CHAPTER 14. Dial-Up Connections
SOME OF THE MAIN TOPICS IN THIS CHAPTER ARE
The Point-to-Point Protocol and the Serial Line Internet Protocol 229
The Serial Line Internet Protocol (SLIP) 230
The Point-to-Point Protocol (PPP) 231
Configuring a Windows XP Professional Client for Dial-Up 236
When Dial-Up Isn’t Fast Enough 238
If you operate a large corporate network, you might be tempted to skip this chapter. After all, you probably have one or more routers/firewalls and other devices connecting your corporate network to the Internet using a large dedicated data pipe, such as a T1, a T3, an ATM (Asynchronous Transfer Mode), a Frame Relay, or a MPLS (Multi Protocol Label Switching) and/or a SONET connection. However, if you have workers on the move, or employees who work from home, one of the cheapest options available is dial-up. It might be your only option at times. By using a dial-up modem you can connect to the Internet and begin to work immediately using pre-existing copper telephone lines. Obviously, if you can use one of the various flavors of broadband connection, which are discussed in following chapters, that’s the preferred method. But despite the rapid adoption of broadband at home and on the road (hotels and so forth), DSL and cable Internet providers still don’t have nearly the user base of traditional dial-ups. So why are dial-up connections still important in a corporate setting? Keep in mind the following:
![]() As with any new technology, you should always have a backup solution in place in case of failure. Eliminating a single point of failure in your design saves you time and gets the network and/or systems back online faster. What happens if your primary network connection fails? You can use backup solutions to satisfy your business need for the day or two it takes to fix your higher bandwidth connection.
As with any new technology, you should always have a backup solution in place in case of failure. Eliminating a single point of failure in your design saves you time and gets the network and/or systems back online faster. What happens if your primary network connection fails? You can use backup solutions to satisfy your business need for the day or two it takes to fix your higher bandwidth connection.
![]() You might need to support mobile employees staying overnight at a hotel that only provides dial-up access.
You might need to support mobile employees staying overnight at a hotel that only provides dial-up access.
![]() You might have to support ROBO or SOHO-based users. Many corporate network users utilize resources from home offices. Will any of them still require dial-up to gain access to your network’s resources?
You might have to support ROBO or SOHO-based users. Many corporate network users utilize resources from home offices. Will any of them still require dial-up to gain access to your network’s resources?
![]() For non-corporate users, there will come a time when you indeed need a broadband connection. You don’t want to spend hours downloading a few files from the Internet. At this point in time, however, a simple dial-up connection might satisfy your needs.
For non-corporate users, there will come a time when you indeed need a broadband connection. You don’t want to spend hours downloading a few files from the Internet. At this point in time, however, a simple dial-up connection might satisfy your needs.
Tip
You might need to remotely administer your systems and network infrastructure out of band (OOB). You can do so by connecting a dial-up line to just about any device that supports it and then configure it with authentication. When the main network does go down, you can still access your devices via the dial-up network. This is a common configuration on most networks today.
Just as you can use Virtual Private Networks (VPNs), which are discussed in Chapter 46, “Virtual Private Networks (VPNs) and Tunneling,” to create a secure path through the Internet, you can create VPNs using dial-up techniques and then use a server to process incoming connections. Until the telecoms and Internet service providers have finished wiring their networks for unlimited broadband connections, you might have no choice other than dial-up access.
For these reasons (and more), you should read this chapter to understand just how dial-up protocols, such as PPP, work because there is a good chance that you will be using PPP in the future for encapsulation of your dial-up lines, T1s, and other network systems.
Note
This chapter covers the basics of establishing a typical dial-up connection to the Internet. However, remember that in the case of a dial-up connection, the payload in your network packets is sent out on the Internet, where it is possible for someone to intercept your data. If you are dialing into the Internet instead of a server at your business, read Chapter 47, “Encryption Technology,” so that you can use the latest techniques to keep others from viewing your data.
Tip
By using dial-up, you can connect to an Internet Service Provider (ISP) for Internet access and then you can build a VPN tunnel to the corporate network via a Client VPN device set to terminate your connection and authorize you for access to resources. You can also use any connection to the Internet, but in most cases you will find that you will be using dial-up over traditional copper-based telephone cabling.
