Chapter 6 PSK Authentication
IN THIS CHAPTER, YOU WILL LEARN ABOUT THE FOLLOWING:
✓ Simultaneous Authentication of Equals (SAE)
This chapter discusses preshared key (PSK) authentication, which was originally intended as a simple security solution to be used in small office/home office (SOHO) environments. PSK authentication is also known by the more common name of WPA-Personal or WPA2-Personal. Although 802.1X/EAP is the preferred security method for the enterprise, PSK authentication is used in many enterprises despite its weaknesses. We will explore the PSK security mechanisms, risks, and the importance of entropy. We will also discuss per-user/per-device implementations of PSK that some WLAN vendors offer as an enhancement to static PSK authentication solutions. Finally, we will discuss a proposed replacement for PSK authentication called Simultaneous Authentication of Equals (SAE).
WPA/WPA2-Personal
As you know, the IEEE 802.11i security amendment, which was ratified and published as IEEE Standard 802.11i-2004, defined a robust security network (RSN) using stronger encryption and better authentication methods. The 802.11i amendment is now part of the IEEE 802.11-2012 standard. As you learned in Chapter 5, “802.11 Layer 2 Dynamic Encryption Key Generation,” the 802.11-2012 standard defines authentication and key management (AKM) services. AKM services require both authentication processes and the generation and management of encryption keys. An authentication and key management protocol (AKMP) can be either a preshared (PSK) or an EAP protocol used during 802.1X/EAP authentication. 802.1X/EAP requires a RADIUS server and advanced skills. The average home Wi-Fi user has no knowledge of 802.1X/EAP and does not have a RADIUS server in their home. PSK authentication is meant to be used in small office/home office (SOHO) environments because the stronger enterprise 802.1X/EAP authentication solutions are not available. Therefore, the security used in SOHO environments is PSK authentication. WPA/WPA2-Personal is the same thing as PSK authentication.
Most SOHO wireless networks are secured with WPA/WPA2-Personal mechanisms. Prior to the IEEE ratification of the 802.11i amendment, the Wi-Fi Alliance introduced the Wi-Fi Protected Access (WPA) certification as a snapshot of the not-yet-released 802.11i amendment, supporting only TKIP/ARC4 dynamic encryption-key generation. 802.1X/EAP authentication was required in the enterprise, and a passphrase authentication method called WPA-Personal was required in a SOHO environment.
WPA-Personal allows an end user to enter a simple ASCII character string, dubbed a passphrase, anywhere from 8 to 63 characters in size. Behind the scenes, a “passphrase to PSK mapping” function takes care of the rest. Therefore, all the user has to know is a single, secret passphrase to allow access to the WLAN.
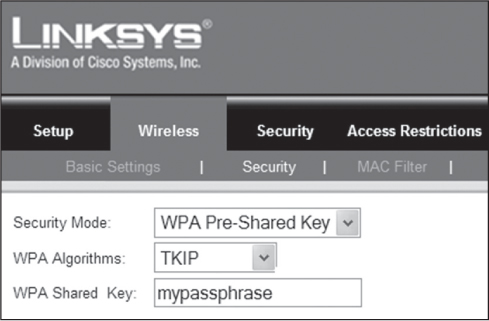
In June 2004, the IEEE 802.11 TGi working group formally ratified 802.11i, which added support for CCMP/AES encryption. The Wi-Fi Alliance therefore revised the previous WPA specification to WPA2, incorporating the CCMP/AES cipher. Therefore, the only practical difference between WPA and WPA2 has to do with the encryption cipher. WPA-Personal and WPA2-Personal both use PSK authentication methods; however, WPA-Personal specifies TKIP/ARC4 encryption and WPA2-Personal specifies CCMP/AES. WLAN vendors have many names for PSK authentication, including WPA/WPA2-Passphrase, WPA/WPA2-PSK, and WPA/WPA2-Preshared Key. For example, Figure 6.1 shows a Linksys Wi-Fi router that uses the term WPA Pre-shared Key. The correct Wi-Fi Alliance terminology is WPA/WPA2-Personal. All of these terms refer to 802.11 PSK authentication.
