Chapter 38. Successfully implementing Kerberos delegation
Kerberos delegation is a method of securely transferring a user’s credentials from the client’s PC to the middle application tier such as a web server, then on to a back-end database tier. In this chapter, I’ll explain some of the issues, talk about the prerequisites, and discuss the steps of implementing Kerberos delegation in your environment.
I first became interested in digging deeper into Kerberos delegation when I asked a group of approximately 50 database professionals the following question at a local PASS chapter meeting: “How many people have attempted to set up Kerberos delegation?” I was shocked to see so few hands, and then shocked again after hearing that not one of them was successful.
I’ve implemented Kerberos with a client for a scaled-out SharePoint and Reporting Services environment and ran into little difficulty doing so. It did take time to troubleshoot, but in the end there was victory. So why was I so successful? I think it was partially due to a fantastic relationship with the system administrator, who was patient, curious, and not operating a systems environment in fire-fighting mode. I also had an old colleague who’d traveled the Kerberos delegation path before and forwarded us some notes and resources. I’m indebted to Goran and Richard for their help in the past, in turn making this chapter possible.
Over the last few months, I’ve scoured many Microsoft Knowledge Base articles, white papers, webcasts, blogs, books, and magazines to see that there are truly a lot of factors that can affect whether a Kerberos delegation implementation is successful. Upon setting up a virtual fictitious environment with which to test my findings, I quickly felt the pain of others who’d traveled this path before me. I spent a number of hours troubleshooting some pretty mind-numbing errors. This chapter draws together what I’ve absorbed and distills it into a package to make your implementation of Kerberos delegation successful.
Understanding the issues that Kerberos delegation resolves
It isn’t uncommon for a new technology solution to come along and for IT people to look around to see if they have a business problem that this new technology will resolve. This isn’t always a bad thing, but sometimes businesses get skeptical and wonder if their IT staff are just looking for a reason to play with something new. Kerberos delegation is likely not one of those technologies. What Kerberos delegation gives us is fantastic for business, but there’s no shiny exterior or crinkly wrapper. In fact I’d guess that a large percentage of IT people didn’t know that Kerberos delegation was introduced in Windows Server 2000 to lay a foundation for single sign-on. I’d imagine Kerberos is often stumbled upon only after a scale-out project is embarked upon, and things don’t go quite as planned, as is the case with the sidebar titled “Twelve Angry Techs.”
Twelve Angry Techs—humorous SQL Server Magazine article
Hopefully this chapter will help prevent you from running into some of the issues this group encountered:
http://www.sqlmag.com/Article/ArticleID/99207/Twelve_Angry_Techs.html.
The double hop
The difficulty with Kerberos delegation is that people often “don’t know what they don’t know.” They’re forced to take error messages (the symptoms of the problem) and do some research until they uncover the mystery of their problem. Frequently, this problem is the one referred to as the double-hop issue. Out of the box, the Windows Server platform isn’t configured to have users’ credentials passed from the client machine to a middle business tier, which in turn passes the users’ credentials on to the back-end data tier. The environment can be set up to operate that way, but it requires effort and understanding before this scenario will be possible. This chapter will step you through the configurations needed to successfully accomplish a double hop (and multi hops) in the most common environments.
A generic infrastructure—our business challenge
In order to understand this double hop issue better, it might be helpful to provide a simple scenario to use as an example. Let’s assume the following scenario as laid out in figure 1.
Figure 1. Our fictitious “SSTB.local” Active Directory domain

A business user, Joan, needs to access her corporate intranet server called vWebTier. This is shown in figure 1 as the 1st Hop. When she runs her intranet applications, the intranet server passes her credentials on to the database server called vDataTier. This step is shown in the figure as the 2nd Hop. The database recognizes Joan’s credentials on the domain and gives her the appropriate information based on her predefined access, mapped to a SQL Server login and associated database user. An audit application installed on the database server is able to recognize that it was Joan who requested customer information, and logs her user account in the audit log.
This scenario was made possible because Kerberos delegation was put in place. The next section explains some of the important aspects of delegation you need to understand before implementing it in your environment.
Understanding Kerberos delegation
Kerberos is an involved authentication protocol developed at MIT. Microsoft’s implementation of Kerberos debuted with the advent of Active Directory (AD) in Windows Server 2000. There are many detailed Knowledge Base articles, white papers, blogs, and webcasts on the subject. Many of these resources are referenced at the end of the chapter if you need a more detailed explanation of Kerberos delegation. This section focuses on what you need to understand before you talk with your Windows admin, so that you can get her support and cooperation in implementing a Kerberos delegation solution.
Service principle names
Microsoft Product Support Services has indicated that when troubleshooting Kerberos delegation issues with customers, the bulk of problems commonly revolves around service principle names (SPNs). An SPN is a registration in Active Directory that enables the user to locate a service in an Active Directory domain. The SPN is made up of a few basic parts:
- The service being provided
- The computer hosting the service
- The port number (if you aren’t using the service’s default port)
- The user or computer account context that the service is running
Now that we have an idea what an SPN is, let’s look at the ones we’ll need to create. Someone with Domain Admin or Enterprise Admin privileges creates an SPN by using setspn.exe. Setspn ships with Windows Server 2008, but for Windows Server 2003 it’s part of the Windows Server 2003 Service Pack 2 32-bit Support Tools package, which is available from http://www.microsoft.com/downloads.
