It may be easier if the pseudocode were automatically given to us. Certain tools exist that may be able to help us with that. Let's try and decompile passcode.exe (https://github.com/PacktPublishing/Mastering-Reverse-Engineering/blob/master/ch7/passcode.exe) using the standalone version of Snowman (https://derevenets.com/). Once the file has been opened, click on View->Inspector. This should show a box containing resolved functions from the program. Look for the function definition _main and select it to show the equivalent pseudocode of the assembly language. This highlights the assembly language line in the left-hand pane and the psuedocode in the middle pane:

As of the time of writing this book, the output C source may help, but not all are correctly decompiled. For instance, the loop where "e" was being compared was not decompiled correctly. The output shows a while loop, but we expect that the v10 variable should have its value read from the offset calculated in the password string. However, most of the code should somehow aid us in understanding how the program should work. The decompiler engine for this is open source (https://www.capstone-engine.org/), so not much should be expected as support won't always be there.
The good news is that there are more powerful decompilers that exist, such as HexRays. Most institutions and some individual analysts and researchers who perform reverse engineering are willing to pay for these decompilers. HexRays is one bang for its buck for most reverse engineers.
Here's a HexRays decompiled version of passcode.exe:
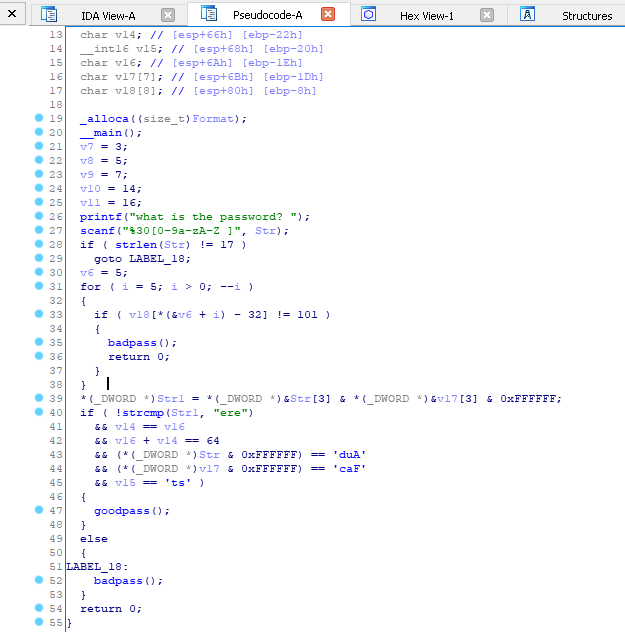
Decompilers are continuously developed since these tools speed up analysis. They do not decompile perfectly, but should be near the source.
