Now that we have both the install and scan roles completed, we can run our first scan. The only file we have not covered yet is the site.yml one; this one looks like slightly different to the ones we have been using in other chapters:
---
- hosts: scap
gather_facts: true
become: yes
become_method: sudo
vars_files:
- group_vars/common.yml
roles:
- { role: install, tags: [ "scan" ] }
- { role: scan, tags: [ "scan" ], report_name: "01-initial-scan" }
As you can see, we are tagging the roles as well as passing a parameter when running the scan. For now, we are just going to run playbook without using any tags. To run the playbook, issue the following command:
$ ansible-playbook -i production site.yml
This will give us the following results:
PLAY [scap] ****************************************************************************************
TASK [Gathering Facts] *****************************************************************************
ok: [box1]
TASK [install : install the packages needed] *******************************************************
changed: [box1] => (item=openscap-scanner)
changed: [box1] => (item=scap-security-guide)
TASK [scan : run the openscap scan] ****************************************************************
fatal: [box1]: FAILED! => {"changed": true, "cmd": ["oscap", "xccdf", "eval", "--profile", "xccdf_org.ssgproject.content_profile_pci-dss", "--fetch-remote-resources", "--results-arf", "/tmp/box1_results_01-initial-scan.xml", "--report", "/tmp/box1_report_01-initial-scan.html", "/usr/share/xml/scap/ssg/content/ssg-centos7-ds.xml"], "delta": "0:01:03.459407", "end": "2018-05-16 08:17:50.970321", "msg": "non-zero return code", "rc": 2, "start": "2018-05-16 08:16:47.510914", "stderr": "Downloading: https://www.redhat.com/security/data/oval/com.redhat.rhsa-RHEL7.xml.bz2 ... ok", "stderr_lines": ["Downloading: https://www.redhat.com/security/data/oval/com.redhat.rhsa-RHEL7.xml.bz2 ... ok"], "stdout": "Title Ensure Red Hat GPG Key Installed Rule xccdf_org.ssgproject.content_rule_ensure_redhat_gpgkey_installed Result pass Title Ensure gpgcheck Enabled In Main Yum " xccdf_org.ssgproject.content_rule_chronyd_or_ntpd_specify_multiple_servers", "Result", " pass"]}
...ignoring
TASK [scan : download the html report] *************************************************************
changed: [box1]
PLAY RECAP *****************************************************************************************
box1 : ok=4 changed=3 unreachable=0 failed=0
I have truncated the scan results in this output, but when you run it, you will see a large section of failed output colored red. As already mentioned, this is to be expected and is nothing to worry about.
A copy of the HTML report for our initial scan should be on your Ansible controller now; you can open it in your browser with the following command:
$ open generated/box1_report_01-initial-scan.html
Or, open the generated folder and double-click on box1_report_01-initial-scan.html:
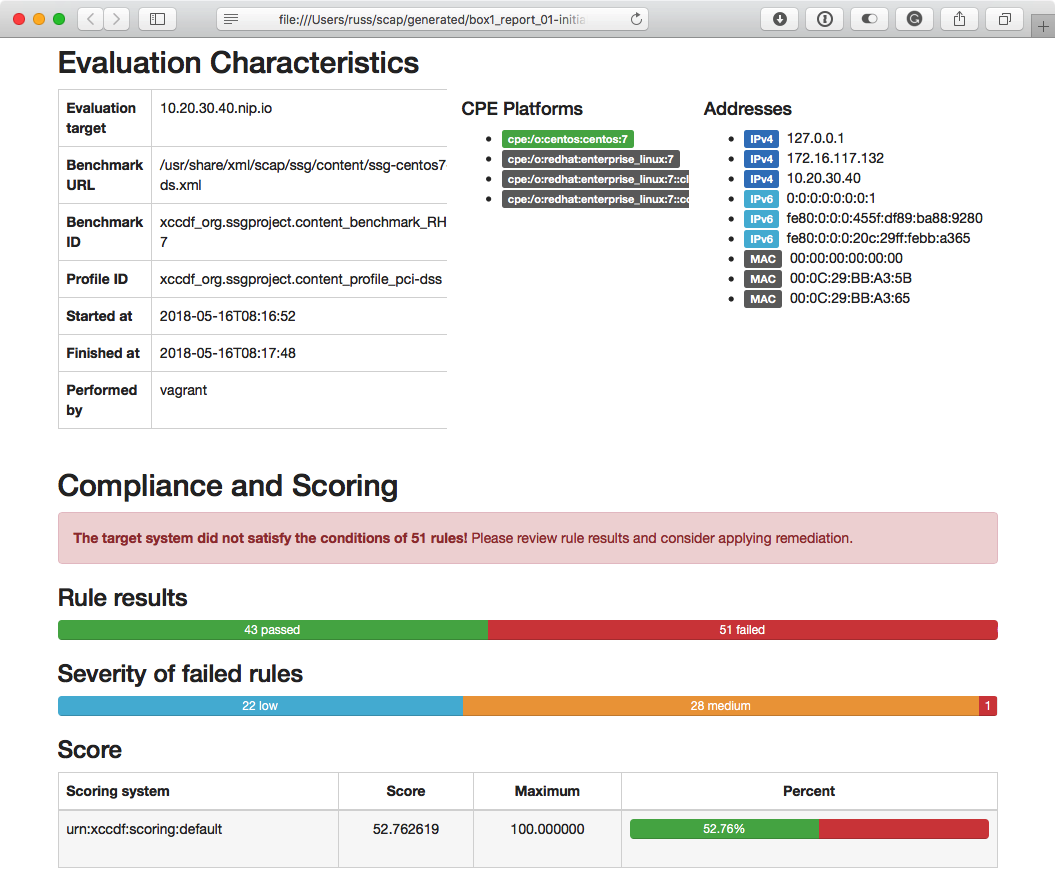
As you can see from the example, our host failed 51 of the 94 checks OpenSCAP ran. Let's look at doing something about getting that number of failed checks down.
