Volatility can be downloaded from https://www.volatilityfoundation.org/releases. For this section, our VirtualBox host is in a Linux Ubuntu machine. The Volatility command parameters shown here should also be the same when used in Windows.
First, we need to identify the exact operating system version using Volatility using the imageinfo parameter, as shown in the following examples:
vol -f ~/memory.dmp imageinfo

Again, ~/memory.dmp is the file path of the memory we just dumped. The result should show a list of the identified OS profile. For Windows 7 SP1 32-bit, we would be using Win7SP1x86 as our profile for succeeding Volatility commands.
Next, we will have to list down the running processes and identify which is our packed executable. To list down running processes, we will be using the pslist parameter, as shown in the following examples:
volatility --profile=Win7SP1x86 -f ~/memory.dmp pslist

Looking at the second column's last line in the previous screenshot, we find upxed.exe. We need to note down the process ID (PID) which has a value of 2656. Now that we have retrieved the PID of our packed executable, we can dump the process to file using the procdump parameter, as shown in the following code:
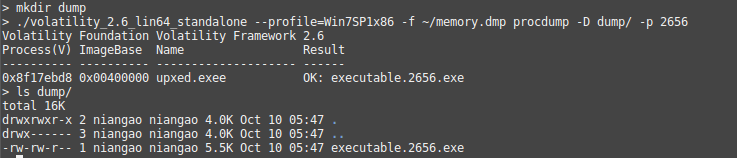
volatility --profile=Win7SP1x86 -f ~/memory.dmp procdump -D dump/ -p 2656
procdump will save the process executable in the dump/ folder set by the -D parameter, as shown in the following screenshot:
Volatility has a wide range of features to choose from. Feel free to explore these arguments as these may help in fitting analysis situations.
