Chapter 2: Simplifying Codes and Cryptograms
41
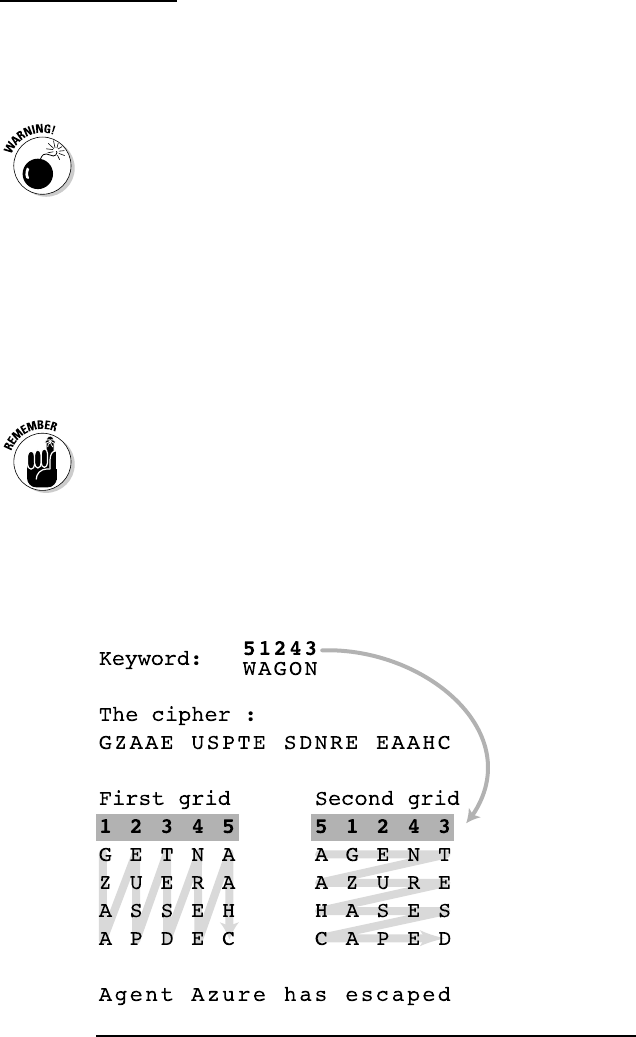
You need to know the order of the columns in order to crack
these ciphers. This is where a keyword comes in, with the
alphabetic rank of its letters determining the number sequence
(see the previous section on keywords for more info).
Don’t include any repeated letters in your keyword.
The alphabetic order of the letters in the keyword determines
the order of the columns in the cipher, and the number of
columns too. In the example here, WAGON gives you five col-
umns, one for each letter, and a number sequence of 51243.
Count the number of letters in the cipher, and divide that
count by the number of keyword letters to get the number
of rows. In the example in Figure 2-13, there are 20 letters,
divided by 5 (the number of letters in WAGON), which gives
you 4 rows of letters.
Null letters, like X, J, Z, and Q, often fill any spaces left at the
bottom of the grid.
Now you’re ready to start writing the cipher in columns. Number
the columns in order (1, 2, 3, 4, 5 in this example), and write
the letters of the cipher down the columns, one after the other.
Follow the path of the arrow for the first grid in Figure 2-13.
Figure 2-13: A short Columnar Transposition Cipher.

Part I: Code and Cryptogram Strategies
42
If you’re right-handed, write this first grid of the cipher letters
on the left side of your paper. If you’re left-handed, write this
first grid of the cipher on the right side of your paper. Trust
us, it makes it easier.
Now, you’ve done all this work — and the message still
doesn’t make sense! But don’t give up — you’re very close
now. Here’s where the keyword comes into its own.
Draw a second grid with the same number of columns, and
this time write the keyword’s number sequence above the
columns. That sequence was 51243 in our example.
Now transcribe the columns from your first grid into the
second grid, writing them in the order dictated by the key-
word. So the first column, numbered 1 from the first grid gets
put into the column numbered 1 in the second grid, which
happens to be in the second position in this instance.
You can now read the message, starting at the top left corner,
reading across the rows (following the path of the arrow on
the second grid in Figure 2-13). You just need to add spaces
between the words, but you’ve come this far, so that part
will be a cinch! Ignore any null letters that were added to the
end of the message (unless they’re a special code from your
partner in crime, too!).
Looking at Letter Frequency
Analysis
Letter frequency analysis is the way to crack substitution
ciphers. It means pretty much what it says: You break down
a cipher into its components and analyze how often each
one occurs. With an understanding of the letter frequencies
that occur in English, you can get a handle on cracking the
cipher.
When you use letter frequency analysis to crack a code, you
simply count how many times each symbol appears in a
section of encoded text. If it’s English, you can be fairly

