Part I: Code and Cryptogram Strategies
36
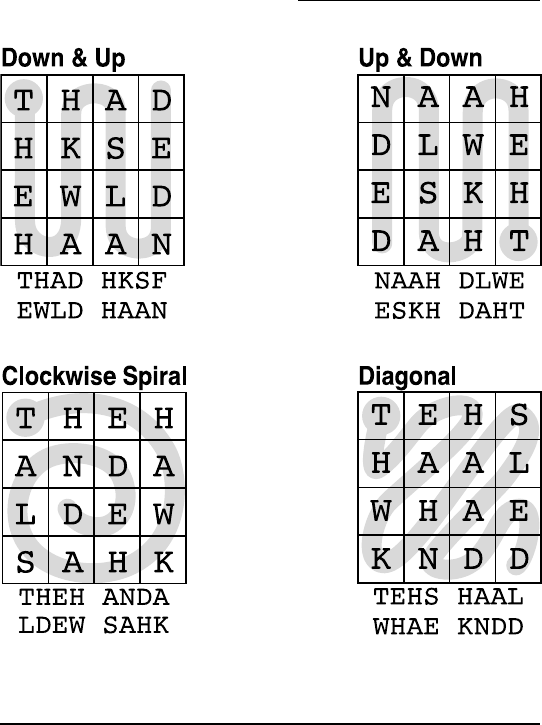
Figure 2-11: Some Twisted Path Ciphers, all encrypting the 16-letter
message THE HAWK HAS LANDED.
In Chapters 11 and 13, we present a few of this type of letter-
marking code, in which tiny dots are added to mark the letters.
Detect the dots and write down the letters to reveal all!
Anagrams and other cryptic riddles
Anagrams, cryptic clues, and riddles have been around as long
as cryptology. Each is a great way of hiding a few words. People
even use anagrams of their names to create new personas and
pseudonyms. In Chapter 12, we present you with a delectable
assortment to try. And who knows, maybe you’ll venture into
the world of cryptic crosswords and enjoy it!
Chapter 2: Simplifying Codes and Cryptograms
37
Anagrams
Anagrams simply rearrange the letters of a word, or words, to
create new words. Short words are generally easy to decipher
(TEACH = CHEAT), but long anagrams can be challenging to
figure out because of the many possible solutions. THE MORSE
CODE turns very nicely into HERE COME DOTS, but it could
also be SMOOTH DECREE, or one of several hundred other
combinations.
Some of the anagrams in this book are just jumbled collec-
tions of letters, and others spell out new words — we know
you can spot which is which!
When you’re faced with an unruly collection of letters, try
some of the following tricks to help you tame them:
✓ Write the anagram backward or in a circle. The idea is to
mix up the letters even more to help break up the strong
patterns you’re seeing in the starting words.
✓ Divide the letters into vowels and consonants. This tip is
particularly helpful for long anagrams.
✓ Write the scrambled letters in alphabetical order.
✓ Look for common patterns that you can make with the
group of letters you have: SH, CH, TH, HE, AN, RE, IE, LL,
EE, and so on.
In this book, we make sure that the message’s letter count
pattern is given in the anagram. So if the words in the final
message are PICK UP ANDREWS AT TWO, the anagram has
the numbers (4, 2, 7, 2, 3) at the end.
Cryptic Clues
We include a few of the simpler varieties of Cryptic Clues in
this book. For a more complete discussion of these tricky puz-
zles, coauthor Denise recommends Cryptic Crosswords & How
to Solve Them by Fred Piscop (Sterling) and Solving Cryptic
Crosswords by B. J. Holmes (A & C Black).
The basic construction of any cryptic clue is that it must
contain the base clue (which is a straight definition for the
answer, like a regular crossword clue) as well as some sort of
word play. The base clue almost always occurs either at the
start or end of the clue (not in the middle).