The Point-to-Point Protocol and the Serial Line Internet Protocol
Communication on the Internet is based on the TCP/IP suite. TCP/IP is covered in detail in Chapter 24, “Overview of the TCP/IP Protocol Suite”; other services, applications, and tools designed to work with TCP/IP are discussed in Chapters 25, “Basic TCP/IP Services and Applications,” 27, “Troubleshooting Tools for TCP/IP Networks,” and 28, “BOOTP and Dynamic Host Configuration Protocol (DHCP).”
A dial-up connection is a point-to-point link using a phone line. A router or server on the remote network is your connection point to that network using a modem or a bank of modems grouped together. The remote access server at the ISP (or maybe your corporate dial-in modem bank) creates point-to-point connections with dial-in clients. After a point-to-point connection is established, you need a method for sending data across it. Addressing at this point doesn’t necessarily matter because the conversation has only two parties, and they are transparent to the network transport protocol.
The Serial Line Internet Protocol (SLIP) was the first widely adopted protocol, and was initially found mainly on Unix systems. Many operating systems (including Unix, Linux, and Windows) still support SLIP today, although it’s not commonly in use. Although you will find SLIP in use on older Unix-based systems, some systems are either too outdated or are end of life (EOL). Consequently, support on those systems is no longer offered. Because of these facts, you find SLIP in use when working heavily with antiquated Unix-based systems. On the other hand, if you are working with modern network and system infrastructure, it’s a good bet that you will be working with PPP. PPP is more robust and has replaced SLIP in all but the most unique cases.
PPP makes up for many of the shortcomings of SLIP. For example:
![]() PPP offers synchronous as well as asynchronous communications, whereas SLIP offers only synchronous.
PPP offers synchronous as well as asynchronous communications, whereas SLIP offers only synchronous.
![]() PPP includes error correction. SLIP relies on either the error-correction capabilities of the hardware used to make the connection or the error-correction capabilities of TCP/IP.
PPP includes error correction. SLIP relies on either the error-correction capabilities of the hardware used to make the connection or the error-correction capabilities of TCP/IP.
![]() PPP provides for automatic, dynamic address assignment. SLIP must be manually configured prior to dialing or during the initial session setup.
PPP provides for automatic, dynamic address assignment. SLIP must be manually configured prior to dialing or during the initial session setup.
![]() PPP provides for compression. SLIP—for the most part—does not. There are variations of SLIP, such as Compressed SLIP, or CSLIP, that enable compression, but these are uncommon and often proprietary implementations.
PPP provides for compression. SLIP—for the most part—does not. There are variations of SLIP, such as Compressed SLIP, or CSLIP, that enable compression, but these are uncommon and often proprietary implementations.
![]() Multiple protocol stacks can use the same PPP link (such as IP and IPX). Higher layer protocols, such as the network layer’s IP and IPX, are able to traverse the link whereas SLIP is limited to IP only. Things come full circle, though. As more and more standardization is done with TCP/IP and its suite of protocols, you will find that IP is the only protocol you will see and use regardless. Even factoring that in, however, PPP still brings much more to the table than does SLIP.
Multiple protocol stacks can use the same PPP link (such as IP and IPX). Higher layer protocols, such as the network layer’s IP and IPX, are able to traverse the link whereas SLIP is limited to IP only. Things come full circle, though. As more and more standardization is done with TCP/IP and its suite of protocols, you will find that IP is the only protocol you will see and use regardless. Even factoring that in, however, PPP still brings much more to the table than does SLIP.
SLIP and PPP are nonroutable, due to their point-to-point connection. Both SLIP and PPP can encapsulate protocols such as IP, and then pass them on to routers or other devices so the data can reach its intended destination. At the receiving end of a connection, the PPP or SLIP information is stripped off and the protocol (such as IP) that was sent across the serial link (such as a modem) is then transmitted through a network as if it were coming from a computer or another device attached to the network.
Note
Encapsulate is a networking term that means a particular protocol is carrying, in its payload section, another packet generated by a different protocol. SLIP is one of the simplest of the protocols developed for this purpose, using only two characters to successfully transmit other protocols across a point-to-point connection. PPP is more complicated, adding its own protocol header information to the packet (and stripping it off at the other endpoint), to make communications a little more flexible and reliable.
