Drummond Reed and Alex Preukschat
By now, it should be clear that SSI is not just a point technology, like web shopping carts or mapping apps. It is a fundamental technology shift, akin to the internet or the web itself. As such, it doesn’t have just one primary feature or benefit—or even just a small set of them. Rather, it offers an entire spectrum of features and benefits that vary in their impact depending on the particular use cases, application, or industry.
The reason is that the SSI digital identity model solves fundamental problems in digital trust, and it does so at an infrastructure level—much like the internet solves fundamental problems in data sharing at an infrastructure level. So, just like the internet, SSI can eliminate the need for thousands of smaller “bandage” solutions by providing a solid layer of open standard infrastructure.
This approach provides a wide swath of benefits for almost anyone using the internet, and that’s what we’ll explore in this chapter. To do this, we’ve developed a tool, the SSI Scorecard, that classifies 25 major features and benefits of SSI into the five categories shown in table 4.1. In part 4 of this book, we use this SSI Scorecard to analyze the impact of SSI across the use cases for a representative set of industry verticals.
The five categories are as follows:
-
Bottom line —Features and benefits that deliver directly to a company’s bottom line because of cost reduction or new revenue opportunities made possible with SSI.
-
Business efficiencies —Features and benefits of SSI that enable the digital transformation of business via business process automation (BPA).
-
User experience and convenience —The same five features and benefits as the business efficiencies category, but through the lens of how they benefit the end user.
-
Relationship management —Features and benefits focused on how SSI will transform aspects of customer relationship management (CRM), digital marketing, and loyalty programs.
-
Regulatory compliance —Features and benefits based on how SSI will strengthen cybersecurity and cyberprivacy infrastructure and automated how companies can comply with regulations.
Table 4.1 SSI Scorecard is a tool for analyzing the impact of SSI for any use case, application, industry, or vertical market.
4.1 Feature/benefit category 1: Bottom line
This category represents the easiest sale in business: features and benefits that deliver directly to a company’s bottom line, that is, they either make a company more money or save it money—quickly. Following are five ways SSI can do this.
4.1.1 Fraud reduction
The first and fastest way SSI can help the bottom line is by reducing fraud. Javelin Strategy reported that in 2016, 15.4 million consumers were victims of identity theft or fraud, costing a total of $16 billion in losses [1]. Javelin also reported that new account fraud—criminals opening up new accounts under victims’ names—increased from $3 billion in 2017 to $3.4 billion in 2018 [2].
Although the potential savings from fraud reduction vary by industry segment, it is one of the largest potential sources of savings for some industries. For example, the National Health Care Anti-Fraud Association estimates that in 2017, health care fraud cost the United States about $68 billion annually—about 3% of the nation’s $2.26 trillion in health care spending.
Bottom line: even if fraud reduction were the only benefit of SSI, it would warrant a massive investment by businesses and governments worldwide. Indeed, fraud reduction is one of the primary reasons the global credit union industry is embracing SSI as its first significant use of blockchain technology by introducing the MemberPass digital credential as a standard way for any credit union member to prove their identity (https://www.memberpass.com).
4.1.2 Reduced customer onboarding costs
The cost of customer onboarding varies by industry, but in financial services, in particular, the cost of Know Your Customer (KYC) compliance has gone through the roof. According to Thomson Reuters, out of 92% of the firms it surveyed, KYC onboarding processes cost an average of $28.5 million [3]. Ten percent of the world’s top financial institutions spend at least $100 million annually on it [4]. And onboarding a new financial services customer takes anywhere from one to three months on average [5].
There is also a steep cost for not being compliant with these regulations. In 2018, Fenergo reported that a staggering $26 billion in fines had been imposed on financial institutions worldwide for non-compliance with KYC, Anti-Money Laundering (AML), and sanctions regulations in the last decade [6].
Although SSI in general and verifiable credentials in particular are not a silver bullet for all the complexity of automating customer onboarding and ensuring KYC and AML compliance, they are a major new weapon in this arms race—a weapon that benefits all three sides: customers, financial institutions, and regulators. By securely and privately digitizing the information that companies must gather from their customers under these regulations—and enabling it to be cryptographically verified in real time with a full audit trail—SSI has the potential to save all three groups many billions of dollars annually. And it can reduce customer onboarding time from months to days or even hours.
4.1.3 Improved e-commerce sales
Statista reported that in 2019, an estimated 1.92 billion people purchased goods or services online, and e-retail sales passed $3.5 trillion [7]. Nasdaq predicts that by 2040, around 95% of all purchases are expected to be via e-commerce [8].
More than a third of online Black Friday 2018 sales were completed on smartphones [9]. But on average, only 2.58% of e-commerce website visits convert into a purchase [10]. The global cart abandonment rate for e-commerce is close to 70%. The Baymard Institute averaged rates from 40 different studies, which give rates from as low as 55% to as high as 81%, to arrive at a global average of 69.89% [11].
When you add the fact that 80% of online shoppers stop doing business with a company because of poor customer experience [12], the improved convenience (no forms to complete), privacy (minimal disclosure through zero-knowledge proof attestations), and safety (automatic blinding of purchase data) of shopping with an SSI digital wallet means the impact of SSI on improving e-commerce sales is something that no online merchant can afford to ignore.
Of course, SSI technology alone can’t make up for poor website design, missing information, or low-quality products. But by removing so much of the friction from the web shopping experience, SSI digital wallets can help level the playing field between smaller e-commerce sites and giants like Amazon and Alibaba.
4.1.4 Reduced customer service costs
Customer service has become one of the primary battlegrounds of modern business. Gartner predicts that 89% of businesses are expected to compete mainly on customer experience [13].
But it is an expensive proposition. Forbes reports that in 2018, businesses were losing $75 billion per year through poor customer service—up $13 billion since 2016 [14]. According to Infosecurity Magazine, just one persistent customer service issue—lost passwords—costs businesses an average of over $60 per incident [15].
SSI can have a significant impact on improving the customer experience (CX) and reducing customer-service costs. Passwordless authentication is only the start—the rest of this chapter is filled with examples such as permanent connections (no more losing track of customers), premium private channels, workflow automation, and integrated loyalty management. All of this goes straight to the bottom line—84% of companies that improve their CX report an increase in their revenue [16].
4.1.5 New credential issuer revenue
All of the preceding features and benefits apply to a company’s existing lines of business. SSI also opens up new revenue opportunities for a surprisingly wide variety of companies. Any business whose interaction with its customers produces a measure of knowledge about their attributes and interests—or a measure of trust in their behavior—is now in a position to monetize that data in a permissioned and privacy-respecting way: by issuing customers (suppliers, partners, contractors, and others) verifiable credentials that help them use this knowledge. Even better, customers can be the distribution channel for this knowledge to verifiers who need it.