Note
I don’t provide the direct link to the support tools mentioned in this section because they would be long hyperlinks, and when new service packs come out in the future, it’s best you use the latest files. Use the search bar at the top of http://www.micosoft.com/Downloads to find the most up-to-date version for your edition of Windows Server 2003.
The setspn.exe command-line tool provides the three main functions of listing, adding, and deleting SPNs. When the support tools are installed, a new Programs group is added to your Start menu. Click on Command Prompt in the Windows Support Tools group so that you’re in the path of the installed applications. Let’s start off by listing the SPNs that are set in the functioning environment where delegation is in place, as shown in listing 1.
Listing 1. Finding out the SPNs that are currently in place
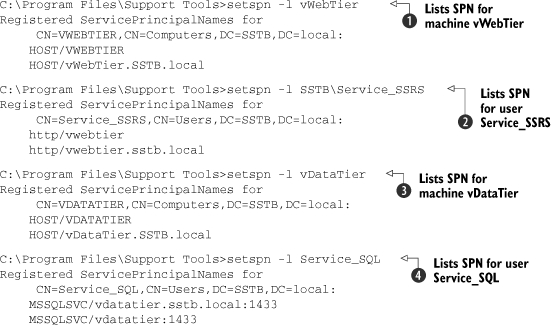
In the first command ![]() , we’re using setspn to list the service principle names in place for the machine named vWebTier. You can also see that the
machine is part of the SSTB.local domain and there are two HOST registrations for vWebTier. One entry is for HOST/VWEBTIER,
which registers the NetBIOS name of the machine, and a second entry HOST/vWebTier.SSTB.local registers the fully qualified
domain name (FQDN) for the server. Windows automatically creates these two registrations as soon as the machine is added to
the domain.
, we’re using setspn to list the service principle names in place for the machine named vWebTier. You can also see that the
machine is part of the SSTB.local domain and there are two HOST registrations for vWebTier. One entry is for HOST/VWEBTIER,
which registers the NetBIOS name of the machine, and a second entry HOST/vWebTier.SSTB.local registers the fully qualified
domain name (FQDN) for the server. Windows automatically creates these two registrations as soon as the machine is added to
the domain.
The second command ![]() lists the SPNs for the services associated with the user account Service_SSRS. Note that the HTTP service is running on the
host vWebTier, but the service is registered to the user account, not to the machine. This causes confusion for many, and is the reason why
duplicate SPNs are mistakenly created. We chose to register the service to the user account Service_SSRS as opposed to the
computer account vWebTier, because we’re going to run the IIS application pool under the context of Service_SSRS. Service_SSRS
will be responsible for passing credentials on to the vDataTier database server. You’ll also notice that the domain name SSTB
was specified in this command, but all of the commands in listing 1 return DC=SSTB,DC=local, indicating that Active Directory already knows the domain context regardless of whether SSTB is indicated in the command.
lists the SPNs for the services associated with the user account Service_SSRS. Note that the HTTP service is running on the
host vWebTier, but the service is registered to the user account, not to the machine. This causes confusion for many, and is the reason why
duplicate SPNs are mistakenly created. We chose to register the service to the user account Service_SSRS as opposed to the
computer account vWebTier, because we’re going to run the IIS application pool under the context of Service_SSRS. Service_SSRS
will be responsible for passing credentials on to the vDataTier database server. You’ll also notice that the domain name SSTB
was specified in this command, but all of the commands in listing 1 return DC=SSTB,DC=local, indicating that Active Directory already knows the domain context regardless of whether SSTB is indicated in the command.
The third command ![]() lists the SPNs for the computer vDataTier, and again, because this machine is a member of the domain, the HOST services were
automatically registered with the NetBIOS name and the FQDN.
lists the SPNs for the computer vDataTier, and again, because this machine is a member of the domain, the HOST services were
automatically registered with the NetBIOS name and the FQDN.
The last command ![]() lists the SPNs for the service account with which the SQL Server service is running on vDataTier. If the SQL Server was originally
installed with LocalSystem as opposed to using a domain user for its service account, SQL Server would’ve automatically created
an SPN on the vDataTier computer account.
lists the SPNs for the service account with which the SQL Server service is running on vDataTier. If the SQL Server was originally
installed with LocalSystem as opposed to using a domain user for its service account, SQL Server would’ve automatically created
an SPN on the vDataTier computer account.
Duplicate SPNs
When SQL is installed with a domain account, no automatic registration takes place. If you originally installed SQL with LocalSystem, ensure that you list the SPNs for the computer account to check that the SPNs are no longer there (or delete them if they are), as duplicate SPNs listed in both the user account and the computer account will prevent Kerberos Delegation from functioning.
Note
Some services do automatic registration under certain circumstances; therefore, always list SPNs for both user accounts (under which the service runs) and computer accounts to see that a service for a host doesn’t show up in two accounts.