Part I: Code and Cryptogram Strategies
38
A well-constructed cryptic clue is self-checking — when you
get it, you get confirmation and a wonderful “ah-ha!” moment.
Anagrams
Anagrams are a popular feature in cryptic clues. The letters
from a word in the clue are jumbled up to reveal the answer.
Here’s an example:
Confused tale for a duck (4)
In this clue, confused is an anagram indicator. It tells you that
some letters in the clue need to be “confused” or muddled up
to find the answer. You’ll come across tons of anagram indica-
tors, but some of the main ones include the following:
✓ Agitated
✓ Badly
✓ Broken
✓ Confused
✓ Cooked
✓ Damaged
✓ In pieces
✓ Mangled
✓ Mistaken
✓ Muddled
✓ Shaken
✓ Silly
✓ Stirred
✓ Twisted
✓ Unruly
✓ Upset
The letter count is also very helpful. You can see that the
answer to this clue has four letters. Generally, this means you
can search through the clue for a four-letter word (or a few
words that exactly add up to four letters) that can be jumbled
to give the answer.

Chapter 2: Simplifying Codes and Cryptograms
39
This example includes a few options: TALE, FOR + A, and DUCK.
Jumbling the letters of DUCK doesn’t bring any joy, nor does
FOR with A. TALE, however, can be rearranged to TEAL —
which is a type of duck.
The clue can be read as the following instruction: “If you mix
up the letters from the word TALE, you get the name of a
duck, which has four letters.”
Double Definitions
Double Definition clues may look very confusing, but they’re
simply two definitions for the same word, strung together.
Here’s an example:
Gaze at the timepiece (5)
These clues become clearer if you mentally add a comma
between the two definitions:
Gaze at, the timepiece (5) = WATCH
Hidden Words
Hidden Words are words that are literally hidden within a
clue. Here’s an example:
Wasps almost carry a sacred song (5)
The word carry is an indicator, giving you a hint to what sort of
cryptic clue this is. Hidden Word clues are indicated by words
like carry, hold, hidden, part of, in, found in, and so on. In this
case, carry means the answer is carried within the letters of
Wasps almost.
Wasps almost carry a sacred song (5) = PSALM
Here’s another one to try:
Glimpse a gleaming hidden raptor (5)
With Hidden Word clues, you know the number of letters (five
in this case), so you can simply move through the sequence
of letters in the clue, looking for the group of five consecutive
letters that spell out the answer. Did you find it? Of course
you did. EAGLE.

Part I: Code and Cryptogram Strategies
40
Double Level Puzzles
The Double Level Puzzles in Chapter 13 are the hardest in
the book, and each puzzle consists of two ciphers. The first
cipher produces a keyword. Then you use this keyword to
unlock the second cipher. Each puzzle in this chapter has
individual instructions with it because each has some
particular quirks.
Keywords
The keywords in Double Level Puzzles are used in different
ways. They may reveal which path to take in a Twisted Path
Box Cipher, or how many rails to use in a Rail Fence Cipher.
Sometimes a keyword can encode a number sequence (as in a
Columnar Transposition Cipher, which we feature in Chapter
13). All you need to do is find the alphabetical order of the
letters in your keyword, and then use that order to generate a
number sequence.
For example, if the keyword is BRAZIL, it equates to 251634.
A comes first in this set of letters alphabetically, B is second,
I comes next in the alphabet, so it’s third. L and R come next,
and finally Z is in sixth place. The alphabetical position of each
letter is written above the word; see Figure 2-12 for an example.
Figure 2-12: The keyword and its numerical counterpart.
You then use this sequence (251634) to put columns of
encrypted text in the correct order. (Read on to discover
everything else you need to know to solve Columnar
Transposition Ciphers!)
Columnar Transposition Ciphers
It’s rumored that a Columnar Transportation Cipher is fea-
tured on the Krytpos sculpture by James Sanborn, which
stands in front of the CIA headquarters in Langley, Virginia.
These ciphers are similar to box ciphers, but they’re much
more complicated transposition ciphers because the columns
of letters are mixed up!
..................Content has been hidden....................
You can't read the all page of ebook, please click here login for view all page.
