So far, we haven't had to put any hardcoded fixes in place to resolve any of the problems found in the scans. We have had to create a few files and folders to allow the fixes to be applied, but that was more to let the automated remediation work, rather than a fix.
At the time of writing, there are known issues with two of the five problems that are currently showing on my scans; these are:
- xccdf_org.ssgproject.content_rule_audit_rules_privileged_commands
- xccdf_org.ssgproject.content_rule_audit_rules_login_events
There are fixes being worked on. You can find them on Red Hat's Bugzilla at:
- https://bugzilla.redhat.com/show_bug.cgi?id=1570802
- https://bugzilla.redhat.com/show_bug.cgi?id=1574586
So, leaving these two to one side, there are three I can fix now. To do this, I am going to create a separate role and playbook, as by the time you read this, the following fixes may not be needed:
$ ansible-galaxy init roles/final-fixes
Jumping straight into roles/final-fixes/tasks/main.yml, our first fix is to rotate the logs daily rather than weekly, which is the default. To do this, we will use the lineinfile module to replace weekly with daily:
- name: sort out the logrotate
lineinfile:
path: "/etc/logrotate.conf"
regexp: "^weekly"
line: "daily"
The next task adds a fix that should make its way through to the scap-security-guide package at some point:
- name: add the missing line to the modules.rules
lineinfile:
path: "/etc/audit/rules.d/modules.rules"
line: "-a always,exit -F arch=b32 -S init_module -S delete_module -k modules"
As you can see, here, we are using the lineinfile module again. This time, we are adding a line to /etc/audit/rules.d/modules.rules if it is not already present. This adds a rule that takes into account 32-bit kernels, as well as the 64-bit ones, which the remediation scripts already configured.
Next, we are adding a fix for a script that should have been executed during the bash script execution. First of all, we need to create a file using the file module:
- name: add file for content_rule_file_permissions_var_log_audit
file:
path: "/var/log/audit/audit.log.fix"
state: "touch"
We then need to copy and then execute the portion of the bash script that failed when we first ran it:
- name: copy the content_rule_file_permissions_var_log_audit.sh script
copy:
src: "content_rule_file_permissions_var_log_audit.sh"
dest: "/tmp/content_rule_file_permissions_var_log_audit.sh"
- name: run the content_rule_file_permissions_var_log_audit.sh script
command: "bash /tmp/content_rule_file_permissions_var_log_audit.sh"
The bash script itself can be found at roles/final-fixes/files/content_rule_file_permissions_var_log_audit.sh, and it looks like this:
if `grep -q ^log_group /etc/audit/auditd.conf` ; then
GROUP=$(awk -F "=" '/log_group/ {print $2}' /etc/audit/auditd.conf | tr -d ' ')
if ! [ "${GROUP}" == 'root' ] ; then
chmod 0640 /var/log/audit/audit.log
chmod 0440 /var/log/audit/audit.log.*
else
chmod 0600 /var/log/audit/audit.log
chmod 0400 /var/log/audit/audit.log.*
fi
chmod 0640 /etc/audit/audit*
chmod 0640 /etc/audit/rules.d/*
else
chmod 0600 /var/log/audit/audit.log
chmod 0400 /var/log/audit/audit.log.*
chmod 0640 /etc/audit/audit*
chmod 0640 /etc/audit/rules.d/*
fi
Finally, we need to create a playbook file called final-fixes.yml. This should run the role we have just created and then run a final scan:
---
- hosts: scap
gather_facts: true
become: yes
become_method: sudo
vars_files:
- group_vars/common.yml
roles:
- { role: final-fixes }
- { role: scan, report_name: "04-final-fixes" }
To run the playbook, use the following command:
$ ansible-playbook -i production final-fixes.yml
This will give the following results:
PLAY [scap] *************************************************************************************
TASK [Gathering Facts] **************************************************************************
ok: [box1]
TASK [final-fixes : sort out the logrotate] *****************************************************
changed: [box1]
TASK [final-fixes : add the missing line to the modules.rules] **********************************
changed: [box1]
TASK [final-fixes : add file for content_rule_file_permissions_var_log_audit] *******************
changed: [box1]
TASK [final-fixes : copy the content_rule_file_permissions_var_log_audit.sh script] *************
changed: [box1]
TASK [final-fixes : run the content_rule_file_permissions_var_log_audit.sh script] **************
changed: [box1]
TASK [scan : run the openscap scan] *************************************************************
fatal: [box1]: FAILED! =>
...ignoring
TASK [scan : download the html report] **********************************************************
changed: [box1]
PLAY RECAP **************************************************************************************
box1 : ok=8 changed=7 unreachable=0 failed=0
Open the report that was generated using the following command:
$ open generated/box1_report_04-final-fixes.html
This shows us that there are just the two medium checks with known issues that are still failing:
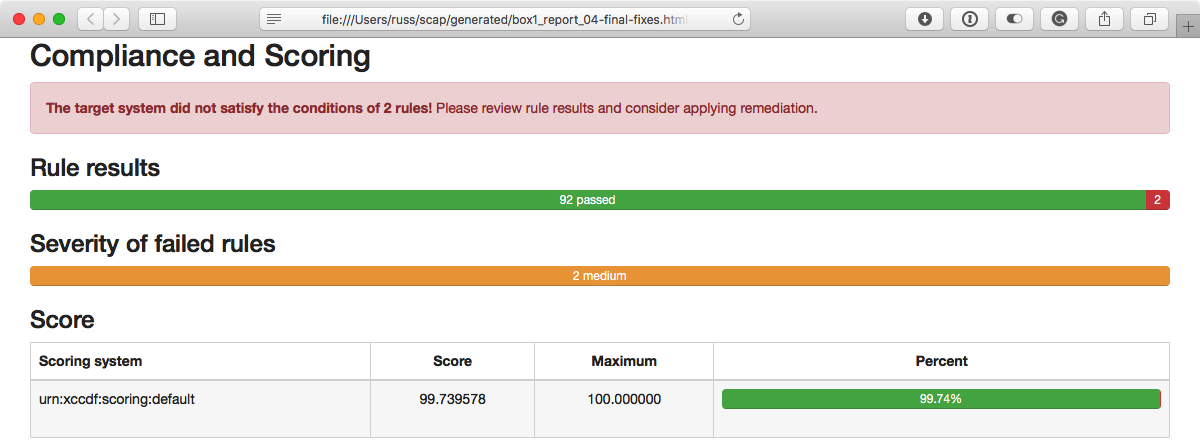
Hopefully, by the time you are reading this, your hosts will be getting a clean bill of health and this last section won't be needed, which is why I split it off from the main site.yml playbook.
