed to keep people out of a facility, there also needs to be a way to let authorized individuals into the facility. Gates of various types allow for monitored, controlled access to a secured facility. Not only do they allow for identification and authentication of individuals wishing to gain entry but they also restrict the flow of traffic into and out of a facility.
Gates are also a weak point in the perimeter, so their security should be heightened to compensate. The mere presence of a security guard at the gate is a deterrent, because it sends the message to intruders that the area is actively monitored and their presence may be detected. The same guard can perform identification and authentication tasks by checking ID badges of those wishing to enter through the gate and cross referencing with a list of authorized individuals. A guard can also strengthen the use of ID cards as an access control by physically inspecting the card to ensure that the picture on the ID matches the face of the individual attempting to use the card.
Building Security and Access
In some cases, building security and perimeter security are the same. This is most often the case with organizations located in urban office buildings. The organization’s perimeter is the outer wall of the building itself. In other cases, the building will be located at the center of a large, open expanse of landscaped ground. Under those circumstances, building security is a second layer of defense behind perimeter controls.
Building security involves some aspects previously discussed in perimeter security: lighting, security guards, and gates. It also includes elements such as locks.
Lighting design, both outside the building and in the entryway, is an important part of building security. Sensitive areas, including entryways, loading docks, and utility boxes, should be well lit to deter intruders and to enable security guards to monitor those areas.
Security guards stationed at the entry points to the building provide the same benefits as those stationed at a gate. Their presence is a deterrent, and they can perform identification and authentication tasks. The next section covers securing entry points in depth.
Access controls for building security revolve around the concept of the locked door. A locking mechanism can be as simple as a deadbolt with a key held by the building owner, or it can involve a system that combines ID badges and biometrics, which you will learn about later in this chapter. It is important to remember that when designing a locking mechanism, an intruder often takes the path of least resistance. A complex and highly secure lock might not prevent an intruder from entering the building if the intruder can simply remove the hinges that attach the door to the wall or break a nearby window. The lock strength must be matched by the integrity of the door and the surrounding area.
Points of Entry and Exit
Points of entry are weaknesses in any perimeter or building security plan. They must be designed to allow authorized individuals to access the building or facility, while identifying unauthorized individuals and preventing those people from entering (or exiting, in some cases).
Ensure your entry points are designed so that it is difficult or impossible to approach them undetected. They should be well lit and free from heavy landscaping that might provide cover to an intruder. Security guards posted nearby provide another layer of security at entry and exit points.
Cameras filming these areas not only allow security guards to monitor for suspicious activity but they also provide a record of who comes and goes. Although this may not prevent an intruder from entering the facility, it will provide evidence of his or her activity later.
It is important to note that when designing a physical security system, you should not only be concerned with who enters a facility but also with who leaves. This is especially important in specialized facilities such as daycare facilities, hospitals, and prisons, which are designed to keep people in as much as to keep people out. In a daycare center, it would be a catastrophic failure of physical security if a child were to wander away from the facility. Potential exit points must be monitored as closely as the official entry points to prevent this type of situation. Similarly, in healthcare facilities, especially those that serve mental health patients, exit points must be secured to prevent patients from leaving and becoming lost or harmed.
Physical Obstacles and Barriers
Physical barriers play an important role in perimeter and building security. Bollards are short vertical posts designed to control traffic and prevent vehicular attacks on a building. Bollards are designed to allow easy pedestrian access to an area while preventing vehicular access. They are often installed in areas where terrorist attacks are a concern. Some bollards, such as those shown in FIGURE 9-2, are retractable.

FIGURE 9-2 Bollards are permanent or retractable barriers designed to block vehicular access to an area.
Courtesy of KVDP.
Moveable concrete barriers are used in places where access and traffic patterns must be changed to suit differing circumstances. They are often used in large public areas during special events such as festivals and concerts, where crowd control and security are a major concern.
Granting Access to Physical Areas Within a Building
Once inside the building, different areas require different security measures. Generic work areas, for example, may not require any additional security systems beyond perimeter and building security. Simply monitoring those areas for suspicious behavior is usually sufficient. Sensitive areas such as data centers, however, require additional layers of security.
Non-Sensitive Work Areas
The primary physical security concern in nonsensitive work areas is suspicious behavior. These areas are often lightly monitored for the health and safety of employees and to ensure that employees are engaged in work activities.
These areas can also be targets for social engineers. Appropriate lighting, visible security personnel, and surveillance cameras are common ways to secure nonsensitive work areas.