FIGURE 6.1 Vendor terminology example
Preshared Keys (PSK) and Passphrases
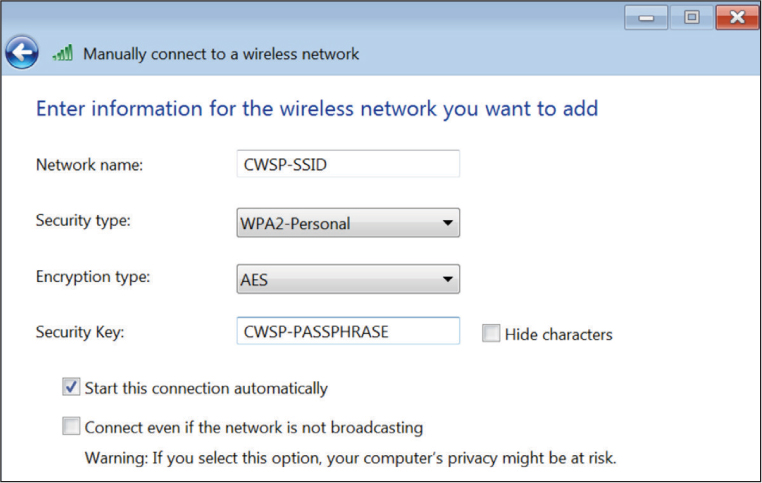
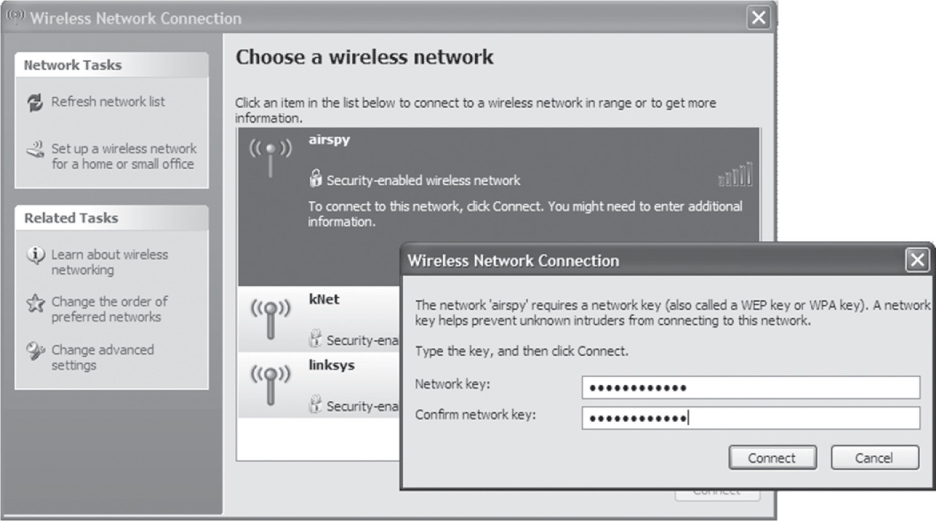
A preshared key (PSK) used in a robust security network is 256 bits in length, or 64 characters when expressed in hex. A PSK is a static key that is configured on the access point and on all the clients. The same static PSK is used by all members of the basic service set (BSS). The problem is that the average home user is not comfortable with entering a 64-character hexadecimal PSK on both a SOHO Wi-Fi router and a laptop client utility. Even if home users did enter a 64-character PSK on both ends, they probably would not be able to remember the PSK and would have to write it down. Most home users are, however, very comfortable configuring short ASCII passwords or passphrases. As shown in Figure 6.2, the home user enters a passphrase, which is an 8-to 63-character string entered into the client software utility on the end-user device and also at the access point. The passphrase must match on both ends.
FIGURE 6.2 Client configured with passphrase
As you learned in Chapter 5, a passphrase-PSK mapping formula is defined by the 802.11-2012 standard to allow end users to use a simple ASCII passphrase that is then converted to the 256-bit PSK. Here is a quick review of the formula to convert the passphrase to a PSK:
PSK = PBKDF2(PassPhrase, ssid, ssidLength, 4096, 256)
A simple passphrase is combined with the SSID and hashed 4,096 times to produce a 256-bit (64-character) PSK. Table 6.1 illustrates some examples of how the formula uses both the passphrase and SSID inputs to generate the PSK.
TABLE 6.1 Passphrase-PSK mapping
Passphrase (8–63 characters) |
SSID |
256-bit/64-character PSK |
carolina |
cwsp |
db119f5a0f86166dc2c12f6f6dcc2ac2121f1decf83c83d |
certification |
cwsp |
e7b3a9521a6c71236ff47cfa310f942b1a9cbb04307191ed |
Victoria |
cwsp |
538e225e1d04cce3a274d2c1ca748f3e37b5cbdfe31c04e |
The whole point of the passphrase-PSK mapping formula is to simplify configuration for the average home end user. Most people can remember an 8-character passphrase as opposed to a 256-bit PSK.
The 256-bit PSK is also used as the pairwise master key (PMK). The PMK is the seeding material for the 4-Way Handshake that is used to generate dynamic encryption keys. Therefore, the PSK in WPA/WPA2-Personal mode is quite literally the same as the PMK.
Previously, you learned that the 802.1X/EAP process generates a PMK and that every supplicant has a unique PMK. The same cannot be said when PSK authentication is used. The 256-bit PSK is the PMK. Because every client station uses the same PSK, or passphrase that is converted to a PSK, every client station has the same pairwise master key (PMK). This presents a serious security risk.
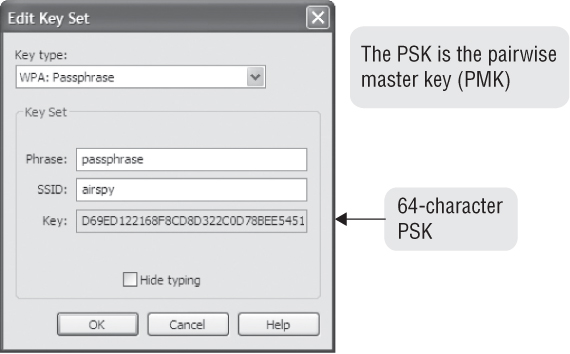
If a hacker is able to obtain the passphrase maliciously, the hacker could then use the passphrase-PSK mapping formula to re-create the 256-bit PSK. As you can see in Figure 6.3, most protocol analyzers are aware of the passphrase-PSK mapping formula and use the SSID and passphrase inputs to re-create the 256-bit PSK. Remember that the PSK is also used as the pairwise master key (PMK). An online 256-bit PSK generator can be found at www.wireshark.org/tools/wpa-psk.html.
FIGURE 6.3 Passphrase-PSK mapping
The 4-Way Handshake uses a pseudo-random function to combine the PMK with the Authenticator Nonce (ANonce), Supplicant Nonce (SNonce), Authenticator Address (AA), and Supplicant Address (SPA) to create a pairwise transient key (PTK). As you learned in previous chapters, the PTK is used by the client station and the AP to encrypt/decrypt unicast 802.11 data frames.
