Authentication Factors
As described earlier in the chapter, an authentication factor is a way of confirming the identity of the subject. The three primary authentication factors are:
- Something you know—Secret knowledge, such as a password
- Something you have—A token or device
- Something you are—Unique physical characteristics of a person, such as those that can be detected by a retinal or iris scan, fingerprint scan, or voice analysis
Most authentication systems rely solely on the first factor, implemented as a username and password combination. For access to highly sensitive data, you might combine the first two factors, requiring a token just to access the login screen, where the user would enter his or her username and password. The most sensitive data are protected by all three factors. For example, the United States military uses Sensitive Compartmented Information Facilities (SCIFs). Just to walk through the door of a SCIF requires recognition of identifying characteristics such as a retinal or fingerprint scan (the “something you are” factor), swiping an ID badge (the “something you have” factor), and typing in a PIN (the “something you know” factor).
Something You Know
A password is the most common authentication tool. Many people use passwords every day to check email, log into online banking, and use the ATM. The biggest challenge facing administrators of password systems is convincing users to use strong passwords. Users are primarily concerned with convenience. Ideally, you would prefer to have a simple, easy-to-remember password. However, simple passwords or ones based on your name or a dictionary word are also easy for malicious users to guess. An easily guessed password is almost as unsecure as no password at all.
 TIP
TIP
One solution to the password problem is the use of a passphrase, such as “INeedToRememberASecurePassword.” It is longer than a typical password, but easier for a human to remember. In systems with maximum password lengths, you can use a passphrase as a mnemonic device to remember complicated passwords. For example, the passphrase “Anyone for some tennis?” could be a reminder for the highly secure password “ne14+10s.”
To address this problem, you need to set password requirements on length and composition. For example, you could require that a password have at least eight characters, and that it must contain a combination of uppercase and lowercase characters, as well as numeric or punctuation characters. This system ensures strong passwords, but you might have difficulty remembering them. Because users are primarily concerned with convenience, not with the security of the system, they often write down difficult passwords and post them in obvious locations. A malicious user with physical access to your work space can easily find the desired password.
In addition to addressing password complexity, it is also important to remind users that they should use a separate password for their work account and any personal accounts they may have. One of the most significant security risks facing organizations today is the risk that another website, not associated with your company, could be compromised and the attacker could gain access to an improperly protected password list. The attacker may then try logging in to your site with the usernames and passwords on the list. If users have used their work password on other sites, chances are that, with a big enough list, an attacker will stumble upon an active account.
Something You Have
Used alone, a physical token or device is generally used to provide physical security. Think of a smart card ID that you wave in front of a reader to gain access to specific floors of an office building. Tokens are also used in conjunction with passwords to provide logical access controls. Tokens can take a variety of forms such as the smart card or a time-variable token such as RSA’s SecurID. FIGURE 1-4 shows an example of the smart card authentication devices used by the U.S. Government, known as the Common Access Card (CAC) in military organizations or the Personal Identity Verification (PIV) card in other government agencies.

FIGURE 1-4 Smart card authenticator issued to U.S. government employees.
© United States Department of Defense
Time-variable tokens change users’ passwords at regular intervals, usually every 30 to 60 seconds. Users have a physical device that tells them what their password is set to at the moment they need to log in. This two-stage authentication process ensures that passwords are not guessed or stolen—and if they are, damage is limited because the password is valid for only a brief period of time. This token may be a separate device or, more commonly, an app running on a user’s smartphone. FIGURE 1-5 shows the Google Authenticator app configured to work with the multifactor authentication systems of a variety of services.