And verifiers will pay for that valuable knowledge for the same reason they pay for customer profile data (from data brokers), credit history (from credit rating agencies), background checks (from background verification companies), and other customer data sources today. SSI can transform this current market much as the web transformed the newspaper classifieds market, the auction market, and the retail market. For example, SSI can provide the following:
-
Broader, richer, and more diverse profiles of the customer than those available from third-party sources today
-
Fully permissioned and GDPR-compliant data because the customer is the vehicle for sharing the information for their own benefit
-
Fresher, richer, and more contextual data about preferences, interests, and relationships
-
Selective disclosure of attributes (meaning data owners can choose which pieces of data they want to share)—something that is all but impossible for business-to-business data sharing that takes place behind the customer’s back
4.2 Feature/benefit category 2: Business efficiencies
As important as the immediate bottom line is, SSI’s larger impact will be in re-engineering business processes—a field known as business process automation (BPA) or, more broadly, digital transformation. This kind of paradigm shift does not happen very often; it is analogous to the transition businesses underwent from snail mail to email, from phones to fax machines, and from paper to the web.
As we illustrated in chapter 3, these efficiencies are not limited to just one area of business but accumulate across entire workflows and even across entire industries. In this section, we look at five areas where SSI can directly impact business efficiencies.
4.2.1 Auto-authentication
Perhaps no area of web experience is more despised by individuals and companies alike than login. The 2015 TeleSign Consumer Account Security Report said the following [17]:
-
54% of people use 5 or fewer passwords across their entire online life.
-
7 in 10 people no longer trust passwords to protect their online accounts.
In 2019, Auth0 reported that [18]
-
The average American email address has 130 accounts registered to it [19].
-
The number of accounts per user is doubling every 5 years [20].
-
58% of users admit to forgetting their password frequently [20].
-
The average internet user receives roughly 37 “forgot password” emails each year [20].
But besides the sheer hassle, the real impact of username/password-based login is the friction:
-
The average person has between 7 and 25 accounts that they log in to every day [21].
-
Around 82% of people have forgotten a password used on a website [22].
-
Password recovery is the number-one request to help desks for intranets that don’t have single sign-on portal capabilities [20].
In short, by moving from conventional login to SSI auto-authentication—using an SSI digital wallet to automatically exchange strong cryptographic proofs instead of a username and password—we can finally “kill the password.” (For an example of how this works, see the third scenario in chapter 3. For technical details, see chapters 5 and 7.) It will be like replacing frequent, error-prone toll booths with a wide-open, well-paved highway. Everyone can go about their business faster, more easily, and more safely.
4.2.2 Auto-authorization
Authentication (login) is just the first step in most trusted business processes. It proves that you are the rightful owner of an account. But it does not answer the next questions: What are you authorized to do? What privileges should you be granted? What actions can you take?
In the world of identity and access management (IAM), this is called authorization. It is an even more challenging problem than authentication. But this is where verifiable credentials truly shine. To use the analogy illustrated in figure 4.1, if verifiable credentials are a hammer, then authentication is only a thumbtack. Authorization is a full 16-penny nail.
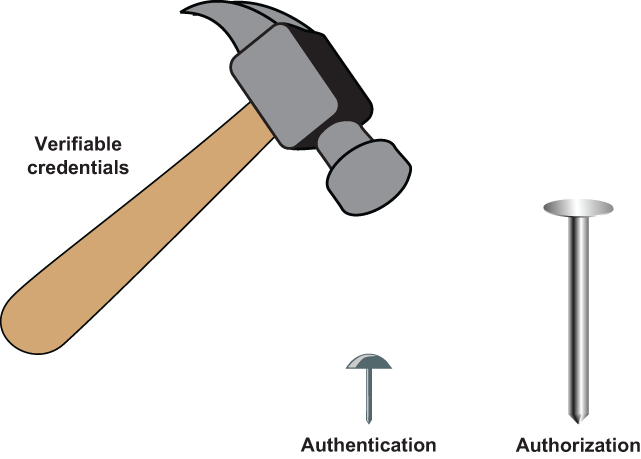
Figure 4.1 While authentication is important, authorization is actually a much bigger nail for the SSI verifiable credentials hammer to hit.
The reason verifiable credentials are such a powerful tool for authorization is that they can solve three hard problems in one stroke:
-
They can provide exactly the right claims needed for an authorization decision. These decisions are made by applying the verifier’s access control policies. Attribute-based access control [23] is based on specific attributes of the identity owner: age, gender, zip code, browser type, and so on. Role-based access control is based on the role or roles of the identity owner: employee, contractor, customer, regulator, etc. Either way, verifiable credentials represent the fastest and easiest way for the verifier to request and the holder to supply the precise claims needed. See chapter 7 for details.
-
They can be cryptographically verified in real time. To be confident in an authorization decision, a verifier must trust the claims being presented. As explained in chapter 2, the whole point of SSI architecture is to enable a verifier’s agent to verify the issuer’s signature on the holder’s proof in seconds.
-
They can be bound to the holder of the credential as the authorized party. One of the greatest sources of fraud is stolen usernames/passwords—they have grown into a $6 billion annual market precisely because they are not verifiable [24]. With verifiable credentials, there are several techniques for proving that the claims they contain were issued to the credential holder. These include sharing proof of a biometric for the holder and cryptographically linking credentials to a holder using zero-knowledge proofs (ZKPs). See chapters 5, 6, and 7 for details.
Using a verifiable-credentials model, a verifier’s job can be simplified into three steps:
-
Determine the set of claims —attributes describing the subject of a verifiable credential (for example, age, location, employment, education)—that the verifier needs for any particular authorization decision.
-
Determine the issuers—or governance framework —that the verifier trusts for those claims. See chapter 11 for details.
-
Make it easy for users to acquire those credentials so the user experience is as simple and seamless as possible. See chapter 7.
But the SSI model can go one step further in business efficiency. Once a user has established a connection with a verifier and approved sharing the claims necessary to meet the verifier’s policies, the user can apply their own policies to this process. For example, the user can instruct their SSI agent (such as a mobile wallet or a cloud agent—see chapter 9) to automatically share the same claims with the verifier when the user needs to repeat a business process in the future (order a supply, approve a budget, publish a web page).
The entire authentication and authorization process for a user—even if quite sophisticated—can be automated to the point it is carried out entirely by the user’s and verifier’s respective agents, including the audit trail needed for accountability. Obviously, this is a big win for users (see section 4.3). However, for verifiers, the benefits of auto-authorization can be on the same order as the benefits of credit cards for merchants: customers can perform an essential exchange of information far more easily and painlessly, accelerating business for everyone.
4.2.3 Workflow automation
Every business process has a workflow: the series of steps that must be performed to carry it out end-to-end. Each step that crosses a trust boundary—branch to branch, customer to merchant, supplier to vendor, company to government—typically requires the authentication and authorization processes described previously. So SSI agents can already wring out major inefficiencies just by performing auto-authentication and auto-authorization.
But those same agents can also apply the business logic necessary to orchestrate the steps in the process no matter how many trust boundaries it crosses. This is the heart of business process automation (BPA): designing a business process so humans are doing only the steps that require their expertise, awareness, judgment, and empathy. The rest can be assigned to digital agents (which in some cases may further reassign it to robots). Besides enacting the trust infrastructure necessary to do this work safely, SSI agents are ideal for BPA because they can literally “follow a script”—in this case, JavaScript or a similar programming language that instructs them to apply each step in the flow of a business process. Agents can be pre-programmed with such scripts, or they can download them dynamically via SSI connections with orchestration agents whose job it is to maintain a library of the current scripts required for a specific business process.