The ANonce, SNonce, and the MAC addresses of the client station and the access point are all seen in clear text during the 4-Way Handshake frame exchange. Once the hacker has the PMK derived from the passphrase, the final step is to capture a 4-Way Handshake exchange between a client station and an AP with a protocol analyzer. The attacker now has all the variables needed to duplicate the pairwise transient key (PTK). If the hacker can duplicate the PTK, the hacker can then decrypt any unicast traffic between the AP and the individual client station that performed the 4-Way Handshake.
Passphrase-PSK Mapping
In this exercise, you will use a protocol analyzer and passphrase-PSK mapping to regenerate the pairwise master key (PMK). You will then use a capture of a client station’s 4-Way Handshake EAPOL-Key frames together with the PMK to re-create the temporal keys that are used for encryption. You will then be able to decrypt the data frames using the temporal key.
To perform this exercise, you need to first download the PASSPHRASE_PSK.PCAP file from the book’s online resource area, which can be accessed at www.sybex.com/go/cwsp2e.
After the file is downloaded, you will need packet analysis software to open it. If you do not already have a packet analyzer installed on your computer, you can download Wireshark from www.wireshark.org.
Using the Wireshark packet analyzer, open the PASSPHRASE_PSK.PCAP file. Most packet analyzers display a list of capture frames in the upper section of the screen, with each frame numbered sequentially in the first column.
Observe the 4-Way Handshake frame exchange in packets 18–24. Click on frame 34 and observe that CCMP is used to encrypt the 802.11 QoS Data frame.
To create a 256-bit PSK, open a web browser and go to the URL www.wireshark.org/tools/wpa-psk.html. As shown here, enter the passphrase value of certification and the SSID value of cwsp and click the Generate PSK button. Highlight and copy the 256-bit PSK.
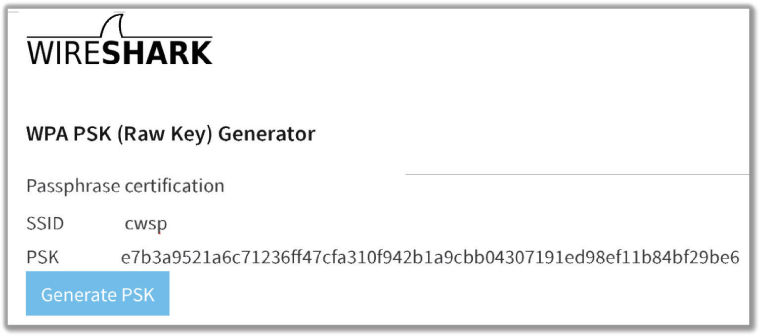
In Wireshark, click Edit
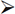 Preferences and expand Protocols. Click and highlight the IEEE 802.11 protocol and then choose the Enable Decryption check box as shown here.
Preferences and expand Protocols. Click and highlight the IEEE 802.11 protocol and then choose the Enable Decryption check box as shown here.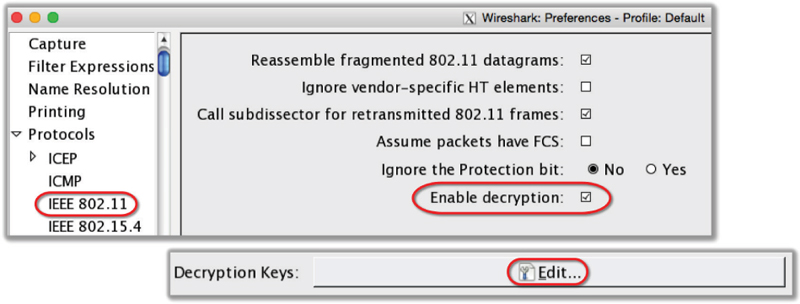
Next to Decryption Keys click the Edit button. Click the New button. Choose wpa-psk from the Key Type drop-down. For the Key value, paste the 256-bit PSK that was created earlier. Click OK. Click Apply and OK to close the encryption key window. Click Apply and OK to close the protocol window.
Notice that all of the previously encrypted 802.11 data frames are now decrypted. Scroll to packet 34 to view a decrypted DHCP discovery request packet.
The SSID and passphrase inputs were used to create the pairwise master key (PMK). Combining the PMK along with the ANonce, SNonce, and MAC addresses found in the 4-Way Handshake enabled you to re-create the pairwise transient key (PTK). The PTK was then used to decrypt the unicast 802.11 data frames.
WPA/WPA2-Personal Risks
The risks involved with WPA/WPA2-Personal are basically twofold: network resources can be placed at risk and the encryption keys can be compromised. First, let us discuss how network resources can be placed at risk. WPA/WPA2-Personal uses the weak PSK authentication method that is vulnerable to an offline brute-force dictionary attack. WLAN auditing software such as coWPAtty and Aircrack-ng can be used for malicious purposes to obtain weak passphrases using an offline brute-force dictionary attack. We will discuss how to protect against these types of attacks later in this chapter.
NOTE
More information about WLAN auditing tools, such as coWPAtty and Aircrack-ng, can be found in Chapter 13, “Wireless LAN Security Auditing.”
The easier way to obtain a WPA/WPA2 passphrase is through social engineering techniques. Social engineering is the act of manipulating people into performing actions or divulging confidential information. The simplest way to get the passphrase is to just ask someone what it is and they may tell you.
As you can see, a hacker can obtain the passphrase using social engineering skills or an offline brute-force dictionary attack. Once the passphrase is compromised, the hacker can use any client station to associate with the WPA/WPA2-Personal configured access point. The hacker is then free to access network resources. This is why PSK authentication was never intended for use in the enterprise and was intended for use as a SOHO security method.