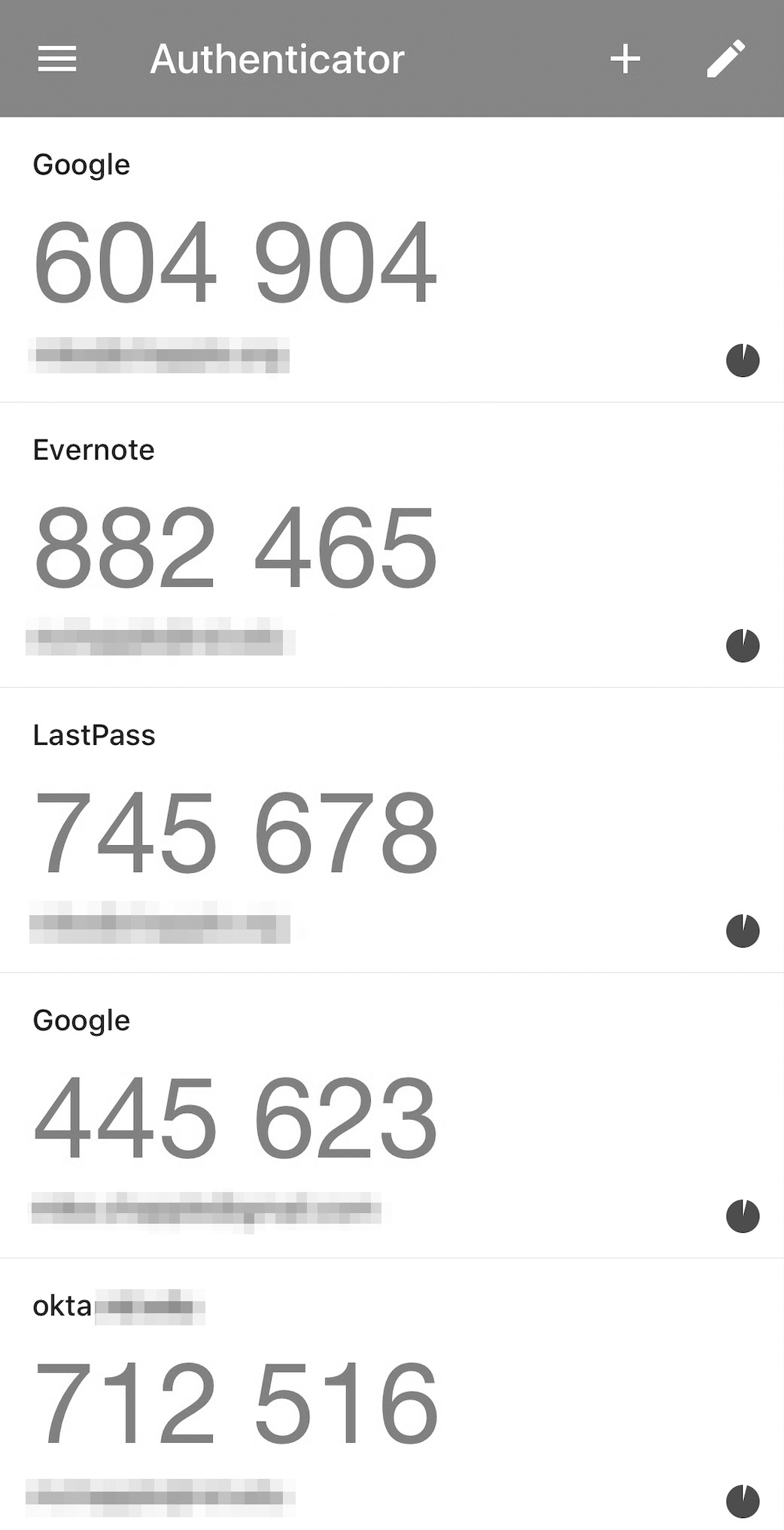
FIGURE 1-5 Google Authenticator app configured to work with a variety of services.
Google, Google Authenticator, and the Google logo are registered trademarks of Google Inc., used with permission.
Possession of the physical device or token is the only way to retrieve the current password. Because the token could be lost or stolen, this type of authentication requires a two-stage login process. For example, a user activates the token to find his or her active password. She enters the password, along with her username, and is granted access to a secondary login prompt. At this second prompt, she enters a conventional password that does not change. In this way, if the user’s conventional password is guessed or stolen, a malicious user would not have the token and would not be able to access the secondary login prompt to enter the stolen password. If the token is lost or stolen, a malicious user is stopped at the secondary login prompt because he or she presumably does not also have the user’s conventional password.
Challenge-response tokens are similar to time-variable tokens. An authentication system using this type of token will begin with a code (the “challenge”), which the user enters into the token device. The token provides another code (the “response”), which the user enters into the authentication system. Assuming that the response code is correct, the user will be granted access to the secondary login system, where he or she enters a conventional username and password. The challenge is chosen randomly and the token must provide the correct response. This reduces the possibility that an attacker will be able to predict a challenge and generate a response in advance if he or she has temporary access to a token.
In some cases, the challenge-response can be even simpler. For example, FIGURE 1-6 shows an example of the Duo smartphone app for multifactor authentication. In the approach used by this system, the user first completes the normal password-based authentication to a web application or other system. After successfully completing this knowledge-based authentication approach, the Duo system then pushes an alert similar to the one shown in Figure 1-6 to the user’s registered smartphone. The user simply taps “Approve” on the smartphone app and the authentication sequence is complete.
