In this chapter, we continue the theme of part 3, exploring the historical origins and movements that led to SSI and the social, political, and philosophical implications going forward. This chapter goes directly to the heart of the matter: belief systems, the overarching mental and value paradigms that define everything we do in our lives—including our technology choices and architectures. Note that this chapter lays the groundwork for understanding chapter 16, which explains the evolution of the SSI community.
15.1 What is a belief system?
Many books have been written and will be written about what belief systems are, but let us try to present a short and (hopefully) generally acceptable definition:
The belief system of a person or society is the set of beliefs they have about what is right and wrong and what is true and false.
Belief systems answer all kinds of minor and major questions of life—and thus can be quite controversial. Such questions include, “Is party A or party B good or bad for the country?” “Are you in favor of the death penalty or against it?” “Do my children need a religious education?” “Is capitalism the source of the wealth gap?”
On almost any issue, the position we take depends on our belief system. This might happen with or without evidence—either way, our belief systems will guide us, even if it consists only of educated guesses or the sum of our life experiences. Belief systems affect everything from the most challenging political, wealth, family, and religious questions to the smallest questions about life.
If we look at SSI from this perspective, it should come as no surprise that some discrepancies exist about what might be considered SSI. For example, one reference point within the SSI community for defining what is considered SSI is based on the 10 principles of SSI defined by Christopher Allen in his 2016 essay “The Path to Self-Sovereign Identity” [1]. One of these is that SSI architecture needs decentralization to be censorship-resistant. Censorship resistance is a key concept of the decentralization community. People in the open source, blockchain, and SSI communities believe centralization needs to be avoided because if any single party has full control, in the long run, that control will be most certainly abused. You may or may not agree with this idea, but in the end, it is your belief system that is guiding you in accepting or rejecting it.
In the early days of SSI technology, many SSI projects chose a blockchain or distributed ledger technology (DLT) to act as a decentralized, verifiable data registry (see chapter 2). Decentralized technologies used for SSI might change in the future, but in this chapter, we explain the differences between first-generation blockchain and DLT technologies to exemplify how nuanced, ideological, and passionate the discussion around decentralization technology can become.
note There is no agreement on the market definition of the terms blockchain and DLT. We are using and explaining them in this chapter to highlight the ideological difference between blockchain and DLT. However, other people claim that blockchain is a subcategory of DLTs. In this chapter, we claim that Bitcoin started the blockchain technology and that DLTs are a separate technology.
We claim that the technology choices made for blockchain or DLT are reflections of belief systems about ownership and governance and highlight how this is relevant for SSI—and probably for anything else in life. The lesson we aim to convey is that keeping an open mind—and remembering that worldviews influence everything we hear and say—will help us to have empathy for people who might make different choices.
15.2 Blockchain and DLT as belief systems
The blockchain ecosystem started with the launch of the Bitcoin network on January 3, 2009, by Satoshi Nakamoto. As we detailed in chapter 13, Satoshi created Bitcoin to act as a peer-to-peer cash system without intermediaries or human authorities issuing currency. Instead, the network issued and registered all transactions in an architecture built on peer-to-peer technology, using monetary incentives based on game theory.
The early adopters of Bitcoin were often interested in cryptography, finance, decentralized systems, libertarian ideology, and the Austrian school of economics, among other things. The years after the launch of the Bitcoin network gave rise to different cryptocurrency-inspired speculation bubbles. The cryptocurrency bull market of 2013 that drove the bitcoin price to $1,200, a historic high at the time, was followed by a bear market that drove the price all the way down to $200 in the following two years.
note Capital B (Bitcoin) refers to the Bitcoin protocol and lowercase b (bitcoin) to the token or cryptocurrency of the Bitcoin protocol.
During this period, a new line of thinking developed that insisted on the virtues of blockchain as an architecture for consensus-driven data, yet without making cryptocurrency tokens the central function of the system. Some of these projects used so-called non-monetary tokens for internal governance functions but limited their transferability or currency-like properties, while others did away with the mechanisms of token economics.
note In the computer security and cryptocurrency industry, the term token generally refers to a cryptographic string of numbers and letters that contains no real data but relates back to real data. One bitcoin is an example of such a cryptographic string, as explained in chapter 6.
