Chapter 16
Data Communication and Computer Networks
This chapter introduces the reader to data communication and computer network. Data communication is the exchange of data between two devices via some form of transmission medium. It is carried within a collection of computers, which are linked together to share information and resources. The discussion begins with an outlook on data communication and its components. It is continued with various transmission modes, transmission media, modulation, and switching techniques. In the later stages of the chapter, the reader is acquainted with different types of network and topologies. The chapter concludes with an overview of various networking devices.
After reading this chapter, you will be able to understand:
The basic concepts of communication and networking
Data communication, which is the exchange of data between two devices using some form of transmission medium
Transmission media, which refers to the physical media through which communication signals are transmitted
Modulation, which is the addition of information to a signal carrier wave
Multiplexing, which is a technique used for transmitting several signals simultaneously over a single communication channel
Switching, which means routing traffic by setting up temporary connections between two or more network points
Computer network—a collection of two or more computers connected together to share information and resources
Network topology, which is the way a network is laid out, either physically or logically
Communication protocol—a set of rules that coordinate the exchange of information
Network devices, which interconnect individual computers for efficient communication
16.1 INTRODUCTION
The term communication in simple words means sending or receiving information. In ancient times, people used the beating of drums, smoke signals, mirrors reflecting sunlight, homing pigeons, and so on to send messages. Another way of long-distance communication was the use of homing pigeons to carry messages. With the advancement in science and technology, various devices were invented for communication. Telegraph was one of the most prevalent ways of data communication in the nineteenth century. In 1870, Alexander Graham Bell invented the telephone, which revolutionized the way long-distance communication used to take place. Voice communication became common after the invention of the telephone. In the 1940s and 1950s, a major breakthrough was made in the development of computers and setting up a network of computers for electronic transfer of information or data communication. In fact, the first network was established in 1940, when George Stibitz and Samuel Williams, researchers at Bell Laboratories, developed complex number generator—one of the earliest digital computers. They made it possible for the users to operate the computer remotely from teletype machines. They also developed a system to allow users to communicate with the machine even more remotely, through telex machines. The advancement of computer networks and later the Internet acted as a boost for data communication.
Whenever more than one computer is used at the same location, networking them together facilitates exchange of data and information (data communication) between connected computers in a fast and efficient manner. Networking also helps sharing expensive resources like printers, backup tape drives, scanners, Internet connections, and so on. In this chapter, we discuss how communication system works, various transmission medias and devices, different techniques of data communication, types of computer network, and various network topologies.
16.2 DATA COMMUNICATION
Data communication is the exchange of data between two devices using some form of wired or wireless transmission medium. It includes the transfer of data, the method of transfer, and the preservation of the data during the transfer process. To initiate data communication, the communicating devices should be a part of an existing communication system. For data communication to be effective, the following three fundamental characteristics should be considered:
THINGS TO REMEMBER
Communication System
A communication system can be defined as the collection of hardware and software that facilitates intersystem exchange of information between different devices. When we communicate, we are sharing information. This sharing can be local (face-to-face communication) or it may be remote (communication over distance).
- Delivery: The system must deliver data to the correct or the intended destination.
- Accuracy: The system must deliver data accurately (error free).
- Timeliness: The system must deliver data in a timely manner without enough time lags.
16.2.1 Components of Data Communication
There are five basic components in data communication system.
- Message: The message is the information that is to be communicated.
- Sender: The sender is the device that sends the message.
- Receiver: The receiver is the device that receives the message.
- Medium: The transmission medium is the physical path that communicates the message from the sender to receiver.
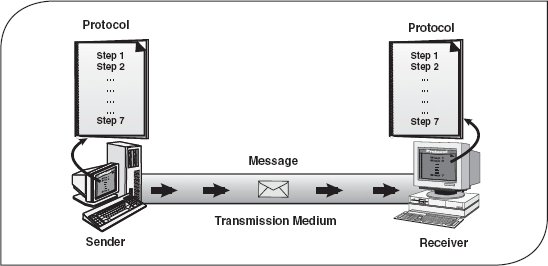
- Protocol: Protocol refers to a set of rules that coordinate the exchange of information. Both sender and receiver should follow the same protocol to communicate data. Without the protocol, the sender and receiver cannot communicate with each other; just as a person speaking English cannot be understood by a person who knows only Hindi (Figure 16.1).
Figure 16.1 Data Communication Components
Suppose you want to convey your final marks to your mother. You call her via telephone and inform her about your marks. Here your marks is the message, you are the sender, your mother is the receiver, the telephone line is the medium, and the language in which you are conversing is the protocol.
16.2.2 Data Transmission Mode
Data transmission mode refers to the direction of signal flow between two linked devices. There are three types of transmission modes: simplex, half-duplex, and full-duplex (Figure 16.2).
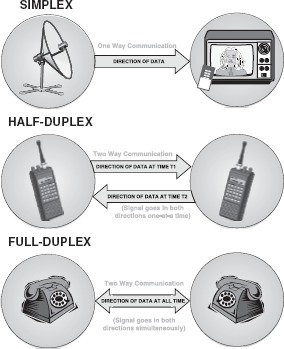
Figure 16.2 Data Transmission Modes
Simplex: Simplex transmission is unidirectional. The information flows in one direction across the circuit, with no capability to support response in the other direction. Only one of the communicating devices transmits information, the other can only receive it. Television transmission can be considered as an example of simplex mode of transmission where the satellite only transmits the data to the television, vice versa is not possible.
Half Duplex: In half-duplex mode, each communicating device can receive and transmit information, but not at the same time. When one device is sending, the other can only receive at that point of time. In half-duplex transmission mode, the entire capacity of the transmission medium is taken over by the device, which is transmitting at that moment. Radio wireless set is an example of half-duplex transmission mode where one party speaks and the other party listens.
Full Duplex: Full-duplex transmission mode, also known as the duplex mode, allows communicating devices to both transmit and receive data simultaneously. A full-duplex mode can be compared to a two-way road with traffic flowing in both directions. A standard voice telephone call is a full-duplex call because both parties can talk at the same time and be heard.
16.2.3 Analog and Digital Data Transmission
The major role of the physical medium is to move the data from one communicating device to another. The data can be transmitted by means of electromagnetic signals. These signals may be in one of the two forms: analog or digital. Depending on the form of signal used, data transmission can be analog data transmission or digital data transmission.
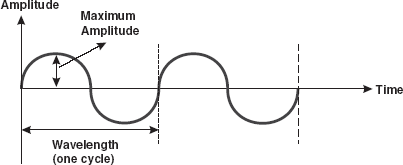
Analog Signals: An analog signal is a continuous waveform that changes smoothly over time. The sine wave is the most fundamental form of an analog signal (see Figure 16.3). Sine waves can be described by three characteristics.
- Amplitude: It is the value of the signal at any point on the wave. The maximum amplitude of a sine wave is the highest value it reaches on the vertical axis. The unit for amplitude depends on the type of the signal. For electrical signals, the unit is normally volts and amperes.
- Frequency: It refers to the number of cycles a signal completes in 1s. In other words, frequency means the number of times a signal wave goes up and down in a second and it is measured in Hertz (Hz). For example, if a signal wave completes one cycle in 1s, its frequency is 1 Hz.
- Wavelength: It refers to the distance between successive similar points of a given wave, that is, one cycle of the waveform.
Analog signals are perfect for carrying data such as voice or sound. However, these signals are prone to errors or noise that can be caused by the outside sources. Attenuation is another problem with analog signals because the amplitude of the wave naturally changes over distance.
Digital Signals: Digital signal is the data stored in the form of 0s and 1s. When the signal is at a high point, its value is 1 and when it is low, its value is 0. A signal in digital format has precise voltages that are not affected by noise or attenuation as compared with analog signals, which are very prone to noise. Digital signals can be represented by a graph similar to a bar graph. In Figure 16.4, 1 can be encoded as a positive voltage and 0 as a zero voltage.

Figure 16.4 Digital Signal
To transmit data over analog telephone lines, a modem is required to convert the digital data signals to analog signals. When transmitted over long distances, analog signals require to be amplified, which can possibly distort the value of the data transmitted. When analog data is converted to digital data, it can be transmitted over digital signals faster and without distortion.
16.2.4 Data Communication Measurement
The measurement of the quantity of data that can be passed over a communication link in a given time is done in terms of bandwidth. Fundamentally, bandwidth refers to the maximum volume of data that can be transferred over any communication medium at a given point of time. The more the data needed to be transmitted in a given period, the more is the bandwidth required. On digital circuits, bandwidth is measured in bits per second (bps), which refers to the number of bits transmitted per second. A 1,000 bps is 1 kilobit per second or 1 kbps.