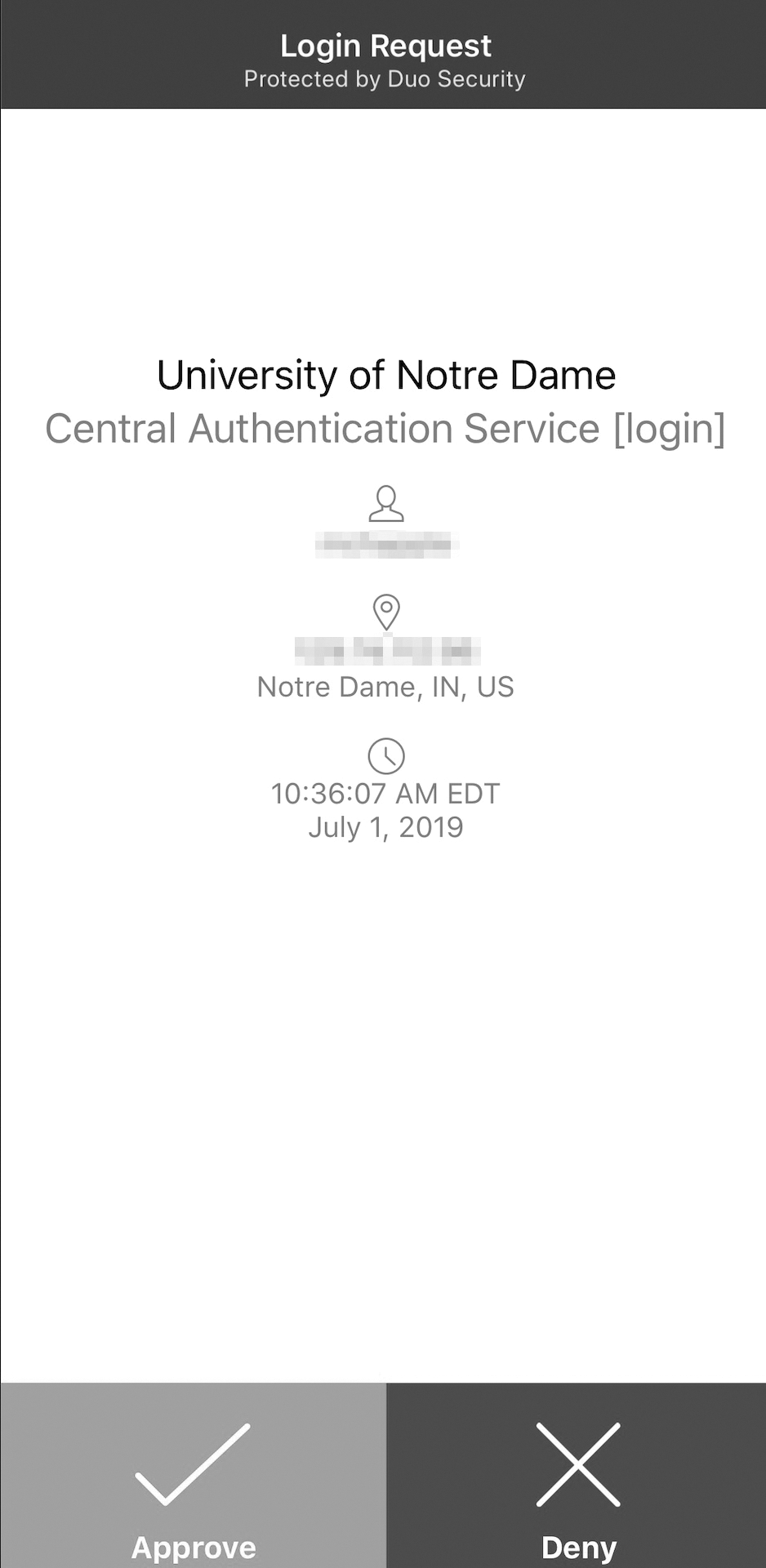
FIGURE 1-6 Push authentication request from Duo to a user’s smartphone.
Courtesy of Duo Security.
Something You Are
This is the most advanced as well as the most time-tested of the three primary authentication factors. It relies on either physical or behavioral characteristics. Humans have been using characteristics to authenticate each other for millennia. Consider an infant who recognizes its mother or other primary caregiver. The infant uses visual cues, scent, and the sound of the caregiver’s voice to authenticate the caregiver’s identity and determine whether to settle or scream.
 NOTE
NOTE
Biometrics, which includes fingerprints, retinal scans, and so on, is an important “something you are” authentication factor.
Biometrics is the study of physical human characteristics. Access control systems use biometrics to accurately identify and/or authenticate an individual. There are two primary types of biometric authentication systems: physical and behavioral. Physical biometrics read physical characteristics, such as fingerprints, retinal scans, hand geometry, and facial recognition. Physical biometrics are highly reliable because they measure characteristics that are unique to each individual. Even identical twins do not have the same fingerprints or retinal scans.
Fingerprints are commonly used to authenticate access to physical devices or facilities. FIGURE 1-7 shows an example of the use of fingerprint authentication by military troops in the field.

FIGURE 1-7 Fingerprint scanning for authentication.
© United States Department of Defense
Facial recognition is also growing in popularity because of its ease of use. Some smartphone models offer facial recognition to unlock the phone, make purchases, and perform other authenticated actions. One common example of this is the FaceID technology used on some Apple devices. Airports are also now using facial recognition technology for security screening, as shown in FIGURE 1-8.

FIGURE 1-8 Facial recognition in use at airport security screening (U.S. government photo).
© Glenn Fawcett/U.S. Customs and Border Protection
Behavioral characteristics may include tempo or speed of typing (or keystroke dynamics), writing rhythms, and voice recognition. Behavioral biometrics requires a significant “training period” for the system to “learn” a legitimate user’s behavior patterns. They are also much more subject to error than physical characteristics.