We have already discussed the second risk involved with WPA/WPA2-Personal. If a hacker is able to obtain the passphrase maliciously, the hacker can use the passphrase-PSK mapping formula to re-create the 256-bit PSK and therefore the PMK. The hacker can use the PMK combined with a packet capture of the 4-Way Handshake to re-create the unicast encryption key. As demonstrated in Exercise 6.1, if the hacker can duplicate the PTK, the hacker can then decrypt any unicast traffic between the AP and the individual client station that performed the 4-Way Handshake. Also keep in mind that WPA-Personal uses legacy TKIP encryption, which is considered to be a weak form of dynamic encryption. As mentioned many times in this book, TKIP is not supported for 802.11n and 802.11ac data rates. If PSK authentication is chosen, only WPA2-Personal devices that use CCMP encryption should be deployed.
Entropy
In digital communications, entropy is a measure of uncertainty associated with a random variable. The complete explanation of the information theory on which entropy is based is well beyond the scope of this book, but we will attempt to explain entropy as it relates to the use of passphrases.
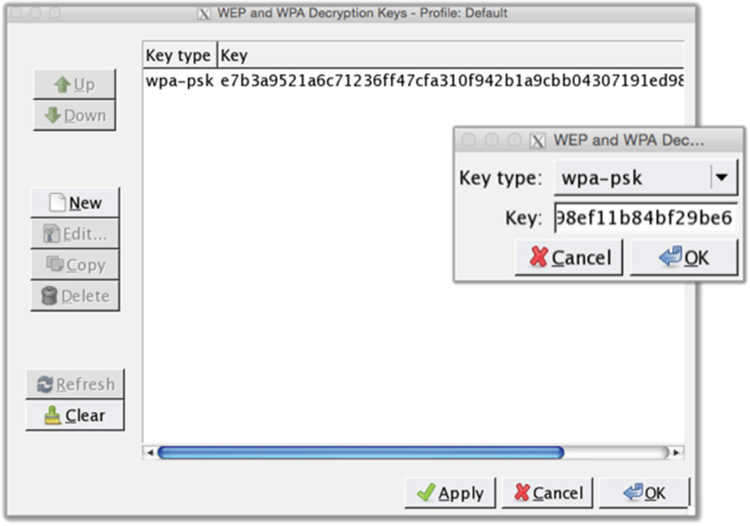
The random act of flipping a coin can be used to visualize entropy. The final result of a coin flip will either be “heads” or “tails,” but there is no way to tell what the result will be each time the coin is flipped. The measure of uncertainty associated with the randomness of a coin flip is equal to one bit of entropy. Another example of entropy is when you roll a single die, it will land on one of six sides. As shown in Figure 6.4, the measure of uncertainty associated with the random roll of a single die is equal to 2.58 bits of entropy. A random variable has a certain number (N) of outcomes. A coin flip has two possible outcomes whereas the roll of a die has six possible results. The roll of the die has more uncertainty than a coin flip; therefore, it has more bits of entropy. The more randomness there is to a situation, the more measureable bits of uncertainty exist. The formula to calculate entropy is log2(N), where N is the number of possible outcomes. Thus, the formula for the role of the die is log2(6), which is equal to 2.58 bits. To confirm this, you can calculate the inverse formula, which is 2^2.58, which is approximately 6 (we rounded down to 2.58).
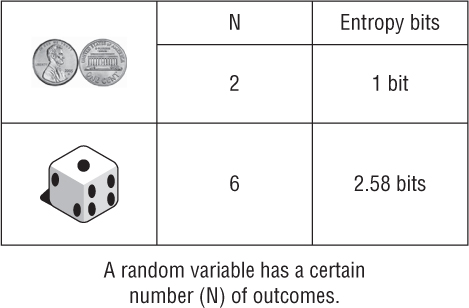
As shown in Table 6.2, entropy bits can also be applied to individual characters in a password or passphrase. For example, if a personal identification number (PIN) was created from the numerical digits, each character of the PIN has 10 possibilities (0–9). Based on complex informational theory, each character created strictly from numerical digits would have 3.3 bits of entropy. If the single-case letters were used in a PIN, each character of the PIN has 26 possibilities (a–z). Based on complex informational theory, each character created strictly from numerical digits would have 4.7 bits of entropy.
Symbol set |
N of symbols |
Entropy bits per character |
Numerical digits (0–9) |
10 |
3.32 bits |
Single-case letters (a–z) |
26 |
4.7 bits |
Single-case letters and digits (a–z, 0–9) |
36 |
5.17 bits |
Mixed-case letters and digits (a–z, A–Z, 0–9) |
62 |
5.95 bits |
Mixed-case letters, digits, and symbols (Standard U.S. keyboard) |
94 |
6.55 bits |
Passwords or passphrases by themselves have an entropy value of zero. It is the method you use to select the passphrase that contains the entropy. When strong passwords or passphrases are created, they should include a combination of uppercase and lowercase letters, numbers, and special symbols. A strong passphrase will have more entropy bits per character than a password created from a name or phone number. The more entropy (measured in bits) that is contained within the method you use to create your passphrase, the more difficult it will be to guess the passphrase.
Now let’s discuss how many entropy bits are contained in a passphrase used in WPA/WPA2-Personal. The following is a quote from the original 802.11i-2004 amendment:
A passphrase typically has about 2.5 bits of security per character, so the passphrase mapping converts an n octet password into a key with about 2.5n + 12 bits of security. Hence, it provides a relatively low level of security, with keys generated from short passwords subject to dictionary attack. Use of the key hash is recommended only where it is impractical to make use of a stronger form of user authentication. A key generated from a passphrase of less than about 20 characters is unlikely to deter attacks.
