The safest option is to not use the Internet to investigate the attack at all, but this is often impractical. If you do use the Internet, you should use indirection to evade the attacker’s potentially watchful eye.
One indirection tactic is to use some service or mechanism that is designed to provide anonymity, such as Tor, an open proxy, or a web-based anonymizer. While these types of services may help to protect your privacy, they often provide clues that you are trying to hide, and thus could arouse the suspicions of an attacker.
Another tactic is to use a dedicated machine, often a virtual machine, for research. You can hide the precise location of a dedicated machine in several ways, such as the following:
By using a cellular connection
By tunneling your connection via Secure Shell (SSH) or a virtual private network (VPN) through a remote infrastructure
By using an ephemeral remote machine running in a cloud service, such as Amazon Elastic Compute Cloud (Amazon EC2)
A search engine or site designed for Internet research can also provide indirection. Searching in a search engine is usually fairly safe, with two caveats:
The inclusion of a domain name in a query that the engine was not previously aware of may prompt crawler activity.
Clicking search engine results, even for cached resources, still activates the secondary and later links associated with the site.
The next section highlights a few websites that provide consolidated information about networking entities, such as whois records, DNS lookups (including historical lookup records), and reverse DNS lookups.
The two fundamental elements that compose the landscape of the Internet are IP addresses and domain names. DNS translates domain names like www.yahoo.com into IP addresses (and back). Unsurprisingly, malware also uses DNS to look like regular traffic, and to maintain flexibility and robustness when hosting its malicious activities.
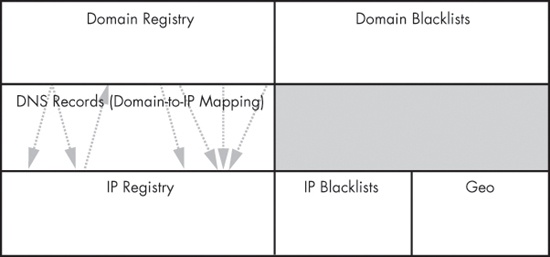
Figure 14-1 shows the types of information available about DNS domains and IP addresses. When a domain name is registered, registration information such as the domain, its name servers, relevant dates, and contact information for the entity who registered the name is stored in a domain registrar. Internet addresses have registries called Regional Internet Registries (RIRs), which store IP address blocks, the blocks’ organization assignment, and various types of contact information. DNS information represents the mapping between a domain name and an IP address. Additionally, metadata is available, including blacklists (which can apply to IP addresses or domain names) and geographical information (which applies only to IP addresses).
While both of the domain and IP registries can be queried manually using command-line tools, there are also numerous free websites that will perform these basic lookups for you. Using websites to query has several advantages:
Many will do follow-on lookups automatically.
They provide a level of anonymity.
They frequently provide additional metadata based on historical information or queries of other sources of information, including blacklists and geographical information for IP addresses.
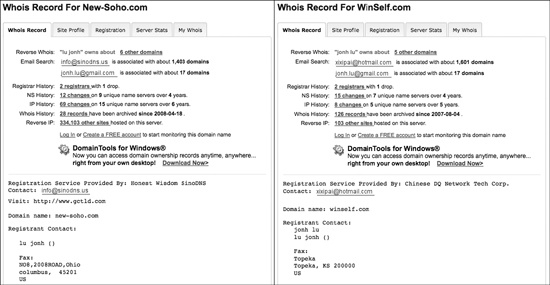
Figure 14-2 is an example of two whois requests for domains that were used as command-and-control servers for backdoors used in targeted attacks. Although the backdoors were different, the name listed under the registration is the same for both domains.
Three lookup sites deserve special mention:
DomainTools (http://www.domaintools.com/)
Provides historical whois records, reverse IP lookups showing all the domains that resolve to a particular IP address, and reverse whois, allowing whois record lookups based on contact information metadata. Some of the services provided by DomainTools require membership, and some also require payment.
RobTex (http://www.robtex.com/)
Provides information about multiple domain names that point to a single IP address and integrates a wealth of other information, such as whether a domain or IP address is on one of several blacklists.
BFK DNS logger (http://www.bfk.de/bfk_dnslogger_en.html)
Uses passive DNS monitoring information. This is one of the few freely available resources that does this type of monitoring. There are several other passive DNS sources that require a fee or are limited to professional security researchers.