This line of thinking initially was called DLT to emphasize the role of the ledger over the token. Different technology players started creating decentralized data systems for the corporate world with a wider range of governance options, including highly centralized ones. This period is relevant to SSI because the worlds of blockchain, SSI, and DLT started cross-pollinating, exchanging ideological approaches and technical architectures.
To highlight how SSI relates to those blockchain and DLT technologies, we think that exploring the underlying belief systems can illuminate the sometimes abstract debates around technology choices. While they may become outdated over time, the core idea is to understand that even technology choices are influenced by belief systems. Note that neither of the two examples we use has to represent reality—they are just illustrations.
15.2.1 Blockchain “believers”
Adherents to early blockchain projects like Bitcoin and Ethereum tend to distrust traditional centralized institutions, even claiming this distrust as a core motivation to invest in decentralization projects. They often believe that, over the long run, centralized institutions will side with the strong or the large against the small, weak, or independent actors in an economy or society. As such, individuals need tools to protect themselves against the dominance of these centralized institutions of commerce, information, and law.
For cypherpunks (chapter 13), the key to a healthy system lies in decentralizing power. Because their trust in institutions is low, blockchain believers want governance systems that are as decentralized as possible. Many lobby for mechanisms to block or disincentivize re-centralization, such as incenting anyone to run an infrastructural node in order to have as many different node operators as possible—which also helps ensure censorship resistance. (A node is a computer or server running specific software that can connect with other nodes to run a peer-to-peer network.) In many of these systems, a unique token also plays a central and structural role. This is why blockchain discourse often focuses on disruptive change of economic and social power structures, often modeled on the classic Silicon Valley trajectory from startup to transnational corporation.
15.2.2 DLT “believers”
DLT believers tend to trust some centralized institutions more than others. They often see in decentralized technologies an opportunity to optimize current business and compliance processes—or discover new business opportunities in transparency and cooperation. For a DLT believer, some centralized institutions can work well, particularly if they incentivize a common architecture across industries, limiting competition to the services offered on top of a shared infrastructure.
For many, their distrust of tokens is rooted in legal, transparency, and regulatory concerns. Others fear that tokens could create new forms of monopoly or centralization. In both cases, DLTs are generally designed less to disrupt industries than to make industries more stable, compliant, and efficient. DLT believers strive to shift the terms of cooperation and competition in ways that create new business models.
15.3 How are blockchains and DLTs relevant to SSI?
If the main differences between blockchain and DLT believers are their attitudes toward economic and social central authorities, SSI complicates this further by focusing on a wider problem space. For example, the SSI ecosystem is motivated to help people and companies protect their privacy (from both the state and other people and companies) through decentralization. Many (not all) governments are generally comfortable with this approach because it does not undermine their authority. They know people are increasingly concerned about the prying eyes of big tech companies. Some governments actively encourage market solutions to privacy concerns, especially if those solutions can relieve them of the onerous task of enforcing citizens’ privacy.
In that sense, the SSI community—as you can read in more detail in chapter 16—is less rebellious or anarchistic than some of the blockchain early adopters. As an overall community, it wants to use decentralization to fulfill its vision of creating identity systems that enable trust and defend privacy without having to rely on a central party.
However, the challenge is that decentralization isn’t black and white but comes in various shades. Achieving decentralization is a fundamental and ongoing design challenge: depending on the use case, different levels of decentralization might be possible or necessary. To understand this, let’s explore some specific characteristics of blockchain and DLT systems.
15.4 Characterizing differences between blockchain and DLT
Between the two extremes of blockchain and DLT believers, there are many shades of gray. We can simplify somewhat by creating two general classifications:
-
Blockchains are trustless or permissionless systems: i.e., they are more open to new participants without permission from a centralized authority.
-
DLTs are trust-based or permissioned systems that generally require permission for future unknown participants to join.
Figure 15.1 illustrates the spectrum of possibilities between these two approaches. It is important to note that, while blockchain and DLT architectures have been driving SSI in its early days, new approaches to decentralized architectures such as pure peer-to-peer (P2P) networks are also emerging. So, there may be other ways to fulfill the decentralization and openness requirements of the SSI principles without depending on either blockchains or DLTs.
