Inside GPMC, you can view the current permission settings for any GPO by clicking on the GPO and then visiting the Delegation tab. To see the same information in text format from PowerShell, we can use the Get-GPPermissions cmdlet as shown in the following command. The -all specification at the end of the command tells Group Policy that we want to see all permissions that are listed inside the Delegation tab:
Get-GPPermissions -name "MyNewGPO" -all

This is a pretty normal listing of default permissions on a GPO, except that you can see our definition for Server Administrators that shows up as a result of Security Filtering being specified for that individual group.
In addition to viewing all of the permissions for a GPO, you can filter that output down to selectively view GPO permissions that are related to a single user or group. Earlier, when we covered the topic of modifying Security Filtering via PowerShell, we used a switch called -TargetType and we set it to group, because we were injecting a group into those Security Filtering permissions. The -TargetType switch can also be set to user to query or set information for a specific user, which we will accomplish here.
I am currently working with the GPO called Map Network Drives. My user named Jackson needs to have permissions to be able to edit this particular GPO. I am going to use PowerShell to query this GPO specifically for Jackson's user account to quickly check his level of permissions:
Get-GPPermissions -name "Map Network Drives" -TargetType User -TargetName "Jackson"
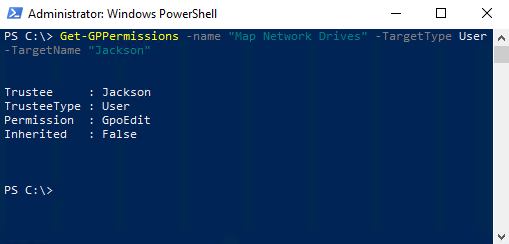
Sure enough, here we can see that Jackson has the Permission called GpoEdit, which means he has sufficient rights to edit this GPO if he should have the need to do so.
