CHAPTER 21
CYBERSECURITY
Protecting Cyberspace and Digital Technology
The next Pearl Harbor we confront could very well be a cyberattack that cripples our power systems, our grid, our security systems, our financial systems, our governmental systems…
Leon Panetta, shortly before becoming Secretary of Defense, 2011
CHAPTER OVERVIEW
The “next Pearl Harbor” has become something of a cliché, used over the years to describe a myriad of security threats. In some ways the phrase may also exaggerate the cybersecurity challenge, since most experts discount a near-term attack claiming thousands of lives in a matter of minutes. But in two important regards the analogy may actually underplay the seriousness of cyberattacks. First, unlike the terrible but localized strike on Pearl Harbor, a catastrophic surprise attack on cyber infrastructure could immediately impact citizens across the nation and world, with significant and poorly understood ramifications. Second, cyberattacks, both from criminals and enemy groups, are more than a potential hazard. They are already taking a substantial toll every day, from espionage to lost business productivity and stolen money.
Perhaps no other component of homeland security matches the technical, social, and strategic complications of cybersecurity. The cyber domain and the battle to secure it involve every critical infrastructure and the increasingly complex interdependencies among them. Cyberspace and digital technologies provide crucial tools to avoid and respond to human-made and natural disasters, while at the same time offering new means for terrorists to organize and strike. This chapter describes the nature of cyber threats, their impact, and means to mitigate them. It addresses systems and measures to protect government, commercial enterprises, and individuals from the malicious use of cyberspace and digital technologies.
CHAPTER LEARNING OBJECTIVES
After reading this chapter, you should be able to
1. Define key elements of cybersecurity.
2. Identify major categories of cyberattacks.
3. List common types of malicious software.
4. Outline various ways that terrorists use information technology.
5. Provide examples of safe computing practices.
THE THREAT
In the years after 9/11, cyberattacks on government agencies and large corporations grew in frequency and impact. Meantime, terrorist groups increased the sophistication of their interactive financing, organizing, and recruiting. Events during the years 2008 to 2010 removed any doubt about the cyber threat. During this period, massive distributed denial-of-service (DDoS) attacks swamped servers used by the governments of Estonia and the Republic of Georgia during disputes with Russia; thousands of classified U.S. government documents appeared on the Internet, courtesy of WikiLeaks and an alleged “insider” accomplice in the U.S. Army; mysterious software called Stuxnet damaged Iran’s uranium enrichment infrastructure; and well-trained intruders (said by U.S. officials to include Chinese and Russian experts) broke into classified federal networks and corporate sites, stealing government secrets, weapons plans, and corporate intellectual property. Meantime, criminal hackers penetrated more and more major consumer companies, demonstrating to huge numbers of Americans that their personal and financial information was at risk.
Now when experts warn of a “digital Pearl Harbor” that could result in significant financial damages or even loss of life, more and more Americans pay attention.
Definition
Cybersecurity can be defined as protecting digital information, property, and networks from theft, corruption, and natural disaster while at the same time keeping them accessible and productive for intended users.
Categories of Cyberattacks
Malicious activities in cyberspace can be divided into three major categories:
• Exploitation: This involves taking advantage of digital systems for nefarious reasons. It can include everything from the theft of credit card information by criminal hackers to widespread Internet espionage carried out by foreign intelligence services.
• Disruption: Whether from teenage coders vandalizing a web page or trained cyberwarriors taking down an enemy’s public communication sites, disruption involves degrading the operation of cyberassets.
• Destruction: The most serious form of cyberattack is destruction, which involves using digital assets to create physical, real-world damage, such as commandeering the control system at an electrical company to create a blackout.
INSIDER ATTACKS
Insiders include current or former members of an organization. It’s not surprising that insiders have been involved in many significant cyberattacks. They have the greatest access to computers and business records and thus are often in position to tamper with them. Adding to the danger is that many cybersecurity measures have focused on external threats, leaving internal access open or simply depending on the goodwill of employees to follow security regulations.
