Wireshark is an open source sniffer, a packet capture tool that intercepts and logs network traffic. Wireshark provides visualization, packet-stream analysis, and in-depth analysis of individual packets.
Like many tools discussed in this book, Wireshark can be used for both good and evil. It can be used to analyze internal networks and network usage, debug application issues, and study protocols in action. But it can also be used to sniff passwords, reverse-engineer network protocols, steal sensitive information, and listen in on the online chatter at your local coffee shop.
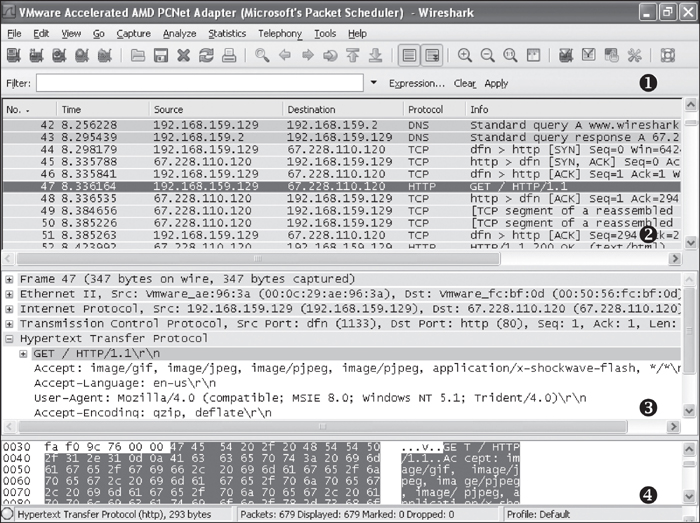
The Wireshark display has four parts, as shown in Figure 3-10:
The Filter box ❶ is used to filter the packets displayed.
The packet listing ❷ shows all packets that satisfy the display filter.
The packet detail window ❸ displays the contents of the currently selected packet (in this case, packet 47).
The hex window ❹ displays the hex contents of the current packet. The hex window is linked with the packet detail window and will highlight any fields you select.
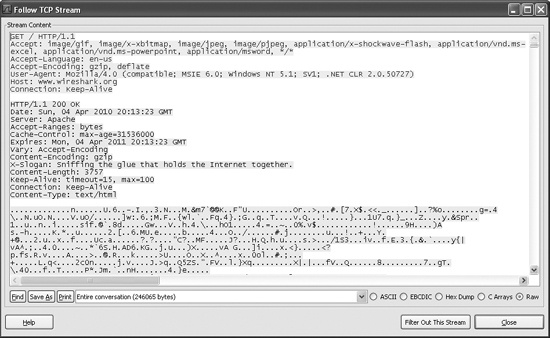
To use Wireshark to view the contents of a TCP session, right-click any TCP packet and select Follow TCP Stream. As you can see in Figure 3-11, both ends of the conversation are displayed in session order, with different colors showing each side of the connection.
To capture packets, choose Capture ▶ Interfaces and select the interface you want to use to collect packets. Options include using promiscuous mode or setting a capture filter.
Warning
Wireshark is known to have many security vulnerabilities, so be sure to run it in a safe environment.
Wireshark can help you to understand how malware is performing network communication by sniffing packets as the malware communicates. To use Wireshark for this purpose, connect to the Internet or simulate an Internet connection, and then start Wireshark’s packet capture and run the malware. (You can use Netcat to simulate an Internet connection.)
Chapter 14 discusses protocol analysis and additional uses of Wireshark in more detail.