SSI is a significant leap forward in BPA because process improvements no longer need to be limited to a single company or a single supply chain. Like the internet and the web, SSI enables BPA workflows to be carried out across any set of trust boundaries, according to any set of policies (governance framework—see chapter 11) agreed to by the participants. It is truly “worldwide BPA.”
4.2.4 Delegation and guardianship
Digital agents can be given instructions and assigned responsibilities via program code. But most business processes require specific human workers to perform specific functions or make specific decisions as part of the process. How are those humans assigned those responsibilities?
This is the job of a subclass of verifiable credentials called delegation credentials. They are how a holder can prove that they have the authority to carry out a specific task or make a specific decision as part of a business process. The following are some common examples in a corporate context:
-
Employees can be given a delegation credential to send tweets from the company’s Twitter account or post new articles to the company’s blog.
-
Drivers can be given a delegation credential to pick up and deliver goods on behalf of the company.
-
Officers can be given specific delegation credentials authorizing them to execute specific types of contracts on behalf of the company: HR officers to sign an employment contract, procurement officers to sign a purchase order, CFOs to execute a bank order, and so on.
-
Board members can be given delegation credentials to execute electronic board votes that do not require them to be physically present for a meeting.
There are countless more examples from every context that needs to carry out business processes—governments, schools, non-profits, churches, even households. For example, parents could use delegation credentials to specify how much screen time their children are allowed or what kinds of foods they are permitted to buy for lunch at school.
The parental example brings up another case: taking responsibility for an individual who is not in a position to wield SSI technology on their own. There are many examples besides babies or young children: the elderly, individuals with disabilities, refugees and displaced peoples, and individuals without mobile phones or internet access.
To enjoy the same rights to self-sovereign identity as everyone else, these individuals need digital guardians—individuals or organizations who can operate SSI agents and wallets on their behalf. This form of “complete delegation” is carried out using a guardianship credential. It acts much like the digital equivalent of a guardianship order from a court (and may be authorized by such an order once court systems begin officially recognizing verifiable credentials). It enables the guardian to set up and operate an SSI agent and wallet on behalf of the dependent and, when necessary, prove that they are acting in the capacity of a guardian. This extends the benefits of SSI to any person regardless of physical, mental, or financial capacity.
note Official legal recognition of verifiable credentials for guardianship of dementia patients is already being explored in the Province of Ontario, Canada. See https://www.secours.io.
4.2.5 Payment and value exchange
Mention the phrase digital wallet, and the first thought that comes to many people’s minds is payments—because that’s the primary task for which we use our physical wallets today (figure 4.2). If digital wallets are the core metaphor for SSI, people will expect them to be used for payment in addition to identity.

Figure 4.2 Digital wallets are the core metaphor for SSI—so it feels natural that they would be applied to payments.
Indeed, since SSI digital wallets incorporate everything necessary for the trusted exchange of digital information—DIDs, private connections, private keys, agent endpoints—extending them to the safe exchange of digital payments is very natural. The good news is
-
From the standpoint of SSI agents, payments are just another type of workflow.
-
SSI wallets can be designed to work with any type of currency (including cryptocurrencies) as well as with any type of payment system or network (including credit/debit card networks).
-
With digital wallets and verifiable credentials, payment can be integrated directly into workflows that require KYC and AML, as discussed earlier.
Even better news: payments are just one type of value exchange that can be automated using SSI. The term payment usually means a specific type of currency—fiat currencies like dollars, pounds, euros, and yen, or cryptocurrencies like bitcoin and ether. However, there are many additional means of value storage and exchange: points, airline miles, coupons, and other loyalty programs. And SSI digital wallets and agents can be used for all of them as fast as these value-exchange systems can be translated to verifiable credentials and agent-to-agent protocols. (See section 4.4.5.)
This, in turn, means payments can be integrated into almost any business process workflow at almost any level of assurance and regulatory compliance. Payment automation is the frosting on the SSI-enabled BPA cake.
4.3 Feature/benefit category 3: User experience and convenience
This category looks at the same five features and benefits as the last category (business efficiencies), but this time through the lens of how they benefit the end user.
4.3.1 Auto-authentication
How much do users hate passwords? A July 2019 study by MobileIon reported in Security InfoCenter [25] said that when users encounter password troubles,
-
IT security leaders felt they could reduce their risk of breach by almost half (43%) by eliminating passwords.
-
86% of those security leaders would do away with passwords if they could.
-
88% of these leaders believed that in the near future, mobile devices will serve as individuals’ digital ID to access enterprise services and data.
In February 2019, user-centric biometric authentication leader Veridium published a study of more than 1,000 U.S. adults who have experience with biometrics (such as Apple’s TouchID or FaceID) that found 70% wanted to expand their use into everyday login [26]. Speed (35%), security (31%), and not having to remember passwords (33%) were cited as the primary incentives.
On May 1, 2018, Microsoft announced in a blog post that it was “Building a world without passwords” [27]:
Nobody likes passwords. They are inconvenient, insecure, and expensive. In fact, we dislike them so much that we’ve been busy at work trying to create a world without them—a world without passwords.
This is why Microsoft has been a major supporter of DIDs—the decentralized identifiers at the core of SSI—and is building DID-based passwordless authentication into multiple products (see https://www.microsoft.com/en-us/security/business/identity/own-your-identity).
In short, the age of the password is about to pass, and for users everywhere, it could not come fast enough. There will be rejoicing in the streets.
4.3.2 Auto-authorization
If passwordless auto-authentication replaces the login screen, auto-authorization will replace many (but not all) web forms. Can you hear more rejoicing?
Here are some realities about online forms:
-
81% of people have abandoned a form after beginning to fill it out [28].
-
29% of people cite security reasons as one of their main concerns when completing online forms [29].
-
More than 67% of site visitors will abandon a form forever if they encounter any complications; only 20% will follow up with the company in some way [29].
-
23% of people will not fill out a checkout form if the company requires them to create a user account [29].
-
Better checkout design can reduce form abandonment by as much as 35%, which translates into nearly $260 billion in recovered orders [29].
When you stop to think about it, SSI auto-authorization solves almost every typical complaint about online forms:
-
There is no typing. All the information being requested by the verifier is transferred from claims to your digital wallet. And even if new self-attested data is requested, your agent can capture it for you so you’ll never have to type it again.
-
Your connection is your account. The whole idea of “click here to automatically create an account with this form data” goes away. You automatically have an “account” anywhere you have a connection.
-
Data verification is built in. The main point of verifiable credentials is that the issuer has already vetted the claims data.
-
Security is built-in. All proofs and data sent by your SSI agent automatically use your encrypted private connection with the verifier.
-
Privacy and selective disclosure are built in. First, verifiers can now ask only for the minimum information they need—reducing their potential liability. Second, the proof your agent sends can be read only by the verifier. If the verifier needs a copy of the underlying data (e.g., asks you to share your actual birth date instead of just proving you are over 18), your agent should be able to automatically warn you if that data will not be covered by a satisfactory privacy policy or governance framework.
-
Auditing is built in. Your agent can automatically track all the information you share—without requiring you to share that history with anyone else.