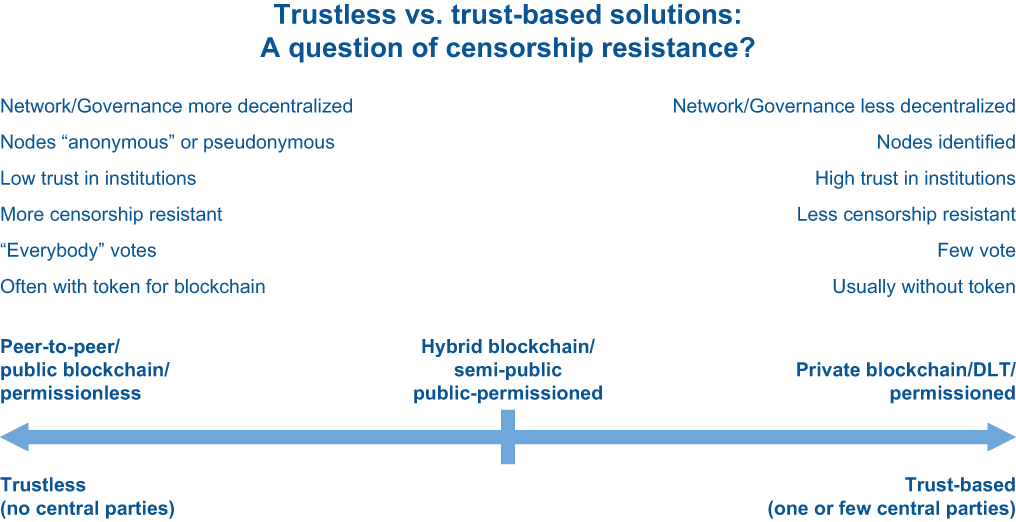
Figure 15.1 Trustless systems are more open and internally governed, usually using token-based systems, while trust-based systems tend to delegate governance and gatekeeping to trusted authorities.
Starting with network governance, we can explore how blockchains, hybrid blockchains, and DLTs differ with regard to decentralization.
15.4.1 Governance: How open is the network to open participation?
The governance of a blockchain or DLT is defined by how open it is to participation. The more decentralized and open to participation it is, the more challenging it usually is to create a system that is resistant to new forms of attack:
-
Blockchain—Governance in a blockchain like Bitcoin is decentralized through the global distribution of all nodes, each node containing all the blockchain data. This is enabled by free open source software that allows anyone to participate in Bitcoin. It also enables the relative decentralization of mining (which has become more centralized over time) [2] to reach a consensus on the truth in that blockchain. In Bitcoin and similar blockchain efforts, every effort is taken to maximize and protect decentralization according to the consensus around how that might be best achieved.
-
Hybrid blockchain—Governance in a semi-public or public permissioned blockchain is often defined by the validator nodes that are identified. These are usually controlled by public institutions like government agencies, consortia, educational institutions, and corporations. However, read access to the ledger is open to everyone, which is different from DLTs, which limit read access as well.
-
DLT—Governance in DLTs is mostly centralized in one or a few validator nodes that are identified and other nodes that might have read access with the permission of the validator nodes. Governance is closed: the network is made up of nodes by permission, and new nodes can only join with permission from the current validator nodes and/or external authorities.
15.4.2 Censorship resistance: How centralized is trust?
Censorship resistance [3] is often related to the level of decentralization of a blockchain or DLT. The fewer parties control a system, the less censorship-resistant it is because those few parties can influence censor transactions:
-
Blockchain—Censorship resistance in Bitcoin was envisioned as very strong by decentralizing the verification of transactions in many computers. However, the progressive concentration of mining that has come with increased hashing power (the total computational power behind a network) is a specter that may threaten Bitcoin’s censorship-resistance. This is a constant source of discussion in systems like Bitcoin.
-
Hybrid blockchain—Trust in a hybrid blockchain is lower than in a private permissioned DLT, but that trust is delegated to publicly identified nodes. Censorship resistance in this model depends on the nodes’ geographic and participant distribution, the level of transparency of their selection and expansion, and the risk of active attacks against the identified nodes. For example, if you run a network in Japan and all your nodes are Japanese, in the end, the Japanese government will most likely have the final say in architecture and governance.
-
DLT—Trust in the participating nodes in this model is high and can make sense when a corporation wants to organize its own internal network or when an industry or government wants to organize a consortium where all participants trust each other. Censorship resistance in this model is low, but that is rarely a key requirement since permissions and access are already in centralized hands. The more trust people have in the public or private institutions administering the DLT, the less need there is for more decentralization.