In the digital context, the level of bandwidth falls into three categories.
- Narrowband: In narrowband, there is a single transmission channel of 64 kbps or less. With advances in network technology, narrowband has come to be associated with any channel operating at less than 1.544 Mbps.
- Wideband: It is a medium-capacity communication channel, which carries data at speeds between 1.544 Mbps and 45 Mbps.
- Broadband: It is a transmission medium, capable of supporting a wide range of frequencies. It can carry multiple signals by dividing the total capacity of the medium into multiple, independent bandwidth channels, where each channel operates only on a specific range of frequencies. The bandwidth capacity in broadband is equal to 45 Mbps. Broadcast television, cable television, microwave, and satellite are examples of broadband technologies. These technologies are capable of carrying a great deal of information in a short amount of time, but are more expensive to use than technologies like the telephone, which require less bandwidth.
16.3 TRANSMISSION MEDIA
Transmission media refers to the physical media through which data can be transmitted from one point to another. As already stated, the data is transmitted from one device to another through electromagnetic signals. An electromagnetic signal is the combination of electric and magnetic fields, vibrating in conjugation with each other. Electromagnetic signals include power, voice, radio waves, infrared light, visible light, ultraviolet light, X-rays, and gamma rays. All these together constitute an electromagnetic spectrum. These signals can travel through vacuum, air or any other transmission medium. Voice signals are generally transmitted as current over metal cables. Radio frequencies are generally transmitted through air or space. Third type of electromagnetic energy is the visible light, which is currently being used for communication through fibre optic cable. Transmission media can be divided into two broad categories: guided/wired media and unguided/wireless media.
16.3.1 Guided/Wired Media
Guided transmission media use a cabling system that guide the data signals along a specific path. Cable is the medium through which information usually moves from one network device to another. It consists of a cable composed of metals like copper, tin, or silver. The data signal in the guided medium is bound by the cabling system; hence, guided medium is also known as bound medium. There are three basic types of guided media—twisted pair, coaxial cable, and optical fibre.
Twisted Pair: The biggest network in the world, the telephone network, originally used only twisted-pair cabling and still does for most local connections. The name comes from the fact that each individually insulated conductor is part of a pair, making this a balanced medium, and that each pair is twisted together along its length, which helps to further protect it from interference from external sources. Each pair consists of a wire, used for receiving data signal, and a wire used for transmitting data signal. Twisted pairs are used in short-distance communication (less than 100 m). It comes in two forms, namely, unshielded and shielded with a metal sheath or braid around it. The two are commonly known as unshielded twisted pair (UTP) and shielded twisted pair (STP).
- UTP Cable: It is the most common type of telecommunication medium in use today. It is most suited for both data and voice transmission, hence is commonly used in telephone systems. The cable has four pairs of wires inside the jacket. Each pair is twisted with a different number of twists per inch to help eliminate interference from adjacent pairs and other electrical devices. The tighter the twisting, the higher the supported transmission rate and the greater the cost per foot. Each twisted pair consists of two metal conductors (usually copper) that are insulated separately with their own coloured plastic insulation (Figure 16.5).
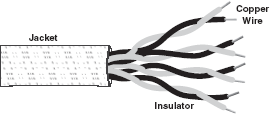
Figure 16.5 Unshielded Twisted-Pair Cable
- STP Cable: This cable has a metal foil or braided mesh covering that covers each pair of insulated conductors. The metal foil is used to prevent infiltration of electromagnetic noise. This shield also helps to eliminate crosstalk, a phenomenon that can be experienced during telephone conversation when one can hear another conversation in the background. A disadvantage of UTP is that it may be susceptible to radio and electrical frequency interference. Shielded twisted pair is suitable for environments with electrical interference; however, the extra shielding can make the cables quite bulky (Figure 16.6).

Figure 16.6 Shielded Twisted-Pair Cable
Note: All signalling over twisted pair is of the baseband type. Baseband transmission use the entire media bandwidth for a single channel, that is, only one signal can be carried at a time, and all the systems take turns using it.
Coaxial Cable: Coaxial cables have a single central conductor, which is made up of solid wire (usually copper). This conductor is surrounded by an insulator over which a sleeve of metal mesh is woven to block any outside interference. This metal mesh is again shielded by an outer covering of a thick material (usually PVC) known as jacket (Figure 16.7).

Figure 16.7 Coaxial Cable
Although coaxial cabling is difficult to install, it is highly resistant to signal interference. It can support greater cable lengths between network devices than twisted-pair cable. In addition, as compared to twisted pairs, it also offers higher bandwidth. A coaxial cable is capable of transmitting data at a rate of 10 Mbps. It is more expensive per foot, but cheaper per bytes of data transferred in a second. Coaxial cable is very robust and is commonly used in cable TV network.
Optical Fibre: Twisted-pair and coaxial cable transmit data in the form of current. Optical fibre, on the other hand, consists of thin glass fibres that can carry information in the form of visible light. The typical optical fibre consists of a very narrow strand of glass called the core. Around the core is a concentric layer of glass called the cladding. A typical core diameter is 62.5 microns (1 micron=10-6m). Cladding generally has a diameter of 125 microns. The cladding is covered by a protective coating of plastic, known as jacket (Figure 16.8).
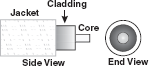
Figure 16.8 Optical Fibre
Optical fibre has the ability to transmit signals over much longer distances than coaxial and twisted pair. Light signal, unlike electrical signal, does not heat up the wire and is not susceptible to outside interference. It is extremely hard to tap into, making it desirable from the security point of view. Optical fibre also has the capability to carry information at vastly greater speeds. A single optical fibre can pack hundreds of fibres, where each fibre has the capacity equivalent to that of thousands of twisted-pair wires. This capacity broadens communication possibilities to include services such as video conferencing and interactive services. However, fibre optics cable is by far the most expensive per foot. Moreover, it is more difficult to install and modify (Figure 16.9).
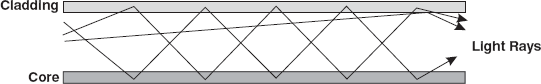
Figure 16.9 Signals Carried Over an Optical Fibre
THINGS TO REMEMBER
Optical Fibres
Optical fibres work on the principle that the core refracts the light and the cladding reflects the light. The core refracts the light and guides the light along its path. The cladding reflects the light back into the core and stops it from escaping through the medium. These light pulses, which can be carried over long distances via optical fibre cable, carry information.
16.3.2 Unguided/Wireless Media
Unguided media facilitates data transmission through earth's atmosphere (air, water, or vacuum) at a much faster rate and provides wide area coverage. The data signals are not guided or bound to a fixed channel to follow. Some commonly used unguided media of transmission include radio frequency (RF) propagation, microwave transmission, satellite transmission, infrared wave transmission, Bluetooth, and Wi-Fi.
RF Propagation: In RF propagation, the signal is carried over carrier waves (waves which carry signals over them), which have frequencies in the range of RF spectrum. There are three types of RF propagation, namely, ground wave, ionospheric, and line of sight.
Ground wave propagation follows the curvature of the earth. They have carrier frequencies of up to 2 MHz. AM radio is an example of ground wave propagation (Figure 16.10).

Figure 16.10 Ground Wave Propagation
In ionospheric propagation, the signal wave bounces off the earth's ionosphere layer in the upper atmosphere. It operates in the frequency range of 30–85 MHz. As this type of propagation depends on the earth's ionosphere, it changes with the day timings and weather (Figure 16.11).
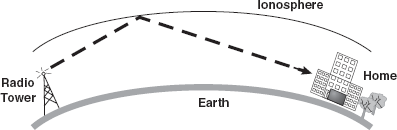
Figure 16.11 Ionospheric Propagation
Line of sight propagation transmits exactly in the line of sight. The receiving station must be in view of the transmitting station. It is sometimes called space waves or tropospheric propagation. It is limited by the curvature of the earth for ground-based stations (50 km) (Figure 16.12).
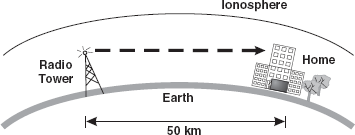
Figure 16.12 Line of Sight Propagation
Microwave Transmission: Microwave transmission use microwave signals that travel at a higher frequency and are popularly used for transmitting data over long distances. Microwave communication uses parabolic antennas (satellite TV dish antennas) that are mounted on the tower, which could be tens of kilometers away, but in line of sight. Due to long distances, repeaters are used at regular intervals in between the transmitter and the receiver to boost the signals. Normally, the distance between the repeaters goes up roughly with the square root of the tower height. For example, for a 100 m high tower, repeaters can be spaced at 80 km apart (Figure 16.13).