Creating SPNs
Now that we’ve shown the results we’re looking for, let’s demonstrate how to create those registrations.
In figure 1, the SSTB.local Active Directory domain has an IIS web server called vWebTier with an application pool running under the context of a domain user account called Service_SSRS. The following command shows how to create an SPN for this service:
setspn.exe -A HTTP/vWebTier SSTBService_SSRS
The syntax for the command is
setspn.exe -A {service}/{server}[:port] [{domain}{user account}]
As discussed earlier, you need to create a second SPN that’s similar to the previous one, but the second must have the fully qualified domain name (FQDN) for the server:
setspn.exe -A HTTP/vWebTier.SSTD.local SSTBService_SSRS
That takes care of the web server; now let’s look at the database server. The data tier needs to be in the same domain or a trusted domain within the Active Directory forest. For more information on domains and forests, see the sidebar titled “Forest, trees, and domains.” The SQL Server vDataTier is in the same domain, and the SQL Server service runs under the context of a domain user account, Service_SQL. The two registrations that we’ll need to enter are as follows:
setspn.exe -A MSSQLSVC/vDataTier SSTBService_SQL
setspn.exe -A MSSQLSVC/vDataTier.SSTD.local SSTBService_SQL
Forests, trees, and domains
Wikipedia explains the structure of the Active Directory in the following manner:
“The forest, tree, and domain are the logical parts in an AD network. The AD forest contains one or more transitive, trust-linked trees. A tree is a collection of one or more domains and domain trees, again linked in a transitive trust hierarchy.”
For a more in-depth explanation, please see http://en.wikipedia.org/wiki/Active_Directory.
This SQL Server is installed as a default instance, and therefore listens on port 1433 for SQL traffic. If the instance of SQL Server were configured on port 2433, then the registrations would change to look like this:
setspn.exe -A MSSQLSVC/vDataTier:2433 SSTBService_SQL
setspn.exe -A MSSQLSVC/vDataTier.SSTD.local:2433 SSTBService_SQL
Warning
It’s important to note the direction of the slashes that separate the service from the host and the domain from the account. The setspn tool won’t tell you if you have them incorrect!
Adding yet another tier to our example
Let’s say we have another server that an application from vWebTier attempts to access called vOLAPCube, and it houses SQL Server 2005 Analysis Services cubes for the sales department. The OLAP Services also runs under the domain user account Service_OLAP. The SPN necessary is
setspn.exe -A MSOLAPSvc.3/vOLAPCube SSTBService_OLAP
Constrained delegation
Kerberos delegation allows the authentication process to trust a computer or a user account to pass along credentials to another computer. This concept concerned some people, and rightly so, as it allows the account to pass credentials of the current user to any service on any server in the domain or forest. For that reason, constrained delegation was introduced with Windows Server 2003. This allows only specified services running on specified servers to impersonate a user, not carte blanche impersonation privileges for the account.
Figure 2 shows the dialog box with the Delegation tab of a user account participating in Kerberos constrained delegation. As configured, this account is only able to delegate credentials to the SQL Server Service on computer vDataTier over port 1433. Trust This User for Delegation to Specified Services Only is the option that enforces constrained delegation.
Figure 2. User account tab for Service_SSRS
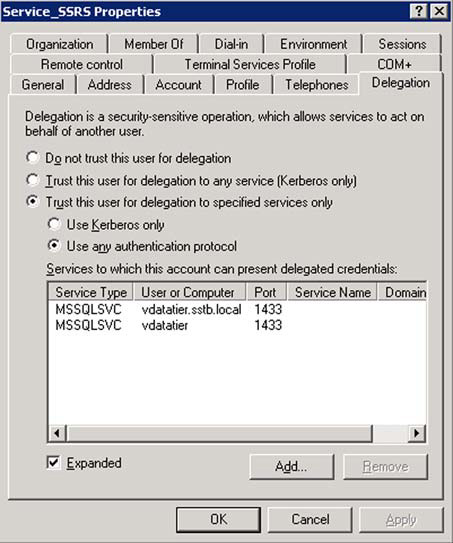
If a user clicks on the radio button next to Trust This User for Delegation to Any Service (Kerberos Only) then the account is unconstrained; this means that the account can impersonate the domain user when accessing any service on any machine. This scenario is shown in figure 2.
If the constrained delegation option isn’t showing up on the Delegation tab in figure 2, this could mean that you need to raise the domain functional level to a minimum of Windows Server 2003, as is shown in figure 3. To see the domain function level, have your domain admin open the Active Directory Domains and Trusts management console found in the Administrative Tools group located in the Control Panel. Once in the Active Directory Domains and Trusts console, right-click the domain and click Raise Domain Functional Level as shown in figure 4.