The character of insider threats varies considerably and can involve a range of motivations, from anger at superiors to greed. Attacks have commonly involved theft of data or sabotage of systems. In some cases, security violations may stem from benign motives that nonetheless create major risk, such as an employee who uses an unauthorized home computer to catch up on work. Insiders could also be instruments for conducting terrorist attacks, but coordinating a deliberate act of terror through an insider requires either recruiting or placing operatives with appropriate skills in positions of access. That said, foreign intelligence services have a proven record of placing agents in sensitive U.S. security positions. And since “self-radicalized” Americans have attacked an Army base and in several cases volunteered to bomb U.S. cities, they would certainly seem willing to sabotage IT systems if given the chance.
OUTSIDER ATTACKS
More and more malicious cyber intrusions are coming from outside, either from attackers within the United States or abroad. The overwhelming majority of these attacks occur through the Internet, which allows anyone, anywhere with the right capabilities to attack any system accessible through the web.
Most of this malicious activity takes the form of cybercrime, from identity theft to spamming. Surveys suggest the source of this activity is dynamic, which in part reflects the spread and influence of information technologies.
Many successful cyberattacks are conducted by individuals; any determined state or nonstate group can conduct significant malicious digital activity. Mastering skills to plan and conduct a rudimentary digital strike is not difficult. A vast amount of online material explains how to attack computer systems.
The rapid growth of organized cybercriminal groups is responsible for much turmoil online. Organizations not only mount and conduct significant operations, but also “rent” their services and even conduct their own research and development.
“Hacktivists” typically have ideological rather than pecuniary motives for hacking. For example, they may seek to disrupt or deface the website of a company or government organization with whose policies they disagree.
Of special concern is the increasing use of cyber tactics by nations for everything from economic espionage to actual attacks. Numerous countries have developed offensive cyber capabilities, in some cases including the ability to enlist cybercriminals in their activities.
MALICIOUS SOFTWARE
Cybersecurity includes the protection of hardware, including antitampering technologies and other programs to prevent contamination and exploitation of computer chips. However, most cyberattacks rely on malicious software, also known as malware, which can infect computers in a number of ways, with results ranging from simple vandalism to the theft of credit card information or valuable intellectual property. Sophisticated malware, combined with hacking, can include “trapdoor” or “backdoor” instructions to allow an attacker to gain access to a computer whenever he or she wishes. A malicious code could be a “Trojan horse” (code hidden in a legitimate program that directs unauthorized functions), a virus (a code that attacks single computers and often needs to be executed by a user to replicate itself), a worm (which infects multiuser systems and can spread by itself), or a “logic bomb” (a time-delayed virus that strikes well after it enters a computer system, sometimes based on a specific time period or action by the host system). Malware can propagate, directing an infected system to replicate attack instructions and forward them to other systems. This can involve a proxy, or “zombie” computer—which, without the owner’s knowledge, is enlisted as part of a huge “(ro)botnet” to overwhelm targets with a DDoS attack.
Malware can also allow an attacker to spy on a user, such as by monitoring keystrokes. A 2009 attack, nicknamed “GhostNet,” was reported to turn on a computer’s video camera and microphone without alerting the user.1
Other programs are designed to profit by e-commerce systems, such as “stealware,” which exploits traffic generation programs; or “adware,” which diverts users to unwanted advertising. When used at scale to infect massive numbers of users, these programs can generate substantial profits for their creators.
Extremely sophisticated attacks may be called advanced persistent threats (APT), in which an adversary targets and then gains control over a computer system for an extended period.
Malicious software has existed for years, from back when viruses spread on floppy disks carried from computer to computer. But the penetration of the Internet, used by much of the world’s population; expanding numbers of devices “at the edge” of networks, including mobile phones; increasing wireless connections; and trends such as “teleworking” have dramatically expanded the problem.
HUMAN ENGINEERING
Many forms of malware rely on human mistakes to spread, mistakes ranging from failing to install updated antivirus software to violating corporate security regulations. The process of tricking network users is called human engineering. It can be as simple as a hacker pretending to be a network administrator and calling users until he finds someone gullible enough to reveal a password, to a “Nigerian” scam, in which a stranger proposes a fast-money scheme via email. “Phishing” and the more targeted “spear phishing” involve sending fake messages from an apparently trusted source to trick users into providing personal information. A more sophisticated version of this tactic is “pharming,” in which a “phisher” creates a fake, or “spoofed,” website to fool users into believing they’re interacting with a legitimate site.