In addition, verifiable credentials let you prove many more things about yourself—as an individual, a student, an employee, a volunteer, or in any other role you play—than you could prove via any web form today. With auto-authorization, your ability to perform tasks online comes much closer to your ability to perform those same tasks in the real world—i.e., using your physical wallet, paper credentials, and face-to-face verification—but orders of magnitude faster.
4.3.3 Workflow automation
From the standpoint of the end user, SSI has the potential to reduce workflow steps that currently can take hours or days to as little as pressing a few buttons on a smartphone. One such scenario—selling a car and transferring the title and registration from one owner to another—was described in detail in chapter 3.
Many more of these scenarios are covered in part 4, where we examine the impact of SSI across different industries and vertical markets. You will see the same patterns repeated over and over: a business process carried out, step by step, by employees, contractors, suppliers, regulators, and other participants exchanging verifiable credentials (or digitally signed messages authorized by these credentials) between their agents and wallets. For every step, all of the following are performed automatically for the user:
-
Verification that the step is being performed in the right sequence of the business process (and its preconditions have been met).
-
Validation that the claims or messages meet the requirements of the business process.
-
Routing of the credential or message produced to the next agent or agents needed in the process.
-
Logging of the action taken to provide a full digitally signed audit trail (or even automated reporting to regulators—see section 4.5.5).
Perhaps the ultimate example of consumers experiencing the convenience of SSI-enabled workflow automation is the perennial change-of-address problem. An individual is moving house and needs to inform dozens if not hundreds of agencies, suppliers, and contacts about the new address. Despite the advent of the internet and the web, this is still an excruciatingly labor-intensive process for the individual. The main reason? Account takeover. A fraudulent change of address is the first step in hijacking a bank account, credit card account, company account, or other valuable account to steal from it—or use that account to steal from others. So companies need to add extra hoops for you to jump through to ensure that it’s really you requesting a change of address.
With SSI and verifiable credentials, a change of address can be performed in three easy steps:
-
Obtain a verifiable credential of your new address from a widely trusted issuer.
-
Send a proof of that credential over all your connections who need to know your new address.
-
Each of their back-end systems can verify the proof and update their systems with your new address with high confidence that it is valid.
Voilà. Tens of hours of human labor and hundreds of dollars in business savings for every single change-of-address notification. Given that in America alone, an average of 35 million people move house every year [30], this alone adds up to hundreds of millions of person-hours and hundreds of billions of dollars in savings every year.
4.3.4 Delegation and guardianship
As we described earlier, delegation credentials enable much of this workflow automation magic. Fortunately, the process of obtaining (or assigning) delegation credentials is just another workflow. The delegator first establishes a connection with the delegate (or vice versa) and then issues a credential granting the necessary authorizations.
As we cover in more technical detail in part 2, delegation credentials can be revised or revoked as conditions and positions change, with both the requirements and the current status being maintained by orchestration agents. All of this can be set forth in one or more governance frameworks that define the legal and business rules applying to the entire business process, whether it is taking place entirely inside one company, across a supply chain, across an entire industry, or in a wide-open process such as international shipping that crosses multiple industries and government jurisdictions. As a general rule, if humans can define the rules of the process, including who can make what decisions when, then SSI agents, wallets, and verifiable credentials can be used to automate the necessary exchanges of data. The end result is that many of today’s most difficult user experience challenges—especially entering or interpreting data presented by machines—can be simplified by focusing on the analysis and decisions that humans really need to make.
4.3.5 Payment and value exchange
For decades, the challenge of moving money safely has been the focus of entire industries—banking, credit unions, credit cards, and now cryptocurrencies. It is the very heart of human economic activity. And, like the human heart, it is the most vulnerable to attackers. As Willie Sutton famously answered when asked why he robbed banks, “Because that’s where the money is.”
So there has always been a tension between making it easier to move money and making it safe to do so. Every means of value transfer from Pony Express to PayPal has spawned a new legion of criminals to exploit it. Cryptocurrencies—arguably the most friction-free way to move money ever invented—are no different. CoinDesk reported that in the first nine months of 2018, nearly $1 billion had been stolen from cryptocurrency exchanges and other crypto holders [31]. This shows that the easier it becomes to move money, the easier it can become to steal it unless the proper protections are put in place.
note In 2017, during the CoinDash ICO, a hacker compromised the CoinDash website (Wordpress) to substitute their own crypto wallet address for the legitimate CoinDash wallet address. As a result, customers thinking they were purchasing from CoinDash ended up sending over $7 million to the hacker. If verifiable SSI authentications had been in place, customers would have been immediately warned that the attacker’s wallet address didn't authenticate properly, which would have signaled them that they were sending money to the wrong wallet. See Yuval M., 2017, “CoinDash TGE Hack findings report 15.11.17,” CoinDash, https://blog.coindash.io/coindash-tge-hack-findings-report-15-11-17-9657465192e1.
While SSI is not a panacea, it does provide a complete infrastructure for trusted information exchange. This includes payments and other forms of value exchange as discussed earlier. With all of the protections that SSI digital agents, wallets, connections, and verifiable credentials provide, SSI could be the infrastructure that finally—from the perspective of end-user experience—makes digital payments one-click easy and secure at the same time.
The effect on digital commerce can be profound. Amazon’s one-click purchasing capability famously helped vault it to the forefront of e-commerce. With the expiration of Amazon’s one-click patent [32] and the arrival of an SSI payments infrastructure, a feature that once exclusively belonged to Amazon could now become “one click everywhere.”
4.4 Feature/benefit category 4: Relationship management
While saving time and money is important, another category of features and benefits is not purely monetary: those that increase the trust, productivity, and value of relationships. Customer relationship management (CRM) is already a dominant industry in its own right. In January 2019, Forbes reported that [33]
-
CRM now makes up nearly 25% of the entire enterprise software revenue market.
-
Worldwide spending on CRM software grew 15.6% to reach $48.2 billion in 2018.
-
Salesforce is the leader, with 19.5% of the CRM market, followed by SAP at 8.3%.
The impact of SSI on CRM has long been anticipated by a movement known as vendor relationship management (VRM). Its leader, Doc Searls, who led Project VRM at the Harvard Berkman Center for three years, pithily summarizes VRM as “the inverse of CRM.” In other words, VRM is about how customers can control their relationships with companies instead of how companies can control their relationships with customers. Doc wrote the foreword to this book because of how deeply intertwined SSI and VRM have become over the past decade.
This section examines five key ways that SSI will enable better relationship management in both directions.
4.4.1 Mutual authentication
The first place SSI can improve relationships is right at the very start. This is when the parties are most vulnerable—when they are meeting each other for the first time, especially digitally.
On the web today, this is a struggle from both sides. First, imagine how hard it is for a website to prove that it is authentic when phishing sites and phishing emails have become so good that even trained professionals can have a hard time spotting them. (During the writing of this book, one of the co-authors received an email from his bank—a household brand—that was so realistic, it took three phone calls to determine it was a phishing attempt.) Verizon’s 2018 Data Breach Incident Report said phishing accounted for 93% of all data breaches [34]. Between October 2013 and May 2018, the U.S. Federal Bureau of Investigation (FBI) reported $12.5 billion in company losses due to phishing [35].
Now turn the tables and think about how hard it is for you, the end user, to prove to a website that anything about yourself is authentic. Most of us have a hard time even proving we are human. How many of us have tripped up over something like figure 4.3?

