Alex Preukschat and Drummond Reed
Self-sovereign identity—commonly abbreviated SSI—is a new model for digital identity on the internet: i.e., how we prove who we are to the websites, services, and apps with which we need to establish trusted relationships to access or protect private information. Driven by new technologies and standards in cryptography, distributed networks, cloud computing, and smartphones, SSI is a paradigm shift for digital identity similar to other technology paradigm shifts: for example, the shift from keyboard-driven user interfaces (e.g., MS-DOS) to graphical user interfaces (e.g., Windows, Mac, iOS), or the shift from dumb phones to smartphones.
However, the SSI paradigm shift is deeper than just a technology shift—it is a shift in the underlying infrastructure and power dynamics of the internet itself. In this way, it is closer to other infrastructure paradigm shifts such as those in transportation:
Each of these shifts in technology resulted in deeper, structural changes to the shape and dynamics of society and commerce. The same is true of the paradigm shift to SSI. While the details are evolving rapidly, the “big picture” of SSI that has already emerged is remarkably coherent and compelling—and this is what is driving adoption.
In this book, we endeavor to explain this SSI paradigm shift in the most approachable way possible. Our motivation is not to impose our vision of the world on you but to humbly convey the technological, business, and social movements that have come together to make SSI possible. Our starting point is this claim:
The Internet was built without an identity layer.
—Kim Cameron, Chief Architecture of Identity, Microsoft [1]
What did Kim Cameron—Microsoft’s chief architect for identity from 2004 to 2019—mean by that quote? What is an “identity layer?” Kim gives an answer in his groundbreaking series of essays called “The Laws of Identity,” published on his blog over a series of months in 2004 and 2005:
The Internet was built without a way to know who and what you are connecting to. This limits what we can do with it and exposes us to growing dangers. If we do nothing, we will face rapidly proliferating episodes of theft and deception that will cumulatively erode public trust in the Internet.
Kim was saying that when the internet was initially developed in the 1960s and 1970s by the U.S. military (sponsored by the Defense Advanced Research Projects Agency, or DARPA), the problem it was designed to solve was how to interconnect machines to share information and resources across multiple networks. The solution—packet-based data exchange and the TCP/IP protocol—was so brilliant that it finally enabled a true “network of networks” [1]. And the rest, as they say, is history.
What Kim was driving at, however, is that with the internet’s TCP/IP protocol, you only know the address of the machine you are connecting to. That tells you nothing about the person, organization, or thing responsible for that machine and communicating with you. (Hackers have demonstrated how to change a computer’s hardware [MAC] or IP address before it is sent to remote network devices. This makes it nearly impossible to rely on, or trust, current network-level identifiers.)
This seems like a fairly easy problem to solve—after all, people and organizations built the internet, and we control (or at least we think we do) all the “things” that are using it. So, how hard could it be to design a simple, standard way to identify the person, organization, or thing you are dealing with over the internet?
The answer turns out to be: very, very hard.
Why? In a nutshell, the original internet was not very big. The people using the network were mostly academic computer scientists. Most of them knew each other, and they all needed access to expensive machines and sophisticated technical skills to participate. So even though the internet was designed to be decentralized and to have no single points of failure, early on it was effectively a relatively small club.
Needless to say, that has changed completely. There are now billions of people and multiple billions of devices on the internet, and almost all of them are strangers. In this environment, the unfortunate truth is that there are many, many people who want to deceive you about who or what you are dealing with over the internet. Identity (or the lack of it) is one of the primary sources of cybercrime.
1.1 How bad has the problem become?
Recall the final sentence of Kim Cameron’s 2005 prediction about the internet’s missing identity layer: “If we do nothing, we will face rapidly proliferating episodes of theft and deception that will cumulatively erode public trust in the Internet.”
Despite all the efforts to solve the internet identity problem, the lack of a breakthrough solution has proved Kim’s prognosis true in spades. Never mind that by 2017, the average business user had to keep track of 191 passwords [2] or that username/password management has become the most hated consumer experience on the internet. That’s just an inconvenience.
Where’s the foul? The deeper damage is in cybercrime, fraud, economic friction, and the ever-growing threats to our online privacy.
The litany of statistics goes on and on:
-
IBM President and CEO Ginni Rometty described cybercrime as “the greatest threat to every profession, every industry, every company in the world” [3].
-
Global cybercrime damages are predicted to cost $6 trillion annually by 2021 [4].
-
Over 90% of American consumers believe they have lost control of how their personal information is collected and used by all kinds of entities [5].
-
In 2016, three billion Yahoo accounts were hacked in one of the biggest breaches of all time [6].