— 802.11i-2004 amendment
What this quotation means is that each character in a passphrase is worth only 2.5 bits of entropy because most users choose easy-to-remember words as opposed to a mix of alphanumeric and punctuation characters. Therefore, an 8-character passphrase would only contain 20 bits of entropy before the passphrase-to-PSK mapping hash algorithm is calculated. Because the passphrase-to-PSK mapping mixes the SSID with the passphrase, approximately 12 extra bits of entropy are added. Therefore, a typical 8-character passphrase used in a WPA/WPA2-Personal configuration would have a total of 32 bits of entropy.
Please do not confuse entropy security bits with the number of digital bits in a PSK. The passphrase-to-PSK mapping formula will always convert any passphrase of 8 to 63 characters into a 256-bit PSK. Remember that entropy bits are a measure of uncertainty associated with a random variable. The random variable is basically the strength of the passphrase.
The biggest question is the number of bits of entropy needed to protect current data communications. Current information technology security best practices state that 96 bits of entropy should be safe; however, 128 bits might be needed in the future. This all sounds pretty scary if you are using a simple passphrase for your home Wi-Fi router—and you should be scared. As mentioned earlier, the simple passphrases used by most users are susceptible to brute-force offline dictionary attacks. Both the IEEE and the Wi-Fi Alliance recommend a passphrase of 20 characters or more, which would give you at least 62 bits of entropy. The entropy of the passphrase increases significantly if a combination of uppercase and lowercase letters, numbers, and special symbols are used in the passphrase. The entropy of a passphrase also increases with each extra character that is added to the passphrase.
In summary, always use, at a minimum, a 20-character passphrase and mix up the characters for your home Wi-Fi solution. Sadly, most people will use their dog’s name or their telephone number for their passphrase. In that case, the bigger risk is a social engineering attack because the passphrase can be easily guessed. Passphrases were never intended for the enterprise. Enterprise APs usually give you the choice of entering either a passphrase or a 64-character PSK. If, for some reason, static PSK authentication must be used in the enterprise, at the minimum, use a strong 20-character or longer passphrase.
Proprietary PSK
Although the use of passphrases and PSK authentication is intended for use in a home environment, in reality WPA/WPA2-Personal is often still used in the enterprise. For example, even though fast secure roaming (FSR) mechanisms are now possible, many older VoWiFi phones and other handheld devices still do not yet support 802.1X/EAP. As a result, the strongest level of security used with these devices is PSK authentication. Cost issues may also drive a small business to use the simpler WPA/WPA2-Personal solution as opposed to installing and configuring a RADIUS server for 802.1X/EAP.
The biggest problem with using PSK authentication in the enterprise is social engineering. The PSK is the same on all WLAN devices. If end users accidentally give the PSK to a hacker, WLAN security is compromised. If an employee leaves the company, all the devices have to be reconfigured with a new PSK. Because the passphrase or PSK is shared by everyone, a very strict policy should be mandated stating that only the WLAN security administrator knows the passphrase or PSK. That, of course, creates another administrative problem because of the work involved in manually configuring each device.
Several enterprise WLAN vendors have come up with a creative solution to using WPA/WPA2-Personal that solves some of the biggest problems using a single passphrase for WLAN access. Each computing device will have its own unique PSK for the WLAN. Therefore, the MAC address of each STA will be mapped to a unique WPA/WPA2-Personal passphrase. A database of unique PSKs mapped to usernames or client stations must be stored on all access points or on a centralized management server. The individual client stations are then assigned individual PSKs that are created either dynamically or manually. As shown in Figure 6.5, the multiple per-user/per-device PSKs can be tied to a single SSID. The PSKs that are generated can also have an expiration date. Unique time-based PSKs can also be used in a WLAN environment as a replacement for more traditional username/password credentials.
FIGURE 6.5 Per-user/per-device PSK
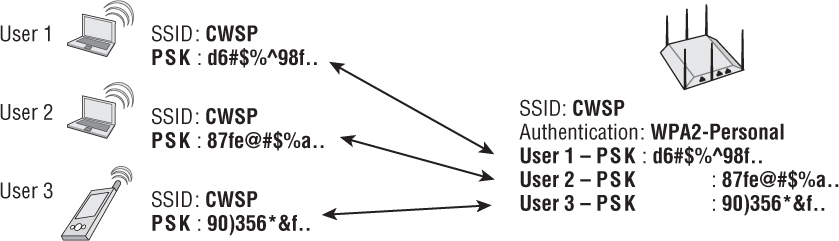
Three WLAN vendors offering proprietary PSK solutions, which provide the capability of unique PSKs for each user or each device, are Aerohive Networks, Ruckus Wireless, and Xirrus. Proprietary PSK solutions provide a way to implement unique per-user/per-device credentials without the burden of deploying a more complex 802.1X/EAP solution. Social engineering and brute-force dictionary attacks are still possible, but they are harder to accomplish if strong and lengthy passphrase credentials are implemented. If a unique PSK is compromised, an administrator only has to revoke the single PSK credential and no longer has to reconfigure all access points and end-user devices.
Some WLAN client devices have limited support for 802.1X/EAP. In situations such as these, proprietary PSK solutions may be of benefit for those classes of devices and a vast improvement over standard static PSK authentication. A proprietary PSK solution offers unique user or device credentials that standard PSK cannot provide. Additionally, proprietary PSK solutions with unique credentials do not require anywhere near the complex configuration needed for 802.1X/EAP. Another advantage of a per-user/per-device implementation of PSK authentication is that every user or device has a unique PMK that is derived from the unique PSK. Keep in mind that these proprietary implementations of per-user/per-device PSK authentication are still susceptible to offline brute-force dictionary attacks. Although the passphrases are unique, they should still be 20 characters or more.