Figure 4.3 A CAPTCHA (completely automated public Turing test to tell computers and humans apart) can often be difficult for even a real human to pass.
If it’s that hard to prove you are even human, imagine how hard it is to prove these:
Generally, these tasks are impossible over the internet without first proving your real-world identity to the website (somehow) and then having the website independently verify information about you from some authoritative source (like a credit rating agency)—or worse, a data broker that may or may not have accurate information about you (let alone permission from you to share it).
This problem has become acute in both directions—and SSI can solve it in both directions. The beauty of SSI auto-authentication (see the earlier sections) is that your agent can share verifiable credentials with a website, and the website’s agent can share verifiable credentials with you. Both agents can automatically verify the credentials on behalf of their owners to make sure they meet their respective policies. If so, the relationship can proceed without a hitch. If either agent spots a problem, it can immediately flag its owner—or simply deny the connection, so its owner is never bothered. This is how all our digital relationships should work: mutual auto-authentication on both sides that will put phishers permanently out to sea.
4.4.2 Permanent connections
The second major benefit SSI brings to relationship management is a feature no network has ever offered before: permanent connections. By permanent, we mean a connection that can last forever if both parties want it to (the mathematical techniques used to generate DIDs produce numbers so large that, even after thousands of years, the chances of generating the same ones are infinitesimally small).
How can SSI make such a promise? No other digital connection—phone number, email address, Twitter handle, Facebook friend, LinkedIn connection—can make that promise. The reason is that they all depend on some form of intermediary service provider for the connection to keep working. And no intermediary service provider can promise to always be in business and always maintain your connections no matter what you do or what your connections do.
Most of them promise you the exact opposite: they can terminate your service at any time, for any reason. Just read your terms of service.
With SSI—and the decentralized networks that make it work—there is no intermediary service provider. Your connections belong to you. You and the other party are the only ones who can terminate a connection because one or both of you want to end the relationship.
How valuable is this to you—the individual who wants to stay in touch with the people, organizations, and businesses in your life when you move, change jobs, graduate from school, or change service providers? And how valuable is it to all of your contacts and vendors who are trying to keep track of you? Earlier in this chapter, we quantified that simply automating the change-of-address process could save millions of hours and billions of dollars annually. Multiply that by all the other information we’d like to keep in sync with each other over permanent connections, and the total savings could be an order of magnitude greater.
4.4.3 Premium private channels
Permanence is not the only benefit of SSI connections. Because they are based on DIDs, DID documents (with public keys), and the DIDComm protocol (see chapter 5), SSI connections natively support end-to-end secure encrypted communications.
From a marketing perspective, we can call these premium private channels: premium because they are exclusive to you and your connection—they are not shared by anyone else; private because all your communications are automatically encrypted and decrypted by your respective agents without any effort on your part; and channels because you can use them to send and receive any messages or content your respective agents can “speak.”
So your connections can be used—without any permission from anyone else—with any SSI-enabled application: messaging apps, voice and video apps, data-sharing apps, social networking apps, productivity apps, payment apps, games, and so on. Every one of these apps can have access to every SSI feature described in this chapter.
Messaging apps have been moving in this direction for some time. Apple iMessage, WhatsApp, Signal, and Telegram all support end-to-end encryption in one form or another. Others, like WeChat and Alipay in China, have also integrated messaging with secure payment and so many other plug-in functions such that many Chinese spend their entire day living and working in these apps [36].
SSI makes premium private channels a universal capability that can be integrated with any app and can work across any trust boundary—just like the internet and the web. You will find multiple examples in parts 3 and 4 of this book. For instance, CULedger, a global consortium of credit unions developing SSI infrastructure for the credit union industry, plans to use premium private channels to request secure, digitally signed authorizations and consents from credit union members for actions that would otherwise require members to send a fax or make an in-person visit to a credit union office (see https://www.memberpass.com).
4.4.4 Reputation management
Reputation systems have become an essential feature of doing business on the web. For example, a Spiegel Research Center study showed nearly 95% of shoppers read online reviews before making a purchase [37]. A 2016 Harvard Business School study said a one-star increase on Yelp could lead to a 5-9% increase in revenue for a merchant [38].
However, it is precisely because they are so valuable that attacking reputation systems has become big business. A February 2019 study from Fakespot, which analyzes customer reviews, revealed that 30% of reviews on Amazon are fake or unreliable, and a whopping 52% of reviews posted on Walmart.com are inauthentic [39]. Worse, the rise in fake reviews is undermining consumer confidence in reputation systems. A Bright Local 2018 study said 33% of all consumers reported spotting “lots” of fake reviews and that the number went up to 89% for 18-to-34-year-olds who are savvier at detecting the signs of a fake review.
Amazon has long tried to fight this gaming with various protection measures, including its Amazon Verifier Purchase program that is supposed to ensure the reviewer actually bought the product (figure 4.4). However, this works only if a reviewer actually purchased the product at Amazon, and even then, it is relatively easy for a savvy marketing company to subsidize these purchases or find other ways around Amazon’s rules. And if Amazon has these issues, imagine the scope of the problem for smaller sites that have only a tiny fraction of Amazon’s security budget.

Figure 4.4 An Amazon Verified Purchase mark is supposed to confirm that the reviewer bought the reviewed product—but they are not difficult to work around.
At this point in the book, it should be obvious how SSI can help with this problem. First, reputation systems can require verifiable credentials for reviewers, weeding out the bots. Second, they can require a verifiable credential for a product purchase—a verifiable receipt—so programs like Amazon Verified Purchase can work independently of any particular retailer. Third, reviewers can start to build a reliable reputation independent of not just any product vendor but any retailer—so we can start developing an ecosystem of widely trusted independent reviewers that can become the web equivalent of, say, Walter Mossberg of the Wall Street Journal or Jon Udell in his days at Byte Magazine.
In short, reputation management can become an integral part of relationship management. Any two parties that develop a connection and engage in interactions with each other—purchases, contracts, consulting, or just community engagement—should be able to provide verifiable reputational feedback to each other and the larger community.
The implications extend to any online survey, poll, or vote where it matters that
Gaming these types of systems with fake votes has become so common that the security community gave it the name Sybil attack after the famed case of multiple-personality disorder that was the subject of a 1973 book and a 1976 movie. As fake reviews, fake sites, and fake news multiply like rabbits online, the ability of SSI to counter Sybil attacks and anchor the trustworthiness of reputation systems may become one of its most valuable contributions to the future health of the web.
4.4.5 Loyalty and rewards programs
Every relationship involves an exchange of value of some kind between the two parties—even if it’s just an exchange of pleasantries among neighbors. If that exchange is monetary, our earlier discussions of how SSI enables new forms of payment apply. But the stronger a relationship grows, the higher the probability that it involves some form of non-monetary value exchange.
Rewards programs are a perfect example. Whether they involve miles, points, stamps, or some other measure of value, they are an informal, direct, relationship-based way of thanking a customer for past loyalty and incentivizing future loyalty. And they work:
-
69% of consumers say their choice of retailer is influenced by where they can earn customer loyalty/rewards program points [40].
-
A 5% increase in customer loyalty increases the average profit per customer by 25-100%.