Chapter 2: Simplifying Codes and Cryptograms
43
certain that the four most commonly occurring symbols will
be E, T, O, and A. E is almost always the most frequently used
letter.
We can’t give you a definitive list of the frequency of letters
in English (or any language) because it changes depending on
which texts have been analyzed. We chose one for you, but
if you’re interested in finding out more, check online or in a
cryptography book.
Letter frequency lists read from left to right, from the most
frequently used letters to the least.
We broke this list into five letter groups (and six at the end)
just to make it a bit easier for you to read.
ETAON RISHD LFCMU GYPWB VKXJQZ
Short ciphertexts with fewer than 100 characters may not
fit well with the standard letter-frequency patterns. The
frequencies can still help you make educated guesses, though.
And ciphers of less than 20 letters may have more than one
solution!
Letter and word patterns
If you keep the following pointers in mind, you’ll be well on
your way to becoming an expert cryptographer!
✓ The 12 most common letters at the beginning of words in
English are TAI SOW CMB PHD.
This doesn’t mean that more words in the dictionary
start with T than all the others. Instead, it refers to how
often words starting with T are seen in a piece of writing.
The prize position of T is linked to how often words like
THE, THAT, THIS, THAN, THERE, and so on are used in
writing.
✓ The 12 most common ending letters in English are EST
NDR YOL AFG.
✓ Q is always followed by U.

Part I: Code and Cryptogram Strategies
44
✓ If you have a vowel, the consonant that most often fol-
lows it is N: AN, EN, IN, ON, UN — they’re all popular!
✓ The most common three-letter words in English are AND
and THE (see, each appears twice in this sentence!).
✓ The most common four-letter word in English is THAT.
✓ The most frequently seen double letters in English are
LL, followed by EE, SS, OO, TT, FF, RR, NN, PP, and CC.
✓ Two-letter words always have at least one vowel, and are
almost always one consonant and one vowel.
✓ Letters that appear fairly evenly throughout a ciphertext
are more likely to be vowels.
✓ Forty percent of any English message is vowels, give or
take just 1 percent either way.
✓ Letters that appear less often and are linked with a few
repeating characters are more likely to be consonants.
For example, K appears after C, L, N, R, and S, and the
vowels, but rarely with other letters.
If you’re interested in discovering a bigger list of letter fre-
quencies, common letter patterns, and further discussion on
this fascinating topic, check out Word Searches For Dummies
by Denise Sutherland (Wiley).
Pattern words
Pattern words are a crucial part of cracking any cipher.
They’re simply any word that has repeated letters in it (not
just double letters, although those are good, too). The pattern
these repeated letters create makes it possible to hunt for the
words in an encrypted text.
THAT is the most common pattern word. Any cipher word
that’s in the pattern 1 - - 1 is almost definitely THAT (see, the
T appears twice).
Check out dictionaries of pattern words (The Cryptogram
Dictionary by Lloyd MacCallum is one you may like). These
useful books can tell you all the words that fit the 1 2 2 1 -
pattern, for example (ASSAY, DEEDS, KOOKY, TEETH, and
TOOTH, just in case you were wondering). The numbers rep-
resent the repeating letters.

Chapter 2: Simplifying Codes and Cryptograms
45
With practice you’ll pick up some of the more common pat-
tern words, like PEOPLE (1 2 - 1 - 2), SELLS (1 - 2 2 1), ELEVEN
(1 - 1 - 1 -), and ILLEGALLY (- 1 1 - - - 1 1 -).
Adding some space
In particularly difficult ciphertexts, the spaces between words
are removed. Would we be that mean? Yes, yes we would . . .
but we also give you a clever trick to help you crack this par-
ticular problem.
The letter H often occurs before E (THE, THEN, THERE, THEY,
and so on) but very rarely after E.
Start by using a letter frequency analysis of your ciphertext to
pinpoint the code letter for E (it’s probably the most common
letter).
Then look at the ciphertext for which letters appear before
and after the encrypted E. The one that almost always appears
before the encrypted E, and not often after it, is probably the
letter H.
Now, as long as the secret message doesn’t talk a lot about
how to behave on behalf of bareheaded racehorses who
somehow have preheated beehives, you’ll be fine.
It’s all Greek to me!
Some ciphers use straight substitutions with established
alphabets, such as Cyrillic, Greek, or Korean. So it’s not writ-
ten in a particular language, and you don’t need a language
class — you just use the symbols and their rough equivalents
in English. In this book we use Greek.
The Greek code letters in this book do not necessarily corre-
spond with their actual English equivalents. We just use them
as cipher symbols.
The world uses many notation systems to communicate:
shorthand, semaphore, Braille, maritime signal flags, Morse
code, and musical notation are just a few examples. In this
book we use Morse code, that darling of the radio waves.
..................Content has been hidden....................
You can't read the all page of ebook, please click here login for view all page.