Proprietary implementations of PSK authentication are not meant to be a replacement for 802.1X/EAP. However, multiple use cases for per-user and per-device PSK credentials have gained popularity in the enterprise. Some of these use cases include:
Legacy Devices Supplement to 802.1X/EAP security to provide legacy devices with unique PSK credentials.
Personal Devices Bring your own device (BYOD) security to provide unique PSK credentials for employee personal devices.
Guest Access Provide unique PSK credentials for access to the guest WLAN.
IoT Devices Machines and sensors with 802.11 radios often do not support 802.1X/EAP. Provide Internet of Thing (IoT) devices with unique PSK credentials.
Simultaneous Authentication of Equals (SAE)
The 802.11s amendment was ratified in 2011 with the intention of standardizing mesh networking of 802.11 WLANs. The 802.11s amendment is now part of the 802.11-2012 standard. The amendment defined a Hybrid Wireless Mesh Protocol (HWMP) that 802.11 mesh portals and mesh points could use to dynamically determine the best path selection for traffic flow through a meshed WLAN. HWMP and other mechanisms defined by the 802.11s-2011 amendment have not been embraced by WLAN vendors because of competitive reasons. The majority of WLAN vendors do not want their APs to accept mesh communications from a competitor’s APs. As a result, the major WLAN vendors offer proprietary mesh solutions using their own mesh protocols and metrics.
The 802.11s-2011 amendment also defined RSN security methods that could be used by mesh portals and mesh points. An Authenticated Mesh Peering Exchange (AMPE) is used to securely create and exchange pairwise master keys (PMKs). 802.1X/EAP could be one method used to derive a PMK in a mesh environment. This method is not ideal for mesh points because the RADIUS server resides on the wired network. Therefore, the 802.11s-2011 amendment proposed a new peer-to-peer authentication method called Simultaneous Authentication of Equals (SAE). SAE is based on a Dragonfly key exchange. Dragonfly is a patent-free and royalty-free technology that uses a zero-knowledge proof key exchange, which means a user or device must prove knowledge of a password without having to reveal a password.
Although SAE has yet to be implemented for 802.11 mesh networks, the Wi-Fi Alliance views SAE as a more secure replacement for PSK authentication. As you have already learned, PSK authentication is susceptible to brute-force dictionary attacks and is very insecure when weak passphrases are used. With the current implementation of PSK authentication, brute-force dictionary attacks can be circumvented by using very strong passphrases between 20 and 63 characters. Dictionary attacks against strong passphrases could take years before they are successful. However, dictionary attacks are feasible and more easily achieved via the combined resources of distributed cloud computing. The bigger worry is that most users usually only create an 8-character passphrase, which can usually be compromised in several hours or even minutes. The ultimate goal of SAE is to prevent dictionary attacks altogether. As of this writing, the Wi-Fi Alliance has a proposed program of interoperability certification for SAE.
Some of the proposals from the Wi-Fi Alliance regarding an SAE certification program include the following:
WEP and TKIP must not be used for SAE.
For transition purposes, WPA-2 Personal and SAE must be supported simultaneously within the same BSS.
For transition purposes, WPA2-Personal devices and SAE devices should use the same passphrase.
Think of SAE as a more secure PSK authentication method. The goal is to provide the same user experience by still using a passphrase. However, the SAE protocol exchange protects the passphrase from a brute-force dictionary attacks. The passphrase is never sent between 802.11 stations during the SAE exchange.
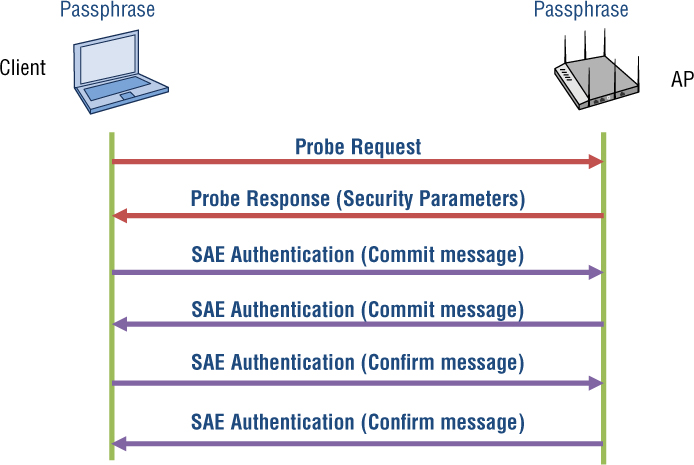
As shown in Figure 6.6, an SAE process consists of a commitment message exchange and a confirmation message exchange. The commitment exchange is used to force each radio to commit to a single guess of the passphrase. The confirmation exchange is used to prove that the password guess was correct. SAE authentication frames are used to perform these exchanges. The passphrase is used in SAE to deterministically compute a secret element in the negotiated group, called a password element, which is then used in the authentication and key exchange protocol.