-
80% of hacking-related breaches are due to compromised user passwords [7].
-
The Equifax breach has cost the company over $4 billion in total [8].
-
According to a 2014 study from Ctrl-Shift, the cost of identity-assurance processes exceeds £3.3 billion per annum in the UK alone [9].
Our failure to solve the internet identity problem is reaching the breaking point. Either we fix it, or the very future of the internet is in doubt.
1.2 Enter blockchain technology and decentralization
Like many disruptive innovations, breakthroughs can come from unexpected places. When Satoshi Nakamoto first published Bitcoin: A Peer-to-Peer Electronic Cash System in October 2008 [10], no one expected it could also inspire a fundamental transformation in how we think about identity and trust online.
Yet identity and money have been very closely intertwined for centuries—a history explored in rich and entertaining detail in David Birch’s 2014 book Identity is the New Money [11] (read chapter 17 on money and identity for more details). So it is not surprising that by 2015, when Bitcoin’s decentralized blockchain model had started to capture the attention of industry and the world press, it finally came to the internet identity community’s attention.
At the Spring 2015 Internet Identity Workshop (IIW), a three-day gathering of internet identity experts that has been held twice a year every year since 2004, several sessions were held on “blockchain identity.” That kicked off an informal group to study how best to apply blockchain tech to the challenges of user-centric identity management that IIW had been working on for over a decade. At the Fall 2015 event, that group reported out in a series of sessions that caught fire within the IIW community.
Two months later, the U.S. Department of Homeland Security Science & Technology division published a Small Business Innovation Research (SBIR) grant topic entitled “The Applicability of Blockchain Technology to Privacy Respecting Identity Management” [12]. It said:
The potential applicability of blockchain technology goes beyond crypto-currencies (which is simply an application built on top of that technology) to many other uses such as smart contracts, provenance and attribution, distributed validation of information, and more.
This SBIR topic is focused on determining and demonstrating if classic information security concepts such as confidentiality, integrity, availability, non-repudiation and provenance as well as privacy concepts such as pseudonymity and selective disclosure of information can be built on top of the blockchain to provide a distributed, scalable approach to privacy respecting identity management.
Here was a U.S. government agency proposing that the same principles of blockchain technology that power Bitcoin could potentially solve critical problems with the internet’s missing identity layer. And it was not alone. The European Union was exploring decentralized digital identity via a number of initiatives (see the International Association for Trusted Blockchain Applications, https://inatba.org; the EU Blockchain Observatory & Forum, https://www.eublockchainforum.eu; and the European SSI Framework [eSSIF], https://ssimeetup.org/understanding-european-self-sovereign-identity-framework-essif-daniel-du-seuil-carlos-pastor-webinar-32), the Chinese government was making Blockchain technologies a national priority [13], and Korea was creating public/private consortia specifically for decentralized identity (http:// didalliance.org). And they were all doing this for the same reason: the possibility of moving from centralized to decentralized digital identity systems.
But why was decentralization so important?
1.3 The three models of digital identity
That question is best answered by the evolutionary progression of internet identity models.
note This way of describing the evolution of internet identity was first proposed by Timothy Ruff in 2018: “The Three Models of Digital Identity Relationships,” Everynym, https://medium.com/evernym/the-three-models-of-digital-identity-relationships-ca0727cb5186.
1.3.1 The centralized identity model
The first model is the easiest to explain. It is the model we have long used with almost all identifiers and credentials such as government ID numbers, passports, identity cards, driving licenses, invoices, Facebook logins, Twitter handles, and so on. All of these are issued by centralized governments or service providers like banks or telecom companies. This centralized model is so prevalent in the real world that it can be divided into two types:
-
Scandinavian model —Private companies (financial and telecom firms) provide a centralized digital identity service to interact with the government (TUPAS in Finland, BankID in Sweden, and so on)
-
Continental model —In Europe, governments provide digital identity services to companies allowing interaction with their citizens.
note These centralized models are described in the excellent 2016 World Economic Forum report “A Blueprint for Digital Identity” at http://www3.weforum.org/docs/WEF_A_Blueprint_for_Digital_Identity.pdf.
The centralized model is also the original form of internet identity—and the one that, in many cases, we still use today. You establish an identity by registering an account (typically a username and password) with a website, service, or application. For this reason, the model is also called account-based identity.

Figure 1.1 The relationship of an individual to a website (or application) under the internet’s original centralized, account-based identity model
In figure 1.1, “You” are a dotted circle because, in the world of centralized identity, the real You doesn’t exist without an account in some centralized system. The real You is given permission to plug into a website, service, or application because the Org is lending you credentials that represent you with limited controls and permissions. At the end of the day, those credentials belong to the Org. If you delete all your accounts at these centralized providers, your ability to access services will be revoked. The You in figure 1.1 will disappear from the internet completely. Yet all the data about you will still belong to the Org, outside of your control.
