Let's start with a policy setting that every company in the world should be putting into place for their users and computers. The purpose of having user accounts in the first place is to make sure that you can limit access to certain things based on who is logged in, and to be able to track which users are accomplishing which tasks. Therefore, it should be part of any company's employee handbook that users always lock their screens when they walk away from their desk. This is especially important with mobile computers, such as laptops. Imagine logging into your machine, connecting your company VPN, and then walking across the coffee shop to grab your drink. Just that quickly, someone sitting at the table behind you could open up your mapped drive and start deleting everything. Always lock your screens! But alas, not everybody will remember that they are supposed to do this. To counteract this potential malicious activity, we can utilize Group Policy to force an idle-time lockout policy that will automatically lock the screen after a certain amount of idle (inactive) time has passed on any domain-joined computer.
For this first example, I will walk through the steps for creating and linking our new GPO. I know we have already covered this topic, but it's a good and quick refresher for anyone new to Group Policy administration. For the remainder of the tasks outlined in our chapter, we will assume that you already have a firm handle on how to create your GPOs, link your GPOs, and filter your GPOs.
Open GPMC, and the first thing we need to do is create our new GPO. Right-click on the Group Policy Objects folder and choose New. I have named my new GPO Idle-time lockout policy, as you can see here:

You will also notice in the Scope tab that this new GPO is not yet linked anywhere, so at the moment it is not applying to anybody. This is a good thing, as we want to do some thorough testing on this new GPO setting prior to rolling it around to our workstations. Next, we want to populate this GPO with the setting that it needs to be able to tell the client computers how to enforce an idle lockout timer. Right-click on the new Idle-time lockout policy GPO, and choose Edit.... Then browse to the setting that we are going to manipulate, which is located at Computer Configuration | Policies | Windows Settings | Security Settings | Local Policies | Security Options | Interactive logon: Machine inactivity limit:

Double-click on the Interactive logon: Machine inactivity limit setting, and configure it accordingly for your environment. In order to easily test that this is working on my LAPTOP1 machine, I am going to set the idle timer very low, at one minute (60 seconds actually, as the setting needs to be specified in the number of seconds). That way, I can filter the GPO to my machine and know whether it is working in a very short amount of time:

Before clicking on OK, take a peek over at the Explain tab. This tab is always incredibly useful for showcasing what exactly each setting is going to do, so that you can be sure it will accomplish the task that you are asking of it:

After clicking OK, this 60-second idle timer is now configured inside the new GPO. The final step to test this out is to apply the GPO to a client computer and see what it does. I have an OU that I use for testing all of my new GPO settings, appropriately called Testing GPOs. I will now right-click on that OU from inside GPMC, and choose the option to Link an Existing GPO..., after which I am presented with a list of all the GPOs in my environment:

Selecting the new Idle-time lockout policy and clicking OK, my GPO is now successfully linked to the Testing GPO's OU. I then use Active Directory Users and Computers to move my LAPTOP1 computer object inside that Testing GPO's OU, and after restarting LAPTOP1, it is now receiving the new GPO setting. We can verify this by logging into LAPTOP1 and running the GPRESULT /R command:
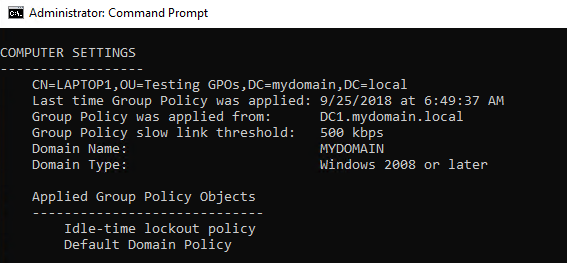
After letting my LAPTOP1 workstation sit around without any mouse or keyboard input for a solid 60 seconds, we can see that, yes indeed, the screen has locked itself out and is now forcing me to re-enter my password to continue with my work:

Now, remember, implementing security and maintaining user-friendliness is always a sliding scale. The more strict your security posture, the more annoyed your users are going to be. How many Christmas cards would you like to receive this year? Make sure to cross-check your policy settings with a little bit of common sense. Do you really want all machines to lock themselves out after only one minute of inactivity? Will that drive users crazy? Maybe there is a more realistic compromise, something such as 3-5 minutes.