FIGURE 6.6 SAE authentication exchange
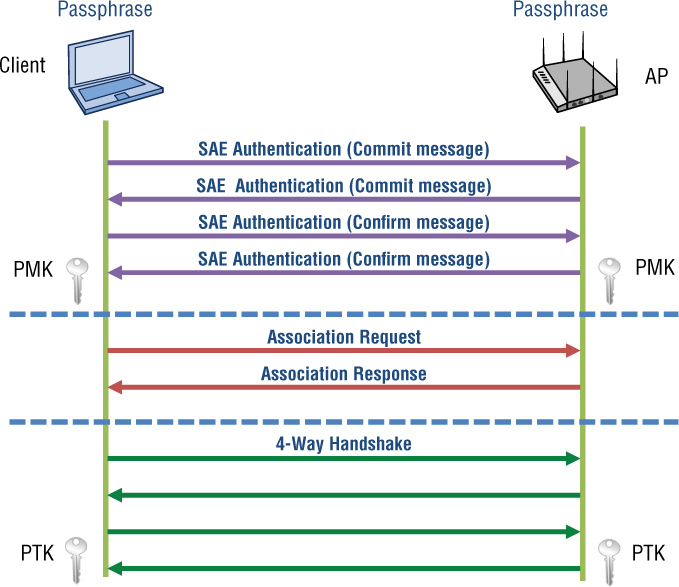
The original intent of the 802.11s amendment was to generate a pairwise master key (PMK) from the SAE exchange, which would then be used to derive a mesh temporal key (MTK) to be used for encrypting unicast traffic between mesh APs. The Wi-Fi Alliance wants to also use an SAE exchange between an AP and client station. As depicted in Figure 6.7, once the SAE exchanges are complete, a unique pairwise master key (PMK) is derived and installed on both the 802.11 AP and the client station. SAE authentication is performed prior to association. Once the PMK is created and the association process completes, the AP and the client can then commence a 4-Way Handshake to create a pairwise transient key (PTK).
FIGURE 6.7 SAE authentication, association, and 4-Way Handshake
What about roaming when using SAE authentication? There are two potential methods:
Option 1 A client station could roam to a new AP with the following sequence of frame exchanges: Probe Request/Response frame exchange, SAE authentication frame exchange, reassociation frame exchange, and then a 4-Way Handshake.
Option 2 A client station can be SAE authenticated to many APs simultaneously by completing the SAE protocol with any number of APs while still being associated to another AP. In other words, a client could perform an SAE commit and confirm exchange with a potential roaming target prior to roaming to the target AP. This creates a PMK on neighboring APs. When the client roams, the PMK is already on the target AP and all the client has to do is a reassociation frame exchange and a 4-Way Handshake when it actually roams. This option would be slightly faster when roaming if the client station was SAE preauthenticated to the AP that is the roaming target.
As previously mentioned, the goal of SAE is to address the previous weaknesses with PSK authentication. Because the SAE exchange allows for only one guess of the passphrase, brute-force offline dictionary attacks are no longer viable. An attacker with a protocol analyzer will not be able to determine the passphrase or the PMK from listening to the SAE exchange. Additionally, the SAE exchange is also resistant to forging and replay attacks. Even if the passphrase is compromised, it could not be used to re-create any previously generated PMKs.
Summary
WPA/WPA2-Personal methods have come a long way from WEP in both end-user configuration convenience and the security they provide. However, the entropy strength of a passphrase still depends on the complexity used in creating the passphrase.
Even though 802.1X/EAP authentication is the recommended solution in the enterprise, static PSK authentication is often deployed in the enterprise despite the security risks. As a result, some WLAN vendors offer per-user/per-device implementations of PSK authentication. In the near future, Simultaneous Authentication of Equals (SAE) may replace PSK authentication as a more secure solution for home and enterprise settings.
Exam Essentials
Explain PSK authentication. PSK authentication is meant to be used in SOHO environments because the stronger enterprise 802.1X/EAP authentication solutions are not available. PSK authentication is also known by the more common name of WPA-Personal or WPA2-Personal.
Define entropy and how it relates to PSK authentication. Passwords or passphrases by themselves have an entropy value of zero. Entropy is a measure of uncertainty associated with a random variable. The method you use to select a passphrase can be measured in terms of randomness.
Understand passphrase-to-PSK mapping. Explain how the passphrase-to-PSK formula uses a hash algorithm to mix the SSID with the passphrase. Understand the security weaknesses associated with this method.
Explain the advantages of proprietary PSK solutions. Proprietary PSK solutions prevent social engineering and employee sharing of a passphrase. Proprietary PSK solutions greatly limit the ability of malicious users to decrypt user traffic and simplify administration.
Review Questions
1. What can happen when a hacker compromises the preshared key used during PSK authentication? (Choose all that apply.)
A. Decryption
B. Spoofing
C. Encryption cracking
D. Access to network resources
E. Denial of service
2. When configuring an 802.11 client station for WPA2-Personal, what security credentials can be used? (Choose all that apply.)
A. Server-side certificate
B. 64 hex-character PSK
C. 8-63 character PSK
D. Token card
E. Client-side certificate
F. 64-character passphrase
G. 8-to-63 character passphrase
3. What inputs are used by passphrase-PSK mapping to create a final 256-bit PSK during 802.11 PSK authentication? (Choose all that apply.)
A. BSSID
B. SNonce
C. SSID
D. Client MAC address
E. AP MAC address
F. Passphrase
G. ANonce
4. Tammy, the WLAN security engineer, has recommended to management that WPA-Personal security not be deployed within the ACME Company’s WLAN. What are some of the reasons for Tammy’s recommendation? (Choose all that apply.)
A. Static passphrases and PSKs are susceptible to social engineering attacks.
B. WPA-Personal is susceptible to brute-force dictionary attacks, but WPA-Personal is not at risk.
C. WPA-Personal uses static encryption keys.
D. WPA-Personal uses weaker TKIP encryption.
E. 802.11 data frames can be decrypted if the passphrase is compromised.
5. When considering the 4-Way Handshake that is used to create dynamic encryption keys, what is the main difference between 802.1X/EAP and PSK authentication? (Choose all that apply.)