That is only one of the many problems with centralized identity. Others include the following:
-
The burden of remembering and managing all the usernames and passwords (and, in some cases, other multi-factor authentication tools such as one-time codes) falls entirely on you.
-
Every site enforces its own security and privacy policies, and they are all different (a classic example is the maddingly different rules about passwords: minimum length, special characters allowed, and so on).
-
None of your identity data is portable or reusable anywhere (users are warned to never reuse passwords).
-
These centralized databases of personal data are giant honeypots that have led to some of the biggest data breaches in history.
1.3.2 The federated identity model
To alleviate some of the pain points of centralized identity, the industry developed a new model called federated identity. The basic idea is simple: insert a service provider called an identity provider (IDP) in the middle (figure 1.2).

Figure 1.2 The three-way relationship involved in the federated identity model
Now you can just have one identity account with the IDP, and it, in turn, can log you in and share some basic identity data with any site, service, or app that uses that IDP. The collection of all the sites that use the same IDP (or group of IDPs) is called a federation. Within a federation, each of the Orgs is often called a relying party (RP).
Three generations of federated identity protocols have been developed since 2005—Security Assertion Markup Language (SAML), OAuth, and OpenID Connect—and they have all had some real success. Using these protocols, single sign-on (SSO) is now a standard feature of most corporate intranets and extranets.
Federated identity management (FIM) also started to catch on in the consumer internet, where it began to be called user-centric identity. Using protocols like OpenID Connect, social login buttons from Facebook, Google, Twitter, LinkedIn, etc. are now a standard feature on many consumer-facing websites (figure 1.3).

Figure 1.3 Examples of the proliferation of social login buttons that try to ease the pain of internet identity for mere mortals
Despite all the work that has gone into federated identity since 2005, it has still failed to provide us with the internet’s missing identity layer. There are numerous reasons:
-
There isn’t one IDP that works with all sites, services, and apps. So users need accounts with multiple IDPs—and pretty soon, they start forgetting which IDP they used with which site, service, or app.
-
Because they have to serve so many sites, IDPs must have “lowest common denominator” security and privacy policies.
-
Many users—and many sites—are uncomfortable with having a “man in the middle” of all their relationships that can surveil a user’s login activity across multiple sites.
-
Large IDPs are some of the biggest honeypots for cybercrime.
-
IDP accounts are no more portable than centralized identity accounts. If you leave an IDP like Google, Facebook, or Twitter, all those account logins are lost.
-
Due to security and privacy concerns, IDPs are not in a position to help users securely share some of their most valuable personal data: passports, government identifiers, health data, financial data, etc.
1.3.3 The decentralized identity model
A new model, inspired by blockchain technology, first surfaced in 2015. (The FIDO [Fast IDenfication Online] Alliance started in 2013; however, it uses a hybrid approach where connections are peer-to-peer but key management is performed centrally by the FIDO Alliance rather than by a blockchain.) This model no longer relied on either centralized or federated identity providers but was fundamentally decentralized. It accelerated rapidly, assimilating new developments in cryptography, distributed
databases, and decentralized networks. It began spawning new decentralized identity standards such as verifiable credentials (VCs) and decentralized identifiers (DIDs) that we explain in more detail in chapter 2 and part 2 of this book.
However, the most important difference in this model is that it is no longer account-based. Instead, it works like identity in the real world: i.e., it is based on a direct relationship between you and another party as peers (figure 1.4). Neither of you “provides,”
“controls,” or “owns” the relationship with the other. This is true whether the other party is a person, an organization, or a thing.

Figure 1.4 The peer-to-peer relationship enabled by the decentralized identity model—returning people to direct, private connections secured by public/private key cryptography
In a peer-to-peer relationship, neither of you has an “account” with the other. Rather, you both share a connection. Neither of you fully “owns” this connection. It is like a string that you are both holding—if either one of you lets go, the string will drop. But as long as you both want it, the connection will persist.
Peer-to-peer connections are inherently decentralized because any peer can connect to any other peer anywhere—exactly how the internet works. But how does this become an identity layer? And why does it need blockchain technology?