The Serial Line Internet Protocol (SLIP)
For some time, SLIP was a de facto standard in the Unix community as a means for establishing a point-to-point connection between two computers. It was finally documented in RFC 1055, “A Nonstandard for Transmission of IP Datagrams over Serial Lines: SLIP,” in 1988. Yes, you read that right—a nonstandard. Although there are standards for IP, there is no standard for SLIP that concisely defines the protocol. SLIP is a simplified protocol that encapsulates and sends data across a connection.
SLIP has been implemented in many ways, using different packet sizes, but the basic protocol consists of using two special characters:
![]() END—This character (decimal value of 192) is used to delineate the end of a packet.
END—This character (decimal value of 192) is used to delineate the end of a packet.
![]() ESC—Not to be confused with the ASCII character set escape character, the SLIP ESC character (decimal value of 219) is used when a character in a packet is the same as the END character. In such a case, the character is “escaped” by prefixing the ESC character before the character that is the same as the END character. ESC just tells the receiving end that this is not the end of the packet, but an actual data byte in the packet. This is a common method used by many protocols to make it possible to use character sequences that otherwise would violate protocol rules.
ESC—Not to be confused with the ASCII character set escape character, the SLIP ESC character (decimal value of 219) is used when a character in a packet is the same as the END character. In such a case, the character is “escaped” by prefixing the ESC character before the character that is the same as the END character. ESC just tells the receiving end that this is not the end of the packet, but an actual data byte in the packet. This is a common method used by many protocols to make it possible to use character sequences that otherwise would violate protocol rules.
Note
ASCII (American Standard Code for Information Interchange) was the standard method for representing alphanumeric characters in non-IBM systems, from early VT-style terminals to more modern enhanced terminal emulators. IBM used its own character coding scheme, EBCDIC (Extended Binary-Coded Decimal Interchange Code), for its mainframes and some other systems.
More recently, UNICODE has been adopted by systems such as Windows NT/2000/XP/2003, and many other operating systems, including Unix and Linux. UNICODE can be used to represent not just the basic alphanumeric character set used for English, but also more than 34,168 characters, covering about 24 different languages. The coding scheme used by UNICODE is extensible, so in addition to historical and many modern language scripts, UNICODE can be adapted to include lesser-used languages as time goes by.
SLIP is a simple protocol. Just start sending the characters of a packet and send the END character at the end of each packet. Use the ESC character inside the packet if one of the data bytes is the same as the END character so that the receiving end can interpret the byte correctly.
Although it was a good start, several problems can occur when using SLIP:
![]() No maximum packet size is defined, so it depends on the particular implementation. The Berkeley Unix SLIP drivers use a maximum of 1,066 bytes. There might be other ways to configure this setting, however, so make sure you check the system documentation for more information.
No maximum packet size is defined, so it depends on the particular implementation. The Berkeley Unix SLIP drivers use a maximum of 1,066 bytes. There might be other ways to configure this setting, however, so make sure you check the system documentation for more information.
![]() No mechanism is used to configure the address of the sending or receiving end of the connection. Therefore, static addresses must be assigned in advance if the protocol encapsulated by SLIP is to be sent past the receiving computer or router to another host. In other words, before a SLIP connection can be set up, both sides must configure the link for the protocol to be used on the link. Because most dial-up connections today make use of the Dynamic Host Configuration Protocol (DHCP) to conserve the IP address space, SLIP won’t work with an ISP or a dial-up server that uses DHCP.
No mechanism is used to configure the address of the sending or receiving end of the connection. Therefore, static addresses must be assigned in advance if the protocol encapsulated by SLIP is to be sent past the receiving computer or router to another host. In other words, before a SLIP connection can be set up, both sides must configure the link for the protocol to be used on the link. Because most dial-up connections today make use of the Dynamic Host Configuration Protocol (DHCP) to conserve the IP address space, SLIP won’t work with an ISP or a dial-up server that uses DHCP.
![]() SLIP just sends packets across the line. It doesn’t prefix a header to the data like other protocols (such as TCP and IP) do. Thus, SLIP can’t indicate to the receiving end of the connection what type of protocol is being used. Of course, the most common use for connecting to the Internet is TCP/IP, so IP packets generally are assumed for most connections. However, in the early days of SLIP, it often was used to connect one computer to another, and a separate connection was required if both computers used multiple protocols, such as IP, IPX/SPX (Internet Packet Exchange/Sequenced Packet Exchange), or DECnet.