A. 802.1X/EAP supplicants all use the same PMK.
B. Clients that use PSK authentication all use the same PTK.
C. 802.1X/EAP supplicants all use a different PMK.
D. Clients that use PSK authentication all use a different PTK.
E. 802.1X/EAP supplicants all use a different PTK.
F. Clients that use PSK authentication all use the same PMK.
6. What is the Wi-Fi Alliance recommendation for the number of characters used in a passphrase for WPA/WPA2-Personal security?
A. 6 characters
B. 8 characters
C. 10 characters
D. 12 characters
E. 20 characters
7. Don has been hired as a consultant to secure the Maxwell Corporation’s WLAN infrastructure. Management has asked him to choose a WLAN authentication solution that will best protect the company’s branch offices from unauthorized users. The branch offices will use older VoWiFi phones that do not support opportunistic key caching (OKC) or fast BSS transition (FT). The company is also looking for the strongest dynamic encryption solution for data privacy reasons. Management is also looking for the cheapest solution as well as a solution that is easy to administer. Which of these WLAN security solutions meets all the objectives required by management? (Choose the best two answers.)
A. WPA-Personal
B. WPA2-Personal
C. WPA-Enterprise
D. WPA2-Enterprise
E. Proprietary PSK
8. When considering the 4-Way Handshake that is used to create dynamic encryption keys, what can be said about both 802.1X/EAP authentication and proprietary per-user/perdevice implementation of PSK authentication? (Choose all that apply.)
A. 802.1X/EAP supplicants all use the same PMK.
B. Clients that use per-user/per-device PSK authentication all use the same PMK.
C. 802.1X/EAP supplicants all use a different PMK.
D. Clients that use per-user/per-device PSK authentication all use a different PMK.
E. Clients that use per-user/per-device PSK authentication all use the same PTK.
9. The IEEE 802.11-2012 standard requires an authentication and key management protocol (AKMP) that can be either a preshared (PSK) or an EAP protocol used during 802.1X/EAP authentication. What is another name for PSK authentication? (Choose all that apply.)
A. Wi-Fi Protected Setup
B. WPA/WPA2-Personal
C. WPA/WPA2-PSK
D. WPA/WPA2-Preshared Key
E. WPA/WPA2-Passphrase
10. Which of these terms best describes a measure of uncertainty associated with a random variable?
A. Entropy
B. Encryption
C. Encapsulation
D. Encoding
11. After viewing the image shown here, identify the type of WLAN security method being used.
A. EAP-TLS
B. CCMP/AES
C. Dynamic PSK
D. EAP-TTLS
E. None of the above
12. Which of these passphrases is the least susceptible to a brute-force offline dictionary attack?
A. 20-character passphrase using numerical digits (0–9)
B. 20-character passphrase using single-case letters (a–z)
C. 20-character passphrase using single-case letters and digits (a–z, 0–9)
D. 20-character passphrase using mixed-case letters and digits (a–z, A–Z, 0–9)
13. Based on the IEEE’s estimation of entropy strength for each character used in the average WPA2 passphrase, how many entropy bits of security would be in an 8-character passphrase?
A. 8 bits
B. 12 bits
C. 20 bits
D. 32 bits
E. 64 bits
14. Which of these security methods is being considered by the Wi-Fi Alliance as a replacement for PSK authentication?
A. Per-user/per-device PSK
B. Wi-Fi Protected Setup (WPS)
C. Simultaneous Authentication of Equals (SAE)
D. EAP-PSK
E. WPA2 Personal
15. What are some of the advantages of using SAE authentication over PSK authentication? (Choose all that apply.)
A. Protects against brute-force dictionary attacks.
B. Protects against forgery and replay attacks.
C. Protects against rogue APs and clients.
D. PMKs cannot be compromised or regenerated.
E. PMKs are no longer needed.
16. After viewing the image shown here, what type of credentials can be strengthened with the software application that is depicted? (Choose all that apply.)
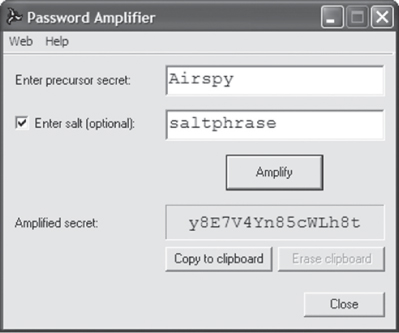
A. Passwords
B. Shared secrets
C. Passphrases
D. Pairwise master keys
E. Pairwise transient keys
F. Group temporal keys
17. The ACME Company is using WPA2-Personal to secure handheld barcode scanners that are not capable of 802.1X/EAP authentication. Because an employee was recently fired, all the barcode scanners and APs had to be reconfigured with a new static 64-bit PSK. What type of WLAN security solution may have avoided this administrative headache?
A. MAC filter
B. Hidden SSID
C. Change the default settings
D. Proprietary PSK
18. If an 802.1X/EAP solution is not available in the enterprise, which of these security credentials should be used instead?
A. MAC filter
B. WPA passphrase with at least 62 bits of entropy
C. WPA2 passphrase with at least 62 bits of entropy
D. Static WEP key
19. Which of these Wi-Fi Alliance security certifications specify mechanisms not defined by the IEEE-2012 standard?
A. WPA-Personal
B. WPA-Enterprise
C. WPA2-Personal
D. WPA2-Enterprise
E. Wi-Fi Protected Setup
20. Which one of these use cases for a per-user/per-device implementation of PSK authentication is not recommended?
A. Unique credentials for BYOD devices
B. Unique credentials for IoT devices
C. Unique credentials for guest WLAN access
D. Unique credentials for legacy enterprise devices without 802.1X/EAP support
E. Unique credentials for enterprise devices with 802.1X/EAP support