Another effective form of human engineering is “baiting.” This could involve an office worker finding a “lost” flash drive left in the cafeteria or restroom and then plugging it into a computer to find the rightful owner—never realizing the drive was contaminated with malware and intentionally left as bait
Human engineering can also be used against cyberattackers. “Honey pots” are systems intentionally left vulnerable in order to attract and catch hackers.
Purpose and Effects of Attacks
Digital attacks encompass everything from website vandalism driven by the animus of teenagers to cyberwarfare supporting strategic conflict between rival nation states.
Most cyberattacks are unsophisticated and easily defeated by basic security measures. But in unusual cases, even relatively modest digital strikes can inflict costly damage. The “Love Bug” worm, unleashed in 2000, caused millions of infections and up to an estimated $10 billion in damages and lost productivity.2
While some networks remain vulnerable to attacks or even mistakes by single individuals, penetrating modern, sophisticated, and well-protected systems can be a substantial undertaking, including the required financial investment. Despite such challenges, there have been more, and increasingly sophisticated, attacks, indicating that attackers are willing to commit substantial resources, and also that the level of resources required may in many cases be less than expected. Government officials have reported the massive, systematic theft of intellectual property from U.S. corporations and government agencies, including plans for advanced weapons. The Director of National Intelligence has cited an industry estimate that $1 trillion worth of intellectual property was lost to cybercrime in 2008 alone.3
Along with the threat of online financial loss is the danger of damage to offline, “real-world” critical infrastructure. Supervisory control and data acquisition (SCADA) systems, also known simply as “control systems,” use digital technology to control physical processes. Their widespread implementation in recent years has in some cases outrun sound security practices. SCADA attack scenarios are disturbing and numerous, especially now that software manages controls from huge industrial plants to the elevators, copiers, and sprinkler systems in many office buildings. Possible attacks include causing short circuits or other damage in the electrical grid, leading to blackouts; releasing deadly chemicals from refineries or chemical plants; disrupting air traffic control systems or even the operation of individual passenger jets dependent on “fly by wire” technology; gaining control of signal lights and associated systems to cause trains to crash or major commuter routes to gridlock; and wiping out financial data, preventing consumers from accessing online accounts and ATMs, disrupting the stock market, and preventing corporations from conducting transactions. There is even the possibility of using cyberattacks against life-saving medical equipment.
Such threats have been the subject of warnings, and even fodder for popular entertainment, for decades. Some observers claim the first major attack of this type was actually conducted in the 1980s by the United States, which let Soviet spies steal technology that had been secretly sabotaged, ultimately causinga major Russian pipeline explosion.4 However, in recent years the threat has appeared more and more concrete. The Stuxnet attack on Iranian nuclear facilities demonstrated the ability of software to cause machinery to damage itself. The 2010 attack apparently targeted centrifuges at the Natanz nuclear enrichment facility, using highly customized malware to disrupt a SCADA system, sending machines out of control. In the United States, government officials have confirmed probes against America’s electrical and financial systems, among others, along with massive numbers of attacks on military systems, including the penetration of the Pentagon’s “secret” network. Sophistication of attacks has also grown, as evidenced by the successful hack of RSA, a leading cybersecurity company, and the subsequent use of that stolen information to attack Lockheed Martin, America’s largest defense contractor.5
Even more dramatic details of cyberwarfare, including by China and Russia, apparently remain classified.
TERRORIST USE OF CYBERSPACE
The Internet is often thought of as a target for terrorists, but it is used far more frequently to support their activities. Today, active terrorist groups have an established presence on the Internet using hundreds of websites. These sites are used to serve terrorists and their support groups, communicate with potential supporters, and influence the international press. The Internet is sometimes called the “ultimate safe haven” for terrorists.