-
76% of consumers think that loyalty programs are part of their relationship with brands [41].
-
The loyalty management market is expected to grow from $1.93 billion in 2016 to $6.95 billion in 2023 [42].
However, for consumers today, managing loyalty programs is anywhere from mildly inconvenient to downright irritating. Imagine if every retailer you dealt with required you to use a different type of money and a different wallet—one dedicated to their specific store. That would be ridiculous—and yet that is how loyalty programs work today.
SSI-based relationship management (also called vendor relationship management or VRM, as noted earlier) can turn that on its head. Now every loyalty program can be designed to use its own premium private channel to the consumer’s own SSI digital wallet. No matter what kind of loyalty currency is involved, they can all be managed securely and privately in one place. Consumers gain dramatically greater convenience and control; retailers gain simpler and more effective loyalty programs that can also take advantage of all the other features of SSI.
4.5 Feature/benefit category 5: Regulatory compliance
Our final category may be the least “sexy” but is still very significant because it covers how SSI can contribute to the strength of our global cybersecurity and cyberprivacy infrastructure. In this section, we cover five major ways SSI can help all actors in the global economy comply with regulations designed to keep us safe while at the same time encouraging greater economic activity through open and fair competition.
4.5.1 Data security
We could begin this section with a shower of statistics about the state of security on the internet, but they are all summed up in this 2015 quote in Forbes from Gina Rommety, CEO of IBM, when she addressed the CISOs (chief information security officers), CIOs, and CEOs of 123 companies in 24 industries [43]:
We believe that data is the phenomenon of our time. It is the world’s new natural resource. It is the new basis of competitive advantage, and it is transforming every profession and industry. If all of this is true—even inevitable—then cyber crime, by definition, is the greatest threat to every profession, every industry, every company in the world.
That same Forbes article said market estimates of the size of the worldwide cybersecurity industry range from $77 billion in 2015 to $170 billion by 2020. It is one of the fastest-growing of all enterprise software segments.
By attacking the very root of the problem—digital identity—SSI represents a sea change in cybersecurity. As we explain in great technical detail in part 2, SSI digital wallets and agents will help users generate and manage private keys, automatically negotiate pairwise pseudonymous DIDs, form secure connections, and communicate over premium private channels that provide the data security required by regulations such as the Health Insurance Portability and Accountability Act (HIPAA) in the United States and the General Data Protection Regulation (GDPR) in Europe. This alone will lock down acres of current vulnerabilities—one reason the U.S. Department of Homeland Security funded much of the research into the decentralized identifier and decentralized key management standards that are the foundation of SSI.
note See the SBIR research funding topic “Applicability of Blockchain Technology to Privacy Respecting Identity Management” at https://www.sbir.gov/sbirsearch/detail/867797 and the news release at https://www.dhs.gov/science-and-technology/news/2017/07/20/news-release-dhs-st -awards-749k-evernym-decentralized-key.
SSI can also “detoxify” personal data so it can no longer be used for identity theft and related cybercrimes. Today this personal data is valuable because if a thief has enough of it, they can impersonate you to either break into current accounts or open new accounts in your name. But with verifiable credentials, your personal data alone can no longer be used to steal your identity. If the thief does not have your private keys, they cannot produce proofs of your verifiable credentials.
This means breaches of huge corporate databases containing personal data will become a thing of the past. Unlike usernames, passwords, and other personal data today, your private keys will never be stored in some centralized corporate database that serves as a giant honeypot for criminals. They are always stored in your local devices, with an encrypted backup copy in the cloud (or wherever you direct it to go). This means to steal an identity, a thief has to break into your personal SSI wallet(s), one at a time.
This is like forcing criminals to eat by catching tiny minnows one at a time instead of spearing a whale (figure 4.5). Give criminals that choice, and they will find another way to eat.

Figure 4.5 SSI will force identity thieves to try to steal private keys one wallet at a time (left) vs. break into giant corporate honeypots of personal data (right).
4.5.2 Data privacy
Security and privacy go hand in hand, and privacy is every bit as much of a concern on the internet today. In June 2018, Entrepreneur Magazine reported that 90% of internet users were “very concerned” about internet privacy [44]. The same article reported that the Cambridge Analytica data scandal so tarnished Facebook’s reputation that only 3% of users trust how Facebook is handling their personal data (and only 4% trust Google).
Part of what has pushed internet privacy to this crisis level is the sheer economic value of personal data in today’s digital economy. In an April 2019 review of Shoshana Zuboff’s book The Age of Surveillance Capitalism (https://shoshanazuboff.com/book), The Nation magazine said [45]:
Zuboff shows that these increasingly frequent invasions of our privacy are neither accidental nor optional; instead, they’re a key source of profit for many of the 21st century’s most successful companies. Thus, these companies have a direct financial stake in the broadening, deepening, and perfecting of the surveillance they already profit from—and in making sure that it remains legal.
Shifting the balance of power in privacy and personal data control will not be easy. However, SSI can help companies comply with applicable privacy legislation in three specific ways:
-
Selective disclosure —SSI verifiable credential exchange technology, specifically for credentials that use zero-knowledge proof (ZKP) cryptography (see chapter 6), enables companies to request proofs of exactly the personal data they need and no more. For example, a company can request proof that you are over a specific age rather than your actual birthdate.
-
Verifiable consent —Many consumers have no idea where companies get their personal data. Did it come from online forms they filled out? From marketing partners? From third-party data brokers? With verifiable credentials, there is a clear, verifiable chain of consent to share data that starts with the individual and can easily be traced and audited by the responsible SSI agents.
-
Governance frameworks —Today, most privacy policies are highly custom documents written by lawyers to protect specific companies—not your privacy. This is why a 2012 study by privacy researchers Lorrie Faith Cranor and Aleecia McDonald estimated that the average person would require 76 workdays to read the privacy policies on the websites they visit each year, which for the United States alone would add up to 53.8 billion hours or $781 billion in labor costs [46]. With SSI, company-specific privacy policies could begin to be replaced by governance frameworks that
These steps could become the first internet-scale implementation of the principles of privacy by design developed and advocated by former Ontario information and privacy commissioner Ann Cavoukian.
4.5.3 Data protection
Although closely related to data privacy, data protection goes beyond privacy controls to enumerate a larger set of specific principles to protect an individual’s personal data. Although the European Union’s GDPR (https://gdpr.eu) is the best-known data-protection legislation, it is by no means the only one. The California Consumer Privacy Act (CCPA, https://oag.ca.gov/privacy/ccpa) and, more recently, the California Privacy Rights Act are setting new standards for data-protection regulation in the U.S. Many other countries have or are enacting data protection laws along the same lines.
In addition to the data privacy compliance mechanisms listed in the previous section, there are other very specific ways SSI can enable individuals to exercise their rights and companies to comply with their responsibilities under these data protection acts:
-
Pseudonymous identifiers —GDPR encourages the use of pseudonyms to minimize correlation. SSI connections use pairwise pseudonymous peer DIDs by default.
-
Data minimization —GDPR requires collecting no more personal data than is necessary for the purpose for which it is being processed. SSI selective disclosure and ZKP credentials are ideal for meeting this requirement.