SLIP just sends packets across the line. It doesn’t prefix a header to the data like other protocols (such as TCP and IP) do. Thus, SLIP can’t indicate to the receiving end of the connection what type of protocol is being used. Of course, the most common use for connecting to the Internet is TCP/IP, so IP packets generally are assumed for most connections. However, in the early days of SLIP, it often was used to connect one computer to another, and a separate connection was required if both computers used multiple protocols, such as IP, IPX/SPX (Internet Packet Exchange/Sequenced Packet Exchange), or DECnet.
![]() No provisions are in the protocol for error detection or correction. This is left up to higher-level protocols. Because SLIP was developed for use over slow links, retransmission of packets found to have errors by higher-level protocols is an expensive proposition in terms of bandwidth.
No provisions are in the protocol for error detection or correction. This is left up to higher-level protocols. Because SLIP was developed for use over slow links, retransmission of packets found to have errors by higher-level protocols is an expensive proposition in terms of bandwidth.
![]() SLIP provides no compression algorithm. So over the slow serial lines used for dial-up access, large amounts of the available bandwidth are wasted. For example, for a particular connection, most of the data in an IP header would not change from one packet to the next. Having to resend these unchanged bytes over and over again for each packet just wastes bandwidth.
SLIP provides no compression algorithm. So over the slow serial lines used for dial-up access, large amounts of the available bandwidth are wasted. For example, for a particular connection, most of the data in an IP header would not change from one packet to the next. Having to resend these unchanged bytes over and over again for each packet just wastes bandwidth.
Because SLIP was widely deployed when the Internet became commercially available, it was a common protocol that many people used for an Internet connection early on. Initially, when first released, Microsoft’s desktop offerings (Windows 9x) supported SLIP and that continues today. (Windows Server 2003 supports the SLIP and PPP remote access protocols.)
All that said, you can probably understand why the Point-to-Point Protocol was developed. PPP replaces SLIP and provides a more robust method for sending and receiving data across serial connections, such as when dialing into a corporate modem bank or accessing the Internet.
For more information about SLIP, see RFC 1055, “A Nonstandard for Transmission of IP Datagram’s over Serial Lines: SLIP” and RFC 1144, “Compressing TCP/IP Headers for Low-Speed Serial Links.”
Note
Although Windows XP and Server 2003 do include support for SLIP, keep in mind that newer systems only support outgoing connections. Windows Server 2003 and Microsoft Windows XP do not support SLIP for incoming connections.
The Point-to-Point Protocol (PPP)
Like SLIP, PPP is a means for encapsulating packets from other protocols and transmitting them across a serial (or other point-to-point) link. Unlike SLIP, PPP provides a wide range of features that improve on the simple process of just sending data packets across the wire. PPP is documented in RFC 1662, “The Point-to-Point Protocol (PPP).” The pertinent features that PPP offers are listed here:
![]() High-Level Data Link Control (HDLC)—PPP bases its frame format on the High-Level Data Link Control protocol, which is a standard method used for point-to-point connections. HDLC, developed by the International Organization for Standardization (ISO), is a bit-oriented protocol found on the data link layer of the OSI Model. It has been widely deployed for many reasons, not the least of which is that it’s the default protocol used when configuring most Cisco router interfaces. If you need to encapsulate a T1 for a point-to-point connection, it’s most common to use HDLC or PPP. HDLC (unlike other technologies) can support both half-duplex and full-duplex communication, and point-to-point and multi-point networks, which is very common in today’s use of IPSEC-based VPN tunnels to interconnect offices over the Internet.
High-Level Data Link Control (HDLC)—PPP bases its frame format on the High-Level Data Link Control protocol, which is a standard method used for point-to-point connections. HDLC, developed by the International Organization for Standardization (ISO), is a bit-oriented protocol found on the data link layer of the OSI Model. It has been widely deployed for many reasons, not the least of which is that it’s the default protocol used when configuring most Cisco router interfaces. If you need to encapsulate a T1 for a point-to-point connection, it’s most common to use HDLC or PPP. HDLC (unlike other technologies) can support both half-duplex and full-duplex communication, and point-to-point and multi-point networks, which is very common in today’s use of IPSEC-based VPN tunnels to interconnect offices over the Internet.