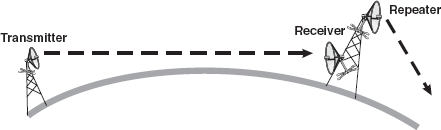
Figure 16.13 Microwave Transmission
Satellite Transmission: Satellite transmission is also a kind of line of sight transmission. Satellites are set in geostationary orbits directly over the equator, which rotates in synchronization to earth, hence they look stationary from any point on earth. These geostationary orbits are placed 36,000 km above the earth's surface. The communication is carried through uplinks and downlinks. The uplink transmits the data to the satellite and downlink receives the data from the satellite. Uplinks and downlinks are also called earth stations because they are located on the earth. The area shadowed by the satellite in which the information or data can be transmitted and received is called the footprint (Figure 16.14).
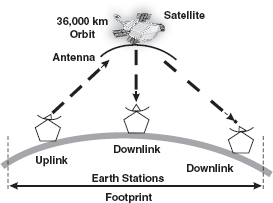
Figure 16.14 Satellite Transmission
Infrared Wave Transmission: Infrared frequencies are just below the visible light spectrum. These are the high-frequency waves used for short-range communication. The waves are cheap, directional, and can be easily built; however, the waves do not pass through solid objects. Infrared waves are used in TV remotes, garage doors, and wireless speakers. Computer machines in an office can easily be connected in a wireless local area network (LAN) using infrared waves (Figure 16.15).

Figure 16.15 Infrared Wave Transmission
Bluetooth: Bluetooth system is named after a Danish king Harold Blatand (Bluetooth in English) who is known for his contribution to unification of tribes from Denmark, Norway, and Sweden. The Bluetooth technology is used to create a personal area network (PAN) or piconet that lets electronic devices, such as computers, cell phones, PDAs, wireless keyboards, etc., to communicate with each other within the range of 10 m. It uses radio signals that are omni-directional, that is, signals travel in all directions from the source. Hence, the communicating devices need not be aligned with each other.
When Bluetooth-capable devices come within range of one another, an electronic conversation takes place to determine whether they have data to share or whether one needs to control the other. The user does not have to manually operate on the devices, as connections are set automatically. Once the conversation has occurred, devices form a piconet. Once the piconet is established, the member devices randomly hop frequencies in unison so they stay in touch with one another and avoid other piconets that may be operating in the same room.
The key features of Bluetooth are its roubtness, low complexity, and low power requirements that make it suitable for handheld devices like cell phones, PDAs, etc. Today, almost all the small handheld devices are Bluetooth enabled. The Bluetooth radio-link uses a fast acknowledgement and frequency-hopping scheme to make. However, the maximum data transmission rate that it supports is only 1 Mbps, which makes it unsuitable for exchanging large files or folders. Moreover, the maximum range for this technology is 30 feet, which limits the space of PAN and the connection accessibility for electronic devices to perform an action (Figure 16.16).
Figure 16.16 Bluetooth Communication
Wi-Fi: The term Wi-Fi which stands for Wireless Fidelity is widely used for creating wireless LANs and also for providing wireless Internet access. To create wireless LAN, the devices in the network, such as computer, laptop, PDA, etc., should be equipped with wireless network interface card (NIC) to send and receive Wi-Fi signals. A Wi-Fi-enabled device should be within a specific range (that is, up to 50 m) from the network to connect to it.
The major benefit of Wi-Fi is that it allows developing low-cost wireless networks by reducing the cost of wires for connecting devices. Elimination of wires enables the wireless devices to move from one location to another (within the range) without losing the connectivity. Though Wi-Fi enables availing network services at low cost, it has some disadvantages also.
The weak security is one of the disadvantages of Wi-Fi that makes the wireless network vulnerable to attack from the intruders. Wi-Fi signals are not confined to the boundaries of building (in which the wireless LAN is operating); thus any intruder can easily gain access to the network by standing outside the building Another disadvantage of Wi-Fi network is its susceptibility to interference from other devices operating in the same area such as wireless phones, other wireless networks, etc (Figure 16.17).
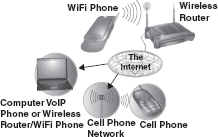
Figure 16.17 Wi-Fi
16.4 MODULATION
Consider a scenario where a boy standing over the roof of his house has to deliver a paper to the boy standing over the roof of the house in front. Due to the distance between the two roofs, the first boy cannot just hand over the paper to the other. In addition, paper alone cannot travel the distance (if thrown) because it is lightweight. Therefore, the first boy wraps the paper onto a stone and throws it towards the other boy, who catches the stone wrapped in the paper. The boy takes off the paper from the stone, reads the message, and discards the stone. In this manner, the first boy is able to deliver a message to the other boy. In the same way, before a signal is transmitted in a wide communication system, the signals (paper) are superimposed on a carrier signal (stone), which propagates by means of an electromagnetic wave. This process is called modulation. Modulation is the addition of information (or the signal) to a signal carrier wave. These carrier waves carry the signals to travel over long distances. Generally, there are three forms of modulation: amplitude, frequency, and phase.
16.4.1 Amplitude Modulation (AM)
In this modulation, the amplitude of a carrier wave is varied in accordance with the characteristic of the modulating signal. The frequency of the carrier remains the same, only the amplitude changes to follow variations in the signal. In simpler words, the two discrete binary digits (0 and 1) are represented by two different amplitudes of the carrier signal. Figure 16.18 depicts how the modulating signal is superimposed over the carrier signal that results in an amplitude-modulated signal.
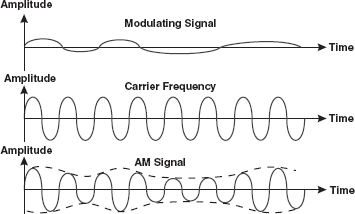
Figure 16.18 Amplitude Modulation
16.4.2 Frequency Modulation (FM)
In this modulation, the instantaneous frequency of carrier wave is caused to depart from the centre frequency by an amount proportional to the instantaneous value of the modulating signal. In simple words, FM is the method of impressing modulating signal onto a carrier signal wave by varying its instantaneous frequency rather than its amplitude (see Figure 16.19).
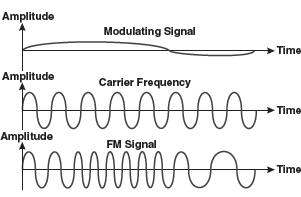
Figure 16.19 Frequency Modulation
16.4.3 Phase Modulation (PM)
PM is the encoding of information into a carrier wave by variation of its phase in accordance with an input signal. In this modulation technique, the phase of sine wave carrier is modifed according to the amplitude of the message to be transmitted. This technique is also called phase shift keying (PSK), which refers to the simple case of PM by a simple signal with only two states (Figure 16.20).
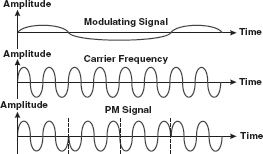
Figure 16.20 Phase Modulation
16.5 MULTIPLEXING
In a network environment, it is common that the transmission capacity of a medium linking two devices is greater than the transmission needs of the connected devices. Hence, the medium can be shared so that it can be used fully. This can be done by multiplexing. Multiplexing is a technique used for transmitting several signals simultaneously over a single communication channel. An analogy of multiplexing can be made with a multilane highway. Just as a multilane highway can carry increased volumes of traffic in multiple lanes at higher speeds and at relatively low incremental cost per lane, higher-capacity circuit can carry multiple conversations in multiple channels at relatively low incremental cost per channel.
16.5.1 Multiplexers
In a multiplexed system, several devices share the capacity of outputs single communication link called common medium. The communication device (on the sender's side) that multiplexes (combines) several signals into one data communication signal to be transmitted over the common medium is called a multiplexer (MUX). At the receiving end, a demultiplexer (DEMUX) completes the communication process by separating multiplexed signals from a transmission line and distributing it to the intended receiver (Figure 16.21).

Figure 16.21 A Multiplexed System
Signals are multiplexed using two basic techniques: frequency-division multiplexing (FDM) and time division multiplexing (TDM).
FDM: FDM is used when the bandwidth of the transmission medium between the MUX and DEMUX is much greater than the requirements from any one stream being multiplexed. FDM is usually used for broadband analog transmissions. In this technique, signals from each sending device are modulated using carrier waves with different frequencies. These modulated signals are then combined into a single composite signal that is transported over the common medium. Each modulated signal acts as a channel. One of the most common examples of FDM is the transmission of radio stations. Figure 16.22 gives a conceptual view of FDM.