One use of the Internet is to conduct psychological warfare, or attempts to spread rumors, disinformation, and threats that will undercut public confidence and morale. For example, since the 9/11 attacks, al-Qaida has produced websites with frequent warnings of even larger impending attacks against the United States. The contents of the sites are often reported by the Western media, which in turn generates public worries. Web sites are also used to explain and justify terrorist activities. Al-Qaida has skilled video and interactive producers who create slick propaganda presentations, sometimes in English and targeted against Americans, which often distributed across the Internet by “jihobbyists” around the world. The same is true of videos showing terrorist beheadings of hostages and attacks on U.S. troops. The Basque separatist organization ETA, has maintained websites in several languages.
Terrorists also use the Internet as a vast library for obtaining and sharing information, in several cases gathering intelligence from public sources on potential targets. Websites disseminate important operational data, from tutorials on how to spread computer viruses to how to manufacture bombs and poisons.
Finally, terrorists employ the Internet to plan and coordinate operations. Gone are the days when enemy agents had no choice but to rely on secret transmitters or coded messages in foreign radio shows. Chat rooms, e-mail, and information posted both overtly and covertly on websites can carry instructions. These orders can be sent to trained operatives or even targeted directly at self-radicalized Americans. As discussed in Appendix A, U.S. homegrown violent extremism (HVE) has included Islamists who consumed terrorist propaganda online and sometimes communicated with al-Qaida figures via e-mail before attacks.
While terrorists are active on the Internet, so are U.S. and allied security officials. For example, a number of self-radicalized individuals have been identified by their online activity and then targeted by FBI “sting” operations. The U.S. intelligence community has also engaged in effective intelligence collection and operations on the Internet.
CYBER DEFENSE
Cyber defense covers a range of elements, including software, hardware, and human behavior. There are three main categories:
• Prevention: The first step is keeping opponents from launching an attack. In cyberwarfare against terrorists and nation states, this can involve deterring attack by the threat or initiation of offensive cyberstrikes or even physical attacks. Broader elements of defense common in commercial cybersecurity include improved software design (such as designing systems to “fail secure” rather than “fail insecure”), use of firewalls, proper access control and authentication (including ensuring that only approved people are allowed on systems to engage in authorized activities), and encryption (or encoding information to make it useless if stolen or intercepted). Increasingly, this entails protecting not just “data at rest,” such as information in databases, but also “data in transit” between devices or networks. The latter is increasingly important due to the proliferation of mobile computing and devices, wireless connections, and cloud computing. Prevention also includes the important but sometimes overlooked areas of training, for example to prevent employees from falling prey to human engineering, and physical security, which includes preventing unauthorized personnel from gaining access to computers and cabling (intelligence agents have been known to pilfer data from laptop computers left in hotel rooms).
• Detection: An attack that goes undetected can: continue (for example, stealing data over a protected period), be used against other systems (which have not been inoculated against a new method of attack), allow cybercriminals to take next steps in their acts (such as making unauthorized charges on a credit card), or simply lie in wait (as with a logic bomb—code designed to trigger a malicious function under certain circumstances). For these reasons, intruders often attempt to hide their actions from human operators and software systems. Intrusion detection systems (IDSs) are used to monitor and respond to improper attempts to access networks. Other technologies, such as deep-packet inspection and behavioral analysis, can recognize, and then work with other software to block, malicious software, even in massive data streams, before it can cause damage.
• Response: After an actual or attempted attack, response can include upgrading security (including across multiple systems, especially if the strike is a brand-new, or “zero-day,” attack against a specific type of software vulnerability); notification (for example, a company letting customers know their credit card information was stolen); or forensics, which can include determining how the attack was conducted and by whom.