The answer lies in public/private key cryptography: a way of securing data via mathematical algorithms based on cryptographic keys held by each party. Instead of using blockchain technology for cryptocurrency, identity management uses it for decentralized public key infrastructure (DPKI). In the next few chapters, we’ll go into this in greater detail. But in essence, blockchain technology and other decentralized network technologies can give us a strong, decentralized solution for
-
Exchanging public keys directly to form private, secure connections between any two peers
-
Storing some of these public keys on public blockchains to verify the signatures on digital identity credentials (aka verifiable credentials) that peers can exchange to provide proof of real-world identity
Ironically, this means the best overall analogy for the decentralized identity model is, in fact, exactly how we prove our identity every day in the real world: by getting out our wallet and showing the credentials we have obtained from other trusted parties. The difference is that with decentralized digital identity, we are doing this with digital wallets, digital credentials, and digital connections (figure 1.5).

Figure 1.5 The essence of decentralized digital identity: turning physical identity credentials in our physical wallets into digital credentials in digital wallets
1.4 Why “self-sovereign”?
As the decentralized digital identity model started to catch on, it quickly developed the moniker self-sovereign identity and then the acronym SSI. Initially, this term was quite controversial due to its connotations [14]. What made the term so “sticky” [15]—to the point that it is now the standard term for this new identity model used by top industry analyst firms and leading digital identity conferences around the world? (The European Identity Conference, hosted every spring by the EU analyst firm Kuppinger Cole, has a track called “Self-Sovereign Identity.”)
Let’s start with the word sovereign. This is not a word most of us use in everyday speech, so it has some cachet by itself. By definition, it is a powerful word—sometimes used as a direct synonym for king or head of state, but today also meaning autonomous or independent. The other frequent connotation is sovereign nation or sovereign state. The Dictionary.com definition of sovereignty is
the quality or state of being sovereign, or of having supreme power or authority; the status, dominion, power, or authority of a sovereign; royal rank or position; royalty.
Add the word self in front of it, and suddenly the meaning stands out: “a person who is neither dependent on nor subjected to any other power or state.” Given that, what individual would not want to be “self-sovereign”? Conversely, what government might not have serious concerns about its citizens flocking en masse to a new technology called “self-sovereign”?
But of course, the term we are discussing is not self-sovereign but self-sovereign identity. When you apply that term to a person, following our logic, it literally translates to
A person’s identity that is neither dependent on nor subjected to any other power or state.
Aha. Now we can finally understand why the term caught on. When it comes to expressing personal identity, many individuals worldwide will find that definition attractive. And many self-sovereign nations might gladly help endow their citizens with the power of self-sovereign identity—especially because, as we see in chapter 23, government-issued identity does not compete with self-sovereign identity. The two are highly complementary.
But we can also see why the term might be controversial—why, despite its power, it sometimes gets in the way of understanding the value of the decentralized identity model. Unfortunately, the term also tends to perpetuate two of the most persistent myths about SSI:
-
Self-sovereign identity is self-asserted identity. That is, you are the only one who can make identity assertions about yourself. This, of course, is not true, any more than you could be the issuer of all the credentials in your physical wallet today. Most of the information about your identity comes from other trusted sources—that’s the reason other parties are willing to rely on it.
-
Self-sovereign identity is just for people. While the SSI model is very much informed by individuals’ needs for security, privacy, and personal data control, the SSI model applies equally for organizations and things. In fact, it applies to anything that needs identity on the internet.
Since the acronym SSI is now in such wide use within the internet identity industry, that is the term we use throughout this book. (Co-author Alex Preukschat named his webinar series SSI Meetup for the same reason: https://ssimeetup.org.)
1.5 Why is SSI so important?
In many ways, answering this question is the whole point of this book. The chapters in front of you lay out how and why SSI will affect almost everything we do on the internet, day in and day out. Some of these changes may actually be as deep and profound as the internet itself was in the 1980s and 1990s—and the web was after that.
Today, many of us take those two technological advances for granted. Yet if you stop to think about it (if you were even alive back then), the work lives, social lives, and even political lives of billions of people have been radically transformed by the internet and the web. If that seems like an exaggeration, stop to consider that 7 out of the 10 most valuable companies in the world today would not exist without the internet and the web [16].
Forecast We predict that the impact of SSI technology—and the uncounted new patterns of trusted interactions it will enable across all walks of life—will be equally profound.
The fundamental reason is grounded in what we just explained about the term self-sovereign identity: it represents a shift in control. We started out trying to find a solution to the internet’s missing identity layer; we ended up discovering that solving those problems required a shift in control from the centers of the network—the many “powers that be”—to the edges of the network—where all of us exist and interact as peers. This shift in control is wonderfully captured in figure 1.6 from Tim Bouma, co-author of chapter 23.