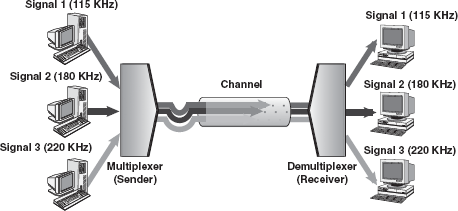
Figure 16.22 Frequency Division Multiplexing
TDM: TDM divides the main signal into time slots, with each time slot carrying a separate signal. It is used for digital communication and can be applied when the data rate capacity of the transmission medium is greater than the data rate required by the sending and receiving devices. Time division MUX allocates each input channel a period of time or time slot. Figure 16.23 gives a conceptual view of TDM. Each sending device is assigned the transmission path for a predefined time slot. Three sending signals, Signal 1, Signal 2, and Signal 3, occupy the transmission sequentially. As shown in the Figure 16.23, time slots A, B, P, Q, X, and Y follow one after the other to carry signals from the three sources, which upon reaching the DEMUX are sent to the intended receiver.
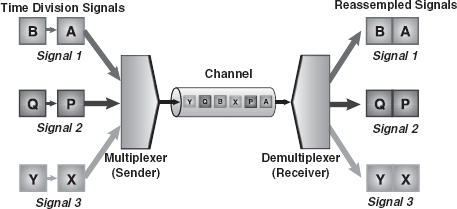
Figure 16.23 Time Division Multiplexing
16.5.2 Asynchronous and Synchronous Transmission
The primary concern while considering the transmission of data from one device to another is to decide whether to send the data one bit at a time (serial mode) or to send a group of bits into a large group (parallel mode). In serial mode, one bit is sent at a given instant; hence, only one communicating channel is needed to transmit data. Since only one communication channel is required, the cost is largely reduced. On the other hand, in parallel mode, multiple bits are sent at any given instance; therefore, more than one channel is needed to transmit data. There is only one way of sending data in parallel mode, but there are two subclasses of serial transmission, namely, asynchronous and synchronous transmission.
Asynchronous Transmission: Asynchronous transmission is so called because the timing of the signal is not important. The information that is received or transmitted follows a predefined pattern. As long as the patterns are followed, the receiving device can retrieve the information without any regard to the timing of the signal sent. However, a synchronizing pulse is necessary for the receiver to know when the data is coming and when it is ending. Hence, each byte of information is preceded by a start bit (denoted by 0) and ended by a stop bit (denoted by 1). Therefore, the information in one byte, that is, eight bits becomes ten bits, increasing the overheads. In addition, the transmission of each byte may be followed by a gap of varying duration, which can further help in synchronizing the information with the data stream or channel. As soon as receiver detects the stop bit, it ignores any received pulses until it detects the next start bit. The asynchronous transmission is slower than the other forms of transmission but at the same time is cheaper and an attractive choice for low-speed communication (Figure 16.24).
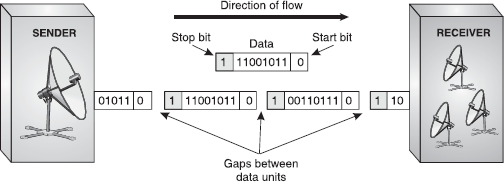
Figure 16.24 Asynchronous Transmission
Synchronous Transmission: Synchronous mode of transmission works on the same media as the asynchronous transmission, but the transmitter does not send start and stop bits to the receiver. The receiver's clock is synchronized with the transmitter's clock. In other words, data is transmitted as an unbroken string of 1s and 0s, and the receiver, on the basis of clock timings, separate the string into bytes. Timing becomes very important in synchronous transmission because without start and stop bits, there is no in-built mechanism to help the receiving device access the incoming information. The advantage of synchronous transmission is speed. With no extra start and stop bits, overhead is lessened, increasing the speed of transmission. Therefore, synchronous transmission is useful for high-speed application like transfer of large data from one computer to another (Figure 16.25).
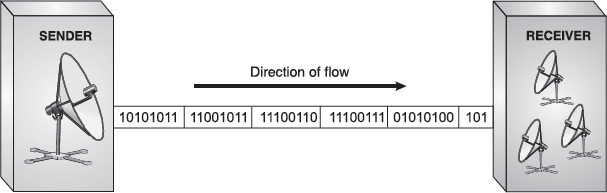
Figure 16.25 Synchronous Transmission
16.6 SWITCHING
Consider a scenario of a small office having four telephone sets used by the four employees for communication. If direct lines were to be used for all the people, six duplex lines are required n(n - 1)/2 lines, where n is the number of telephone sets. This is called point-to-point connection (Figure 16.26).
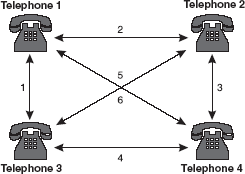
Figure 16.26 Point-to-Point Connection
This method, however, is impractical and wasteful when applied to very large networks. The number and length of the links require too Telephone 3 much of infrastructure; in addition, majority of these links would remain idle and wasted most of the time. A better solution is switching. On a network, switching means routing traffic by setting up temporary connections between two or more network points. This is done by devices located at different locations on the network, called switches (or exchanges). In a switched network, some switches are directly connected to the communicating devices while others are used for routing or forwarding information.
Figure 16.27 depicts a switched network in which communicating devices are labelled A, B, C, and so on and switches are labelled I, II, III, I V, and so on. Each switch is connected either to a communicating device or to any other switch for forwarding information. Notice that multiple switches are used to complete the connection between any two communicating devices at a time, hence saving the extra links required in case of a point-to-point connection.
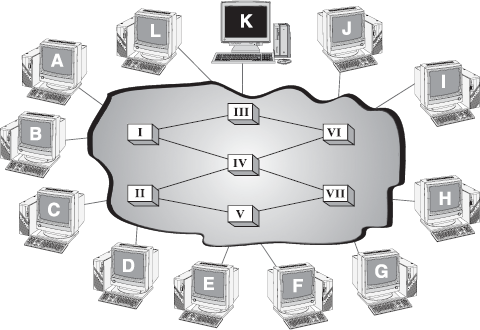
Figure 16.27 Switched Network
Switching traditionally employs three methods: circuit switching, packet switching, and message switching. Out of these, only circuit and packet switching are in use nowadays, message switching has been phased out in general communications.
16.6.1 Circuit Switching
When a device wants to communicate with another device, circuit switching technique creates a fixed-bandwidth channel, called a circuit, between the source and the destination. This circuit is reserved exclusively for a particular information flow, and no other flow can use it. Other circuits are isolated from each other, and thus their environment is well controlled.
THINGS TO REMEMBER
Circuit Switching
Circuit switching is plagued by many disadvantages. When there is no flow of data, the capacity of incurring link is wasted. Circuit switching is less suited to data communication, where the data come in surges with idle gaps between them. It is inflexible as well, that is, once the circuit is established, that circuit is the only path taken by the flow of information whether or not it remains the most efficient and available.
As illustrated in Figure 16.28, if device A wants to communicate with device D, sets of resources (switches I, II, and III) are allocated which act as a circuit for the communication to take place. The path taken by data between its source and destination is determined by the circuit on which it is flowing and does not change during the lifetime of the connection. The circuit is terminated when the connection is closed. Therefore, this method is called circuit switching. A common example of a circuit switched network is public switched telephone network (PSTN).
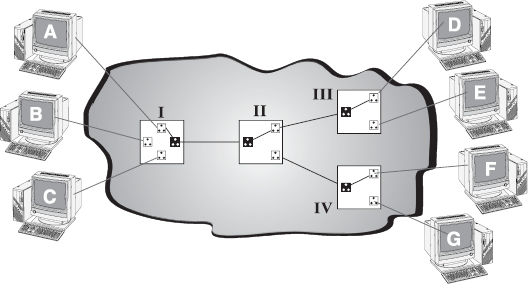
Figure 16.28 Circuit Switching
In circuit switching, data is transmitted with no delay (except for negligible propagation delay). This method is simple and requires no special facilities. Therefore, it is well suited for low-speed data transmission.
16.6.2 Packet Switching
Circuit switching was designed for voice communication. For example, in voice communication such as a telephonic conversation, once a circuit is established it remains busy for the duration of the conversation session. However, circuit switching is marred with many limitations such as in case of idle time (that is, if no data is communicated), the capacity of the link is wasted. This situation is addressed by packet switching.