Figure 3. Dialog box showing that the current domain functional level is set to Windows Server 2003
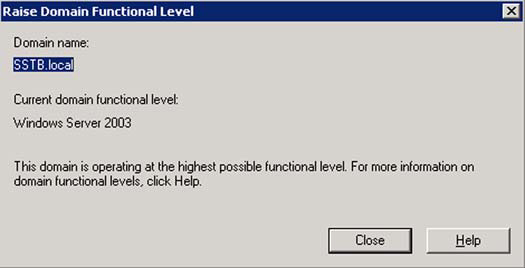
Figure 4. Checking the domain functional level within the Active Directory Domains and Trusts

Note
If your machines aren’t in the same Active Directory domain, but are within the same Active Directory forest and the domains trust one another, the forest functional level will need to be raised to Windows Server 2003 in addition to the domains. Raising the forest functional level can also be accomplished with the Active Directory Domains and Trust management console. Right-click Active Directory Domains and Trusts and click Raise Forest Functional Level, as shown in figure 5.
Figure 5. Checking the forest functional level within Active Directory Domains and Trusts

Implementing Kerberos delegation step by step
This section provides a checklist for each of the components needed to successfully implement Kerberos delegation. Get your domain admin or enterprise admin on board with this project early, as you’ll need them to do many of the tasks for you, especially in the Active Directory subsection.
Configuring the Active Directory
Many of the Active Directory requirements will likely already be in place, but there are some things worth checking. I don’t provide exhaustive explanations and solutions to these requirements, as further details can be found on the internet with your favorite search engine.
Time Sync
If the system time on the computers is more than a few minutes out of sync, you might want to look further into this item. You can adjust the tolerance which Kerberos forgives for the spread of the clocks, but it’s advisable to set up Time Services with a central time source with which to sync.
DNS
DNS is required for Kerberos, as it’s used in querying Active Directory service principle names (SPNs).
Same Domain or Trusted Domain in the Forest
The computers involved need to trust one another in order to encrypt and decrypt the Kerberos-delegated credentials passed from one tier to the next, as previously discussed and illustrated in figure 1.
Domain Users for Service Accounts
In order for Kerberos delegation to function, it’s necessary that the application tier have an IIS application pool configured with a domain user account. For the data tier, it’s possible to use LOCAL SYSTEM to run the SQL Server service; but I strongly recommend you use a domain account, as it’s generally considered a best practice to do so.
SPNs Set for Services
As shown in the section “Constrained delegation,” SPNs are added with setspn.exe. Ensure that SPNs are entered for all services participating in delegation. In our fictitious environment, we entered the following commands to register the SPNs:
setspn.exe -A HTTP/vWebTier SSTBService_SSRS
setspn.exe -A HTTP/vWebTier.SSTD.local SSTBService_SSRS
setspn.exe -A MSSQLSVC/vDataTier SSTBService_SQL
setspn.exe -A MSSQLSVC/vDataTier.SSTD.local SSTBService_SQL
No User Accounts are Marked as Sensitive
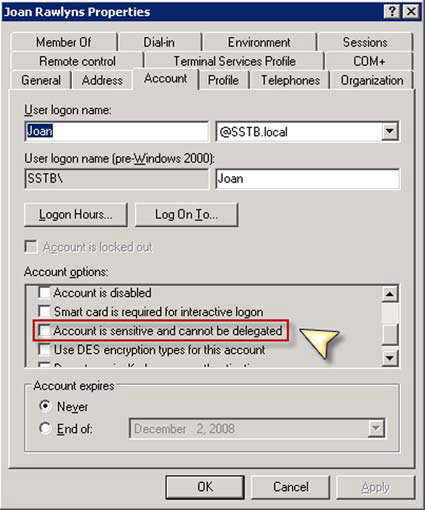
No accounts involved in Kerberos delegation can be marked as sensitive, or delegation won’t succeed. Your domain admin can check this by opening the Active Directory User and Computers management console found in the Administrative Tools group, located in the Control Panel. Once in there, right-click the users, click Properties, and click the Account tab to reveal the Account options, as shown in figure 6.
Figure 6. Properties of domain user account Joan Rawlyns showing that Account Is Sensitive and Cannot Be Delegated isn’t selected
Raise Forest Functional Level
If you plan on using constrained delegation, you’ll need to ensure your domain and forest functional levels are at a Windows Server 2003 level, as discussed earlier in the section “Constrained delegation.”
Set Accounts for Delegation in the Active Directory Users and Com- mputers Management Console
You’ll need to trust the user account for delegation under which the IIS Application pool runs. You accomplish this with the Active Directory User and Computers management console. Select either Trust This User for Delegation to Any Service (Kerberos Only) for unconstrained, or Trust This User for Delegation to Specified Services Only for constrained Kerberos delegation. In our example, shown back in figure 2, you see the Account tab of the user Service_SSRS configured with constrained Kerberos delegation.
Configuring the client tier
If the client computer was purchased in the last five years, it’s more than likely that the workstation meets the requirements for delegation. After meeting the AD requirements in the previous section, make sure the following points are addressed on the client side.
Windows 2000 or Higher for the Client Operating System
Kerberos delegation isn’t supported in any Windows operating system lower than Windows 2000.
Internet Explorer 5.X or Higher for Your Browser
As Internet Explorer is free, and most versions of Windows now come preinstalled with a newer version of IE, having version 5.5 or higher isn’t likely to be an issue.