Government Efforts
As with physical critical infrastructure, the United States has struggled with the appropriate allocation of government versus private sector roles in securing cyberspace. Cybersecurity strategy has included 2008’s National Security Presidential Directive 54/Homeland Security Presidential Directive 23 (NSPD–54/HSPD–23), which established the Comprehensive National Cybersecurity Initiative (CNCI) to safeguard executive branch information systems and assign responsibilities for major security objectives. The Obama administration added recommendations in 2009 and 2011, including guidance on both cybersecurity and the conduct of cyberwarfare by U.S. forces. Additional, classified presidential guidance was also issued.6
In general, the government has avoided assuming regulatory control, and security expense, for the vast cyber assets owned and operated by private entities. Instead, the Department of Defense has assumed cybersecurity missions for its organizations and domain (.mil), with support for security among companies comprising the civilian Defense Industrial Base (DIB). The Pentagon has also expanded its capabilities for warfare in the fifth domain of military action (land, sea, air, and space being the first four domains). The U.S. Cyber Command, along with subordinate commands at each military service, provides the ability to conduct “full-spectrum military cyberspace operations,” including offensive operations against adversaries’ cybersystems. Meanwhile, the Department of Homeland Security has been given increasing power to protect government cyber assets (.gov) while encouraging and supporting good security among private enterprises (.com). In general, private corporations that control the vast majority of America’s cyber assets have not been held to tight regulatory controls over security and have had to fund such activity themselves. Some observers criticize this system, noting that while other nations and terrorist groups threaten America’s private cyber assets, the U.S. government neither actively defends them nor requires them to meet strict security standards. To be sure, the owners of other, non-cyber critical infrastructures, from chemical companies to water utilities, also must maintain their own security. But those physical assets are much less likely to have foreign enemies penetrating them, critics note.
The Departments of Homeland Security and Defense—with it Cyber Command and National Security Agency (NSA), America’s largest intelligence agency and a long-time expert in the cyber domain—coordinate most U.S. government cybersecurity activity. DHS has the Office of Cybersecurity and Communications (CS&C), whose mission includes enhancing the security, resiliency, and reliability of America’s cyber infrastructure, and which also is the sector-specific agency for the IT and communications critical infrastructure sectors. The National Cyber Security Division (NCSD), under CS&C, works with public, private, and international entities to secure America’s cyber assets and execute the 2003 National Strategy to Secure Cyberspace. This includes implementing a cyber–risk-management program for critical infrastructure, issuing alerts and warnings, conducting a major cyber exercise, improving information sharing, responding to major incidents, and aiding in national-level recovery efforts.
US-CERT (Computer Emergency Response Team) is an operational arm of the NCSD, providing security for .gov cyber operations and collaborating with state and local governments and the private sector, including trade groups, Internet service providers (ISPs), security product and service providers, and other organizations participating in cyberattack watch, warning, and response functions. DHS, with assistance from the NSA, manages the “Einstein” series of network intrusion detection and attack prevention systems protecting many federal IT systems.
Another significant federal cybersecurity initiative is the Federal Information Security Management Act (FISMA), which requires federal agencies to conduct yearly reviews of their cybersecurity program and report the results. Under the law, the National Institute of Standards and Technology (NIST) developed cybersecurity standards and guidelines for many federal agencies.
Government Vulnerabilities
For all this effort, great vulnerability remains in public information systems. Federal agencies have repeatedly received poor grades for cyber-security, as judged by FISMA evaluators, “red teams” tasked to find vulnerabilities, and the evidence of actual attacks. Some challenges are systemic. The Department of Defense, for example, has implemented the strategy of “netcentric warfare” which often relies on commercial off-the-shelf systems (COTS) for computer needs. The department also depends on leased commercial telecommunications support. Thus, key elements of “secure” systems can be largely dependent on less secure public infrastructure, software, and equipment. The same is true for civilian agencies, which seek the operational, customer service, and cost efficiencies offered by commercial IT systems and cloud computing while trying to avoid security lapses.
Security among states and localities is even more questionable and preparedness varies greatly from region to region. Some state and local law enforcement agencies still lack high-end computer forensics training and capabilities needed to deal with computer attacks or other forms of electronic crimes, even though effective commercial systems are widely available.
THE ROLE OF THE PRIVATE SECTOR
Not just the owners of critical infrastructure, but institutions such as businesses, schools, and nonprofit organizations of all sizes can and should take precautions against cyberattack. Security experts generally agree on basic principles of a sound IT security program, which includes commonsense measures that even small companies can take to protect themselves.