Packet switching introduces the idea of breaking data into packets, which are discrete units of potentially variable length blocks of data. Apart from data, these packets also contain a header with control information like the destination address, priority of the message, and so on. These packets are passed by the source point to its local packet switching exchange (PSE). When the PSE receives a packet, it inspects the destination address contained in the packet. Each PSE contains a navigation directory specifying the outgoing links to be used for each network address. On receipt of each packet, the PSE examines the packet header information and then either removes the header or forwards the packet to another system. If the channel is not free, then the packet is placed in a queue until the channel becomes free. As each packet is received at each transitional PSE along the route, it is forwarded on the appropriate link mixed with other packets. At the destination PSE, the packet is finally passed to its destination. Note that not all packets of the same message, travelling between the same two points, will necessarily follow the same route. Therefore, after reaching their destination, each packet is put into order by a packet assembler and disassembler (PAD). Figure 16.29 shows that four packets (1, 2, 3, and 4) once divided on machine A are transmitted via various routes, which arrive on the destination machine D in an unordered manner. The destination machine then assembles the arrived packets in order and retrieves the information.
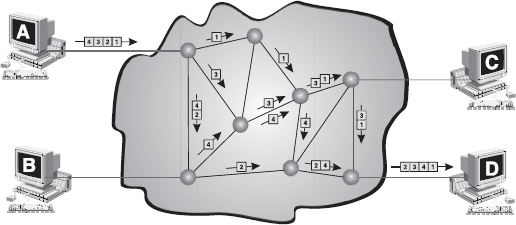
Figure 16.29 Packet Switching
The benefit of packet switching is that since packets are short, the communication links between the nodes are only allocated to transferring a single message for a short period while transmitting each packet. Longer messages require a series of packets to be sent, but do not require the link to be dedicated between the transmission of each packet. This also allows packets belonging to other messages to be sent between the packets of the original message. Hence, packet switching provides a much fairer and efficient sharing of the resources. In addition, if no data is available to the sender at some point during a communication, then no packet is transmitted over the network and no resources are wasted. Due to these characteristics, packet switching is widely used in data networks like the Internet.
16.6.3 Message Switching
Message switching technique employs the “store and forward” mechanism. In this mechanism, a special device (usually, a computer system with large storage capacity) in the network receives the message from a communicating device and stores it into its memory. Then, it finds a free route and sends the stored information to the intended receiver. In this kind of switching, a message is always delivered to one device where it is stored and then rerouted to its destination.
Message switching is one of the earliest types of switching techniques, which was common in 1960s and 1970s. As the delays in such switching are inherent (time delay in storing and forwarding the message) and a large capacity of data storage is required, this technique has virtually become obsolete (Figure 16.30).
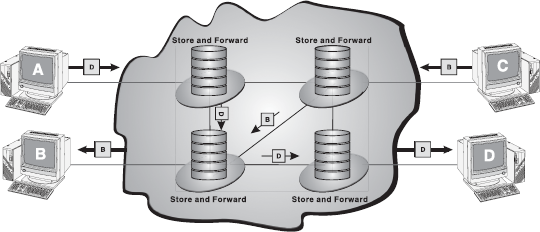
Figure 16.30 Message Switching
16.7 COMPUTER NETWORK
A computer network is a collection of two or more computers, which are connected together to share information and resources. The keyword in the definition is “sharing”—the main purpose of computer networking. The ability to share information efficiently is what gives computer networking its power and appeal. Envision a network as a project team. Through the efforts of all involved—the sharing of time, talent, and resources—a goal is accomplished or a project is completed.
Personal computers are powerful tools that can process and manipulate large amounts of data quickly, but they do not allow users to share that data efficiently. Before networks, users needed either to print documents or to copy files to a disk for others to edit or use them Figure 16.31(a). If others made changes o the document, there was no easy way to merge the changes. This is known as stand-alone environment. However, when two computers are linked together using a cable that allows them to share data, it is known as networked environment. Observe in Figure 16.31(b), the computers and other devices (like printers) are connected together through a cable. This is called a network and the concept of connected computers sharing resources is called networking. Note that computers in a network are interconnected by telephone lines, coaxial cables, satellite links, radio, and so on.
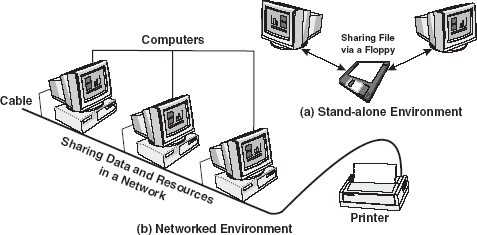
Figure 16.31 Stand-alone and Networked Environment
Technological advances in networking hardware and software have led to greater throughput on all scales and to increasingly tighter integration of networking with all aspects of computing. In tandem with these advances, the idea of networking has entered the common consciousness to an extent that would have been unimaginable a few years ago. This shift in perception has led to an expansion of networking beyond the workplace, which is already beginning to shape developments in networking technology.
Unlike operating system such as DOS that is designed for a single user to control one computer, network operating system (NOS) is an interconnected system of computing devices that provide shared and economical access to computer services. Thus, NOSs coordinate the activities of multiple computers across a network. NOSs are broadly divided into two types namely, client/server networks and peer-to-peer (P2P) networks.
Client/Server Network: In this network, each computer is either a client or a server. To complete a particular task, there exists a centralized host computer known as server and a user's individual workstation known as client. In simple words, client requests a service from the server and the server responds by providing that service. Note that a client/server network centralizes functions and applications in one or more dedicated file servers.
The servers provide access to resources, while the clients have access to the resources available on the servers. A typical example of client–server is sending an e-mail, where the e-mail is first transmitted to the source server. After this, the e-mail is transmitted to the destination server. Lastly, the destination server sends the e-mail to the client at the other end (Figure 16.32).
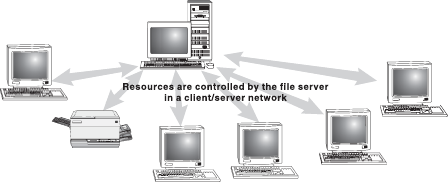
Figure 16.32 Client/Server Network
Generally, the server software runs on a computer, dedicated solely for hosting that software and supporting its services. On the other hand, client software runs on common personal computers or workstations. In a client/server relationship, both the client and server carry out some of the data processing on their ends. In the example, discussed earlier (e-mail) servers are responsible for transmitting the message, while client is responsible for sending and receiving the message.
P2P Network: A P2P network does not rely on dedicated servers for communication; instead, it uses direct connections between clients (peers). A pure P2P network does not have the notion of clients or servers, but only equal peer nodes that simultaneously function as both “clients” and “servers” to the other nodes on the network. That is, every node is able to initiate or complete any supported transaction (file transfer) with the other connected node (Figure 16.33).

Figure 16.33 P2P Networks
The upper limit of the number of nodes that can function as both clients and servers on a P2P network is between 10 and 25. If there are more nodes, then a P2P machine can be used as a dedicated server with additional high-performance hardware. Note that the peer nodes involved in the network may differ in local configuration, processing speed, network bandwidth, and storage quantity.
P2P networks have been designed primarily for small to medium LANs. Many file-sharing services such as Morpheus and Kaaza are used extensively to find files (sound, images, and videos) on the network. However, most of these file-sharing services actually integrate both P2P and client/server networking design. Therefore, these file-sharing applications are technically known as hybrid networks.
Generations in P2P Networks: P2P file-sharing networks can be classified according to their “generations,” which are based on the popular Internet-based file-sharing networks. These generations are listed below:
- First Generation: This generation had a centralized file list like Napster. In the United States of America, judiciary ruled that whoever controlled this centralized file list was responsible for any infringement of copyright, or any other illegal activities, which might occur while transferring files.
- Second Generation: This generation had decentralized file lists such as Gnutella and FastTrack. This was a necessary step for network creators, as a central authority (creators) will be held liable for copyright infringement.
- Third Generation: This generation is an improvement upon previous generations. These networks have in-built features such as efficiency, reliability, and anonymity. Examples of anonymous networks are Freenet, I2P, GNUnet, and Entropy. These networks allow only the known users (friends) to connect to your computer. After connecting, each node can forward requests and files anonymously between its own “friends” nodes.
Difference between P2P and Client/Server Network: Both P2P and client/server networks have associated advantages and disadvantages. These advantages and disadvantages form a part of distinction between the two. These differences are listed in Table 16.1.