![]() Link Control Protocol (LCP)—This is an extensible protocol used to establish, configure, and test the data-link connection. Both sides of the link negotiate parameters with the other side that will be used for the connection, such as the maximum packet size.
Link Control Protocol (LCP)—This is an extensible protocol used to establish, configure, and test the data-link connection. Both sides of the link negotiate parameters with the other side that will be used for the connection, such as the maximum packet size.
![]() Network Control Protocols (NCPs)—NCPs allow for different configuration options, depending on the protocol type of the packets being transported across the PPP link. NCPs enable specific network protocol sessions to be negotiated and set up after the link is established. Even better, PPP allows for multiplexing several different protocols (such as IP and IPX) on the same link.
Network Control Protocols (NCPs)—NCPs allow for different configuration options, depending on the protocol type of the packets being transported across the PPP link. NCPs enable specific network protocol sessions to be negotiated and set up after the link is established. Even better, PPP allows for multiplexing several different protocols (such as IP and IPX) on the same link.
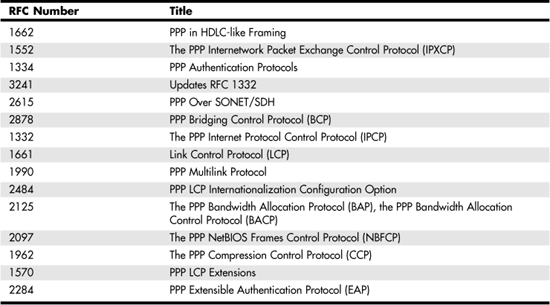
For more information about PPP, extensions, and other specific details, many RFCs are available for you to examine. Table 14.1 lists several RFCs that might be relevant to your situation.
Tip
In Table 14.1 some of the RFCs listed are now standards, whereas others are proposed standards. Yet hardware vendors tend not to wait for a standard to become final before adopting the technology. For more information about RFCs, visit the Web site www.rfc-editor.org.
Table 14.1. RFCs Related to PPP
PPP negotiates a link with a remote system, tests the link, sets up different protocol connections, and then sends your data from one computer to another. Because PPP is used across a point-to-point link instead of a packet-switched network, it can be assumed that packets arrive at the destination in the same order in which they are transmitted. PPP also allows for sending more than one protocol packet type across the same link by multiplexing the various protocols. It also supports full-duplex communications (communications in both directions) on the same link. Additionally, PPP doesn’t just use a special character to indicate the end of a packet (like SLIP does), but instead uses a frame header so that the data packet being transported across the link is fully encapsulated inside the PPP frame.
Figure 14.1 shows the basic layout of a PPP frame.
Figure 14.1. The PPP frame consists of a simple header, the packet being transmitted as payload, and an error-detection field at the end of the frame.
The fields in Figure 14.1 are used in this way:
![]() Flag—This is used to indicate the start of a frame, and it consists of the binary value 01111110.
Flag—This is used to indicate the start of a frame, and it consists of the binary value 01111110.
![]() Address—This field always contains a string of eight 1s, which is interpreted as a broadcast address by many protocols. Because PPP is a point-to-point link, no addressing is required.
Address—This field always contains a string of eight 1s, which is interpreted as a broadcast address by many protocols. Because PPP is a point-to-point link, no addressing is required.
![]() Control—This always contains the binary value 00000011. It is used in HDLC to indicate that this is an unsequenced information (UI) frame. PPP provides a connectionless service.
Control—This always contains the binary value 00000011. It is used in HDLC to indicate that this is an unsequenced information (UI) frame. PPP provides a connectionless service.
![]() Protocol ID—This 2-byte field is used to identify the protocol that is being transmitted inside the payload section of the PPP frame. Protocol ID numbers are assigned by Internet Corporation for Assigned Names and Numbers (ICANN). You can visit its Web site to learn more about protocol number assignment at
Protocol ID—This 2-byte field is used to identify the protocol that is being transmitted inside the payload section of the PPP frame. Protocol ID numbers are assigned by Internet Corporation for Assigned Names and Numbers (ICANN). You can visit its Web site to learn more about protocol number assignment at www.icann.org. You can also find information on Protocol IDs by visiting the Internet Assigned Numbers Authority (IANA) at www.iana.org. An example of PPP can be found by visiting www.iana.org/assignments/ppp-numbers.
