To try out the tools we have learned about, let's try doing some static analysis on ch4_2.exe. To help out, here's a list of what we need to find:
- File information:
- file type
- imported DLLs and APIs
- text strings
- file hash
- What the file does
Jumping right into getting file information, we will use TrID (http://mark0.net/soft-trid-e.html) to identify the file type. Execute the following line:
trid cha4_2.exe
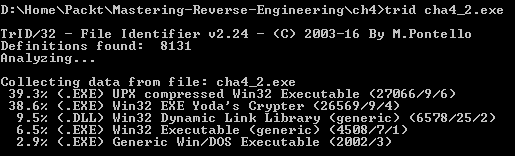
The TrID result tells us that we have here a Windows 32-bit executable file that is UPX packed:
Knowing that this is a UPX packed file, we can try the UPX (https://upx.github.io/) tool's decompress feature to help us restore the file back to its original form before it was packed. A packed file is a compressed executable file that decompresses and then executes the program during runtime. The primary purpose of a packed file is to reduce the file size of executables while retaining the program's original behavior. We will be discussing more about packers in Chapter 10, Packing and Encryption, of this book. For now, let's just unpack this file with the UPX tool using the -d parameter:
upx -d cha4_2.exe
This results to the file being expanded back to its original form:

And if we use TrID this time, we should get a different result:

It is still a Windows executable file, so we can use CFF Explorer to check for more information:

On the left pane, if we select Import Directory, we should see a list of imported library files and API functions it will use, as shown here:

Clicking on USER32.dll, we see that the MessageBoxA API is going to be used by the program.
Using the bintext (http://b2b-download.mcafee.com/products/tools/foundstone/bintext303.zip) tool, we can see a list of text strings found in the file:
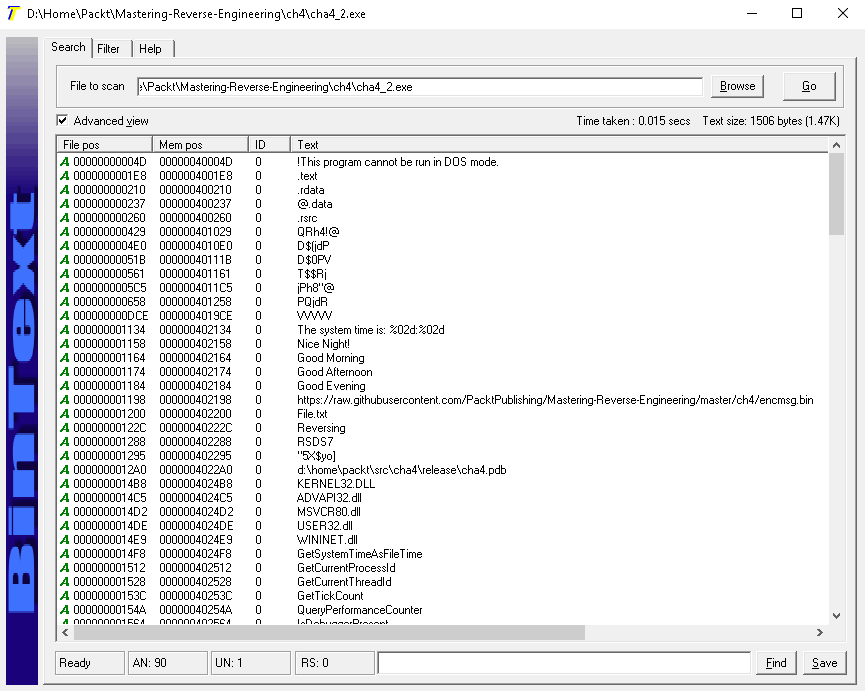
These appear to be the notable text strings, which suggest that the program checks for the time and displays various greetings. It will probably retrieve a file from the internet. It may do something about the File.txt file. But all these are just educated guesses, which makes good practice for reversing, as it helps use to build an overview of the relationship between each aspect of our analysis:
000000001134 000000402134 0 The system time is: %02d:%02d
000000001158 000000402158 0 Nice Night!
000000001164 000000402164 0 Good Morning
000000001174 000000402174 0 Good Afternoon
000000001184 000000402184 0 Good Evening
000000001198 000000402198 0 https://raw.githubusercontent.com/PacktPublishing/Mastering-Reverse-Engineering/master/ch4/encmsg.bin
000000001200 000000402200 0 File.txt
00000000122C 00000040222C 0 Reversing
The hash (MD5, SHA1, SHA256) of a file will help as a reference to every file we analyze. There are a lot of file hash-generating tools available in the internet. To generate the hashes of this file, we chose a tool called HashMyFiles. This is a tool compiled for Windows OS and can be added to the context menu (right-click) of the Windows Explorer:
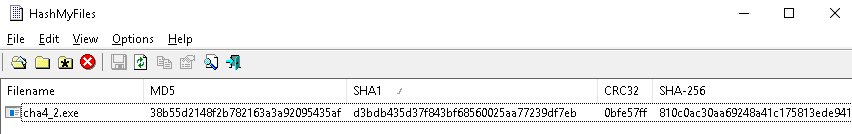
It can display the file's CRC, MD5, SHA1, SHA-256, SHA-512, and SHA-384, as follows:
MD5: 38b55d2148f2b782163a3a92095435af
SHA1: d3bdb435d37f843bf68560025aa77239df7ebb36
CRC: 0bfe57ff
SHA256: 810c0ac30aa69248a41c175813ede941c79f27ddce68a91054a741460246e0ae
SHA512: a870b7b9d6cc4d86799d6db56bc6f8ad811fb6298737e26a52a706b33be6fe7a8993f9acdbe7fe1308f9dbf61aa1dd7a95015bab72b5c6af7b7359850036890e
SHA384: b0425bb66c1d327d7819f13647dc50cf2214bf00e5fb89de63bcb442535860e13516de870cbf07237cf04d739ba6ae72
Usually, we only take either MD5, SHA1, or SHA256.
We should not forget the file size and the creation time using a simple file property check:

The Modified date is more relevant in terms of when the file was actually compiled. The Created date is when the file was written or copied to the directory where it is now. That means that the first time the file was built, both the Created and Modified dates were the same.
To statically analyze the file's behavior, we will be using a disassembly tool known as IDA Pro. A freeware version of IDA Pro can be found at https://www.hex-rays.com/products/ida/support/download_freeware.shtml. But, if you can afford the luxury of its paid version, which we highly recommend, please do purchase it. We find the features and supported architectures of the paid version way better. But for this book, we will be using every available tool that does not require purchasing.
There are currently two known free versions of IDA Pro. We have made backups of the tool available at https://github.com/PacktPublishing/Mastering-Reverse-Engineering/tree/master/tools/Disassembler%20Tools. And since we are dealing with a 32-bit Windows executable file, select the 32-bit version.
Once IDA Pro is installed, open up cha4_2.exe inside. Wait for the auto-analysis to complete and it will redirct the disassembly to the WinMain function:

Scrolling down will show more disassembly code that we learned in Chapter 3, The Low-Level Language. For deadlisting behaviors, we usually look for instructions that call APIs. The very first API we encounter is a call to GetSystemTime:

Following the code, we encounter these API functions in this sequence:
- vsprintf_s
- MessageBoxA
- InternetOpenA
- InternetConnectW
- InternetOpenUrlA
- memset
- InternetReadFile
- InternetCloseHandle
- strcpy_s
- CreateFileA
- WriteFile
- CloseHandle
- RegCreateKeyExW
- RegSetValueExA
With what we learned in Chapter 3, The Low Level Language, try to follow the code and deduce what the file will do without executing it. To help out, here are the expected behaviors of the program:
- Displaying a message depending on the current system time. The messages can be one of the following:
- Good Morning
- Good Afternoon
- Good Evening
- Nice Night
- Reading the contents of a file from the internet, decrypting the contents, and saving it to a file named File.txt.
- Making a registry key, HKEY_CURRENT_USERSoftwarePackt, and storing the same decrypted data in the Reversing registry value.
This may take a long time for beginners, but with continuous practice, analysis will be done at a fast pace.