15.4.3 Openness: Who can run a node?
Blockchains and DLTs are composed of multiple computers or servers (nodes) interconnected in a peer-to-peer network. The easier it is for someone to operate a node, the more decentralized the network can be, although this can be complicated by tiered systems where nodes hold different privileges and responsibilities:
-
Blockchain—The ability to run a node is open to everyone, in principle, but the example of Bitcoin has shown that running a full node has become more difficult and costly over time due to scaling issues with the protocol. The token, or unit of account, is a fundamental aspect of the game theory model of a permissionless blockchain. For example, if an individual user runs a node that is not part of a professional mining pool, it is unlikely they will solve the cryptographic puzzle needed to mine a new block. However, they can still participate in decentralization by running a full node that verifies and relays transactions and verifies new blocks just for the sake of it. Some scalability research points to the importance of these nodes, but this too is a significant point of controversy.
-
Hybrid blockchain—Participation in a hybrid blockchain is usually open to all nodes, but they must fulfill predetermined requirements, usually involving setup, testing, node operation costs, and public or semi-public identification.
-
DLT—Only select, invited, identified nodes in a DLT can validate transactions. Because that process happens externally, a DLT usually does not need tokens except as an anti-spam mechanism.
15.5 Why “believers” and not “proponents” or “partisans”?
There are many different ways to achieve decentralization. Blockchain, DLTs, and pure P2P systems are just three of the possible approaches to SSI technology, and more are likely to appear. What is most beneficial is learning from each other and finding the best technology to improve life for everyone.
In addition, after the “blockchain hype cycle” [4], the keywords blockchain and DLT have lost a great deal of their meaning. We need to look beyond the labels and focus on how decentralization can be achieved for different solutions and use cases. Time might show that some solutions will need permissioned or hybrid models—because governments and institutions will require that from their citizens and companies—while other models might become completely permissionless—because the technology is good enough to eliminate the need for external management by traditional institutions. And sometimes centralized solutions might still be good enough.
We hope these examples convey how belief systems drive technology choices. Let’s explore now how these choices can be expressed in the decentralization community.
15.5.1 How do we measure decentralization?
From a computer science point of view, Satoshi Nakamoto created one possible solution to the long researched double spending problem that had limited the development of digital cash protocols or peer-to-peer electronic cash systems [5]. Satoshi’s proof-of-work (PoW) algorithm, a combination of technology and game theory, also provided a possible solution to the Byzantine Generals Problem [6], a computer science challenge for reaching consensus when communication channels are not safe and cannot be trusted. Much of the technical excitement around blockchain protocol design stems from these new solutions to decentralization obstacles.
In his 2017 reference article, influential Ethereum co-founder Vitalik Buterin [7] laid out his three-part criterion for decentralization. He theorized that centralization could creep back into systems designed to be decentralized if their architecture, logic, and political governance were not designed to maintain decentralization into the future. Of course, this whole discussion is relevant only if you strongly believe that decentralization is essential.
Architectural decentralization is ensured in a P2P network by distributing nodes across various subnetworks; these usually communicate in the traditional TCP/IP addressing structure of the mainstream internet. The portion of nodes that can fail at a given time without bringing down the entire network is a key criterion for this kind of decentralization, as is the portion of nodes owned or controlled by any one entity. In some cases, the portion of nodes located in any one jurisdiction or nation-state may be important, or the portion of nodes reliant on any one manufacturer of hardware, software, or infrastructure.
Logical decentralization means making all core code open source (transparent to independent development teams) and making all data readable across different implementations of a given protocol. Along these lines, important questions include the following:
-
Are the interfaces and data structures one discrete unit or a swarm of many distinct interacting units?
-
What would happen if we cut the system in half, between users and suppliers?
-
Would the two new units continue operating as independent entities if, for instance, half the nodes forked to a different implementation of the protocol?
Political governance decentralization is when a separation of powers between codebase maintenance and operation of the network—in combination with incentive structures informed by game theory—prevents any single stakeholder group (developers, miners, investors, markets, users, and so on) from pushing through changes to the protocol without the collaboration of the majority. On this dimension, the core questions are explicitly political:
-
How many individuals, contracts, or computers are needed to change the protocol?
-
What protects the minority from abuse at the hands of a majority of stakeholders?
-
What incentives do minorities have to stay in the system if their interests diverge from the majority’s?
This last concept of political decentralization is maybe the most ideologically charged and controversial of the three—and the most useful in identifying differences between decentralized systems. Some analysts propose that since blockchain data systems operate as infrastructure for both economic and non-economic systems, the separation-of-powers model of their internal governance should be more explicitly—and more carefully—modeled on the separation of powers in real-world political systems, particularly in modern liberal democracies.
Because of all this, designating a project as “decentralized” is not meaningful unless you consider all aspects of a system and its governance—and specifically how much sustained decentralization is core to its design. Bitcoin has achieved a high level of decentralization largely because of its global scale and the number of stakeholders maintaining equilibrium. But that status was not easily achieved. Building for decentralization is a significant challenge, particularly in smaller and privately controlled protocols. What’s more, the benefits of decentralization are not easily transferable to all use cases; and adequate decentralization is not guaranteed by anchoring data to a highly decentralized protocol or building on top of it.
15.6 Technical advantages of decentralization
From Buterin’s technical point of view, a decentralized system has to be fault-tolerant, attack-resistant, and collision-resistant. These traits often have significant positive side effects for the resilience and durability of a data system that offset the cost of blockchain development:
-
Fault tolerance means decentralized systems can continue working properly even when parts of the network are disconnected by fault or malfeasance, because the network is composed of many parts that can continue operating independently from each other. When they are connected again, even if transactions have been lost, the parts will synchronize based on the incentives in place. Fault tolerance is a fundamental aspect of any decentralized system.
-
Attack resistance for a decentralized system means redundancies make it exponentially more expensive to attack, destroy, or manipulate many nodes simultaneously, as opposed to centralized systems where only one central codebase or database needs to be attacked. Decentralization requires such an attack to be scaled up in proportion to the overall size of the system.
-
Collusion resistance in a decentralized system means it has been designed to prevent or at least disincentivize groups of participants colluding to take advantage of (or force the behavior of) other participants.
The diversity of a decentralized ecosystem is often one of the key elements to make it resistant to all three types of attacks. All these elements need to be assessed and weighed against each other to decide whether a decentralized system is resilient and decentralized enough for a given set of use cases and/or the values of its stakeholders.
While this last criterion of aligning with values is important, building consensus between shareholders can be a slow and costly process. Furthermore, creating decentralized systems can be exceedingly complicated and often expensive—making consensus even more elusive when such systems have no clear revenue model. In such situations, many “shareholders” will rightly question how much decentralization they can afford to pay for beyond the needs dictated by their use case.
The original cypherpunk dream (chapter 13) promises to empower individuals, leading to the belief that decentralized technologies can create a better, utopian world. However, there is also a risk that these technologies could backfire, creating a more dystopian world. Assessing the opportunities and risks requires us to be explicit and deliberate about our beliefs and the governance models encoded in them. It is not always an easy conversation to have, but with our planet’s global infrastructure at stake, the long-term consequences justify the discomfort and friction of some frank talk about politics and values.
References
1. Allen, Christopher. “The Path to Self-Sovereign Identity.” Life with Alacrity. http://www.lifewith alacrity.com/2016/04/the-path-to-self-soverereign-identity.html.
2. Kharif, Olga. 2020. “Bitcoin’s Network Operations Are Controlled by Five Companies.” Bloomberg. https://www.bloomberg.com/news/articles/2020-01-31/bitcoin-s-network-operations -are-controlled-by-five-companies.
3. Andrew, Paul. 2018. “Bitcoin Censorship Resistance Explained. CoinCentral. https://coincen tral.com/bitcoin-censorship-resistance.
4. Litan, Avivah and Adrian Leow. 2020. “Hype Cycle for Blockchain Technologies, 2020.” Gartner Research. https://www.gartner.com/en/documents/3987450/hype-cycle-for-blockchain-tech nologies-2020.
5. Nakamoto, Satoshi. 2008. “Bitcoin: A Peer-to-Peer Electronic Cash System.” https://bitcoin.org/bitcoin.pdf.
6. Stevens, Anthony. 2018. “Understanding the Byzantine Generals’ Problem (and How It Affects You).” Coinmonks. https://medium.com/coinmonks/a-note-from-anthony-if-you-havent -already-please-read-the-article-gaining-clarity-on-key-787989107969.
7. Buterin, Vitalik. 2017. “The Meaning of Decentralization.” https://medium.com/@Vitalik Buterin/the-meaning-of-decentralization-a0c92b76a274.