![]() Frame Check Sequence (FCS)—This field can vary from 2 to 4 bytes in length, depending on the implementation. This provides the capability to store a 16- to 32-bit checksum calculation to ensure the integrity of the frame. This value is calculated by the sender based on the contents of the entire frame. The receiving end of the frame performs the same calculation. If the value does not match that stored in the FCS field, the packet is discarded.
Frame Check Sequence (FCS)—This field can vary from 2 to 4 bytes in length, depending on the implementation. This provides the capability to store a 16- to 32-bit checksum calculation to ensure the integrity of the frame. This value is calculated by the sender based on the contents of the entire frame. The receiving end of the frame performs the same calculation. If the value does not match that stored in the FCS field, the packet is discarded.
The payload section of the PPP frame carries the packet of another protocol, as indicated by the Protocol ID field. The standard maximum length of a PPP frame, called the maximum receive unit (MRU), is defined in the standard as 1,500 bytes in length (which can accommodate a standard IP packet). However, this value can be increased or decreased during the original link negotiations.
Establishing a Link: The Link Control Protocol (LCP)
The process in which a PPP link is established is an orderly process. Each end of the connection first sends LCP frames that are used to test the data link and to configure the parameters that will be used on the link. Next, NCP packets are sent to configure any required options for the protocol(s) that will be encapsulated and sent across the link. After this, the data exchange can begin. When the link is no longer needed, LCP or NCP packets can be used to close the link. Alternatively, an external event, such as a timer, can be used to close an idle link. If you’ve ever been disconnected from a dial-up link to an ISP, you understand this process!
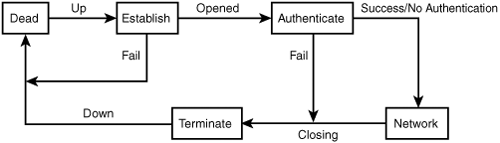
Figure 14.2 shows an example of the phases that a PPP link goes through for establishing and terminating a link.
Figure 14.2. The PPP link must be established before data transfer occurs and terminated when communications are finished.
The steps here are simple:
1. In the beginning, the link is “dead.” No communications exist between the two nodes. Note that when an active link is closed, it is then returned to a “dead” state.
2. When some event (such as a modem dialing into a remote access server) occurs, LCP takes over to negotiate the link. When this task has finished successfully, the PPP link is in the Establish phase. The link is then Up. If the two endpoints of the communication cannot agree on a link, the attempt fails and, as you can see in the diagram, the PPP link is considered again to be in the Dead state.
3. If LCP is able to exchange configuration packets that both sides can agree on, the link is in the Opened state and, if required by the link, an Authenticate state must be reached. This can be done using various methods, which are specified during the link establishment phase. If the authentication method fails, the link proceeds to the Closing state. If it succeeds, or if no authentication is required, then the Network phase is reached.
4. During the Network phase, NCP is used to configure one or more network protocols that will use the link. Remember that PPP can multiplex several protocols across the same link. After this is done, communication takes place using the protocols that are configured. Note that any network protocol can terminate its usage of the link at any time without causing the termination of the actual PPP link.
5. A link can be terminated due to an external event, such as the loss of the carrier signal or because of excessive noise on the line. However, an orderly termination can be done through the exchange of LCP packets. PPP is then considered to be in the Closing state. During the Closing state, PPP signals the network-layer protocols that are using the link so that they can gracefully close their connections.
6. PPP proceeds to the Terminate state, the link is then considered to be Down, and you end up back at the beginning of the model shown in the diagram, where it all started. The PPP link is dead.
LCP is used by both ends of the connection to negotiate the encapsulation options and packet size and then to terminate the link. Each side of the link sends information to the other about the configuration options it supports and which ones it wants to use. A large number of packet types are used by the LCP process to establish, manage, and tear down a link. They can be grouped into three general categories:
![]() Link establishment frames—These frames are used to set up a link and configure the parameters to be used for the link.
Link establishment frames—These frames are used to set up a link and configure the parameters to be used for the link.
![]() Link termination frames—These frames are used to perform an orderly shutdown of the link.
Link termination frames—These frames are used to perform an orderly shutdown of the link.
![]() Link maintenance frames—These frames are used to manage the link and for debugging purposes.
Link maintenance frames—These frames are used to manage the link and for debugging purposes.
