Session settings are needed to protect the customer data from getting hacked. Imagine that your session timeout time is 2 hours; this implies that once an attacker obtains the session ID or once a session ID is generated, the session ID will remain active for 2 hours. It's advisable to set the timeout time value as low as possible.
The following screenshot shows the Session Settings page, where an administrator can configure the Timeout value under Session Timeout for his application users:
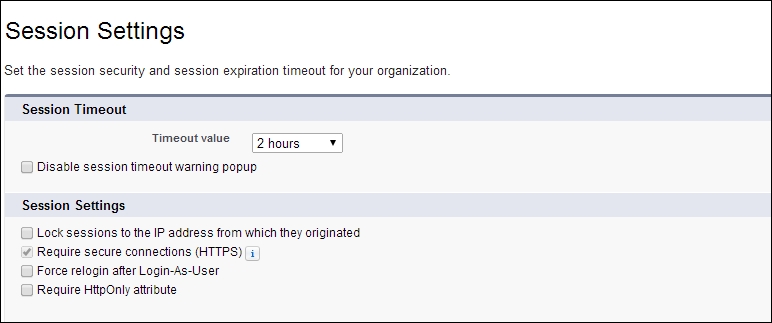
If you have logged in to Salesforce, sometimes you would have observed that we don't need to retype the complete login credentials; this feature can be disabled as a security measure.
The following screenshot shows the Caching and Autocomplete login configurations for the application. Some organizations prefer SMS-based authentication, and one can enable this as shown in the screenshot. Sometimes, there is a risk of pages getting iFramed to other websites. This is technically called as clickjacking. In order to prevent clickjacking, Salesforce provides options to protect the setup, non-setup, and Visualforce pages (pages custom built by the developer) against clickjacking.
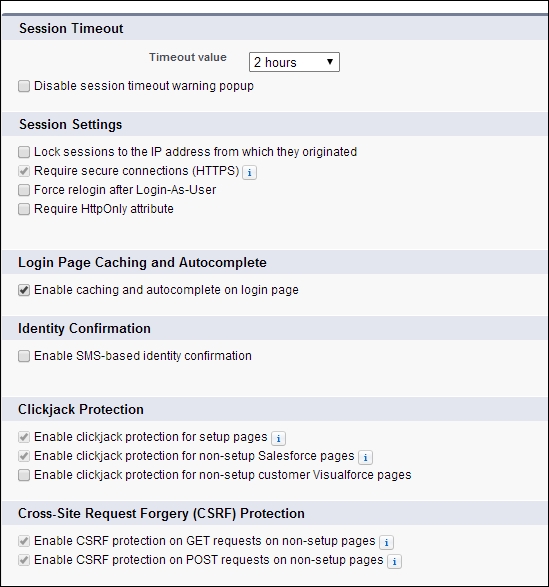
In Cross-Site Request Forgery (CSRF), an attacker uses the cookie of the browser to obtain session information and then performs a malicious attack on the website. The administrators can prevent non-setup pages from this attack, as shown in the preceding screenshot.