LAN Settings
Deselect the option Automatically Detect Settings, as shown in figure 7. To get to the LAN Settings dialog box, go into the Windows Control Panel and choose Internet Options, select the Connections tab, and click on the LAN Settings button.
Figure 7. Confirm that the Automatically Detect Settings option is not selected, and ensure that you Bypass Proxy Server for Local Addresses if you do have a proxy server configured.

The Automatically Detect Settings option seems to be selected by default on many of the desktops that I’ve tested.
Note
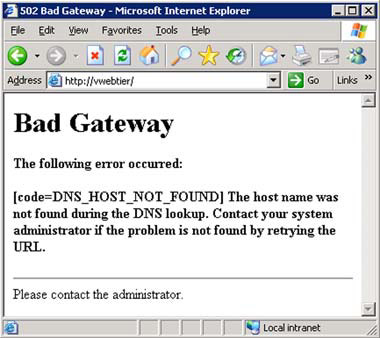
If you don’t deselect the Automatically Detect Settings option, you may be faced with some 502 Bad Gateway error messages, as shown in figure 8.
Figure 8. 502 Bad Gateway error message appears if Automatically Detect Settings is enabled.
If you have a proxy server, ensure that you configure it in the Local Area Network (LAN) Settings dialog box discussed previously, but ensure that you’ve also selected Bypass Proxy Server for Local Addresses. Figure 7 doesn’t show entries for a proxy, as no proxy is present in my environment, but you can see the options available to be enabled if required.
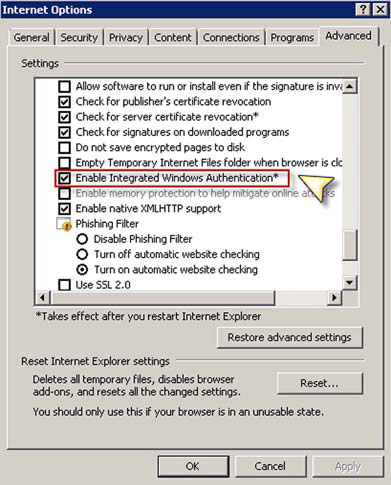
Set Enable Integrated Windows Authentication
Within the Advanced tab of the Internet Options dialog box, ensure that Enable Integrated Windows Authentication* is set, as shown in figure 9. To get to the Internet Options dialog box, go into the Windows Control Panel and choose Internet Options.
Figure 9. Ensuring that Enable Integrated Windows Authentication* is selected
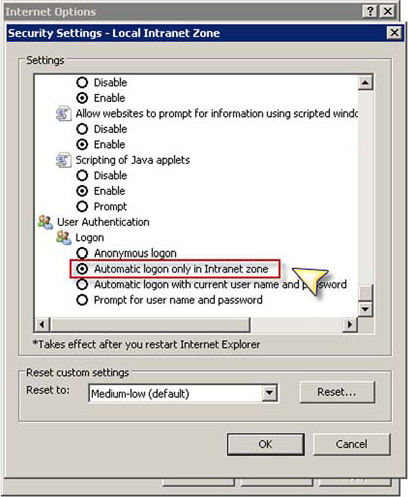
Set Automatic Logon Only in Intranet Zone
Security settings for the local intranet zone should have this option set as shown in figure 10. This is the default setting for this option.
Figure 10. Ensuring that Automatic Logon Only in Intranet Zone is selected
To get to the Security Settings - Local Intranet Zone dialog box from the Security tab of the Internet Options dialog box, first select the Local Intranet zone at the top of the box, and then click the Custom Level... button as shown in figure 11.
Figure 11. Accessing the local intranet zone’s security settings

The client requirements can be loosened to allow for other browsers and other operating systems on the client side if constrained delegation is used in conjunction with the Use Any Authentication Protocol option shown in figure 2. If this is selected, Kerberos isn’t required between the client and the server involved in the first hop. Kerberos is required, though, to make the second hop involving delegation. This configuration is also known as protocol transition and is discussed further in the resources provided in the section “Resources to assist in more complex infrastructures.”
Configuring the web tier
Now that the SPNs have been set, and the Active Directory and client tier requirements have been met, we must now configure the web tier. At this point, you’ll need to configure IIS to host the application. You might want to ask for some assistance from your system administrator or an IIS guru if this isn’t your area of expertise.
This section steps you though making the necessary configuration changes in IIS to support Kerberos delegation. In this section, we’ll configure the IIS web tier by calling the IIS Manager from the Administrative Tools group found in the Windows Control Panel.
Create an IIS Application Pool
To create a new application pool, right-click Application Pool and choose New Pool from within the IIS Manager management console. Give the pool a name and choose to use the default settings for the new application pool.