Table 16.1 Difference between Peer-to-Peer Network and Client/Server Network
| Basis | P2P Network | Client/Server Network |
|---|---|---|
| Client/Server Network | No central repository for files and applications | Resources and data security controlled through the server |
| Maintenance | Low maintenance cost file | A large network requires extra staff to ensure efficient operation |
| Installation | Can be easily installed | Requires experts for proper installation of the network |
| Expensive | No need for a dedicated server, thus not much expensive | Expensive, as it requires a dedicated server |
| Security | Lack of proper drawback | Provides high level of security |
| Dependence | All nodes are independent of each other. Failure occurring in one node does not affect the functioning of other nodes in the network | When server goes down, it affects the functioning of the entire network |
16.7.1 Types of Computer Networks
A network can be as few as several personal computers on a small network or as large as the Internet, a worldwide network of computers. Today, when talking about networks, we are generally referring to three primary categories: LAN, metropolitan area network (MAN), and wide area network (WAN). These categories are defined depending upon various factors like the size of the network, the distance it covers, and the type of link used in interconnection.
LAN: A LAN is a computer network that covers only a small geographical area (usually within a square mile or less) such as an office, home, or building. In a LAN, connected computers have a NOS installed onto them. One computer is designated as the file server, which stores all the software that controls the network. It also stores the software that can be shared by the computers attached to the network. Other computers connected to the file server are called workstations. The workstations can be less powerful than the file server, and they may have additional software on their hard drives. On most LANs, cables are used to connect the computers. Generally, LAN offers a bandwidth of 10–100 Mbps (Figure 16.34).
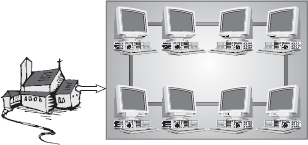
Figure 16.34 Local Area Network
MAN: A MAN is a network of computers spread over a “metropolitan” area such as a city and its suburbs. As the name suggests, this sort of network is usually reserved for metropolitan areas where the city bridges its LANs with a series of backbones, making one large network for the entire city. It may be a single network such as a cable television network or it may be a means of connecting a number of LANs. Note that MAN may be operated by one organization (a corporate with several offices in one city), or be shared and used by several organizations in the same city (Figure 16.35).
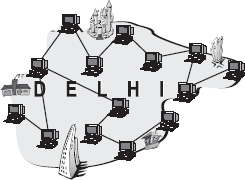
Figure 16.35 Metropolitan Area Network
WAN: A WAN is a system of interconnecting many computers over a large geographical area such as cities, states, countries, or even the whole world. These kinds of networks use telephone lines, satellite links, and other long-range communications technologies to connect. Such networks are designed to serve an area of hundreds or thousands of miles such as public and private packet switching networks and national telephone networks. For example, a company with offices in New Delhi, Chennai, and Mumbai may connect the LANs for each of those locations to each other through a WAN. Although a WAN may be owned or rented by private business, it is usually a public network designed to connect small-and intermediate-sized networks together. The largest WAN in existence is the Internet (Figure 16.36).
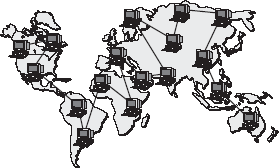
Figure 16.36 Wide Area Network
WAN offers many advantages to business organizations. Some of them are as follows:
- It offers flexibility of location because not all the people using the same data have to work at the same site.
- Communication between branch offices can be improved using e-mail and file sharing. It facilitates a centralized company-wide data backup system.
- Companies located in a number of small, interrelated offices can store files centrally and access each other's information.
16.8 NETWORK TOPOLOGIES
The term topology refers to the way a network is laid out, either physically or logically. A topology can be considered as the network's shape. It is the geometric representation of the relationship of all the links. There are five basic topologies: Bus, Ring, Star, Tree, and Mesh.
16.8.1 Bus Topology
Bus topology uses a common bus or backbone (a single cable) to connect all devices with terminators at both other. As the message passes each station, the station checks the message's destination address. If the address in the message matches the station's address, the station receives the message. If the addresses do not match, the bus carries the message to the next station, and so on. Figure 16.37 illustrates how devices such as file servers, workstations, and printers are connected to the linear cable or the backbone.
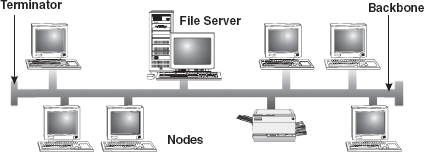
Figure 16.37 Bus Topology
Advantages of Bus Topology: The advantages of bus topology are:
- Connecting a computer or peripheral to a linear bus is easy.
- This topology requires least amount of cabling to connect the computers and, therefore, less expensive than other cabling arrangement.
- It is easy to extend a bus since two cables can be joined into one longer cable with a connector.
Disadvantages of Bus Topology: The disadvantages of bus topology are:
- Entire network shuts down if there is a failure in the backbone.
- Heavy traffic can slow down a bus because computers on such networks do not coordinate with each other to reserve time to transmit.
16.8.2 Ring Topology
In ring topology, computers are placed on a circle of cable without any terminated ends since there are no unconnected ends. Every node has exactly two neighbours for communication purposes. All messages travel through a ring in the same direction (clockwise or counter-clockwise) until it reaches its destination. Each node in the ring incorporates a repeater. When a node receives a signal intended for another device, its repeater regenerates the bits and passes them along the wire (Figure 16.38).
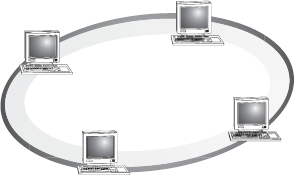
Figure 16.38 Ring Topology
Advantages of Ring Topology: The advantages of ring topology are:
- Ring topology is easy to install and reconfigure.
- Every computer is given equal access to the ring. Hence, no single computer can monopolize the network.
Disadvantages of Ring Topology: The disadvantages of ring topology are:
- Failure in any cable or node breaks the loop and can take down the entire network.
- Maximum ring length and number of nodes are limited.
16.8.3 Star Topology
In star topology, devices are not directly linked to each other, but they are connected via a centralized network component known as hub or concentrator. The hub acts as a central controller and if a node wants to send data to another node, it boosts up the message and sends the message to the intended node. This topology commonly uses twisted-pair cable; however, coaxial cable or fibre optic cable can also be used Figure 16.39
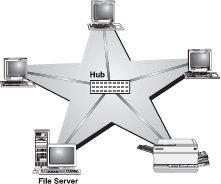
Figure 16.39 Star Topology
Advantages of Star Topology: The advantages of star topology are:
- Star topology is easy to install and wire.
- The network is not disrupted even if a node fails or is removed from the network.
- Fault detection and removal of faulty parts is easier in star topology.
Disadvantages of Star Topology: The disadvantages of star topology are:
- It requires a longer length of cable.
- If the hub fails, nodes attached to it are disabled.
- The cost of the hub makes the network expensive as compared to bus and ring topologies.
16.8.4 Tree Topology
A tree topology combines the characteristics of linear bus and star topologies. It consists of groups of star-configured workstations connected to a bus backbone cable. Not every node plugs directly to the central hub. The majority of nodes connect to a secondary hub that, in turn, is connected to the central hub. Each secondary hub in this topology functions as the originating point of a branch to which other nodes connect (Figure 16.40).
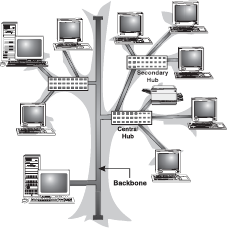
Figure 16.40 tree Topology
Advantages of Tree Topology: The advantages of Tree Topology are:
- The distance to which a signal can travel increases as the signal passes through a chain of hubs.
- Tree topology allows isolating and prioritizing communications from different nodes.
- Tree topology allows for easy expansion of an existing network, which enables organizations to configure a network to meet their needs.
Disadvantages of Tree Topology: The disadvantages of tree topology are:
- If the backbone line breaks, the entire segment goes down.
- It is more difficult to configure and wire than other topologies.
16.8.5 Mesh Topology
In a mesh topology, every node has a dedicated point-to-point link to every other node. Messages sent on a esh network can take any of several possible paths from source to destination. A fully connected mesh network has n(n - 1)/2 physical links to link n devices. For example, if an organization has five nodes and wants to implement a mesh topology, then 5(5 - 1)/2, that is, 10 links are required. In addition, to accommodate those links, every device on the network must have n - 1 communication (input/output) ports (Figure 16.41).
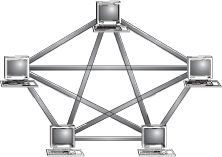
Figure 16.41 Mesh Topology
Advantages of Mesh Topology: The advantages of mesh topology are:
- The use of large number of links eliminates network congestion.