In the centralized and federated identity models, the locus of control is with the issuers and verifiers in the network. In the decentralized SSI identity model, the locus of control shifts to the individual user, who can now interact with everyone else as a full peer.

Figure 1.6 The shift in control that happens in the transition from centralized or federated identity models to the self-sovereign model. Only the latter puts the individual at the center.
This is why SSI is about more than technology. It has important business, legal, and social dimensions as well.
Up to this point, we have referred to SSI as if it were a single movement—one driven by communities like IIW (described earlier), Rebooting the Web of Trust (RWOT, https://www.weboftrust.info/), MyData (https://mydata.org), and the W3C Decentralized Identifier (https://www.w3.org/2019/did-wg) and Verifiable Credentials Working Groups (https://www.w3.org/2017/vc). However, as SSI becomes more mainstream, we predict that different flavors and visions of SSI will be implemented. These differences will depend on the needs, wants, and priorities of different communities implementing SSI. The key will be how different SSI architectures become interoperable the same way the internet made different local networks interoperable. Only if this happens will there be one unified SSI infrastructure.
1.6 Market drivers for SSI
One way to understand the momentum of SSI—and differences in SSI architectures—is to look at what is driving demand. For the business-minded reader, some of these categories might come across as foreign or ideological, but our aim is to reflect what we observe in the market. The drivers fall into three broad categories:
-
Business efficiency and customer experience —This market is focused on security, cost savings, and convenience. As we discuss in chapter 4, this is the primary market demand driving SSI in its early stages. Corporations, governments, universities, NGOs—they all want to improve data security, increase compliance with privacy and data-protection regulations, reduce costs by improving workflows, and be more competitive by offering their customers a better user experience.
These applications of SSI are primarily a disruption to the existing identity and access management (IAM) marketplace. Like most disruptive technologies, they will give rise to new companies, new business models, and new subsegments within the IAM market.
-
Resistance to the surveillance economy —This is a reaction to the prevailing business model and tactics of some of the most dominant companies on the internet today. As has been widely covered in the media, the web’s predominant business model (Web 2.0) is digital advertising. This has led to a worldwide industry that Harvard professor Shoshan Zuboff calls “surveillance capitalism.” The backlash to this model has become the market driver for certain governments, privacy-conscious individuals, and a select number of corporations that want to do more than just ride the next wave of technological innovation and growth—they also want to strategically weaken the business model of the global aggregators, resellers, and distributors of personal data.
Demand in this segment is a mix of ideology (e.g., privacy advocates), consumer sentiment, and strategic positioning. Governments such as the European Union with its General Data Protection Regulation (GDPR) are leading this movement because it puts them on a more level playing field with the internet giants, particularly as exponential technology changes continue to disrupt the “old world.”
-
Sovereign individual movement —This movement is driven by people who want to take back more control over their lives and data. Perhaps the best way to describe this SSI market driver is that it aims to do for decentralized identity what Bitcoin aims to achieve for decentralized money. Permissionless cryptocurrency technologies like Bitcoin want to create fully decentralized economies that do not rely on any central parties for their operation. Individuals in this market segment want to apply the same philosophy to digital identity, opting for SSI architectures that maximize decentralization. To understand their motivations, we recommended reading The Sovereign Individual by James Dale Davidson and William Rees-Mogg [17]. Ironically, it was published in 1997, well before Bitcoin and decentralization became mainstream subjects. However, the book makes its authors look prescient about the decentralization movement—a subject we explore in greater detail in part 3.
Because the biggest initial driver of SSI adoption is the first category of business efficiency and customer convenience, let’s look at a few examples in specific market segments—some of which also shed more light on the other two market drivers.
1.6.1 E-commerce
Figure 1.7 shows the staggering growth of e-commerce. Every e-commerce transaction today involves a digital identity of some kind—either centralized or federated. What happens when consumers are equipped with SSI digital wallets with which they can do all of the following?