-
Data accuracy —GDPR requires that personal data must be accurate and kept up to date. SSI enables data controllers to request personal data supplied by verifiable credentials from reputable issuers—and which can be automatically updated by those issuers when the data changes.
-
Right of erasure (also known as the right to be forgotten)—Enshrined by Article 17 of GDPR, this can be one of the most challenging requirements because it means the data controller (the company) must give the data subject (the individual) a means of confirming what personal data a company holds while at the same time not opening a security hole for attackers. Fortunately, this is precisely the job for which SSI connections and premium private channels were designed. The data subject can use auto-authentication and auto-authorization to request access to the data and, if desired, send a digitally signed request for erasure over the connection. All of these actions can be securely audited for later verification of compliance.
4.5.4 Data portability
GDPR enforces one more data-protection right that is deserving of its own discussion: data portability. This is the right that allows data subjects to obtain data that a data controller holds on them and reuse it for their own purposes. In the words of the first paragraph of Article 20 of the GDPR:
The data subject shall have the right to receive the personal data concerning him or her, which he or she has provided to a controller, in a structured, commonly used, and machine-readable format and have the right to transmit those data to another controller without hindrance from the controller to which the personal data have been provided ...
The GDPR is only one of many new regulations requiring partial or complete data portability across data controllers. Another EU regulation, the Second Payment Services Directive (PSD2), is designed to drive the adoption of open banking in the EU. In addition, the Fifth Anti-Money Laundering Directive (AML5, https://www.electronicid.eu/aml5-new-anti-money-laundering-directive); the Electronic Identification, Authentication, and Trust Services Regulation (eIDAS); and the Directive on Security of Net- work and Information Systems (NIS Directive, https://ec.europa.eu/digital-single-market/en/network-and-information-security-nis-directive) all contain data-portability provisions relevant to SSI. All of these were preceded by the requirement for local telephone number portability (LNP) in the U.S. Telecommunications Act of 1996, which in the U.S. also applies to mobile number portability (MNP). MNP is also required to varying degrees by legislation in Africa, Asia, Australia, Latin America, and Canada.
SSI is ideal for data portability because it solves many of the deep security and privacy issues described in the previous sections. The secret is that SSI connections make it easy for the data to flow in and out of connections with the individual data subject’s own agent(s), where the individual can always exert complete control over the data and the terms and conditions under which they are willing to share it with other parties.
Under this architecture—and especially under governance frameworks designed specifically to work with this architecture—personal data should be able to flow freely between systems while meeting the security, privacy, and control requirements of GDPR and other data protection regulations.
4.5.5 RegTech (Regulation Technology)
As substantial as all these breakthroughs are, the one regulators may get most excited about is the ability to connect directly to SSI ecosystems themselves. In other words, by deploying their own SSI digital agents and connecting directly to the companies being regulated, regulators can be directly in the loop of transactions with specific regulatory requirements—such as KYC requirements for opening a bank account, AML requirements for money transmission, or Anti-Terrorist Finance (ATF) requirements for purchases of certain types of goods.
For example, if a money transmission between two SSI-enabled parties exceeds the threshold over which a financial institution must apply additional AML compliance measures, this can be communicated in real time between the bank’s SSI agent and the regulator’s SSI agent. This has the potential to change the very nature of regulation enforcement from an after-the-fact spot-check auditing activity to a real-time rules-driven monitoring activity—decreasing enforcement costs, speeding up enforcement actions, and improving the quality of enforcement data all at the same time—a rare triple win for government regulation.
This is a highly desirable development given the skyrocketing costs of compliance cited earlier in this chapter. It is also consistent with the rapid growth of the global Regulatory Technology (RegTech) market, which Research and Markets expects to grow from $4.3 billion in 2018 to $12.3 billion by 2023, at a compound annual growth rate (CAGR) of 23.5% [47]. With SSI technology’s ability to connect secure, private, permissioned SSI agents to any business process requiring regulation, that growth figure could become much higher.
As its name indicates, the SSI Scorecard is a tool for analyzing the impact of SSI on any particular use case, application, industry, or vertical market. We do just that in part 4 of this book, where we examine in-depth use cases for SSI across different vertical markets. Each chapter will wrap up with a scorecard for how much impact SSI is likely to have in that market and why. This should help tie together the building blocks, example scenarios, and features/benefits we have covered in part 1 with the real-world scenarios we look at in part 4.
But first, if you want to dive deeper into the technical aspects of SSI architecture and technology, these are covered by some of the leading experts in these subjects in part 2. If you are more interested in the overall economic, political, and social impacts of SSI, you can skip directly to part 3. Or, if you want to read about example use cases for SSI in specific industries and verticals, you can jump to part 4.
References
1. Grant, Kelli B. 2018. “Identity Theft, Fraud Cost Consumers More Than $16 Billion.” CNBC. https://www.cnbc.com/2017/02/01/consumers-lost-more-than-16b-to-fraud-and-identity-theft -last-year.html.
2. Marchini, Kyle, and Al Pascual. 2019. “2019 Identity Fraud Study: Fraudsters Seek New Targets and Victims Bear the Brunt.” Javelin. https://www.javelinstrategy.com/coverage-area/2019-iden tity-fraud-report-fraudsters-seek-new-targets-and-victims-bear-brunt.
3. FinTech Futures. 2018. “The Future of Client Onboarding.” https://www.fintechfutures.com/2018/09/the-future-of-client-onboarding.
4. Callahan, John. 2018. “Know Your Customer (KYC) Will Be A Great Thing When It Works.” Forbes. https://www.forbes.com/sites/forbestechcouncil/2018/07/10/know-your-customer-kyc -will-be-a-great-thing-when-it-works.
5. Dickenson, Kelvin. 2019. “The Future of KYC: How Banks Are Adapting to Regulatory Complexity.” Opus. https://www.opus.com/future-of-kyc.
6. Fenergo. 2018. “Global Financial Institutions Fined $26 Billion for AML, Sanctions & KYC Non-Compliance.” https://www.fenergo.com/press-releases/global-financial-institutions-fined-$26 -billion-for-aml-kyc.html.
7. Statista Research Department. 2020. “E-Commerce Worldwide—Statistics & Facts.” https://www.statista.com/topics/871/online-shopping.
8. Nasdaq. 2017. “UK Online Shopping and E-Commerce Statistics for 2017.” https://www.nasdaq .com/article/uk-online-shopping-and-e-commerce-statistics-for-2017-cm761063.
9. Adobe. 2020. “2020 Holiday Shopping Trends.” http://exploreadobe.com/retail-shopping-insights.
10. Khandelwal, Astha. v2020. “eCommerce Conversion Rate Benchmarks—Quick Glance At How They Stack Up.” VWO Blog. https://vwo.com/blog/ecommerce-conversion-rate.
11. Baymard Institute. 2019. “44 Cart Abandonment Rate Statistics.” https://baymard.com/lists/cart-abandonment-rate.
12. Redbord, Michael. 2018. “The Hard Truth About Acquisition Costs (and How Your Customers Can Save You).” HubSpot. https://research.hubspot.com/customer-acquisition-study.
13. Sorofman, Jake. 2014. “Gartner Surveys Confirm Customer Experience Is the New Battle- field.” Gartner. https://blogs.gartner.com/jake-sorofman/gartner-surveys-confirm-customer -experience-new-battlefield.