Sensitive Work Areas
Sensitive work areas are those areas where the general public is not allowed and are places the average employee may not have access to. Consider a bank branch. The general public is restricted to the lobby area, while employees have access to the area behind the teller windows where cash is counted and stored.
In a bank branch, physical barriers are used to separate the public area—the lobby—from the sensitive work area. A reinforced counter topped with bulletproof glass generally acts as a barrier between the two areas. Security cameras, both hidden and overt, are placed to provide complete coverage of the entire area. Most bank branches have at least one uniformed security guard in attendance at all times.
As another example, consider a technology company engaged in software development work. They might have some nonsensitive areas, such as the reception area, vendor conference rooms, and a common dining area, but then, treat the majority of their work area as sensitive due to the nature of the software development that takes place there. An unauthorized individual accessing the area might be able to discern sensitive product development plans or even tamper with the software.
This company might choose to use a simple badge-based access control system to enter the nonsensitive areas of the facility but require biometric authentication, such as a hand geometry scan, before granting access to the sensitive areas of the building.
Government Facilities
Government facilities often have more stringent security requirements than private-sector facilities. Federal facilities, and the security measures they require, are divided into five levels by the Federal Protective Service (FPS):
- Level I—This facility has 10 or fewer employees, 2,500 or fewer square feet of office space, and little public contact.
- Level II—This facility has 11 to 150 employees, 2,500 to 80,000 square feet of office space, and a moderate volume of public contact. Level II facilities are often located in shared office buildings with private sector businesses.
- Level III—This facility has 151 to 450 employees, 80,000 to 150,000 square feet of office space, and a moderate to high level of public contact. These facilities are usually multistory buildings and often contain several agencies or offices.
- Level IV—This facility has more than 450 employees, 80,000 to 250,000 square feet of office space, and a high volume of public contact.
- Level V—This facility is occupied by one or more agencies with critical national security missions. Level V facilities require tenant agencies to secure the site according to their own needs, insofar as those needs exceed the security levels dictated by a Level IV facility. Examples of Level V facilities include the headquarters buildings of the National Security Agency (NSA), Central Intelligence Agency (CIA), and the military facilities at the Pentagon.
These facilities have strict access control and physical security standards that include control of parking facilities, receiving and shipping procedures, employee and visitor identification, and training requirements.
Regulations at government facilities require that parking facilities be restricted to government vehicles and personnel and that authorized parking spaces be assigned. Systems to tow unauthorized vehicles must be in place. Adequate lighting and closed-circuit television monitoring are also required to ensure the safety of employees and to deter illegal and threatening activities.
Shipping and receiving at government facilities is another area where physical security measures differ from most private-sector facilities. All packages arriving at a classified government facility must be x-rayed and visually inspected to prevent attacks on government employees and facilities through the mail.
As with many secure private sector facilities, all employees at governmental facilities must display an agency-issued photo ID at all times. Visitors must wear a visitor identification badge, sign in with a receptionist or security guard, and be escorted at all times while within the facility.
Computer Rooms and Data Centers
Computer rooms and data centers are specialized forms of sensitive work areas. Access to these areas should be restricted to a few select individuals, and some data centers go one step further by going “dark.” A dark data center is one that is monitored and managed remotely. Robotic devices in dark data centers perform tasks that normally require human intervention, such as cycling the power on a server or changing tapes in a backup system. Because human beings don’t ordinarily work in a dark data center, the lights are usually off. This provides another layer of security. If the lights are on, or light from a flashlight shines through a window or across a video monitor, security personnel will most likely notice this suspicious activity.
Any data center, whether staffed or dark, should have access locks on all server racks and individual systems, as well as restrictions on electronic devices that can be brought into the data center. This prevents unauthorized data removal. Modern electronic devices, such as smartphones and flash storage devices, can hold a significant amount of data and are so small and ubiquitous that they often escape notice.
Port locks on servers and racks prevent intruders from downloading data to a portable device by restricting access to USB ports. Without access to these ports, it is impossible to physically connect a portable device to the server, although wireless access may still be possible.
Computer rooms and data centers usually have strict policies against bringing in food or drink. Although these policies do prevent accidental spills that could damage sensitive equipment, they also minimize the need for custodial maintenance. If the server room rarely needs to be cleaned, custodial staff do not need regular access to that room. The fewer people who have access to a data center, the more secure it is.