An LCP packet can be identified by examining the Protocol ID field of the PPP frame. LCP packets use the protocol ID value of 0xC021. The rest of the LCP frame structure consists of a code that identifies the type of LCP message (one byte) and an identifier field (one byte) that is used to match up requests with replies during the exchange of LCP packets. A length field (2 bytes) is then used to indicate the size of the LCP packet. This is followed by the actual data used for the particular LCP message. The LCP packet rides in the payload section of the PPP frame just like any other protocol.
LCP operates in a request/reply mode in which the LCP Configure-Request packet is first sent to open a link, and contains a list of options that the sender wants to use if they differ from the default values for the option. The Configure-Ack packet type is used for acknowledging that all the received options are acceptable to the other end of the connection.
The Configure-Nack message is used by the receiving end to indicate that it recognizes all the options that were sent, but is rejecting the configuration as a whole because one or more of the option values cannot be used on its side of the connection. This packet also contains a list of the options that are causing the negative acknowledgment along with values it would find okay to use.
The Configure-Reject message is similar to the Configure-Nack but is used when some of the options are not recognized by the receiver or are nonnegotiable. Again, a list of these unrecognized or rejected options is returned in this rejection packet so that the sender can determine what the receiving end is trying to negotiate.
After receiving a Configure-Nack or Configure-Reject message, the sender can send additional Configure-Request packets, changing the values of options so that both sides can come to an agreement. Note that because this is a bidirectional communications path, the options negotiated for traffic going in one direction don’t have to match the options used for traffic going in the opposite direction. Each side sends a Configure-Request to the other side to establish the options it is allowed to use to configure the link for sending to the other side.
After all options in a Configure-Request packet are acceptable to the receiving end, it sends the Configure-Ack message and the link setup is complete. After the link has been established using LCP, NCP packets are used to configure protocol-specific options that will be used on the PPP link.
During the time that the link is maintained, LCP uses maintenance packets for routine procedures to be sure that the link is still up and performing as it should. For example, the Echo-Request packet can be sent to determine whether the link is still operational after some time has passed with no transmissions. The Echo-Reply packet is returned in response to keep the link open.
Other maintenance LCP packets are used to indicate that the protocol the sender wants to negotiate is not supported by the receiver or that the LCP code is not understood by the receiver.
When either side of the connection wants to tear down the link, the Terminate-Request LCP packet is transmitted. The proper response is a Terminate-Ack packet. For a complete listing of LCP packets and their particular formats, see the RFCs listed in Table 15.1.
Network Control Protocols (NCPs)
The most popular protocol stack used with PPP today is TCP/IP. Millions of people each day use TCP/IP to connect to the public Internet. PPP is used to encapsulate the data and pass it to the next point, which allows for the use of multiple NCPs that further configure the protocols that are carried across the PPP link. For example, in the case of IP, the dial-in client must be provided with IP addressing information, which usually is done by a DHCP server.
The Internet Protocol Control Protocol (IPCP) is the NCP used to configure parameters for using the PPP link for transmitting IP packets. The Internetwork Packet Exchange Control Protocol (IPXCP) is used to set up IPX. Other protocols for which there are NCPs include AppleTalk, DECnet Phase IV (oh, the good old days!), and NetBIOS, among others.
The important thing to remember is that the PPP link parameters are negotiated before any actual network protocols are configured or are able to use the link. After the link is established, one or more NCPs use the link to configure the parameters for the protocol that will be carried in the payload section of PPP frames that use the link.
Configuring a Windows XP Professional Client for Dial-Up
You can use a wizard to help configure Dial-Up Networking on a Windows client. The particular dialog boxes displayed vary from one version of Windows to another. This example uses Windows XP Professional to show how to configure a simple dial-up connection to the Internet. You can also set up more complex configurations using the wizard.
First, obtain from your ISP the telephone number that you’ll need, your username and password that will be used to authenticate you on the ISP’s server, and info on whether the ISP uses dynamic addressing (DHCP) or assigns you a static address.
To set up the client software on Windows XP Professional, carry out these steps:
1. Click on Start and select Control Panel and then Network Connections.
2. Under Network Tasks on the left pane on the window, select Create a New Connection. The New Connection Wizard pops up. Click Next to continue.
