- Practical Malware Analysis: The Hands-On Guide to Dissecting Malicious Software
- Praise for Practical Malware Analysis
- Warning
- About the Authors
- Foreword
- Acknowledgments
- Introduction
- 0. Malware Analysis Primer
- I. Basic Analysis
- Conclusion
- Labs
- 2. Malware Analysis in Virtual Machines
- 3. Basic Dynamic Analysis
- Sandboxes: The Quick-and-Dirty Approach
- Running Malware
- Monitoring with Process Monitor
- Viewing Processes with Process Explorer
- Comparing Registry Snapshots with Regshot
- Faking a Network
- Packet Sniffing with Wireshark
- Using INetSim
- Basic Dynamic Tools in Practice
- Conclusion
- Labs
- Lab 3-1
- Lab 3-2
- Lab 3-3
- Lab 3-4
- Questions
- II. Advanced Static Analysis
- 4. A Crash Course in x86 Disassembly
- 5. IDA Pro
- Using Cross-References
- Analyzing Functions
- Using Graphing Options
- Enhancing Disassembly
- Extending IDA with Plug-ins
- Conclusion
- Labs
- 6. Recognizing C Code Constructs in Assembly
- 7. Analyzing Malicious Windows Programs
- The Windows API
- The Windows Registry
- Networking APIs
- Following Running Malware
- Kernel vs. User Mode
- The Native API
- Labs
- Lab 7-1
- Lab 7-2
- Lab 7-3
- Questions
- III. Advanced Dynamic Analysis
- 8. Debugging
- 9. OllyDbg
- 10. Kernel Debugging with WinDbg
- Rootkits
- Loading Drivers
- Kernel Issues for Windows Vista, Windows 7, and x64 Versions
- Conclusion
- Labs
- Lab 10-1
- Lab 10-2
- Lab 10-3
- Questions
- IV. Malware Functionality
- 11. Malware Behavior
- 12. Covert Malware Launching
- 13. Data Encoding
- 14. Malware-Focused Network Signatures
- Network Countermeasures
- Safely Investigate an Attacker Online
- Content-Based Network Countermeasures
- Combining Dynamic and Static Analysis Techniques
- The Danger of Overanalysis
- Hiding in Plain Sight
- Understanding Surrounding Code
- Finding the Networking Code
- Knowing the Sources of Network Content
- Hard-Coded Data vs. Ephemeral Data
- Identifying and Leveraging the Encoding Steps
- Creating a Signature
- Analyze the Parsing Routines
- Targeting Multiple Elements
- Understanding the Attacker’s Perspective
- Conclusion
- Labs
- Lab 14-1
- Lab 14-2
- Lab 14-3
- Questions
- V. Anti-Reverse-Engineering
- 15. Anti-Disassembly
- 16. Anti-Debugging
- 17. Anti-Virtual Machine Techniques
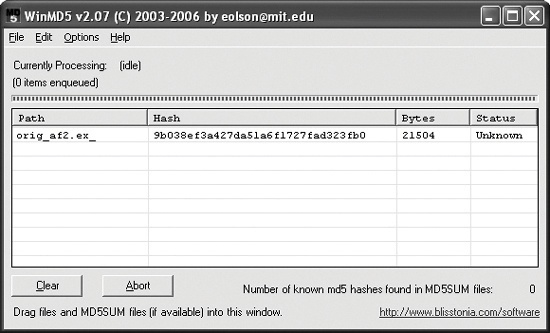
Hashing is a common method used to uniquely identify malware. The malicious software is run through a hashing program that produces a unique hash that identifies that malware (a sort of fingerprint). The Message-Digest Algorithm 5 (MD5) hash function is the one most commonly used for malware analysis, though the Secure Hash Algorithm 1 (SHA-1) is also popular.
For example, using the freely available md5deep program to calculate the hash of the Solitaire program that comes with Windows would generate the following output:
C:>md5deep c:WINDOWSsystem32sol.exe 373e7a863a1a345c60edb9e20ec32311 c:WINDOWSsystem32sol.exe
The hash is 373e7a863a1a345c60edb9e20ec32311.
The GUI-based WinMD5 calculator, shown in Figure 1-1, can calculate and display hashes for several files at a time.
Once you have a unique hash for a piece of malware, you can use it as follows:
Use the hash as a label.
Share that hash with other analysts to help them to identify malware.
Search for that hash online to see if the file has already been identified.
-
No Comment