- If one link becomes unusable, it does not disable the entire system.
Disadvantages of Mesh Topology: The disadvantages of mesh topology are:
- The amount of cabling required is very large.
- As every node is connected to the other, installation and reconfiguration is very difficult.
- The amount of hardware required in this type of topology makes it expensive to implement.
16.9 COMMUNICATION PROTOCOL
Imagine yourself standing near a traffic crossing. You can notice that for smooth movement of the traffic, a functioning traffic light is essential. The red signal sends a message to stop, a yellow signal to wait, and a green signal to cross. This set of rules, which tells a driver when to move and when to stop, are traffic protocols. Similarly, computers adhere to certain protocols that define the manner in which communication takes place. A communication protocol is a set of rules that coordinate the exchange of information. If one computer is sending information to another and they both follow the same protocol, the message gets through, regardless of what types of machines they are and on what operating systems they are running. As long as machines have software that can manage the protocol, communication is possible.
16.9.1 The OSI Model
Open Systems Interconnectione (OSI) is the standard reference model for communication between two end-users in a network. In 1983, International Organization for Standardisation (ISO) published a document called “The Basic Reference Model for Open Systems Interconnection,” which visualizes network protocols as a seven-layered model. The model lays a framework for the design of network systems that allow for communication across all types of computer systems. It consists of seven separate but related layers, namely, physical, data link, network, transport, session, presentation, and application layer.
A layer in the OSI model communicates with two other OSI layers, the layer directly above it and the layer directly below it. For example, the data link layer communicates with the network layer and the physical layer. When a message is sent from one machine to another, it travels down the layers on one machine and then up the layers on the other machine. This route is illustrated in Figure 16.42. As the message travels down the first stack, each layer (except the physical layer) adds header information to it. These headers contain control information that are read and processed by the corresponding layer on the receiving stack. At the receiving stack, the process happens in reverse. As the message travels up the other machine, each layer strips off the header added by its peer layer.
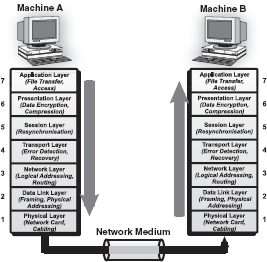
Figure 16.42 Message Transfer in Layered Architecture
Physical Layer: The physical layer defines the physical and electrical characteristics of the network. This layer acts as a conduit between computer's networking hardware and its networking software. It handles the transfer of bits (0s and 1s) from one computer to another. This is where the bits are actually converted into electrical signals that travel across the physical circuit. Physical layer communication media include various types of copper or fibre optic cable, as well as many different wireless medias.
Data Link Layer: The function of the data link layer is to provide service interface to the network layer and is responsible for error-free transmission and preventing the slow receivers from being overflow by the fast senders. To achieve this, the data link layer divides the packets received from the network layer into manageable form known as frames. These data frames are then transmitted sequentially to the receiver. On the receiver end, data link layer detects and corrects any errors in the transmitted data, which it gets from the physical layer.
Network Layer: The network layer is responsible for transporting traffic between devices that are not locally attached. For example, a router (a network layer device) provides the routing services in a network. When a packet is received on a router interface, the destination IP address is checked. If the packet is not destined for the router, then the router will look up the destination network address in the routing table. Once an exit interface is chosen, the packet will be sent to the interface to be framed and sent out on the local network. If the entry for the destination network is not found in the routing table, the router drops the packet.
Transport Layer: The basic function of the transport layer is to handle error recognition and recovery of the data packets. This layer establishes, maintains, and terminates communications between the sender and the receiver. At the receiving end, transport layer rebuilds packets into the original message, and to ensure that the packets arrived correctly, the receiving transport layer sends acknowledgments.
Session Layer: The session layer comes into play primarily at the beginning and end of a transmission. At the beginning of the transmission, it lets the receiver know its intent to start transmission. At the end of the transmission, the session layer determines if the transmission was successful. This layer also manages errors that occur in the upper layers such as a shortage of memory or disk space necessary to complete an operation, or printer errors.
Presentation Layer: The function of presentation layer is to ensure that information sent from the application layer of one system would be readable by the application layer of another system. This is the place where application data is packed or unpacked and is made ready to use by the running application. This layer also manages security issues by providing services such as data encryption and compresses data so that fewer bits need to be transferred on the network.
Application Layer: The application layer is the entrance point that programs use to access the OSI model and utilize network resources. This layer represents the services that directly support applications. This OSI layer is closest to the end-user. Application layer includes network software that directly serves the end-users of the netwrork by providing them user interface and application features like electronic mail, USENET, etc.
16.10 NETWORK DEVICES
Networks are becoming more complicated and more pervasive everyday. Terms like switch, router, gateway, and hub have become part of our everyday language, yet many people do not fully understand the differences between these devices or how to choose the right one for their network. These devices interconnect individual computers and ensure that they communicate efficiently. This section provides some background information on how each device works and gives some guidance in picking the right solution.
NIC: NIC is a hardware device that connects clients, servers, and peripherals to the network through a port. Most network interfaces come as small circuit board that can be inserted onto one of the computer motherboard's slots. Alternatively, modern computers sometimes include the network interface as part of their main circuit boards (motherboards). Each network interface is associated with a unique address called its media access control (MAC) address. The MAC address helps in sending information to its intended destination(Figure 16.43)

Figure 16.43 Network Interface Card
NICs are a major factor in determining the speed and performance of a network. It is a good idea to use the fastest network card available for the type of workstation one is using.
Repeater: A repeater is the most basic device on a network. Signals that carry information within a network can travel a fixed distance before attenuation endangers the integrity of the data. A repeater installed on the link receives signal, regenerates it, and sends the refreshed copy back to the link. Doing this means that the new signal is clean, free from any background noise introduced while travelling down the wire. In Figure 16.44, two sections in a network are connected by the repeater.
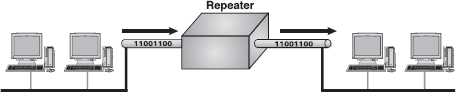
Figure 16.44 Repeater
Repeaters are most commonly used to extend a network cable. All network cable standards have maximum cable length specification. If the distance between two network devices is longer than this specification, a repeater is needed to regenerate the signal. Without the repeater, the signal will be too weak for the computers on each end to reliably understand. A good example of the use of repeaters would be in a LAN using a star topology with unshielded twisted-pair cabling. The length limit for unshielded twisted-pair cable is 100 m. The repeater amplifes all the signals that pass through it allowing for the total length of cable on the network to exceed the 100 m limit. Nonetheless, repeaters have no in-built intelligence and do not look at the contents of the packet as they regenerate the signal. Thus, there is no processing overhead in sending a packet through a repeater. This also means that a repeater will repeat any errors in the original signal.
Hub: A hub is a small box that connects individual devices on a network so that they can communicate with one another. The hub operates by gathering the signals from individual network devices, optionally amplifying the signals, and then sending them onto all other connected devices. Amplification of the signal ensures that devices on the network receive reliable information. A hub can be thought of as the centre of a bicycle wheel, where the spokes (individual computers) meet.
Nowadays, the terms repeater and hub are used synonymously, but they are actually not the same. Although at its very basic level, a hub can be thought of as a multi-port repeater. Typically, hubs have anywhere from 4 to over 400 ports. When a signal is received on one port of the hub, it is regenerated out to all the other ports. It is most commonly used to connect multiple machines to the same LAN. Administrators connect a computer to each port on the hub, leaving one port free to connect to another hub or to a higher-level device like a bridge or router.
Bridge: A bridge is a device that allows division of a large network into two or more smaller and efficient networks. It monitors the information traffic on both sides of the network so that it can pass packets of information to the correct location. Most bridges can “listen” to the network and automatically figure out the address of each computer on both sides of the bridge. It examines each packet as it enters though one of the ports. A bridge first looks at the MAC address of the sender and creates a mapping between the port and the sender's MAC address. It then looks at the address of the recipient, comparing the MAC address to the list of all learned MAC addresses. If the address is in the list, the bridge looks up the port number and forwards the packet to the port where it thinks the recipient is connected. If the recipient's MAC address is not in the list, the bridge then does a flood; it sends the signal to all the ports except the one from where it was received. As a result, a bridge reduces the amount of traffic on a LAN by dividing it into two segments. It inspects incoming traffic and decides whether to forward or discard it (Figure 16.45).

Figure 16.45 Bridge
Bridges can be used to connect networks with different types of cabling or physical topologies. They must, however, be used between networks with the same protocol. Since a bridge examines the packet to record the sender and lookups the recipient, there is overhead in sending a packet through a bridge. On a modern bridge, this overhead is miniscule and does not affect network performance.