-
Enjoy passwordless registration and logins at any SSI-enabled website or service
-
Automatically receive a warning if the site or service they are connecting to cannot present its own trustworthy digital credentials
-
Provide payment directly from their digital wallet without having to fool with “checkout,” third-party wallet providers, or external payment gateways
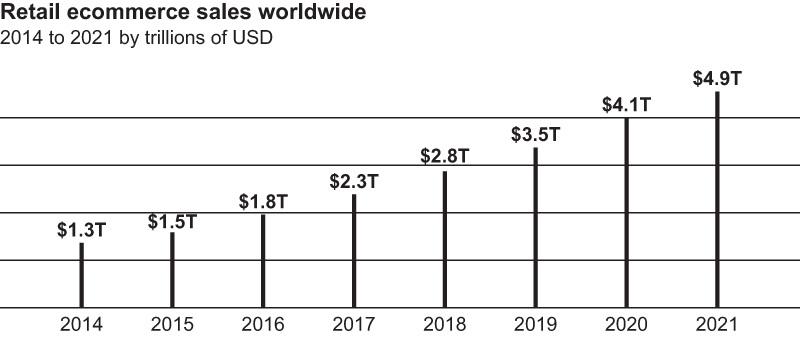
Figure 1.7 The growth in e-commerce sales over the past decade
-
Automatically maintain a private personal log of digital receipts—and provide proof of their purchases to any merchant or recommendation engine of their choice
Not only will the average consumer’s experience of e-commerce be transformed, but the additional friction that SSI will wring out of the global digital economy could potentially be measured in hundreds of billions of dollars.
1.6.2 Banking and finance
According to Citi’s 2018 Mobile Banking Study, almost one-third of all U.S. adults are now using mobile banking. It’s the most popular mobile app after social networking. When it comes to Millennials, the number is almost two-thirds [18].
Nearly all of this mobile banking activity is from dedicated apps provided by banks, credit unions, and other financial institutions directly to their customers. Some of these are award-winning for their usability, security, and privacy features. But most are still dedicated apps with their own logins/passwords that work with a single provider. (Initiatives like Itsme (https://www.itsme.be/en) in Belgium provide a regional solution.)
What happens when individuals gain an SSI digital wallet that does the following?
-
Can work with any financial institution that supports SSI, and can access financial services from the entire marketplace of providers without the friction of filling out the same forms over and over
-
Can provide digital credentials from trusted third parties that are required to pass KYC (know your customer) and AML (anti-money laundering) checks required of every financial institution
-
Can digitally share all the information—digitally signed by trusted issuers—necessary to apply for a loan or mortgage in seconds
-
Can do single-party or multi-party digital signatures to authorize important transactions—up to millions of dollars—with cryptographically-protected audit trails
note SSI digital wallets are also being explored as solutions for regulatory-compliant exchange of cryptocurrencies and central bank digital currencies (CBDC).
These breakthrough benefits are not fictional—some of them are being delivered in production. For example, the global credit union industry has formed a consortium to introduce MemberPass™, the world’s first global digital credential of credit union membership (www.culedger.com).
1.6.3 Healthcare
Practice Fusion, the largest cloud-based electronic health record (EHR) provider in the United States, provides the following statistic about EHR adoption in 2014:
Less than a decade ago, nine out of ten doctors in the U.S. updated their patients’ records by hand and stored them in color-coded files. By the end of 2017, approximately 90% of office-based physicians nationwide will be using electronic health records (EHRs). [19]
Unfortunately, Healthcare IT News reports that the average hospital has 16 different EHR vendors in use at affiliated practices [20]. It goes on to sum up the problem this way:
Achieving interoperability among different EHR platforms is so difficult, in fact, that the Centers for Medicare and Medicaid Services working with the Office of the National Coordinator for Health IT, the federal agency charged with leading public and private healthcare organizations toward interoperability, essentially retooled the meaningful use EHR incentive program to focus on enabling a more unified view of patient data. Health IT shops across America, meet “promoting interoperability.” [20]
Keep in mind that all this is in the context of healthcare IT systems for doctors, hospitals, and medical institutions. It doesn’t even contemplate how the patient could participate in a “unified view” of their own healthcare data. How much easier would the whole EHR portability problem be if patients could use their own SSI digital wallets to do the following?
-
Instantly obtain copies (on their phone, or securely stored in a private cloud) of their EHR records immediately after any medical procedure
-
Securely and privately share their EHR in seconds with the doctors and nurses of their choice
-
Provide secure, legally valid, auditable consent for medical procedures—for themselves, family members, dependents, etc.—directly from their smartphone or other networked device
-
Have a lifetime history of vaccinations, allergies, immunities, etc., available in a verifiable electronic record to share in seconds—in person or remotely—with schools, employers, doctors, nurses, or anyone who needs to verify it
Again, this list is not theoretical. The first major network for the patient-centric exchange of SSI digital credentials for healthcare, Lumedic Exchange, was announced in November 2020 and will go into national deployment in the U.S. in 2021 (https://www.lumedic.io/perspectives/introducing-lumedic-connect). This list doesn’t even mention how your personal EHR might be used by your own apps on your own devices for your own healthcare, or the impact of being able to securely and anonymously share your medical data with universities and medical researchers who can use it to advance the state of public health for all of us. (Dive into these topics in chapter 22 on health and supply-chain management in the pharmaceutical industry.)
