Chapter 2. Defining Digital Identity
In 1974, the family therapist Salvador Minuchin declared that “The human experience of identity has two elements: a sense of belonging and a sense of being separate.” This is as good a description of digital identity as it is our psychological identity. A digital identity contains data that uniquely describes a person or thing (called the subject or entity in the language of digital identity) but also contains information about the subject’s relationships to other entities .
To see an example of this, consider the data record, stored somewhere in your state or country’s computers, that represents your car. This record, commonly called a “title,” contains a VIN (vehicle identification number) that uniquely identifies the car to which it belongs. In addition, it contains other attributes of the car such as year, make, model, and color. The title also contains relationships; most notably, the title relates the vehicle to a person who owns it. In many states, the title is also a historical document, because it identifies every owner of the car from the time it was made.
Digital identity management is about creating, managing, using, and eventually destroying records like the one that contains the title for your car. These records might identify a person, a car, a computer, a piece of land, or almost anything else. Sometimes these records are created simply for inventory purposes, but the more interesting ones are created with other purposes in mind: allowing or denying access to a building, authorizing the creation of a file, allowing the transfer of funds, and so on. The relationships between identities and the authorized actions associated with them make digital identities useful, though, at the same time, difficult to manage.
The Language of Digital Identity
The world of digital identity has its own nomenclature. Most of the terms are familiar but are used in specific ways. This section introduces some of that terminology.
A subject or entity is a person, organization, software program, machine, or other thing making a request to access a resource. A resource might be a web page, a piece of data in a database, or even a transaction on a credit card. To gain access to the resource, the subject lays claim to an identity. Throughout this book, we’ll frequently use the word “subject” instead of “person” to remind us that non-human subjects such as machines or programs often use resources.
In this context, identities are collections of data about a subject that represent attributes, preferences , and traits . Attributes are acquired, describing information about a subject such as medical history, past purchasing behavior, bank balance, credit rating, dress size, age, and so on. Preferences represent desires such as preferred seating on an airline, favorite brand of hot dog, use of one encryption standard over another, preferred currency, and so on. Traits are like attributes, features of the subject, but they are inherent rather than acquired. Another way of thinking about the difference between attributes and traits is that the former may change, but traits change slowly, if at all. Examples of traits include blue eyes for a person, or how and where a company was incorporated. Since the distinction between attributes, preferences, and traits rarely makes a difference in the design of an identity infrastructure, we’ll typically use attributes to mean all three unless there’s a specific need to distinguish among them.
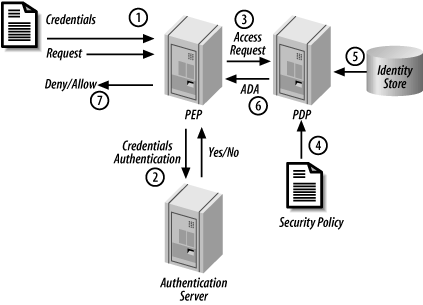
One of the primary purposes of an identity system is to authorize particular actions. This process is shown in Figure 2-1 and is broken down as follows:
To use an identity to justify accessing a resource, a subject must present credentials along with the request. Credentials are proof that a subject has the right to assert that a particular identity belongs to them. Credentials are a way of transferring trust between subjects.
When credentials are presented to a security authority or policy enforcement point (PEP), the authority authenticates the credentials, perhaps using a separate authentication server.
Credentials can be authenticated using many different methods, including a simple username and password, an X.509 certificate, or biometrics . The level of authentication required is usually proportional to the risk that attends accessing the resource.
Once the credentials are authenticated, the authority retrieves the security policy for the resource or passes them to a separate policy decision point (PDP) .
The PDP uses the policy and asserted identity to determine the entitlements and permissions associated with that resource for the asserted identity. Entitlements are the services and resources to which an identity is allowed access. Examples include a credit limit, disk space or bandwidth allocations, and so on. Permissions are the actions that the subject is allowed to perform with respect to the resource, such as withdrawing funds, completing a purchase, or updating a record.
When the PDP transfers this information back to the PEP, it does so in an authorization decision assertion (ADA).
Finally, the PEP either allows or denies the action.