Switch: A switch is a multi-port bridge. It connects individual devices on a network so that they can communicate with one another. The behaviour of a switch is the same as that of a bridge. It is capable of inspecting the data packets as they are received, determining the source and destination device of that packet, and forwarding that packet appropriately. The difference is that most switches implement these functions in hardware using a dedicated processor. This makes them much faster than traditional software-based bridges.
Router: A router is an essential network device for interconnecting two or more networks. Router's sole aim is to trace the best route for information to travel. As network traffic changes during the day, routers can redirect information to take less congested routes. A router creates and/or maintains a table, called a routing table that stores the best routes to certain network destinations. While bridges know the addresses of all computers on each side of the network, routers know the addresses of computers, bridges, and other routers on the network. Routers can even “listen” to the entire network to determine which sections are the busiest—they can then redirect data around those sections until they clear up (Figure 16.46).
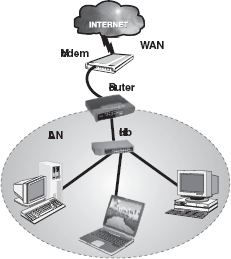
Figure 16.46 Router
Routers are generally expensive and difficult to configure and maintain. They are critical components of a network and if they fail, the network services will be significantly impaired. Most routers operate by examining incoming or outgoing signals for information at the network layer. In addition, they can permit or deny network communications with a particular network.
Gateway: A gateway is an internetworking device, which joins networks operating on different protocols together. It is also known as protocol converter. A gateway accepts the packet formatted for one protocol and converts the formatted packet into another protocol. It can be implemented completely in software, hardware, or as a combination of both. For example, a gateway can receive e-mail message in one format and convert it into another format. One can connect systems with different protocols, languages, and architecture using a gateway (Figure 16.47).
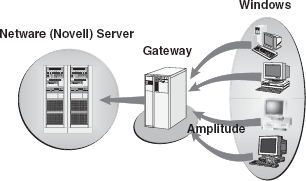
Figure 16.47 Gateway
Let Us Summarize
- Data communication is the exchange of data between two devices using some form of wired or wireless transmission medium. There are five basic components in data communication system: message, sender, receiver, medium, and protocol.
- Data transmission mode refers to the direction of signal flow between two linked devices. There are three types of transmission modes: simplex (unidirectional data flow), half-duplex (bi-directional data flow, but one at a time), and full-duplex (simultaneous bi-directional data flow).
- The data can be transmitted from one point to another by means of electromagnetic signals. These signals may be in one of the two forms: analog or digital. An analog signal is a continuous waveform that changes smoothly over time. Digital data refer to the data stored in the form of 0s and 1s.
- Bandwidth refers to the maximum volume of data that can be transferred over any communication medium at a given point of time. The more the data needed to be transmitted in a given period, the more is the bandwidth required.
- Transmission media refers to the physical media through which data can be transmitted from one point to another. It can be divided into two broad categories: guided/wired media and unguided/wireless media.
- There are three basic types of guided media: twisted-pair, coaxial cable, and optical fibre. Some commonly used unguided media of transmission include RF propagation, microwave transmission, satellite transmission, infrared wave transmission, Bluetooth, and Wi-Fi.
- Modulation refers to the process of superimposing the signals on a carrier wave by changing some of the wave's characteristics (such as amplitude, frequency, or phase) so that it is more suitable for transmission over the medium between transmitter and receiver. Generally, there are three forms of modulation: amplitude, frequency, and phase.
- Multiplexing is a technique used for transmitting several signals simultaneously over a single communication channel. Signals are multiplexed using two basic techniques: FDM and TDM.
- Asynchronous transmission refers to the data transmission of one character at a time, with intervals of varying lengths between transmittals, and with start bits at the beginning and stop bits at the end of each character, to control the transmission.
- Synchronous transmission is a method of communication in which data are sent in blocks, without the need for start and stop bits between each byte. Synchronization is achieved by sending a clock signal along with the data.
- Switching refers to routing traffic by setting up temporary connections between two or more network points. A temporary connection is achieved by devices located at different locations on the network, called switches. Switching traditionally employs three methods: circuit switching, packet switching, and message switching.
- A computer network is a collection of two or more computers, which are connected together to share information and resources. A network can be classified into three categories: LAN, MAN, and WAN.
- Topology refers to the way a network is laid out, either physically or logically. It is the geometric representation of the relationship of all the links. There are five basic topologies: bus, ring, star, tree, and mesh.
- OSI is a standard reference model for communication between two end-users in a network. It consists of seven separate but related layers, namely, physical, data link, network, transport, session, presentation, and application layer.
- To communicate over a network, a particular set of network devices such as NIC, repeater, hub, bridge, switch, router, and gateway are used. These devices interconnect individual computers and ensure that they communicate efficiently.
Exercises
Fill in the Blanks
- .................. is the exchange of data between two devices using some form of wired or wireless transmission medium.
- The three types of data transmission modes are.................., and ..................
- The maximum volume of data that can be transferred over any communication medium at a given point of time is known as..................
- In .................. modulation, the amplitude of a carrier wave is varied in accordance with the characteristic of the modulating signal.
- The communication technique, which combines several signals from different devices and transmits over a common medium, is called ..................
- The switching technique where messages are stored and then forwarded to the nearby communicating device is ..................
- A network spread around Los Angeles and its suburbs can be termed as .................. network.
- A tree topology combines characteristics of .................. and .................. topologies.
- The device, which joins networks operating on different protocols together, is ..................
- The device, ftted onto the computer's motherboard, which enables computer to communicate over the network, is ..................
Multiple-choice Questions
- The transmission mode which allows both communicating devices to transmit and receive data simultaneously is ..................
- Simplex
- Full duplex
- Half duplex
- None of these
- Which of the following medias does not come under the guided media?
- Optical fibres
- Coaxial cable
- Microwave
- Twisted Pair
- LAN stands for ..................
- Long area network
- Local area network
- Local audible network
- Limited area network
- A public switched telephone network (PSTN) uses .................. switching technique.
- Packet
- Message
- Circuit
- None of these
- The network topology in which devices are not linked to each other and where hub acts as a central controller is ..................
- Mesh topology
- Star topology
- Ring topology
- Tree topology
- In ring topology, each ..................
- Node is connected to exactly two others for communication purposes.
- Device is connected to a control unit; communication between one device and another must go through the central unit.
- Node in the ring incorporates a repeater.
- Both (a) and (c).
- The network device that connects two or more networks together and whose sole aim is to trace the best route for the information to travel is ..................
- Hub
- Gateway
- Switch
- Router
- Which of the following cables support the highest bandwidth and faster transmission rate?
- Fibre optic cable
- Coaxial cable
- UTP cable
- Twisted-pair cable
- A computer network, which provides long-distance transmission of data, images, and sound over a large distance, is ..................
- MAN
- WAN
- LAN
- VAN
- Identify the odd term out
- Router
- Switch
State True or False
- LANs operate within a wide area network.
- A telephone line can only send analog signals.
- In a bus topology, the communications channel consists of only one path for a message to travel to the destination.
- Twisted-pair cable is an example of unguided media for data communication.
- Hub is also called as protocol converter.
- Phase modulation is the encoding of information into a carrier wave by variation of its phase in accordance with an input signal.
- Coaxial cable can be easily tapped.
- Mesh topology involves minimum cabling.
- Optical fibre use copper wires for data transmission.
- In full-duplex transmission, both parties can communicate at the same time.
Descriptive Questions
- Write down the advantages and disadvantages of optical fibre.
- Differentiate:
- Time-division multiplexing and frequency-division multiplexing
- Guided and unguided media
- Asynchronous and synchronous transmission
- What is modulation? List its types.
- Explain any three guided and unguided data transmission media.
- What do you mean by computer network? Explain various types of computer networks.
- Explain three basic switching techniques used in the computer network.
- With the help of a diagram, explain various network topologies used to connect computers in a network.
- Describe the following network devices:
- Router
- Hub
- Gateway
- Bridge
ANSWERS
Fill in the Blanks
- Data communication
- Simplex, half duplex, full duplex
- Bandwidth
- Amplitude
- Multiplexing
- Message switching
- Metropolitan area
- Bus, Star
- Gateway
- Network interface card
Multiple-choice Questions
- (b)
- (c)
- (b)
- (c)
- (b)
- (d)
- (d)
- (a)
- (b)
- (c)
State True or False
- False
- True
- True
- False
- False
- True
- True
- False
- False
- True