14. Hyken, Shep. 2018. “Businesses Lose $75 Billion Due to Poor Customer Service.” Forbes. https://www.forbes.com/sites/shephyken/2018/05/17/businesses-lose-75-billion-due-to-poor-customer -service.
15. Palfy, Sandor. 2018. “How Much Do Passwords Cost Your Business?” Infosecurity. https://www.infosecurity-magazine.com/opinions/how-much-passwords-cost.
16. Morgan, Blake. 2019. “50 Stats That Prove the Value of Customer Experience.” Forbes (September 24). https://www.forbes.com/sites/blakemorgan/2019/09/24/50-stats-that-prove-the-value -of-customer-experience.
17. Okyle, Carly. 2015. “Password Statistics: The Bad, the Worse, and the Ugly (Infographic).” Entrepreneur. https://www.entrepreneur.com/article/246902.
18. Autho0. n.d. “Password Reset Is Critical for a Good Customer Experience.” https://auth0.com/learn/password-reset.
19. Dashlane. 2015. “Online Overload: Worse Than You Thought.” http://blog.dashlane.com/wp -content/uploads/2015/07/MailboxSecurity_infographic_EN_final1.jpg.
20. Nielsen Norman Group. n.d. “Intranet Portals: UX Design Experience from Real-Life Projects.” www.nngroup.com/reports/intranet/portals.
21. Chisnell, Dana. 2011. “Random Factoids I’ve Encountered in Authentication User Research So Far.” Authentical. http://usablyauthentical.blogspot.com/2011/09/random-factoids-ive -encountered-in.html.
22. PasswordResearch.com. 2020. http://passwordresearch.com/stats/statistic97.html.
23. Axiomatics. n.d. “Attribute-Based Access Control—ABAC.” https://www.axiomatics.com/ attribute-based-access-control.
24. Detrixhe, John. 2018. “Hackers Account for 90% of Login Attempts at Online Retailers.” Quartz. https://qz.com/1329961/hackers-account-for-90-of-login-attempts-at-online-retailers.
25. Security. 2019. “8 in 10 IT Leaders Want to Eliminate Passwords.” https://www.securitymagazine .com/articles/90530-in-10-it-leaders-want-to-eliminate-passwords.
26. Business Wire. 2019. “Veridium Survey Reveals Strong Consumer Sentiment Toward Biometric Authentication.” https://www.businesswire.com/news/home/20190213005176/en/Veridium -Survey-Reveals-Strong-Consumer-Sentiment-Biometric.
27. Microsoft Security Team. 2018. “Building a World Without Passwords.” https://cloudblogs .microsoft.com/microsoftsecure/2018/05/01/building-a-world-without-passwords.
28. Delgado, Michelle. 2018. “6 Steps for Avoiding Online Form Abandonment.” The Manifest. https://themanifest.com/web-design/6-steps-avoiding-online-form-abandonment.
29. Liedke, Lindsay. 2020. “101 Unbelievable Online Form Statistics & Facts for 2021.” WPForms Blog. https://wpforms.com/online-form-statistics-facts.
30. Holmes, Colin. 2018. “The State of the American Mover: Stats and Facts.” Move.org. https://www.move.org/moving-stats-facts.
31. Khatri, Yogita. 2018. “Nearly $1 Billion Stolen In Crypto Hacks So Far This Year: Research.” CoinDesk. https://www.coindesk.com/nearly-1-billion-stolen-in-crypto-hacks-so-far-this-year-research.
32. Pathak, Shareen. 2017. “End of an Era: Amazon’s 1-Click Buying Patent Finally Expires.” Digiday. https://digiday.com/marketing/end-era-amazons-one-click-buying-patent-finally-expires.
33. Columbus, Louis. 2019. “Salesforce Now Has Over 19% of the CRM Market.” Forbes. https://www .forbes.com/sites/louiscolumbus/2019/06/22/salesforce-now-has-over-19-of-the-crm-market.
34. Verizon. 2018. “2018 Data Breach Investigations Report.” https://enterprise.verizon.com/resources/reports/DBIR_2018_Report.pdf.
35. FBI. 2018. “Business E-mail Compromise: The 12 Billion Dollar Scam.” Alert number I-071218-PSA. https://www.ic3.gov/media/2018/180712.aspx.
36. WeChat Mini Programmer. 2018. “Alipay vs. WeChat Pay: An Unbiased Comparison.” https://medium.com/@wechatminiprogrammer/alipay-vs-wechat-pay-an-unbiased-comparison-52eafab c7ffe.
37. Spiegel Research Center. 2017. “How Online Reviews Influence Sales.” http://spiegel.medill .northwestern.edu/online-reviews.
38. Luca, Michael. 2016. “Reviews, Reputation, and Revenue: The Case of Yelp.com.” Harvard Business School. HBS Working Paper Series. https://www.hbs.edu/faculty/Pages/item.aspx?num =41233.
39. Picchi, Aimee. 2019. “Buyer Beware: Scourge of Fake Reviews Hitting Amazon, Walmart and Other Major Retailers.” CBS News. https://www.cbsnews.com/news/buyer-beware-a-scourge-of -fake-online-reviews-is-hitting-amazon-walmart-and-other-major-retailers.
40. Maritz Loyalty Marketing. 2013. “Holiday Shoppers’ Generosity Extends Beyond Friends and Family to Themselves.” Cision. www.prweb.com/releases/2013/11/prweb11372040.htm.
41. Saleh, Khalid. 2020. “The Importance of Customer Loyalty Programs—Statistics and Trends.” Invesp. https://www.invespcro.com/blog/customer-loyalty-programs.
42. Sonawane, Kalyani. 2020. “Global Loyalty Management Market Expected to Reach $6,955 Million by 2023.” Allied Market Research. https://www.alliedmarketresearch.com/press-release/loy alty-management-market.html.
43. Morgan, Steve. 2015. “IBM's CEO on Hackers: ‘Cyber Crime Is the Greatest Threat to Every Company in the World.’” Forbes. https://www.forbes.com/sites/stevemorgan/2015/11/24/ibms -ceo-on-hackers-cyber-crime-is-the-greatest-threat-to-every-company-in-the-world.
44. Byer, Brian. 2018. “Internet Users Worry About Online Privacy but Feel Powerless to Do Much About It.” Entrepreneur. https://www.entrepreneur.com/article/314524.
45. Fitzpatrick, Katie. 2019. “None of Your Business.” The Nation. https://www.thenation.com/article /shoshana-zuboff-age-of-surveillance-capitalism-book-review.
46. Madrigal, Alexis C. 2012. “Reading the Privacy Policies You Encounter in a Year Would Take 76 Work Days.” The Atlantic. https://www.theatlantic.com/technology/archive/2012/03/reading -the-privacy-policies-you-encounter-in-a-year-would-take-76-work-days/253851.
47. Research and Markets. 2018. “RegTech Market by Application (Compliance & Risk Management, Identity Management, Regulatory Reporting, Fraud Management, Regulatory Intelligence), Organization Size (SMEs, Large Enterprises), and Region—Global Forecast to 2023.” https://www.researchandmarkets.com/research/r8ktnm/global_12_3?w=5.