Identity Scenarios in the Physical World
The concepts and words used in the last section can seem intimidating, but in reality, most of these concepts are perfectly understandable given our everyday experience in commercial transactions in the physical world. To see how some of these ideas map to our everyday understanding, let’s consider a common transaction at a convenience store: buying beer.
When a person (i.e., the subject or entity) wants to buy beer (i.e., perform an action on a resource), he is required to submit proof that he is of legal drinking age. The common way to do that is by presenting a driver’s license. A driver’s license is a credential that asserts that a person has certain attributes and traits. The license contains authorization to perform certain tasks, specifically to drive a car. The clerk (i.e., security authority) examines the license to see if it looks real (i.e., determines the validity of the credential) and uses the picture (i.e., embedded biometric device) to see if the person presenting the license is the same person who owns it (i.e., authenticates the credential). Once certain that the license is authentic, the clerk reads the birth date (i.e., an attribute) from the license and determines whether the person is over 21 (i.e., consults a security policy determined by the state and makes a policy decision about permissions associated with the identity for a particular resource).
Now, suppose the person pays with a credit card. The credit card (a separate identity credential) is presented to the clerk. The clerk just saw the driver’s license and so can establish the validity of this credential based on the first. The clerk, acting as the policy enforcement point, runs the card through the point-of-sale terminal, which transmits identity attributes from the card (the cardholder’s name, credit card number, and expiration date) along with the resource to be accessed (credit in the amount necessary to buy the beer) to the bank, which acts as the policy decision point and determines whether or not the subject is entitled to credit in the necessary amount. The clerk receives the credit authorization (authorization decision assertion) and completes the transaction.
In later chapters, we’ll discuss these terms in detail and see how they apply in less-familiar scenarios.
Identity, Security, and Privacy
Digital identity is often thought of as a subtopic of computer or information security. Certainly, digital identity is an important part of security, but digital identity has greater utility than just protecting information. We’ve already discussed how digital identity enables important business relationships. At the same time, information security is about more than simply performing authorization and authentication. Firewalls, for example, provide security but is not necessarily about identity.
Still, the goal of information security is to protect information from unauthorized access, destruction, or alteration. Privacy is the protection of the attributes, preferences, and traits associated with an identity from being disseminated beyond the subject’s needs in any particular transaction. In a circular manner, privacy is built upon a foundation of good information security, which is, in turn, dependent on a good digital identity infrastructure. This relationship is shown in Figure 2-2.
We will discuss privacy in some detail in Chapter 4. Computer security, beyond the concepts that it has in common with identity, is beyond the scope of this book.
Digital Identity Perspectives
We usually speak of identity in the singular, but in fact, subjects have multiple identities. From our point of view, they tend to seem like different facets of our identity, but other entities have a specific view that corresponds to only a subset of those attributes. For example, my bank sees a set of attributes for me that correspond to my credit card numbers, account numbers, credit score, and so on. My employer sees a different subset that overlaps only in a few points such as name, social security number, and the one bank account I give my employer for depositing my paycheck.
My multiple identities are linked by me and little else. They represent different perspectives on who Phil Windley is and what attributes I possess. Most of these attributes are stored in various formats in myriad databases. In the State of Utah alone, there are over 250 different databases in which portions of my digital identity might be stored, depending on my interactions with the State. These multiple identities, or personas, as they are sometimes called, are tied together by a few common data elements that are used, imperfectly, as keys for accessing them: my name, my address, my social security number, and my birthday.
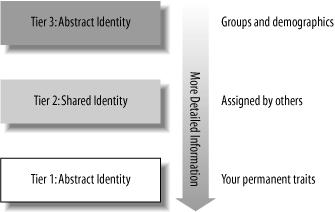
To make sense of all of this, Andre Durand, the founder and CEO of Ping Identity Corp. introduced the concept of “tiers of identity.”[*] Figure 2-3 shows a schematic of these tiers. At the bottom is the first tier, labeled “My Identity.” Tier 1 consists of attributes and traits that are associated with the subject and are both timeless and unconditional. For example, my name is Phillip John Windley, I have blue eyes, and so on.