Principles of Cybersecurity
Crucial to cybersecurity is applying solutions consistently across the organization. Gaps in security measures from either inadequate technologies or lax security practices leave an entire information system vulnerable to intrusion. In many cases, it only takes one weakness—in software, physical security or personnel—for a skilled attacker to gain access to everything.
The best way to validate and maintain security is through a risk-management program, a structured plan that makes sense for the organization based on its needs and available technology. Such a program includes implementing security awareness and training; establishing organization policies and regulations, instituting cooperative security management (such as arrangements with partners, ISPs, and contractors), implementing appropriate physical security measures (locks and guards), and adopting risk mitigation measures (including insurance and contingency planning) to ensure the continuity of operations and disaster recovery.
Steps for Protecting against Cyberthreats
Most cyberattacks can be stopped by basic security precautions, such as those below. They are within the budgets of even small companies, and most should be adopted by individuals and families as well.
Authentication and Password Protection
There are several ways for IT systems to determine which users are allowed access. In general terms, from the user’s perspective, these methods are based on something you know (a password, or in some cases, a picture the user recognizes or personal data he or she provides), something you have (a smart card or token), something you are (your fingerprint or retina scan), and somewhere you are (for example, inside the office versus an unknown location in a foreign country). These methods can be used singly or together (creating “two-factor authentication”).
FIGURE 21.1
GENERIC INDUSTRIAL CONTROL SYSTEM NETWORK ARCHITECTURE - SCADA
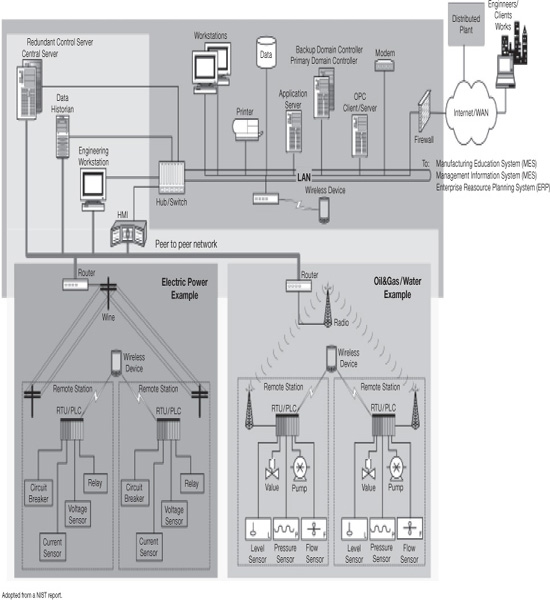
Of these methods, passwords are most basic and ubiquitous. They should be strong (in other words, complicated and not based on words, which can be hacked via “dictionary attacks”) and changed regularly. Employees should be trained to avoid sharing passwords or writing them down (an increasing temptation due to requirement to change them frequently and the sheer number of passwords people must recall for work and personal applications).
Software and Technical Defenses
Antivirus software is a requirement for all business and individual users. It should be loaded on every machine and updated frequently. Firewalls, which prevent threats from the public Internet getting into networks and computers, are another core precaution.
A fundamental but often neglected practice is updating existing software systems with security “patches” issued by software vendors.
Various hardware and software systems provide advanced security, including intrusion detection systems, advanced firewalls, permission control, and multi-domain access systems. Protective measures may be reinforced by network architecture, including such basic design as establishing an “air gap,” or physical separation, between networks. However, as with many other security measures, the effectiveness of an air gap depends on personnel following security rules.
Security Practices
The risk-management and security program should carefully consider the types of information and systems to be protected and the best means of doing so. This often starts with determining what access should be available to which personnel. Many employees may not be given “permissions” to change IT settings or access certain types of information, especially sensitive data such as proprietary intellectual property and personal information on customers (which in some cases must be safeguarded by law).
Employees should be trained on requirements and responsibilities for security, including how to avoid human engineering attacks, such as those discussed earlier. Required procedures could include deleting e-mail from unknown senders, avoiding certain types of outside sites, never downloading or executing software programs except those provided by the company, and following rules against transferring data from the company network to devices such as flash drives or CDs. Many security programs include refresher training on cybersecurity, as well as testing, compliance, monitoring, and audit programs to ensure personnel are meeting their responsibilities.