Configure the Application Pool to Use a Domain Account
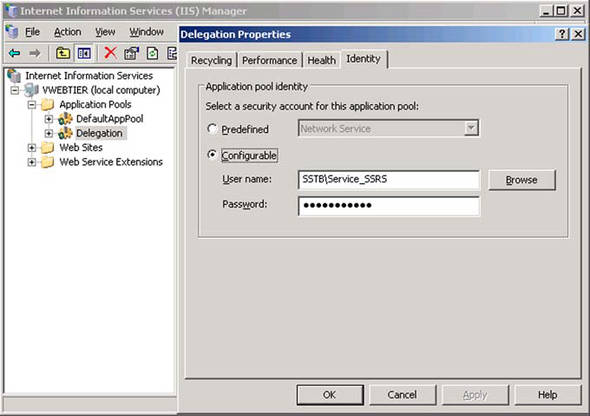
After creating the new application pool, right-click the entry and choose Properties. Click on the Identity tab, select the radio button next to Configurable, and enter the domain user account and password for which you earlier created an SPN. Figure 12 shows the new application pool Delegation, with the identity of SSTBService_SSRS.
Figure 12. Setting the identity of the application pool
Create a New Virtual Directory for Our Application
Now that we have an application pool, we need to set up a virtual directory within a website. To create a virtual directory, right-click the website in which you want the application to reside. Choose New > Virtual Directory to open the Virtual Directory Creation Wizard. Now enter the alias name for your virtual directory. In my example I’ve used the Default Web Site and used an alias of Delegation for the name of the virtual directory. Continue by specifying the path to the website’s ASP.NET code. Next ensure that you choose the permission Run Scripts (such as ASP), then choose Next and Finish.
Configure Virtual Directory to use Application Pool
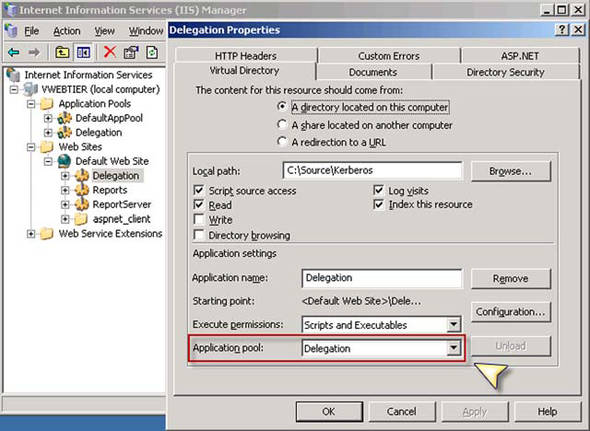
Now that we’ve created the virtual directory, we’ll need to make sure it uses the newly create application pool. Right-click the virtual directory, navigate to the Virtual Directory tab, and ensure that the drop-down selection box for Application Pool has the name of the pool that you recently created. This step is captured in the screenshot in figure 13.
Figure 13. Selecting the application pool you just created for your new virtual directory
Modify the Authentication Method for the Website
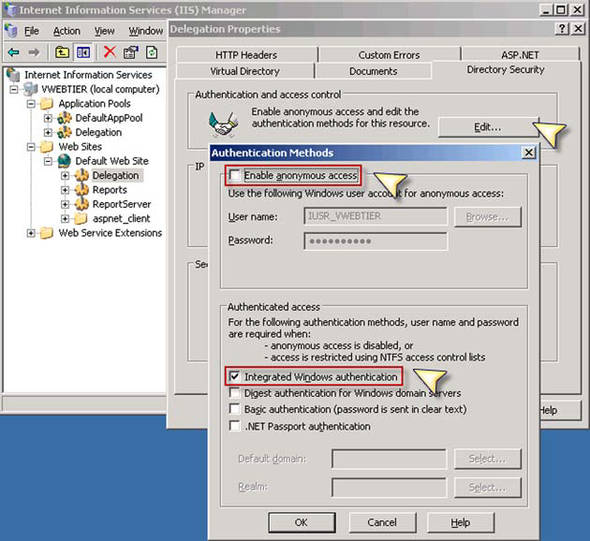
While we’re still in the virtual directory’s Properties dialog box, click on the Directory Security tab and click the Edit button to modify the authentication methods. In this dialog box, set Integrated Windows authentication and clear the Enable Anonymous Access option, as shown in figure 14.
Figure 14. Enabling integrated Windows authentication and disabling anonymous access
Enable the Default Content Page
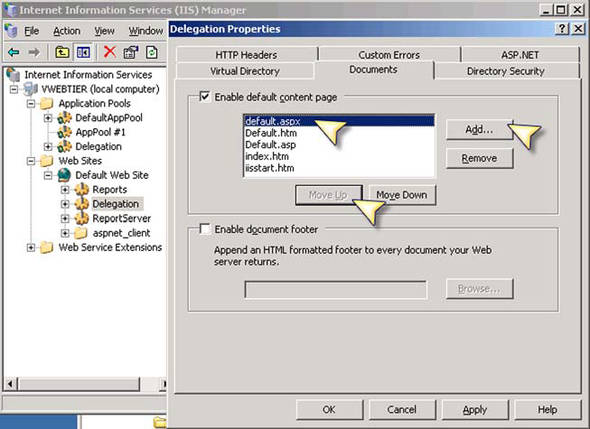
As the last step, we must ensure that the default page is chosen for the site. Specify the ASPX file that’s used for the landing page for this virtual directory. In our example, the page is called default.aspx. For easy navigation to the site content, ensure that you specify the page so that the user isn’t required to do so. Figure 15 shows the Add and Move Up buttons used to place our default page at the top of the list.