Tier 2, labeled “Shared Identity,” consists of the attributes that are assigned to us by others. These attributes are shared , because they are used to identify the individual but are temporarily issued based on some kind of relationship. Your wallet is filled with Tier 2 identities; your driver’s license, your employee badge, your credit card, your health insurance card, and your library card are all examples of identity information that is assigned to you. Once the relationship that defines the identity is terminated, the attributes associated with it are no longer useful.
The topmost layer, labeled “Abstracted Identity” establishes the identity of groups. For example, I may be identified as a “Utahn,” a “white male over 40,” or as a member of any number of other demographic groups. Companies may classify me as a “frequent flier” or a “first time customer.” All of these groupings identify me in some way, but only abstractly. Tier 3 is largely about marketing.
Tier 2 identity relationships usually happen with our consent and are mostly welcome because of the benefit we perceive. Tier 3 relationships are usually forced on us and most people resent them. For example, unsolicited commercial email (usually called “spam”) is a Tier 3 identity issue. Telephone solicitations and even TV advertisements are Tier 3 identity issues as well. The problem with Tier 3 identity is that it is inaccurate and nonspecific. Consequently, Tier 3 identities rarely meet a real need. The benefit is so small as to be inconsequential, so most people perceive Tier 3-based relationships as bothersome.
Identity Powershifts
How your employees and customers perceive your efforts to build a digital identity infrastructure depends in part on being cognizant of people’s inherent dislike of what we can now classify as Tier 3 relationships and sensitive to their desire that you give them real value in any Tier 2 relationships. The identity problems and potential faced by organizations—the very subject of this book—happen in Tier 2.
For the most part, Tier 2 relationships are dictated on the terms of the business or organization and consented to by the individual. This one-way relationship is likely to change over time as service-oriented businesses become more sophisticated. This powershift is brought on by increased service standards and improved systems that make it easier for customers to switch their allegiances. Also, businesses are beginning to offer more customized services, making it more likely that customers will begin to dictate some of the terms in their relationships. It will no longer be a “take-it-or-leave-it” world, but a world based on what some have called “mass customization.”
One of the fallouts from this powershift is identity aggregation . As we’ve noted, individuals mentally aggregate their Tier 2 relationships much more than is possible in the real world. I don’t tend to think of myself as a Key Bank customer; I think of myself in holistic terms, with Key Bank being just one of many relationships that I am party to. Federation and other means of aggregating identity, which we’ll discuss in Chapter 12, are one answer to the identity silos created by the multiple Tier 2 relationships. I have completely separate relationships with my airline and my rental car company, and that creates extra work for me each time I travel. Getting back to value, I’m willing to have those identities aggregated if it makes booking travel more convenient.
Another fallout from this powershift is the convergence of Tier 3 and Tier 2 identities. As sophisticated identity systems allow companies to better identify individual customers and businesses adapt by providing more fine-grained service customization, the need to market to broad demographic groups is lessened. I’m not about to predict the disappearance of spam anytime soon, but it and other mass-market approaches are becoming less and less effective. Good businesses will recognize this shift and move their operations away from broadcast and mass marketing and towards more individual-specific marketing efforts.
Conclusion
I believe that over the next decade we will see brand new mechanisms spring up by which customers can telegraph their desires to businesses, and businesses will find new ways to meet those demands. As an example, not too long ago, I was at a conference and got an email from Doc Searls asking if anyone had a spare power adapter for a Powerbook. He’d forgotten his at home. This simple act was Doc signaling a need to the group he knew was at the conference and used Macs. Later that day, we discussed how it would be nice for Doc to be able to let local businesses know of his need as well, so that they could offer to solve his problem—for a fee, of course. At present, the only way to do this would be for Doc to actually look up local businesses and contact them one at a time. That needn’t be the case in a world with good networks and better identity infrastructures. Doc calls this “demand informing supply.” I like to think of it as the spontaneous fulfillment of desire.
Regardless of what you call it, business is more than just transactions. Business is about relationships—relationships with customers, employees, suppliers, and partners. These relationships—especially those with customers—have tended to be one-way and very impersonal. Digital identity changes that, and just in time, because customers are demanding better and more customized service wherever they happen to be and exactly when they want it.
[*] Durand, Andre. “Three Tiers of Identity.” Digital ID World located at http://www.digitalidworld.com/modules.php?op=modload&name=News&file=article&sid=26.