1.6.4 Travel
Anyone who has traveled internationally knows the fear in the pit of your stomach when you deplane and take the (often very long) walk to customs. The questions flood your mind: “How long will the line be?” “What if it takes hours?” “Will I miss my connecting flight?”
Governments and airport authorities worldwide have been wracking their brains, trying to figure out how to remove that particular friction from international travel. Programs like Global Entry and CLEAR in the U.S., Nexus in Canada, Registered Traveller in the UK, and others worldwide are designed to do a deep check of your identity credentials, enroll your biometrics, and thereby give you a fast track through customs. But these programs cost tens of millions of dollars to set up and tens or hundreds of dollars to enroll in and require dedicated facilities and personnel in every airport.
How much simpler will international travel be when you can travel with a smartphone holding an SSI digital wallet that can do the following?
-
Produce instant proof of any digital credential you possess in a single QR code on your phone, just like a mobile boarding pass
-
At the same time, receive a new credential of having passed through security and/or customs at that particular airport, thereby building a private, verifiable audit trail of your travel that you alone can provide at subsequent checkpoints in your trip
-
Do all of this with privacy by design —specifically by using cryptographic proofs that disclose only the information required to meet government regulations at each checkpoint
-
Have all the travel documents you need—airline tickets, train tickets, hotel reservations, dinner reservations—flow automatically into your digital wallet, so they are always there when you need them
It might sound more like the world of Harry Potter than our world today, but this particular SSI magic carpet ride is the goal of a growing number of airports, travel consortia, and government agencies worldwide. It has been accelerated by the massive impact of the global COVID-19 pandemic—see the November 2020 announcement of the International Air Transport Association (IATA) Travel Pass (https://www.iata.org/en/programs/passenger/travel-pass/). But there are still significant hurdles we need to overcome before a global digital travel credential is a reality.
1.7 Major challenges to SSI adoption
As authors, we believe the SSI paradigm shift is already underway. However, we do not believe it is without significant challenges. At a 2019 event called “The Future of Digital Identity,” hosted by Citi Ventures, Vinod Baya, director and head of emerging technology at Citi, pointed out that there are three major challenges to the adoption of SSI [21]:
1.7.1 Building out the new SSI ecosystem
Some of the benefits of SSI (see chapter 4) can be realized by individual companies or communities. However, the full network effects will only be experienced when multiple industries, governments, and other ecosystems start accepting each other’s digital credentials. This, in turn, depends on achieving real interoperability between the essential components of SSI, as we discuss in chapter 2 and more deeply in part 2. For example, we will need digital credentials to work across different digital wallets from different vendors—some of which will also integrate digital money (fiat or cryptocurrency, for example). While this infrastructure is underway, it is still not mature, and there is much work to be done before it will be fully ready for internet scale.
1.7.2 Decentralized key management
As we explained earlier, the key to SSI is literally keys—cryptographic key pairs where the SSI identity holder holds the private keys in their own digital wallet. Loss of those private keys is tantamount to the complete loss of the holder’s digital identity. Key management has always been the Achilles heel of the adoption of cryptography and public key infrastructure (PKI). It has been so difficult that many experts believe it can only be handled by large enterprises and centralized service providers such as banks or government agencies.
The growth of cryptocurrencies has already led to some significant advancements in decentralized key management, and the rise of SSI is leading to much more research in this area. We believe this is one of the primary hurdles to the ultimate market success of SSI, which is why we cover core innovations in decentralized key management in great detail in chapter 10.
1.7.3 Offline access
SSI is based on digital credentials shared over a digital network. Yet there are many situations where we need to be able to prove our identity without having internet access or a digital device. For example, the Canadian Mounted Police might need to verify a driver’s license in the far north where internet access is simply not available. So SSI solutions need to be able to work offline or with intermittent or indeterminate connectivity. This is a major engineering challenge being tackled by SSI architects, but it is not yet a solved problem.
Moreover, beyond the technical challenges for the adoption of SSI, there are also risks involved with the adoption of any exponential technology. (See Singularity University’s “An Exponential Primer” at https://su.org/concepts.) SSI is not an exception to those challenges. For SSI to deliver its promises and mitigate the risks, the architectural choices made in the early stages of the infrastructure will be critical. This infrastructure is also currently missing the broader expertise needed for a subject as complex as identity. Many of the experts driving SSI have a technical background—and the legal aspects of SSI have attracted some highly internet-proficient lawyers—yet people from all disciplines and spheres of society are needed: sociologists, psychologists, anthropologists, economists, and so on. We hope the involvement of these and others outside the technology community will increase over time.
References
1. Cameron, Kim. 2005. “The Laws of Identity.” Kim Cameron’s Identity Weblog. www.identityblog .com/?p=352.
2. Security. 2017. “Average Business User Has 191 Passwords.” https://www.securitymagazine.com/articles/88475-average-business-user-has-191-passwords.
3. Morgan, Steve. 2015. “IBM’s CEO on Hackers: ‘Cyber Crime Is the Greatest Threat to Every Company in the World.’” Forbes (November 24). www.forbes.com/sites/stevemorgan/2015/11/24/ibms-ceo-on-hackers-cyber-crime-is-the-greatest-threat-to-every-company-in-the-world.
4. Zaharia, Andra. 2020. “300+ Terrifying Cybercrime and Cybersecurity Statistics & Trends.” Comparitech. https://www.comparitech.com/vpn/cybersecurity-cyber-crime-statistics-facts-trends.
5. Rainie, Lee. 2018. “Americans’ Complicated Feelings about Social Media in an Era of Privacy Concerns.” Pew Research Center. www.pewresearch.org/fact-tank/2018/03/27/americans-com plicated-feelings-about-social-media-in-an-era-of-privacy-concerns.
6. Oath. 2017. “Yahoo Provides Notice to Additional Users Affected by Previously Disclosed 2013 Data Theft.” Verizon Media. https://www.oath.com/press/yahoo-provides-notice-to-additional-users-affected-by-previously.
7. Neveux, Ellen. 2020. “80% of Hacking-Related Breaches Leverage Compromised Passwords.” SecureLink. https://www.securelink.com/blog/81-hacking-related-breaches-leverage-compromised -credentials.
8. Lim, Paul J. 2017. “Equifax’s Massive Data Breach Has Cost the Company $4 Billion So Far.” Money. https://money.com/equifaxs-massive-data-breach-has-cost-the-company-4-billion-so-far.
9. Ctrl-Shift. 2011. “Economics of Identity.” https://www.ctrl-shift.co.uk/insights/2014/06/09/ economics-of-identity.
10. Nakamoto, Satoshi. 2008. “Bitcoin: A Peer-to-Peer Electronic Cash System.” https://bitcoin.org/bitcoin.pdf.
11. Birch, David. 2014. Identity Is the New Money. London Publishing Partnership. https://www .amazon.com/Identity-Money-Perspectives-David-Birch/dp/1907994122.
12. SBIR. 2015. “Applicability of Blockchain Technology to Privacy Respecting Identity Management.” https://www.sbir.gov/sbirsearch/detail/867797.
13. Foxley, William. 2019. “President Xi Says China Should ‘Seize Opportunity’ to Adopt Blockchain.” CoinDesk. https://www.coindesk.com/president-xi-says-china-should-seize-opportunity -to-adopt-blockchain.
14. Cameron, Kim. 2018. “Let’s Find a More Accurate Term Than ‘Self-Sovereign Identity.” Kim Cameron’s Identity Weblog. https://www.identityblog.com/?p=1693.
15. Heath, Chip and Dan Heath. 2007. Made to Stick: Why Some Ideas Survive and Others Die. Random House. https://smile.amazon.com/Made-Stick-Ideas-Survive-Others-dp-1400064287/dp/1400064287.
16. Statista. 2020. “The 100 Largest Companies in the World by Market Capitalization in 2020.” https://www.statista.com/statistics/263264/top-companies-in-the-world-by-market-value.
17. Davidson, James Dale and William Rees-Mogg. 1997. The Sovereign Individual: Mastering the Transition to the Information Age. Touchstone. https://www.goodreads.com/book/show/82256.The_ Sovereign_Individual.
18. Citi. 2018. “Mobile Banking One of Top Three Most Used Apps by Americans, 2018 Citi Mobile Banking Study Reveals.” Cision PR Newswire. https://www.prnewswire.com/news-releases/mobile-banking-one-of-top-three-most-used-apps-by-americans-2018-citi-mobile-banking-study-reveals-300636938.html.
19. Vestal, Christine. 2014. “Some States Lag in Using Electronic Health Records.” USA Today (March 14). www.usatoday.com/story/news/nation/2014/03/19/stateline-electronic-health-records/6600377.
20. Sullivan, Tom. 2018. “Why EHR data interoperability is such a mess in 3 charts.” Healthcare IT News. https://www.healthcareitnews.com/news/why-ehr-data-interoperability-such-mess-3-charts.
21. Baya, Vinod. 2019. “Digital Identity: Moving to a Decentralized Future.” Citi. https://www.citi.com/ventures/perspectives/opinion/digital-identity.html.