Figure 15. Enabling the default content page
Configuring the data tier
In our demonstration scenario, the SQL Server relational engine is the last stop for our Windows credentials to be passed. In order to achieve success, we must have the SQL Server service running under the same user account as we defined in the SPN, as discussed previously. To change this, we’d use the SQL Server Service Manager.
If this is the last machine and credentials don’t need to be passed to another machine, then setting the service’s user account to allow delegation isn’t necessary. These settings are only necessary if you have any distributed queries that use data sources located on another machine, requiring the credentials to hop to one more machine. Now that we’ve confirmed the last tier, it’s time to test out our configuration.
Validating delegation from end to end
Now it’s time to test whether we’ve successfully created an environment that will support Kerberos delegation. Luckily we have an application to let us know whether we were successful. This tool is called DelegConfig.
Downloading and installing DelegConfig
DelegConfig was developed by Brian Murphy-Booth from Microsoft, who has frequently had to work with clients to troubleshoot their Kerberos delegation issues. DelegConfig is an ASP.NET application that helps identify what’s preventing you from successfully accomplishing Kerberos delegation. DelegConfig is available from http://www.iis.net/1434/ItemPermalink.ashx. Installing the application on your middle-tier web server will confirm that you can connect from your client application (in this case Internet Explorer) to the IIS Server and pass your credentials on to a back-end database server with Kerberos delegation. Detailed installation instructions can be found here: http://blogs.iis.net/bretb/archive/2008/03/27/How-to-Use-DelegConfig.aspx.
Running DelegConfig from the web tier
DelegConfig can help create the necessary SPNs to make things work, as it can perform the same duties as setspn.exe. I prefer to use DelegConfig after my SPNs are in place. First run DelegConfig from the web tier; then, once successful, call DelegConfig from the client tier.
Running DelegConfig from the client tier
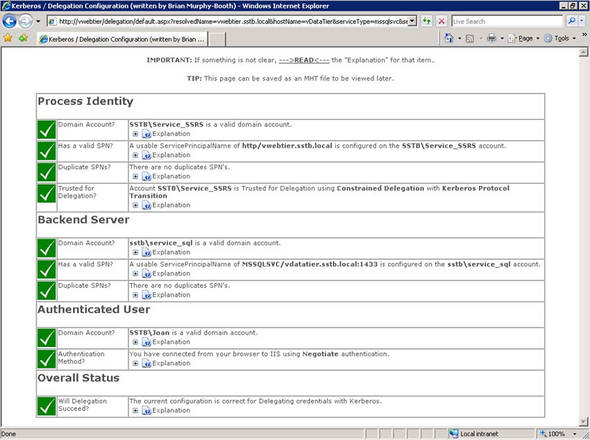
After successfully following the instructions in the “Downloading and installing DelegConfig” section, you should see results similar to figure 16, showing green check boxes. If not, don’t despair, as there are plenty of places to go for further assistance.
Figure 16. DelegConfig confirms a successful Kerberos implementation with big green check boxes.
First off, if DelegConfig doesn’t show a green check, it’ll likely point you in the right direction as to how to fix it. You’ll notice that each section has an expandable Explanation section with insight and background explaining what settings and configurations will lead you toward success. Additionally, revisit the instructions once again located at http://blogs.iis.net/bretb/archive/2008/03/27/How-to-Use-DelegConfig.aspx.
If you’re still stuck, the section “Resources to assist in more complex infrastructures” provides troubleshooting resources and tools to help expose what’s preventing you from successfully implementing Kerberos delegation.
Resources to assist in more complex infrastructures
These resources have proven helpful at bettering my understanding of the complexities of Kerberos delegation, and I hope you find them equally helpful.
Table 1 lists free tools that I’ve found useful. Table 2 lists various blog posts full of helpful information. Table 3 lists Microsoft TechNet articles related to Kerberos. Table 4 lists Microsoft Help and Support articles on the subject. Table 5 lists Microsoft white papers that may be of interest. Finally, table 6 lists some Microsoft webcasts that may be helpful.
