Chapter 12: Discovering ICMP
Everyone is familiar with the Internet Protocol (IP), which is responsible for routing and addressing traffic. However, many are not as familiar with the Internet Control Message Protocol (ICMP), a powerful protocol that plays a major role in delivering data. In this chapter, we'll learn about ICMP, the companion protocol to IP, which works in the network layer of the OSI model. We'll begin with an overview so that you have a general understanding of the main functions of ICMP.
We will then evaluate both ICMP (used with IPv4) and ICMPv6 (used with IPv6) so that you can compare some of the main differences. In addition, you'll get a better understanding of the two types of messages: error reporting and queries. We'll then look at common type and code values, along with a discussion on which types of ICMP messages are no longer used. We'll finish with a discussion on how malicious actors can use ICMP to launch an attack. Then, we'll outline some basic firewall guidelines in terms of what types of ICMP messages to allow on your network.
This chapter will address all of this by covering the following:
- Understanding the purpose of ICMP
- Dissecting ICMP and ICMPv6
- Sending ICMP messages
- Evaluating type and code values
- Configuring firewall rules
Understanding the purpose of ICMP
Early in the 1980s, scientists developed protocols that drove internet traffic. In addition, they identified potential issues that might prevent traffic from reaching its destination, especially when using IP. This is mainly because IP doesn't guarantee delivery and has no way of communicating network problems with end devices. ICMP overcomes the deficiencies of IP by sending query messages and generating error reports on possible issues that may require attention.
As shown in the following table, the network layer is responsible for addressing and routing:
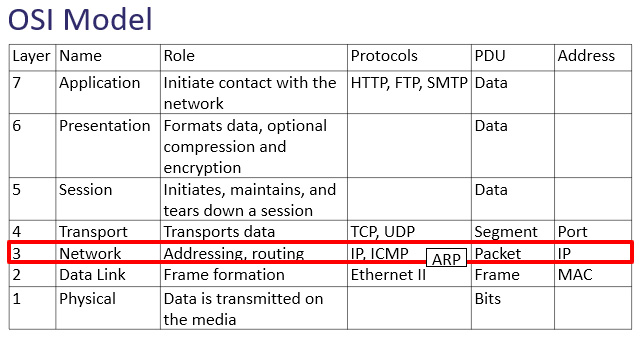
Figure 12.1 – The OSI model network layer
The network layer has three main protocols, which are essential in delivering data. In addition to ICMP, the other protocols are as follows:
- IP is a best-effort, connectionless protocol that routes packets from source to destination using a logical IP address.
- Address Resolution Protocol (ARP) resolves an IPv4 address (network layer) to a Media Access Control (MAC) (data link layer) address on a local area network (LAN) so the frame can be delivered to the appropriate host.
As we learned in Chapter 11, Analyzing IPv4 and IPv6, the network layer is responsible for addressing and routing traffic. Because IP is a best-effort, unreliable protocol, ICMP is essential for data delivery and must be implemented by every IP module.
- Communicate errors that prevent data delivery. Common issues include the network or port being unreachable.
- Issue queries such as an echo request/reply, which is used in the ping network utility, or router solicitation, which provides a way to solicit and receive router information.
As there are two IP versions, there are also two versions of ICMP. These have roles that are specific to their respective IP version:
- IPv4 uses ICMP.
- IPv6 uses ICMPv6.
Because of its role in assisting IP in delivering data, the use of ICMP is made clear in the Request for Comments (RFC) for both versions of ICMP as follows:
- As stated in RFC 792, "ICMP is actually an integral part of IP, and must be implemented by every IP module."
- As stated in RFC 4443, "ICMPv6 is an integral part of IPv6, the base protocol must be fully implemented by every IP version six node."
To communicate either queries or errors, an ICMP message must provide information within the header. In the next section, we'll see how an ICMP packet follows the IP header, along with the three fields that are present in both versions.
Understanding the ICMP header
When communicating information, both ICMP and ICMPv6 packets will follow an IP packet, as shown in the following diagram:

Figure 12.2 – ICMP message following an IP header
All ICMP messages have a common structure that begins with the type, code, and checksum, as shown along the top of the following diagram:

Figure 12.3 – ICMP message
The three fields consistent in an ICMP header are described as follows:
- Type (8-bit): This field indicates the type, such as Type: 3 (Destination unreachable).
- Code (8-bit): The code field further defines the type field. For example, Code: 1 (Host unreachable).
- Checksum (16-bit): This field holds a numeric value used for error detection.
Following the type, code, and checksum field values, you'll find the data payload. The contents will depend on the ICMP type and code, which can be either an ICMP error report or query message.
The entire payload is encapsulated in a frame, as shown in the following diagram:
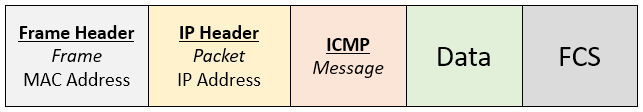
Figure 12.4 – ICMP message in an Ethernet II frame
Here we see the various headers, which include the frame header, IP header, ICMP message, data, and Frame Check Sequence (FCS).
Note
ICMP does not have a transport layer header, as it does not exchange or transport data. Its primary role is to test for reachability and report transmission errors.
To examine several examples of ICMP in detail, we will use the bigFlows.pcap packet capture found at http://tcpreplay.appneta.com/wiki/captures.html#bigflows-pcap. Download the file and open it in Wireshark. Once open, apply the icmp filter. Select any of the ICMP packets and you will see the Type, Code, and Checksum fields. As shown here, we see the specifics of Frame 202:

Figure 12.5 – Frame 202 - ICMP message
In the frame details, we see the following:
- Ethernet II: Frame header
- Internet Protocol Version 6: IP header
- Internet Control Message Protocol: Message
- Data: Specific to an ICMP echo reply
As shown in Figure 12.5, the details for this type of ICMP message include fields for identifiers and sequence numbers that help to match corresponding echoes and replies. This information is used by the host to reconstruct the process that sent the original datagram.
After the Type, Code, and Checksum fields, there is a data portion within the ICMP message. The following section explains what you might find in the data payload.
Investigating the data payload
In an ICMP datagram, the payload is dependent on the type of message. In a standard ICMP request/reply, the data payload is meaningless and will have either ASCII characters or NULL values, depending on the Operating System (OS).
In this section, we'll explore the different payloads you might encounter in an ICMP packet. In addition to data, an ICMP payload can include a watermark, or even evidence of concealed data, such as what you might see in a Loki attack.
Let's start with reviewing what you might see in an ICMP echo request.
Viewing an echo request/reply
To see an example of an echo request, open bigFlows.pcap, and then go to Frame 38, which shows a Type 8, Code 0 message. Expand the ICMP header, as shown in the following screenshot:

Figure 12.6 – ICMP echo request details
For example, in the echo reply shown in Frame 38 the data portion is a string of characters as follows:
00000000138a1a34abcdabcdabcdabcdabcdabcdabcdabcdabcdabcdabcdab cdabcdabcd
In addition, you should see a similar payload in a standard ICMP reply, which you can see in Frame 74.
While in an echo request/reply you will see a string of characters, an error message has a different format for the payload. Let's take a look.
Reporting an error
Whenever ICMP encounters an error, ICMP must return the IP header, plus at least the first 8 bytes (or 64 bits) of the original datagram, to the sender.
Note
The whole length of an ICMP error message cannot exceed 576 bytes.
To see an example, open bigFlows.pcap and use the icmp.type == 3 filter, which will display all ICMP packets with a Type 3: Destination unreachable error message.
Select Frame 4794 and expand the ICMP header where you will see the ICMP Type: 3 (Destination unreachable) Code: 3 (Port unreachable) fields, as shown here in the first section:
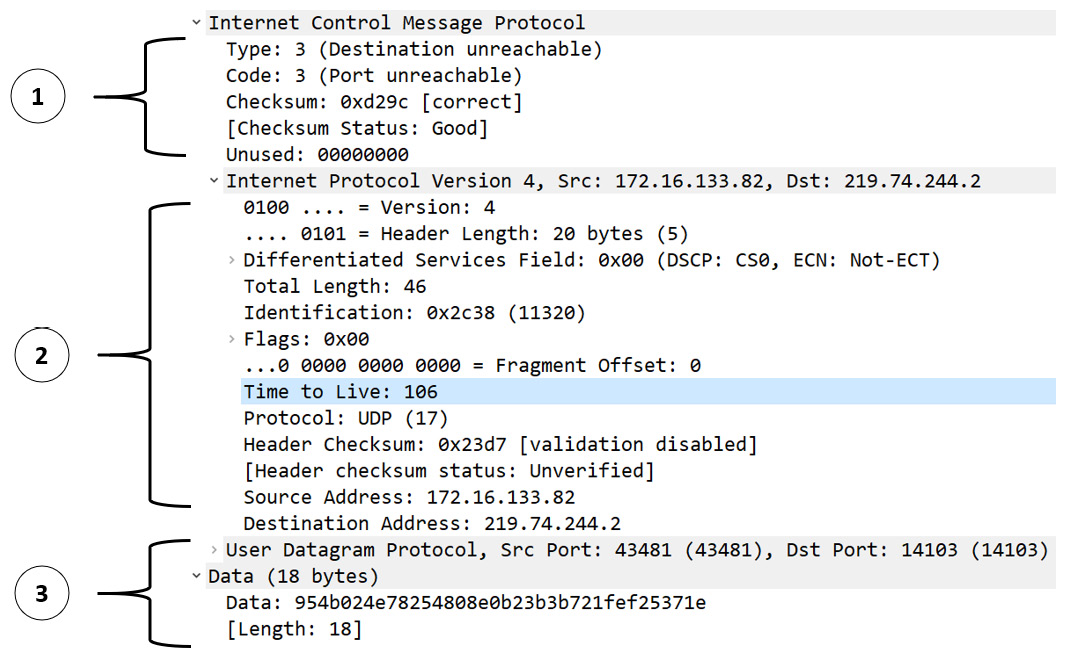
Figure 12.7 – ICMP echo request details
Because this is an error, ICMP has returned the IP header and the original datagram. As you can see, there are several parts to the ICMP packet, as follows:
- The first section (1) is the ICMP header indicating an error.
- The second section (2) is the original IP header.
- The third section (3) is the original User Datagram Protocol (UDP) header followed by the data.
In most cases, the only ICMP payload you might encounter is an echo request/reply along with error messages. However, there are other instances in which you might see a payload. Let's explore when this might happen.
Including other data
ICMP was designed to issue queries and communicate errors on a network. However, over time, ICMP has been used for other purposes, as the data portion in an ICMP request can be modified. One way is by using a non-malicious watermark to identify a company while monitoring the network. Another way is the malicious intent to exfiltrate data by using an ICMP tunnel.
Let's start by seeing how a watermark is used.
Creating a watermark
Paessler, a network monitoring company (https://www.paessler.com/ping-monitoring), uses ping monitoring to assess the health of the devices on the network. When gathering packets while in Wireshark, you'll see that Paessler's packets have a watermark, as shown in the following screenshot:

Figure 12.8 – Ping request with a watermark
In the Packet Bytes panel, you can see in the lower right-hand side an area that is highlighted. The data is as follows: P•I•N•G• •b•y• •P•R•T•G• •N•.
In this case, the watermark is not malicious. However, an ICMP packet can be modified to send data covertly, as we'll see next.
Sending commands covertly
Malicious actors have found numerous ways to conceal their activity. One way to send commands through a network is by using a Loki tool to execute a covert channel attack, which works in the following manner:
- Data is embedded within an ICMP echo packet.
- The data is then covertly sent through the network.
Instead of the watermark as described in the previous section, this type of activity poses a security risk. As a result, the network administrator should tune devices to enable the inspection of ICMP data. If found, the device should send an alert if the payload contains an unrecognized data pattern, as this may be an indication of a covert ICMP tunnel.
We can now see that ICMP is an essential network layer protocol that is used alongside both IPv4 and IPv6 to provide error reporting and informational messages. Next, let's compare the two versions, ICMP and ICMPv6.
Dissecting ICMP and ICMPv6
Although IPv4 and IPv6 are both responsible for routing and addressing data, the two protocols have a number of differences. As a result, there are two versions of ICMP.
In the next section, we'll explore ICMP alongside ICMPv6 so that you understand some of the basic roles and functions in reporting network issues.
Let's start with ICMP, which is used with IPv4.
Reviewing ICMP
ICMP is used alongside IPv4 to communicate network issues that prevent data from being delivered. ICMP error and query messages can alert end systems when there are issues with connectivity and can also obtain diagnostic information from intermediary systems, such as the round-trip time.
As powerful as ICMP is, it cannot make IP a reliable protocol; it only assists in data delivery by providing error messages and information. There are times when the causes of delays in data transmission are outside of the messages that ICMP can send and report. In that case, it's up to the Transmission Control Protocol (TCP), or other higher-layer protocol, to notify the host of transmission errors during delivery.
Next, let's take a look at ICMPv6, which has many of the same functions but also provides additional roles to support IPv6.
Outlining ICMPv6
While IPv4 and IPv6 are similar in terms of their overall functions, IPv6 has many additional benefits, which include the following:
- Options and extensions
- Improved multicast routing
- StateLess Address AutoConfiguration (SLAAC)
As a result, ICMPv6 was developed for IPv6 and is used to communicate updates or error messages. An ICMPv6 message contains the Type, Code, and Checksum details, followed by the contents, which will depend on the type and the code. However, ICMPv6 has options related to IPv6 traffic.
One example is an ICMPv6 router solicitation message, which alerts other routers on the network of their presence. To see an example of ICMPv6 messages communicating to other devices on the network, go to CloudShark: https://www.cloudshark.org/captures/0f90f2c2de86?filter=frame%20and%20eth%20and%20ipv6%20and%20icmpv6.
Download and open test55.pcap in Wireshark. In the display filter, enter icmpv6 and press Enter to run the filter. In the following screenshot, Frame 63 has an ICMPv6 router solicitation message:

Figure 12.9 — ICMPv6 router solicitation
Note
The IPv6 ff02::2 destination address is a multicast address, which are delivered to all nodes on a network using a single address.
Both ICMP and ICMPv6 can provide insight into network activity. The next section explores the two main functions of ICMP: reporting errors and queries.
Sending ICMP messages
ICMP messages are grouped into two categories: error reporting and queries. Some messages are specific to each version; however, a few are common to both versions, as shown here:

Figure 12.10 – ICMP messages
For both categories, each ICMP packet has type, code, and checksum fields. The payload for queries is different from error messages, as each has a different purpose, as we'll see in the following sections.
Let's start with a review of how ICMP reports errors.
Reporting errors on the network
ICMP error messages report on network issues that prevent data from being delivered. Commonly sent error messages are grouped into categories that have a specific purpose, and include the following:
- Destination unreachable is where a router informs the host that the requested destination address can't be reached.
- Time exceeded is sent when either the IPv4 Time to Live (TTL) value or IPv6 hop limit reaches zero.
- Parameter problems can be reported when there is an issue in determining a field value in the header or extension header.
Next, let's take a look at examples of some of the errors that you might see in your network.
Viewing examples
We have already seen an example of a Destination Unreachable message in the Investigating the data payload section. Another error is Time Exceeded. To see an example of this error, open bigFlows.pcap, and then go to Frame 7217, which shows a Type 11, Code 0 message. Expand the ICMP header, as shown in the following screenshot:
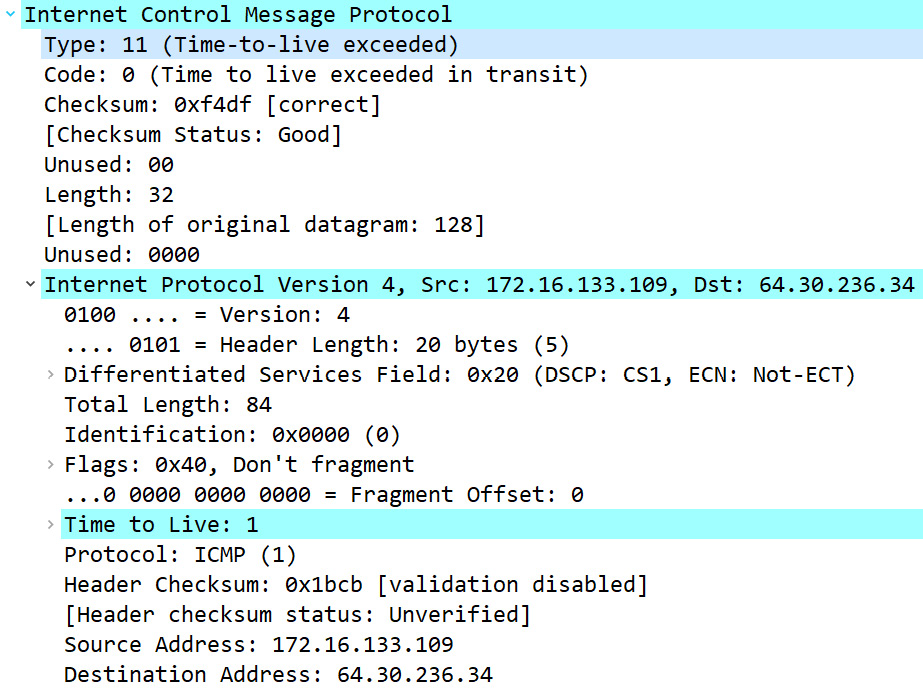
Figure 12.11 – ICMP Time Exceeded error message
In this case, once the packet hits the router, the TTL will have reached zero, and that will trigger the ICMP error.
Another example is a Parameter Problem error message. We can find this by going to CloudShark: https://www.cloudshark.org/captures/bed61f75bde3. Download and open alive6-1.pcap in Wireshark. Go to Frame 3 and expand the ICMPv6 header, as shown:

Figure 12.12 – ICMPv6 Parameter Problem error message
In this case, the error message is Type: Parameter Problem (4) Code: 2 (unrecognized IPv6 option encountered).
As discussed, ICMPv6 has many of the same functions as ICMP but also provides additional reporting to support IPv6. One of the ICMPv6-specific messages is Packet Too Big. Let's take a look.
Monitoring the packet size
In addition to the three error messages reported in IPv4, ICMPv6 includes another error, Packet Too Big, as shown in this diagram listing some of the ICMPv6 error messages:

Figure 12.13 – ICMPv6 error messages
As we learned in Chapter 11, Analyzing IPv4 and IPv6, the payload length is a field value in IPv6. The packet size is monitored as the data travels through the network. If the packet is too large, ICMPv6 will report the Packet Too Big error. This error is sent when a device cannot send the data, as the packet is larger than the Maximum Transmission Unit (MTU) of the outgoing link.
To see an example of an ICMPv6 Packet Too Big message, go to CloudShark: https://www.cloudshark.org/captures/7dd0b50eb768. Download and open packet too big.pcap in Wireshark. Once open, go to Frame 3 and expand the ICMPv6 header, as shown here:
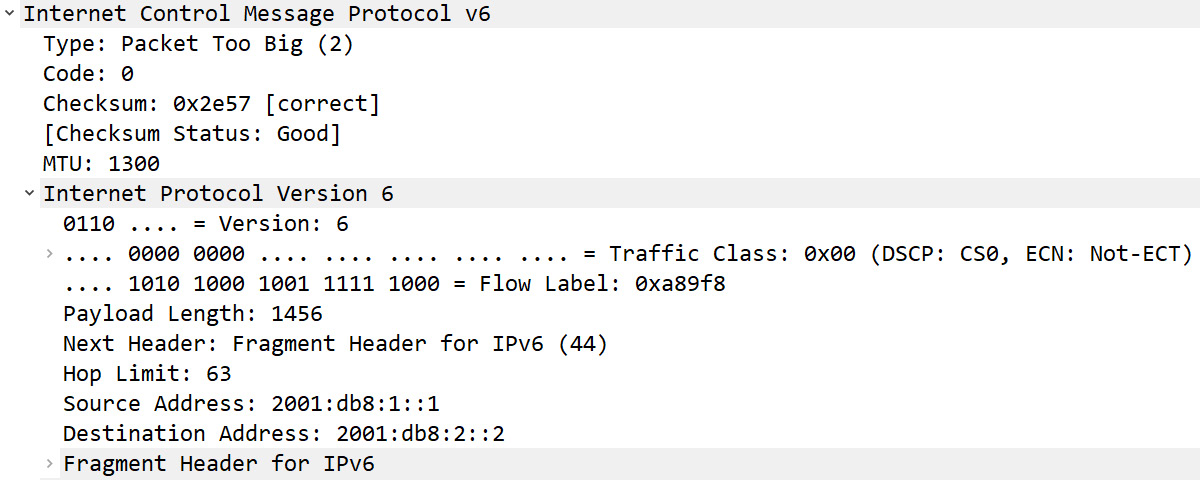
Figure 12.14 – ICMPv6 Packet Too Big error
Because of the complexity of the network, sometimes it's hard to avoid this error. Let's see what options we have when the payload is too big for the MTU.
Managing a Packet Too Big error
When sending data, most OSs employ Path MTU Discovery (PMTUD), a process used to determine what size packet is allowed to travel on the network segment. If the packet is too big, the router will send an ICMPv6 Packet Too Big message back to the host. In that case, one of two things must be done:
- The packet must be discarded.
- The packet must be fragmented if allowed.
Fragmenting the packet will solve the problem of the packet being too big, as it can then be sent out onto the network. As we know, an IPv6 header does not have a fragmentation field and seeks not to fragment packets; however, it can be fragmented by using an extension header. You can see an example of the Fragment Header for IPv6 fragment extension header in the last line of Figure 12.14.
Note
Many devices on the network will block a fragmented packet, and for good reason. Fragmentation puts additional strain on a device and can pose a security risk.
ICMP error messages provide additional information so that the host can see exactly what happened. Errors are received and acted upon by TCP, IP, or user applications. However, in some cases, ICMP messages are ignored.
In addition to sending error messages, ICMP can also request and provide information, as discussed in the following section.
Issuing query messages
An ICMP query has two messages (a request and a reply) that work together and have a specific purpose: to provide status updates and information.
Two examples of requests and replies are as follows:
- Echo request/reply: The ICMP packet works as a probe to test for the reachability of a remote host.
- Router solicitation/advertisement: Provides a way to solicit and receive router information that provides the IP addresses of the interface of an available router.
On a network that is primarily using IPv4, most ICMP messages provide enough information. However, to assist IPv6 in delivering data, ICMPv6 needs to provide information specific to IPv6, as we'll see next.
Providing information using ICMPv6
Although in many ways, ICMP and ICMPv6 are similar, ICMPv6 has more responsibilities. The reason for this is that IPv6 no longer uses ARP broadcasts or Internet Group Message Protocol (IGMP). As a result, ICMPv6 provides additional services to communicate issues on the network, as shown in the following diagram:

Figure 12.15 – ICMPv6 informational messages
Some of the messages unique to ICMPv6 are as follows:
- Neighbor solicitation/advertisement: These types are used for the Neighbor Discovery Protocol (NDP) to provide a method for hosts to share their existence on the network.
- Multicast listener query/report: This is used to exchange group multicast information to routers and hosts.
- Group membership: This is used to alert neighboring routers on hosts included in multicast group membership.
To see an example of the many ICMPv6 messages communicating to other devices on the network, open test55.pcap in Wireshark. In the display filter, enter icmpv6 and press Enter to run the filter.
Create a flow graph by completing the following steps:
- Go to Statistics, and then Flow Graph.
- Once open, go to the lower left-hand corner and select Limit to display filter.
The results are as shown in the following screenshot:

Figure 12.16 – ICMPv6 flow graph
Within the flow graph, you can see Multicast Listener Report and Router Solicitation ICMPv6 packets.
Some of the ICMPv6 reports have additional details. For example, in a separate capture file we can see the details provided in a single report as shown here:

Figure 12.17 – ICMPv6 Multicast Listener Report
Another example of how ICMPv6 communicates on the network is the use of neighbor solicitation. Here is a host that has lost the connection to the gateway. To establish a connection, the host in Frame 99 sends out multicast Neighbor Solicitation messages on the network, as shown in the following screenshot:

Figure 12.18 – ICMPv6 neighbor discovery
The reason you see multiple ICMPv6 packets is that the host is unable to reach the gateway. The Neighbor Solicitation messages will continue until the connection is restored.
As you can see, ICMPv6 is a powerful protocol. In addition to error and information messages, ICMPv6 provides additional information and works with IPv6 to maintain connectivity.
As discussed, ICMP headers hold a value for type and code. Let's take a look at these two fields in order to help us understand what ICMP is trying to tell us.
Evaluating type and code values
The original objective of ICMP was to provide updates on network status and other informational messages. In this section, we'll review the type and code values for ICMP and ICMPv6. Let's start with ICMP.
Reviewing ICMP type and code values
ICMP has been used for IPv4 for many years. There are many different types of ICMP messages, some of which should look familiar, such as these:
- Type 0: Echo reply
- Type 3: Destination unreachable
- Type 5: Redirect
- Type 8: Echo request
- Type 9: Router advertisement
Some, but not all, ICMP types have a corresponding set of code values that further define the ICMP message. For example, Type 3 and Type 9 both have a set of code values.
Type 3 (destination unreachable) has many code values and includes the following:
- Code 0: Net (network) unreachable
- Code 1: Host unreachable
- Code 2: Protocol unreachable
- Code 3: Port unreachable
- Code 4: Fragmentation needed and the Don't Fragment bit was set
Type 9 (router advertisement) only has two code values:
- Code 0: Normal router advertisement
- Code 16: Does not route common traffic
The type and code are the first two fields in an ICMP message and are used to convey information. For example, in Frame 543, ICMP has returned an ICMP Type: 3 and Code: 13, as shown in the following screenshot:
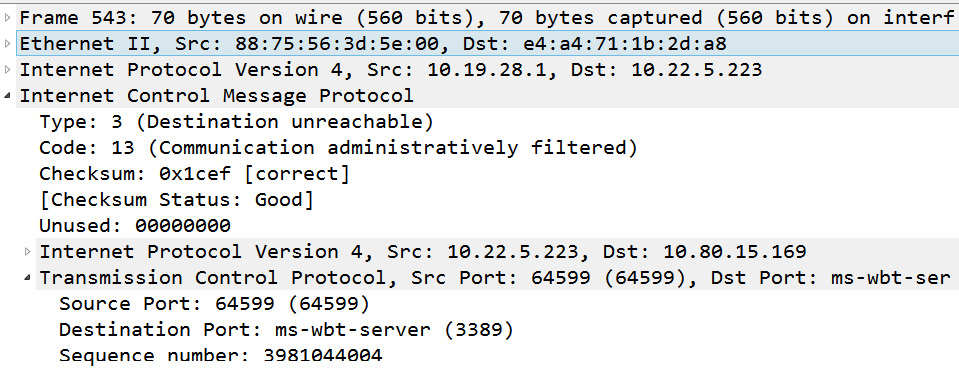
Figure 12.19 – ICMP Type 3 and Code 13
When ICMP returns Type: 3 Destination Unreachable Code: 13 (Communication Administratively Prohibited), this means a firewall is blocking the request.
As we have learned, ICMP headers hold a value for type and code to convey information on what is happening on the network. However, some of the ICMP types are no longer used and are deprecated. Let's explore this.
Discouraging the use of outdated type values
While ICMP lists multiple type values, many are no longer in use because over time they have been found to be ineffective. The outdated and ineffective types are considered deprecated. The following are some of the deprecated ICMP types:
- Type 4: Source Quench
- Type 33: IPv6 Where-are-you
- Type 34: IPv6 I-am-here
- Type 35: Mobile Registration Request
- Type 37: Domain Name Request
Using deprecated ICMP type values is discouraged. To read more on best practices when dealing with ICMP type and code values, visit RFC 7279, found at https://datatracker.ietf.org/doc/html/rfc7279/.
Along with ICMP for IPv4, ICMPv6 is used to communicate updates or error messages and has its own set of type and code values. In the next section, we'll review some of the values for ICMPv6.
Defining ICMPv6 type and code values
Because ICMPv6 provides additional data on IPv6 router and host configuration, you'll find specific type values that help provide this information.
A short list of ICMPv6 type values includes the following:
- Type 1: Destination unreachable
- Type 2: Packet too big
- Type 3: Time exceeded
- Type 4: Parameter problem
- Type 130: Multicast listener query
- Type 131: Multicast listener report
In some cases, the type will have a corresponding code value to further define the message, similar to IPv4. If the type does not have a corresponding code value, the field value will be set to 0, as shown in Figure 12.17.
The following are examples of the various type and corresponding code values for ICMPv6.
Type 1 (destination unreachable) has several code values. Some of them are as follows:
- Code 0: No route to destination
- Code 1: Communication with destination administratively prohibited
- Code 2: Beyond the scope of the source address
- Code 3: Address unreachable
Type 3 (time exceeded) has two codes, as follows:
- Code 0: Hop limit exceeded in transit
- Code 1: Fragment reassembly time exceeded
As we have learned, ICMP can provide a great deal of information on a network, therefore, it's important to understand that this protocol can be used in malicious ways. As a result, the firewall rules should be tuned to prevent malicious activity, as outlined in the next section.
Configuring firewall rules
ICMP supports IP to help ensure data delivery; however, it can also be used in malicious ways. For example, ICMP can be used to conduct reconnaissance as a precursor to an attack, or even to help evade firewall rules. In this section, we'll provide an example of how ICMP can be used to obtain information on the network or to redirect traffic. Then, we'll evaluate some of the firewall rules used to limit the effectiveness of an attack.
Let's start with a brief discussion on a few attacks using ICMP.
Acting maliciously
ICMP can determine a great deal of information about a network. As a result, it can be used as an effective scanning tool. In addition, if security devices aren't tuned to disallow certain types of ICMP packets, you may be the victim of an attack, such as a Distributed Denial of Service (DDoS) or redirect attack.
First, let's start with an overview of a ping sweep, a technique used to see which network hosts might be awake and responding.
Sending malicious ping sweeps
Malicious actors use various techniques to scan a network for vulnerable hosts prior to an attack. One way is by using ICMP ping packets to determine which hosts are alive and responding. A ping sweep (or ping scan) uses a series of ICMP echo request packets on a local area network to see what hosts are alive and responding. As shown in the following diagram, the attacker sends a series of ping packets on the network. Once sent, the attacker then waits to hear a response from a host, in the form of an echo/reply, indicating it is alive:

Figure 12.20 – ICMP ping sweep
Once a responding host is identified, the attacker will send more advanced probes to obtain additional information about the host.
Along with using a series of echo requests/replies, there are several ICMP queries that malicious actors can use to scout information before launching an attack. To see an example of using ICMP packets to probe a network, go to CloudShark: https://www.cloudshark.org/captures/51eabf15169e.
Download and open sniffer_cybercop_scan_1-4223.cap in Wireshark. In the display filter, enter ((ip.src == 192.168.10.33) && (icmp)) && !(ip.src == 192.168.10.138) and press Enter to run the filter, which will then display 12 packets. Create a flow graph by completing the following steps:
- Go to Statistics, and then Flow Graph.
- Once open, go to the lower left-hand corner and select Limit to display filter.
The results are as shown in the following screenshot:

Figure 12.21 – Sending ICMP packets during reconnaissance
In this flow graph, we see how the malicious actor at 192.168.10.33 sends various ICMP messages to the 192.168.10.138 host. In addition to ICMP request packets, the malicious actor also uses timestamp and address mask requests. This type of probe sends various ICMP packets with the hope of getting a reply to help the scanning software rule out different OSs along with other information on the host.
Next, we'll take a look at another type of attack that uses an ICMP redirect message to redirect traffic.
Redirecting traffic
While ICMP is designed to help data move on the network, malicious actors have found ways to use certain types of messages to launch an attack.
ICMP and ICMPv6 both have redirect messages:
- ICMP uses Type 5 – Redirect
- ICMPv6 uses Type 137 – Redirect Message
When used to launch an attack, the malicious actor crafts specially designed redirect messages that can be used to modify the routing tables. The message contains information indicating there is a more optimal route to send traffic. Once the attack is set, the malicious actor poses as a router and sends the specially crafted ICMP message out on the network.
To see an example of using an ICMP redirect packet, go to https://github.com/bro/bro/blob/master/testing/btest/Traces/icmp/icmp6-redirect.pcap. In the middle of the page, select View Raw, and then open icmp6-redirect.pcap in Wireshark. There is only one packet. Expand both the IP and ICMP headers, as shown in this screenshot:

Figure 12.22 – An ICMPv6 redirect packet
Once the host receives the redirect message, the traffic will be redirected to the malicious actor. The malicious actor can then intercept traffic to obtain sensitive information, redirect traffic to another server, or prepare for a more advanced attack.
The last attack we'll cover is an IP/ICMP fragmentation DDoS.
Denying service
One of the ways to disrupt a business is by launching a DDoS. When launched on an internal network, one type of attack is a volumetric DDoS. A volumetric DDoS seeks to flood a device or network with so much traffic that it consumes all the resources, and legitimate traffic is locked out.
One example is a fragmented IP/ICMP volumetric DDoS attack. To look at an example of what you might see during this type of attack, go to https://www.cloudshark.org/captures/962444a14a56. Download and open fragmented-icmp-traffic.pcapng in Wireshark. Once open you will see the following:

Figure 12.23 – fragmented-icmp-traffic.pcapng
Within this capture, you will see the following:
- The host at 192.168.12.1 sends Fragmented IP protocol in Frame 1.
- This is followed by Echo (ping) request in Frame 2.
- The host at 192.168.12.1 then repeats this pattern after every Echo (ping) reply from the host at 192.168.12.2.
This means the host at 192.168.12.2 must continually reassemble the fragmented packets, which will require additional resources.
If you expand the IP header in Frame 1, you will see the following:

Figure 12.24 – A fragmented packet
As illustrated by (1), the protocol that follows the IP header is Protocol: ICMP (1). We also see by (2) that the packet is [Reassembled IPv4 in frame: 2].
The fragmented-icmp-traffic.pcapng capture only has 20 packets; however, if the attack were to continue, this could result in the device being unable to respond to legitimate hosts.
As evidenced, ICMP can be used to obtain information on hosts and act in a malicious manner. As a result, it's best to be aware of the various types and only allow ICMP packets that are absolutely necessary, as we'll see in the next section.
Allowing only necessary types
Because ICMP can affect the operation of important system functions and obtain configuration information, hackers use ICMP messages while conducting reconnaissance on a network or during an active attack. As a result, best practices can include the following:
- Blocking certain ICMP messages with an Access Control List (ACL) on a firewall, especially at border routers
- Configuring an Intrusion Detection System (IDS) to either block or alert the administrator if an ICMP redirect message is detected
While ICMP can be used maliciously, we must remember that diagnostic utilities, such as Ping and Tracert, require ICMP. As a result, a network administrator must decide what types of ICMP packets should be allowed on a network. When setting up your firewall, keep in mind the only essential ICMP traffic is Destination Unreachable (Type 3 for ICMP and Type 1 for ICMPv6), along with the corresponding codes.
All other ICMP types are optional, depending on whether you would like to allow them on your network. Depending on your organization, other types that are allowed can include the following:
- Type 8/0: Echo request/reply
- Type 11: Time exceeded
ICMP helps to ensure that data gets delivered; however, it can be used in malicious ways, therefore, you need to make sure that firewalls are properly tuned.
Summary
By now, you can see the many aspects of ICMP, which is a significant protocol in the TCP/IP suite. We looked at the purpose of ICMP, a method to communicate issues that prevent data delivery. We compared ICMP and ICMPv6, which have similar functions, but we now understand that ICMPv6 has a bigger role. So that you can use this protocol while troubleshooting, we discovered ICMP messages that communicate with hosts to report on transmission errors. In addition, we saw how query messages can be used to attempt to obtain information from a host.
To better understand the ICMP type and code values, we examined how they work when communicating information. In addition, we learned that there are some ICMP types that you will rarely see as they are now deprecated and/or not supported. By now, you should recognize that ICMP is a powerful protocol that helps to move traffic on a network, but can also be used in malicious ways. As a result, you should configure firewall rules that allow or deny specific ICMP types in order to reduce the threat of malicious ICMP traffic on the LAN.
In the next chapter, we'll take a closer look at examining Domain Name System (DNS) traffic with Wireshark. Using practical examples, you'll be able to understand how DNS works when resolving a hostname to an IP address. You'll discover what the field values are in a DNS header, along with stepping through a DNS request/response transaction. In addition, because DNS problems are common on many networks, we'll review tools that can help you calculate DNS response time using Wireshark, along with methods to secure DNS.
Questions
Now, it's time to check your knowledge. Select the best response, and then check your answers with those in the Assessments appendix:
- ICMP communicates issues that prevent data delivery. Common issues include the network or port being _____.
- Stateful
- Inspected
- Unreachable
- ARP enabled
- Some of the ICMP types are no longer used since, over time, they have been found to be ineffective and are considered _____.
- Quenched
- Unreachable
- Digital
- Deprecated
- In ICMPv6, a _____ message can be sent when there is an issue determining a field value in the IPv6 header or the IPv6 extension header.
- Time exceeded
- Parameter problems
- Packet too big
- Source quench
- When setting firewall rules, the only essential ICMP traffic is _____. The others are optional.
- Type 3 for ICMP and Type 1 for ICMPv.
- Type 123 for ICMP and Type 17 for ICMPv.
- Type 1 for ICMP and Type 3 for ICMPv.
- Type 9 for ICMP and Type 104 for ICMPv.
- ICMP can be used in a malicious way. One way is a ______ scan that uses a series of ICMP echo request packets on a network to see what hosts are alive and responding.
- Payload
- Ping
- Port
- Checksum
- In ICMPv6, a _____ message can be sent when a device cannot send the data as the packet is larger than the MTU of the outgoing link.
- Time exceeded
- Parameter problems
- Packet too big
- Source quench
- Some, but not all, ICMP types have a corresponding set of code values that further define the ICMP message. For example, _____ both have a set of code values.
- Type 0 and Type 7
- Type 1 and Type 2
- Type 1 and Type 6
- Type 3 and Type 9
Further reading
Please refer to the following links for more information:
- To read more on RFC 792, Internet Control Message Protocol, visit https://datatracker.ietf.org/doc/html/rfc792.
- Learn more about ICMPv6 from RFC 4443, Internet Control Message Protocol (ICMPv6) for the Internet Protocol Version 6 (IPv6) Specification, at https://datatracker.ietf.org/doc/html/rfc4443.
- To view a discussion on various attacks, including a Loki ICMP attack, visit https://resources.infosecinstitute.com/topic/icmp-attacks/.
- For a discussion on three different methods to extract data using a covert channel, go to https://www.giac.org/paper/gsec/2601/radar-covert-communications-channels/104464.
- At some point, you may need to reference an ICMP type or code value. To see a summary of the most up-to-date values, visit the following:
- For ICMP, visit https://www.iana.org/assignments/icmp-parameters/icmp-parameters.xhtml.
- For ICMPv6, visit https://www.iana.org/assignments/icmpv6-parameters/icmpv6-parameters.xhtml.
