When two devices are connected to each other on the network, they are supposed to communicate; this is considered normal behavior. However, suppose you have thousands of devices connected to your network and you want to figure out the most active device that is generating too much traffic, then in that instance, the Conversations window will be quite useful.
To access this nice tool, click on Statistics | Conversations. After this, you will be presented with a window like the one shown in the following screenshot, which lists various details in terms of several columns listing the packets that were transferred, the bytes that were transferred, the flow of traffic, devices' MAC addresses, and various other details. At the top, you will observe various protocols displayed individually in separate tabs, and along with each active protocol tab, you will notice a number that denotes the number of unique conversations.

Figure 3.6: Conversations window
For example, if you are looking for the devices that generated a lot of packets and from where major data transfer has happened, then open the Conversations dialog, go to the IPv4 tab, and sort the packets column in a descending order. Here, the device listed in the first row is your answer. Take a look at the following screenshot that illustrates the same.
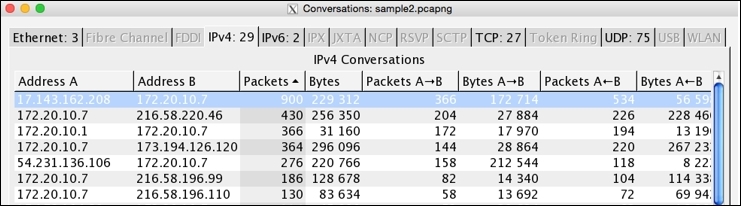
Figure 3.7: Busiest devices
In the first row, we can see how many packets/bytes have been sent and received by each endpoint and the total elapsed duration. If you wish to create a filter for the same, right-click on the first row and then create the respective expression you are thinking about. I chose the first option, A<->B, which only shows packets that are associated with Address A and Address B:

The respective filter will be inserted in the Display Filter dialog, as shown in the following screenshot:
The Conversations dialog will let us collect and analyze details in a more granular form, which can be used in various scenarios while troubleshooting and auditing networking infrastructures.