Table 1. Free tools for testing and implementing
|
Title |
URL |
|---|---|
|
Windows Server 2003 Service Pack 2 32-bit Support Tools |
|
|
Windows Server 2003 Resource Kit Tools (contains KList.exe and KerbTray.exe for troubleshooting) |
|
|
DelegConfig (Kerberos/delegation configuration reporting tool) |
|
|
gssMonger—tool for verifying Kerberos authentication interoperability between Windows and other platforms |
|
|
Kerberos/delegation worksheet |
http://blogs.inetium.com/blogs/jdevries/archive/2006/06/26/245.aspx |
Table 2. Blog posts
|
Title and author |
URL |
|---|---|
|
Ask the Directory Services Team (all articles tagged with Kerberos) |
http://blogs.technet.com/askds/archive/tags/Kerberos/default.aspx |
|
Kerberos Delegation to SQL Server |
|
|
The Problem with Kerberos Delegation |
http://www.identitychaos.com/2008/03/problem-with-kerberosdelegation.html |
|
Spat’s Weblog: “Kerberos delegation .. end to end” |
Part I: http://blogs.msdn.com/spatdsg/archive/2007/11/14/kerberos-delegation-end-to-end-part-i.aspx Part 2: http://blogs.msdn.com/spatdsg/archive/2007/11/20/kerberos-delegation-end-to-end-part-ii.aspx Part 3: http://blogs.msdn.com/spatdsg/archive/2007/11/26/kerb-part-3.aspx |
|
DelegConfig (Kerberos/delegation configuration reporting tool) |
|
|
Essential Tips on Kerberos for SharePoint Developers |
http://blogs.msdn.com/james_world/archive/2007/08/20/essential-guide-to-kerberos-in-sharepoint.aspx |
|
Microsoft BI with Constrained Kerberos Delegation |
http://www.robkerr.com/post/2008/05/Microsoft-BI-with-Constrained-Kerberos-Delegation.aspx |
|
Enterprise Portal Kerberos Delegation for connecting to Reporting/Analysis Services on a different box |
|
|
Understanding Kerberos and NTLM authentication in SQL Server Connections |
|
|
SQL 2008, Kerberos and SPNs |
http://blogs.dirteam.com/blogs/tomek/archive/2008/04/09/sql-2008-kerberos-and-spns.aspx |
Table 3. Microsoft TechNet articles
|
Title |
URL |
|---|---|
|
Kerberos Authentication in Windows Server 2003: Technical Resources for IT Pros |
http://technet2.microsoft.com/windowsserver/en/technologies/featured/kerberos/default.mspx |
|
Kerberos Explained |
|
|
How to: Configure Windows Authentication in Reporting Services |
|
|
Configure Kerberos authentication (Office SharePoint Server) |
Table 4. Microsoft Help and Support articles pertaining to Kerberos delegation
|
Title |
URL |
|---|---|
|
Unable to negotiate Kerberos authentication after upgrading to Internet Explorer 6 |
|
|
How to enable Kerberos event logging |
|
|
How to configure IIS to support both the Kerberos protocol and the NTLM protocol for network authentication |
|
|
How to configure IIS Web site authentication in Windows Server 2003 |
|
|
How to use Kerberos authentication in SQL Server |
|
|
How to make sure that you are using Kerberos authentication when you create a remote connection to an instance of SQL Server 2005 |
|
|
How to configure a Windows SharePoint Services virtual server to use Kerberos authentication |
|
|
You receive an “HTTP Error 401.1 - Unauthorized: Access is denied due to invalid credentials” error message when you try to access a Web site that is part of an IIS 6.0 application pool |
|
|
Authentication may fail with “401.3” Error if Web site’s “Host Header” differs from server’s NetBIOS name |
|
|
How to troubleshoot the “Cannot generate SSPI context” error message |
Table 5. Microsoft white papers
|
Title |
URL |
|---|---|
|
Troubleshooting Kerberos Delegation |
|
|
Planning and Implementing Multitier Applications Using Windows Server 2003 Security Services |
|
|
Kerberos Protocol Transition and Constrained Delegation |
Downloadable: http://www.microsoft.com/downloads/details.aspx?FamilyID=f856a492-ad87-4362-96d9-cbdf843e6634&DisplayLang=en Online: http://technet.microsoft.com/en-us/library/cc739587.aspx |
|
Kerberos Authentication for Load Balanced Web Sites |
|
|
Troubleshooting Kerberos Errors |
|
|
Windows 2000 Kerberos Authentication |
Table 6. Microsoft webcasts
|
Title |
URL |
|---|---|
|
Introduction to Kerberos |
|
|
Troubleshooting Kerberos authentication with secure web applications & SQL Server |
|
|
How to understand, implement, and troubleshoot Kerberos double-hop authentication |
|
|
Configuring Microsoft SQL Server 2005 Analysis Services for Kerberos authentication |
|
|
Understanding, implementing, and troubleshooting Kerberos double-hop authentication |
Summary
Kerberos delegation is a method of securely transferring a user’s credentials from the client’s PC to the middle application tier such as a web server, then on to a back-end database tier. In the chapter, I discussed what service principle names (SPNs) are and how to register them. I explained constrained and unconstrained Kerberos delegation and how to configure accounts to support these two methods. I stepped through requirements for Active Directory and the client, web, and data tiers. I then stepped through implementing and testing Kerberos delegation.
I hope you have a better understanding of Kerberos delegation, and why and when you need it. Most of all, I hope that you were able to successfully implement Kerberos in your environment after reading this chapter.
About the author

Scott Stauffer is an independent consultant working out of the metro Vancouver area, assisting clients with data systems solutions to their business challenges. He has worked in IT for more than 13 years, and although Scott has managed systems with early version SQL Server on OS/2, he really started digging deep into SQL Server with the release of SQL Server 6.5. With a keen interest in continuous learning, sharing knowledge, and building community, Scott founded the Vancouver PASS chapter (http://www.Vancouver.SQLPASS.org) back in September 2004. More recently, he started the Vancouver BI PASS chapter (http://www.VancouverBI.SQLPASS.org) in order to dive deep into the business intelligence features that SQL Server has to offer.