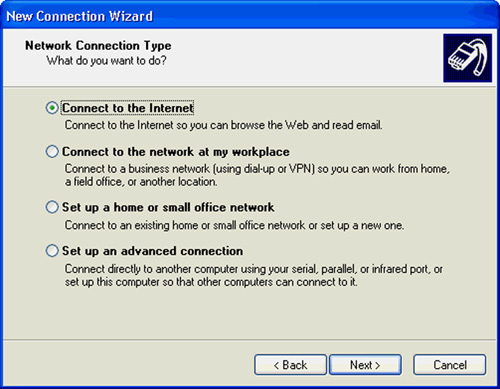
3. The next dialog box the wizard displays gives you the option of selecting the type of connection you want to create. In Figure 14.3, you can see these choices. For the purposes of this example, the radio button Connect to the Internet has been selected. Click Next to continue.
Figure 14.3. Select the type of connection you are creating. In this figure, Connect to the Internet is selected.
4. The next dialog box enables you to choose what kind of connection you want to create. You can choose from a list of ISPs, which will let you select Microsoft’s MSN, or obtain a list of other ISPs. The last selection lets you use a CD from your ISP, such as AOL. For the purposes of this example, the radio button Set Up My Connection Manually has been selected to show the options available.
5. You next choose a type of Internet connection (dial-up broadband service that requires a password, or broadband that is always on). Select the first option, which is to use a dial-up modem connection.
6. You can enter a name for this connection in the next dialog box. This can be useful if you create multiple connections. For example, you might use a broadband connection to connect to your business network. Yet you can still use a dial-up phone-line connection as a backup should the broadband service become unavailable.
7. The Phone Number to Dial dialog box is used for just that purpose—enter the telephone number used to dial into your ISP’s network.
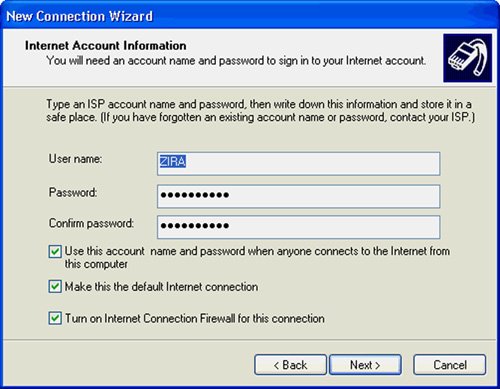
8. Figure 14.4 shows the next dialog box: Internet Account Information. Use this to enter the username and password assigned to you by your ISP. You can also use the other dialog boxes to select other features, such as the Internet Connection Firewall that Windows XP provides.
Figure 14.4. Use this dialog box to enter authentication information given to you by your ISP.
9. The last dialog box lists the choices you made during the connection setup process. In addition, you can choose to add a shortcut to the desktop. Click Finish to exit the wizard.
After you have finished entering the configuration information for the dial-up connection, the Connect dial-up pop-up will appear. You can use this to test the dial-up connection you have just created.
Note
The preceding example showed you how to set up a Windows XP Professional client for a basic dial-up Internet connection. If you’re using Linux at home, it’s recommended that you check the documentation your vendor provides because each distribution of the operating system might have different configuration examples. It’s also a good idea to review any documentation available on the Internet.
When Dial-Up Isn’t Fast Enough
This chapter discussed PPP and SLIP, the two main protocols used by dial-up users to make a connection to the Internet or another network, such as a company network or another WAN. For many users who don’t use a lot of bandwidth, dial-up connections are inexpensive. And for mobile users, a dialup connection is ubiquitous, whereas dedicated solutions—discussed in the next chapter—are not always easily accessed. Because a dial-up connection uses the public switched telephone network (PSTN), there are limits to the amount of information that can be carried across the link using a modem that translates digital signals to analog signals, and then reverses the process at the other end of the connection. Dial-up access should be used when you find that the cost of the service matches the user requirements or when you need a backup connection for when a broadband connection fails. It can also be used for users on the road where hotels offer only dial-up connections.
However, using digital connections it’s possible to get a much faster connection to the Internet or to connect one network to another. In Chapter 15, “Dedicated Connections,” you’ll learn about the methods used for dedicated connections. However, don’t dismiss dial-up networking entirely, even if you are able to obtain a broadband or other fast connection. As slow as it might be, dial-up networking using a modem can serve as a backup when your other, faster connection fails!