System administrators should also remove un-used software and user accounts, which can be used by hackers to gain access to the network.
Good physical security makes it harder for adversaries to gain access from the inside, where cybersecurity may be weaker. Intruders could tap into exposed data lines and steal information being carried through them, sabotage the network, or simply copy a password jotted on a “sticky note” under a keyboard. Given the amount of data now carried over wireless connections and the ability of technologies to detect emanations from electronic equipment, even the person in a van parked across a street could be stealing data.
For more and more enterprises, critical data and network connections walk out of the organization everyday in the laptops and mobile phones of employees. Encryption of data on mobile devices can limit damage if they’re stolen or lost; unauthorized users cannot open the information.
Likewise, hardware should be scrubbed of all data before being discarded (using specialized programs, since simply deleting data using factory-installed software does not always remove it from the system). Sophisticated hackers can recover personal and proprietary information from improperly discarded hard drives.
Backup
No matter how good the security, a cyberattack or disaster is possible, with disastrous results. Copying data and storing it off-site can protect against the loss or corruption of critical information, whether from software bugs, hackers, or natural disasters. Backup, via online services or data storage devices, is a basic best practice for enterprises and individuals alike.
RESILIENCE AND PROSPECTS FOR THE FUTURE
The “cat and mouse” contest between cybercriminals and their targets is evolving at a rapid pace. With each security patch comes the discovery of a new vulnerability. As digital technology enters more aspects of life—from Internet phone calls to “smart houses” and computer-equipped cars—new opportunities arise for exploitation.
Not all risk is from malevolent actors. Natural and human-made disasters threaten America’s interconnected digital systems as well.
A key imperative from the “all-threats” perspective is resilience. Just as the original Internet was designed to avoid a single point of failure, government agencies, businesses, and households must ensure their operations can recover despite attack or disaster. The prudent owner of cyber assets must continually ask the question “What if …?”
CHAPTER SUMMARY
Cyberthreats are real. While the near-term risk of catastrophic attack on the level of WMD is debatable, criminals, foreign nations, and terrorists are already using the Internet and other information technologies to steal money, loot intellectual property, and destroy physical systems. While both public and private sectors have undertaken initiatives to improve cybersecurity, much remains to be done. The first step for most Americans is to take basic, commonsense cybersecurity precautions.
CHAPTER QUIZ
1. What are common ways terrorists use the Internet and digital technology?
2. List major categories of cyberattacks.
3. Define a “logic bomb.”
4. Who is primarily responsible for protecting commercial components of cyberspace?
5. Describe basic methods for individuals and organizations to protect their information technology systems.
NOTES
1. Peter Ford, “Google Is Latest Target of Aggressive Hacking From China,” The Christian Science Monitor, January 13, 2010, at: http://www.csmonitor.com/World/Asia-Pacific/2010/0113/Google-is-latest-target-of-aggressive-hacking-from-China
2. Mark Landler, “A Filipino Linked to ‘Love Bug’ Talks About His License to Hack,” The New York Times, October 21, 2000 at: http://www.nytimes.com/2000/10/21/business/a-filipino-linked-to-love-bug-talks-about-his-license-to-hack.html
3. Remarks by James R. Clapper Director of National Intelligence at the Open Hearing on the Worldwide Threat Assessment, House Permanent Select Committee on Intelligence, February 10, 2011, at: http://www.dni.gov/testimonies/20110210_testimony_hpsci_clapper.pdf
4. “War in the Fifth Domain,” The Economist, July 1, 2010, at: http://www.economist.com/node/16478792?story_id=16478792
5. Julianne Pepitone, “RSA Offers To Replace All SecurID Tokens After Hack Attack,” CNN Money Tech, June 8, 2011 at http://money.cnn.com/2011/06/08/technology/securid_hack/index.htm
6. GAO 11–75, Defense Department Cyber Efforts, DOD Faces Challenges In Its Cyber Activities, General Accountability Office, July 2011.
