AD Security Groups are created from inside the ADUC toolset, and on their own accord security groups don't necessarily have anything to do with Group Policy. So the creation of these groups is outside the scope of our instructions here, but we will assume you have some groups already created that we can play around with. I have created two new groups called "Users needing Blue 1 Desktop Wallpaper" and "Users needing Orange 2 Desktop Wallpaper". Recall that we already have GPOs that are assigning these graphics to people's desktops, and we have done some creative linking in order to get those GPO settings to apply to certain users as they log in to their workstations.
Within the Accounting OU, I have a need for some users to receive the Blue desktop wallpaper, and other users must receive the Orange wallpaper settings. Organizing these GPO links is starting to become cumbersome, as what I really want to do is to have all of my Accounting users inside one single OU. Linking both of those GPOs to this OU is going to result in either one or the other GPO having priority, and so all of my Accounting users would receive the same wallpaper setting. I could split up the wallpaper access by creating an additional OU and then moving half of my users over to that other OU, and linking the GPOs separately to the two different OUs, but that makes the OU structure more confusing. Instead, I am going to leave all user accounts inside the Accounting Users OU, link both of my desktop wallpaper GPOs right to the "parent" Accounting OU, and then utilize the Security Filtering section of those GPOs to specify particular security groups to which they should apply.
Utilizing security filtering is a way of filtering GPO settings to apply to certain users or devices; there is not accommodation inside the Security Filtering section to block these settings for only certain users or devices. While we will discuss a capability to block or deny access for certain people a little later in this chapter, it is important to remember that when you are using the Security Filtering section for manipulating this access, your groups need to contain the list of users or computers that you would like the GPO to successfully apply to. In other words, any users or computers that are not part of this group will not receive the GPO settings.
You can see in the following screenshot that I have now adjusted my GPO links so that both policies concerning desktop wallpaper are linked to the Accounting OU. All of my Accounting computers are in the corresponding nested OU, and the same is true for my Accounting users. As of now, those two GPO settings are going to conflict when a user logs in to a computer, and all users will receive the same wallpaper based on the link order priority inside Group Policy; basically, whichever GPO processes last will win:
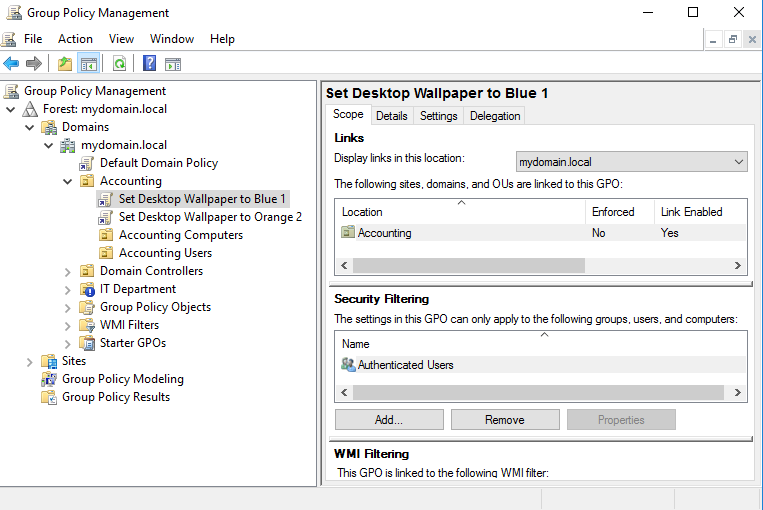
Also seen in the preceding screenshot is that we are looking inside the Scope tab of the Set Desktop Wallpaper to Blue 1 GPO, and you can see here the section called Security Filtering. Currently, the only thing in that list is Authenticated Users, which means that this GPO will apply to any user that resides under this link.
To adjust the scope of this security filter, the first thing we want to do is remove Authenticated Users from the list. To do this, simply choose Authenticated Users and click the Remove button, and it will disappear. Now that the Security Filtering list is empty, this GPO will no longer apply to anyone or anything, even though it is still linked, until we input something new into the Security Filtering section.
Now click the Add... button, and search for the AD Security Group to which you would like this GPO to be filtered. As you can see in the following screenshot, I have selected my new group of users that I would like to have the Blue 1 desktop wallpaper:

I will also adjust the security filtering on my Orange 2 GPO so that only my other new security group, the one that contains users who need the Orange desktop wallpaper, will receive the appropriate settings. I have now successfully filtered both of these GPOs so that they are only applying to users who are listed inside those AD Security Groups. Now if I have new users that need the settings, or users who no longer need those settings, giving or taking away their wallpaper configurations is as simple as adding or removing them from the AD group membership.
In fact, you can modify that AD group membership right from this same screen of the GPMC. At the bottom of the Security Filtering section, next to the Add... and Remove buttons, is a third button called Properties. Select a group from the list, click on Properties, and you will see the list of users or computers that are included inside this list. You also have the ability to add or remove objects from here. Alternatively, you could of course perform this function from inside ADUC:

While our example focused on user accounts because the desktop wallpaper settings are a user configuration inside Group Policy, what I find myself doing more often in day-to-day Group Policy administration is filtering GPOs to computer accounts. The process for security filtering a GPO to a group or groups of computers is exactly the same. Simply create your AD group, add a bunch of computer objects to it, and then set that group as your filter inside GPMC. I often help companies roll out certificates to all of their workstations as part of remote access projects. We roll out those certificates through a process known as autoenrollment, which can be configured via Group Policy. As you can see in the following screenshot, I have created a new GPO for Autoenrollment settings, linked it to my domain, and then security filtered it to two specific groups of computers. Since this GPO is linked way at the top of the domain, if I had left Authenticated Users in that list, I would be sending out certificates to every computer in the domain. However, I was careful to set my Security Filtering settings prior to putting the actual Autoenrollment settings inside my GPO, and as such, only those computers that I manually add into these AD groups will be receiving my Certificate Autoenrollment settings:

