CHAPTER 44. Security Issues for Wide Area Networks
SOME OF THE MAIN TOPICS IN THIS CHAPTER ARE
Computer Viruses, Trojan Horses, and Other Destructive Programs 854
Your Network Under Fire—Common Attacks 857
Spoofing and Impersonation 864
If It’s Too Good to Be True, It Isn’t 865
Staying on Top of Security Issues 869
When all you have to worry about are the computers attached to your local LAN and users you know personally, it’s easy to implement security policies and keep the network virtually safe from things such as viruses or other malicious programs. A properly trained user base, along with security guidelines that allow only outside programs approved for use on the network, can go a long way toward keeping a LAN safe. Of course, it still pays to regularly use an up-to-date virus-scanning program to be absolutely sure that you’ve cleaned up your network.
When you connect to the Internet, however, there are so many different ways that your network can be compromised—even when using a very well-secured firewall. At a company that this author consults for, a recent virus attack required over 500 man-hours to resolve. And, all of this was done in less than 24 hours by a dedicated team of network professionals. When you consider the number of personnel involved, you can get an idea of the reason why you should take proactive measures as best you can. Yet, in an enterprise network, you should have a staff that can handle such an attack. The only way to ensure that you can take care of this type of situation is not just to hire the most competent persons, but also to set aside some of your budget for ongoing training. Things change; things change even faster on the Internet.
Note
The SQL Slammer worm of January 2003 was illustrative of how fast things change on the Internet. This worm, capable of infecting the entire Internet within 15 minutes, has been called the Internet’s first “Warhol” worm, in reference to the popular Andy Warhol quote, “In the future, everyone will be famous for 15 minutes.” By most estimates, the SQL Slammer worm infected over 90% of vulnerable systems within 10 minutes of its first detection. Infected systems doubled every 8.5 seconds, and after only 3 minutes in the wild, the virus was scanning 55 million addresses per second looking for vulnerable machines.
Because of this, and other factors you will learn about in this chapter, it’s best to learn about the most recent kinds of attacks and then locate resources to help you stay aware of the latest news. One of the most common misconceptions about firewalls is that they offer complete protection. However, studies bear out the following facts:
![]() Staying on top of the latest developments in enterprise networking, the Internet, and even a SOHO network can be difficult at times. Part of the misconception may stem from the fact that the term firewall has become somewhat of a buzzword, implying that if some type of firewall is in place then all is well. A firewall is not a single technology. Instead, all but the simplest SOHO firewalls are a combination of technologies, some of which are constantly upgraded (such as those that filter specific Web sites or content). Many high-end firewalls must be updated regularly, as new protocol or application loopholes, worms, and viruses are discovered. In a small company, a firewall is a good idea but it is not a panacea. In both SOHO and large networks, a firewall is not a total solution for keeping out viruses. Thus, in addition to a firewall, you should always use a good antivirus program, and keep it up-to-date. In a large company with a staff of technicians maintaining a firewall, you can still never be sure that you are completely safe from intrusions. Be sure to keep in mind the following points concerning firewalls as well.
Staying on top of the latest developments in enterprise networking, the Internet, and even a SOHO network can be difficult at times. Part of the misconception may stem from the fact that the term firewall has become somewhat of a buzzword, implying that if some type of firewall is in place then all is well. A firewall is not a single technology. Instead, all but the simplest SOHO firewalls are a combination of technologies, some of which are constantly upgraded (such as those that filter specific Web sites or content). Many high-end firewalls must be updated regularly, as new protocol or application loopholes, worms, and viruses are discovered. In a small company, a firewall is a good idea but it is not a panacea. In both SOHO and large networks, a firewall is not a total solution for keeping out viruses. Thus, in addition to a firewall, you should always use a good antivirus program, and keep it up-to-date. In a large company with a staff of technicians maintaining a firewall, you can still never be sure that you are completely safe from intrusions. Be sure to keep in mind the following points concerning firewalls as well.
![]() A firewall can’t protect you from your own internal users. Fired or laid off anyone lately? Do you have an employee who was dissatisfied with his last performance review? Do you have an employee or employees who are not trained on a regular basis about computer security (and by that I mean more than once a year)? You might think that just programmers can open back doors to your network. Yet, perhaps the easiest way into a network is called social engineering—just try calling up a user and telling him that you are from the help desk and need to use his password to download a software update. You’d be surprised. Or, maybe you wouldn’t.
A firewall can’t protect you from your own internal users. Fired or laid off anyone lately? Do you have an employee who was dissatisfied with his last performance review? Do you have an employee or employees who are not trained on a regular basis about computer security (and by that I mean more than once a year)? You might think that just programmers can open back doors to your network. Yet, perhaps the easiest way into a network is called social engineering—just try calling up a user and telling him that you are from the help desk and need to use his password to download a software update. You’d be surprised. Or, maybe you wouldn’t.
![]() Many firewalls are difficult to manage. You can never be sure whether you’ve done all you need to do to block malicious traffic at the perimeter of your network. In an enterprise network, you should consider devoting at least one or more personnel exclusively to maintaining and managing a firewall. For a SOHO network, don’t take for granted a software firewall, much less a cable/DSL router that uses NAT. Email attachments, for example, can defeat a firewall easily. For these types of intrusions, use a good antivirus software (as stated previously) that examines emails as well as files on your computers’ disk drives. And be sure to use the update software to continuously stay on top of new virus definitions.
Many firewalls are difficult to manage. You can never be sure whether you’ve done all you need to do to block malicious traffic at the perimeter of your network. In an enterprise network, you should consider devoting at least one or more personnel exclusively to maintaining and managing a firewall. For a SOHO network, don’t take for granted a software firewall, much less a cable/DSL router that uses NAT. Email attachments, for example, can defeat a firewall easily. For these types of intrusions, use a good antivirus software (as stated previously) that examines emails as well as files on your computers’ disk drives. And be sure to use the update software to continuously stay on top of new virus definitions.
Consider a firewall to be only the first line of defense, not the only defense you put up for your network.
This chapter looks at some of the typical problems that can be introduced into your network from the Internet and then at resources you can use to further educate yourself on these topics.
You’ve Been Targeted!
Too often you are tempted to put in a quick fix and consider a problem solved. However, in the complex matter of network security, you’ll find there are no quick fixes. Because a network is composed of many components, hackers, crackers, and detractors have a large number of devices they can target, such as these:
![]() Routers—These devices stand at the perimeter of your network and sometimes perform firewall functions. The main thing a router can do is to block certain IP addresses or ports. This is the basic function performed by a firewall. Routers, though, are easy targets for many reasons. First, a router is your network’s connection to the Internet, so it’s directly exposed to the whole world. Second, routing protocols can be abused when hackers damage the routing table on your router. What good is a router if it doesn’t know where to relay network traffic to and from? You learn this in more detail later in this chapter when you read about ICMP redirects. Although there isn’t a lot you can do to protect a router from an attack over the Internet, you can take some steps to make it more difficult for potential intruders. You’ll learn about that subject later, in the section titled “Protecting Routers.” And another thing to consider is denial-of-service attacks. Because your router(s) stand at the periphery of your network, a constant stream of network traffic can be used to overwhelm a router and prevent you from receiving incoming data, much less sending data out onto the network.
Routers—These devices stand at the perimeter of your network and sometimes perform firewall functions. The main thing a router can do is to block certain IP addresses or ports. This is the basic function performed by a firewall. Routers, though, are easy targets for many reasons. First, a router is your network’s connection to the Internet, so it’s directly exposed to the whole world. Second, routing protocols can be abused when hackers damage the routing table on your router. What good is a router if it doesn’t know where to relay network traffic to and from? You learn this in more detail later in this chapter when you read about ICMP redirects. Although there isn’t a lot you can do to protect a router from an attack over the Internet, you can take some steps to make it more difficult for potential intruders. You’ll learn about that subject later, in the section titled “Protecting Routers.” And another thing to consider is denial-of-service attacks. Because your router(s) stand at the periphery of your network, a constant stream of network traffic can be used to overwhelm a router and prevent you from receiving incoming data, much less sending data out onto the network.
![]() Host computers—Servers on your network are supposed to provide data, print, email, or other important services to your users. After a host computer has been infiltrated, however, these services can be corrupted or made unavailable. If a hacker gets past the router or firewall, the host computers on your network are usually the next target. This is one good reason to use a private address space on the internal LAN and save your registered IP addresses for use by the routers and firewall devices that actually need a valid address on the Internet. This technique is known as Network Address Translation (NAT). If the intruder does not know the addresses of computers on your network, the intruder will have more difficulty connecting to them and causing trouble. As a general rule, it’s best to always hide information about the configuration of all computers on your internal LAN. If you must create a Web presence on the Internet, consider using a demilitarized zone (DMZ) to segment part of your network that interfaces with the Internet from the inside network.
Host computers—Servers on your network are supposed to provide data, print, email, or other important services to your users. After a host computer has been infiltrated, however, these services can be corrupted or made unavailable. If a hacker gets past the router or firewall, the host computers on your network are usually the next target. This is one good reason to use a private address space on the internal LAN and save your registered IP addresses for use by the routers and firewall devices that actually need a valid address on the Internet. This technique is known as Network Address Translation (NAT). If the intruder does not know the addresses of computers on your network, the intruder will have more difficulty connecting to them and causing trouble. As a general rule, it’s best to always hide information about the configuration of all computers on your internal LAN. If you must create a Web presence on the Internet, consider using a demilitarized zone (DMZ) to segment part of your network that interfaces with the Internet from the inside network.
![]() For more information on firewalls in general and using DMZs, see Chapter 45, “Firewalls.”
For more information on firewalls in general and using DMZs, see Chapter 45, “Firewalls.”
![]() Applications and services—There is a great debate on the Internet about open source code. One side of the debate is this: If the actual code for particular applications is known, it’s easier for patches or modifications to be made when some hacker detects a loophole in the application or service. The opposite argument goes like this: The bad guys also have a copy of the code and can spend all the time they need looking for vulnerable parts of the code that can be used to their advantage. When you are considering installing mission-critical software on a server, which should you use? I can’t really offer an opinion on this because both sides have good arguments. If you use a proprietary program purchased from a vendor, can you depend on the technical support staff of the vendor to help you if the application becomes a target? Microsoft and other vendors regularly post security warnings and patches. Do you install them?
Applications and services—There is a great debate on the Internet about open source code. One side of the debate is this: If the actual code for particular applications is known, it’s easier for patches or modifications to be made when some hacker detects a loophole in the application or service. The opposite argument goes like this: The bad guys also have a copy of the code and can spend all the time they need looking for vulnerable parts of the code that can be used to their advantage. When you are considering installing mission-critical software on a server, which should you use? I can’t really offer an opinion on this because both sides have good arguments. If you use a proprietary program purchased from a vendor, can you depend on the technical support staff of the vendor to help you if the application becomes a target? Microsoft and other vendors regularly post security warnings and patches. Do you install them?
You must pick your vendors carefully—for example, what is the response time when you place a service call for a minor issue? Can you count on vendor support in an emergency, or would you rather have the open source code so that your own staff (and others around the world who use the same code) can immediately begin trying to plug the loophole?
![]() Firewalls—Yes, because most commercial firewall products are well documented, they can be compromised by someone who studies what they protect, and how the firewall does it. Not all firewalls use the same techniques. No single firewall will ever protect you from every threat from the Internet. A skilled staff of professionals, however, can help you mitigate the threats that do get past your firewall.
Firewalls—Yes, because most commercial firewall products are well documented, they can be compromised by someone who studies what they protect, and how the firewall does it. Not all firewalls use the same techniques. No single firewall will ever protect you from every threat from the Internet. A skilled staff of professionals, however, can help you mitigate the threats that do get past your firewall.
![]() Your network—If you’re the sort of person who enjoys causing problems for other people, attacking the entire network is probably going to give you more pleasure than going after only a few host computers or applications. Think of how expensive it is to a large company such as eBay, CNN, or Microsoft when their networks are taken offline due to an attack. If a hacker can disable your entire network, the damage done can become quite expensive.
Your network—If you’re the sort of person who enjoys causing problems for other people, attacking the entire network is probably going to give you more pleasure than going after only a few host computers or applications. Think of how expensive it is to a large company such as eBay, CNN, or Microsoft when their networks are taken offline due to an attack. If a hacker can disable your entire network, the damage done can become quite expensive.
Usually, an attack is not as clearly defined as indicated here. Instead, many attacks are sophisticated combinations of several of the previously described varieties.
Computer Viruses, Trojan Horses, and Other Destructive Programs
Computer viruses have been around for a long time. These are programs that travel from one computer to another, using various methods, such as programs that are not what they appear to be. Shareware downloaded from the Internet is a popular method for spreading virus code. You really should seriously enforce a policy for any programs that are installed on any computer in your network. Even software applications from a known vendor should be tested vigorously in a laboratory setting before being deployed on host computers in the network. Shareware, of course, should be evaluated much more closely. Regardless of any policy you decide to implement, it should be clear that viruses are particularly dangerous and sometimes tricky to avoid. The use of antivirus software is a must and should be required protection on any size network where infiltration and data destruction is undesirable—and that includes just about every network, doesn’t it?
Note
The term virus is used loosely in many publications, as well as within this book, and is meant to include Trojan horses, worms, and other software that can damage your network or data. However, there are some distinctions that will be detailed in the following sections. Keep in mind that the use of antivirus software applies to all types of malicious code and must be regularly updated due to the wide variety of offending programs and the regularity with which they are created and spread.
Trojan horses are programs that an intruder plants on one or more servers in your network. If you have these types of programs, they can be difficult to detect, because many use the same filename as a file that is already part of your operating system or application software. The Trojan horse program is activated by some specific event, such as the arrival of a certain date, or by a user running a program that has been replaced by the Trojan horse. This latter tactic is very popular. Some programs are not what they appear to be.
Worms are usually considered to be self-propagating programs that travel through email as well as by other means. A worm will replicate itself by sending copies of the software to all or most of the addresses in your email address book. A worm travels through the Internet very quickly because of this aspect of its replication. The solution? Don’t open email attachments unless you have a good antivirus program (which you have kept up-to-date). After you open an email that contains a worm virus, all heck can break loose, and the friends in your address book will not be inclined to think very well of you!
Other types of destructive programs can attack your network. This is the case in a denial-of-service attack. The perpetrators never have to intrude into your network. Instead, they use one of several methods (which we’ll talk about in just a minute) to send massive amounts of network traffic to your network router or server. The server or router becomes overwhelmed and can no longer operate efficiently. Other denial-of-service attacks target specific resources, such as servers or applications.
Trojan Horse Programs
Trojan horses are programs that are planted somewhere in your network to wait for a signal before springing into action. After hackers have gained entry to a server in your network, they can easily plant a program and then run the program, at a time they choose. The program can listen on a selected port waiting for a signal. The program can wait until a certain time has passed. Many methods are used to trigger such a program.
When the signal or time comes, the Trojan horse does its destructive chores. One of the most common techniques for hiding these programs is to give them the same name as some other common program on the computer. Indeed, some Trojan horses are nothing more than modified versions of a standard operating-system file. So what appears to be one thing might be something entirely different. As mentioned earlier, a Trojan horse program also can be activated by other means. The main difference between a Trojan horse program (or a worm) and a computer virus is that the virus is usually activated, does its damage, and then attempts to replicate itself by some means, such as mailing itself to everyone in your address book. Trojan horses are more like bombs waiting to go off.
Computer Viruses
Computer viruses come in all sorts of variations. They have been wreaking havoc on computers even before the Internet became commercial. Before the Internet exploded into the large network it is today, bulletin board services were a popular method for exchanging files, such as shareware programs.
A virus program usually is distinguished by two features. First, the virus replicates itself so that it can be spread to other computers. The method of transport can be a floppy disk that has had its boot sector code modified, or it can be a macrovirus that comes as part of an email attachment that uses the Internet email system to move about. Second, a virus usually is created to do something destructive, such as wiping out the contents of a hard disk or damaging some other system resource. However, this second feature is not always present in a computer virus. Some viruses simply display a silly message on the screen to let the user know he’s been hit, and then they do no further damage.
Another thing to keep in mind is that a virus has two functions. First, it needs to be transported to another computer to infect. Second, it requires a mechanism to affect the system. In many cases these are implemented as two separate functions. The transport mechanism does just what it says: It finds a method (such as email) to get the entire virus package to another system (such as by using your address book to email itself to others). Then another part of the virus performs some action on your computer. This can range from a malicious action, such as deleting files, to an innocuous one, such as simply presenting a funny message on your screen. The important thing to remember is that viruses are becoming similar to worms, in that they provide a mechanism to propagate themselves, as well as to cause harm to your computer or network.
Now it seems that most viruses are destructive, so you should always use antivirus software on computers in your network. Although deploying an antivirus application on several hundred or several thousand computers can be expensive, especially when you consider that you also must pay for updates from the vendor, the amount of damage viruses can cause if you do get hit greatly justifies this cost. In an enterprise environment you can usually get a large discount for antivirus software. For some packages, you can simply purchase one copy for a small network, and then create file shares for each disk on a computer and configure the antivirus software to check all disks as well as file shares.
Many small network operators install a good antivirus software package and schedule the software to run on an infrequent basis, such as once weekly. If you are using the software for a home environment where the loss of data is insignificant, that might be a good solution, especially if you have a slow Internet connection. However, if you are operating a business from home (SOHO), I suggest that you run the antivirus software daily. You can schedule most products to run at night when you are not using the network. I also recommend that you use any update software on the same daily basis. Viruses are not picky—they don’t appear on the Internet on just a weekly basis. They can find their way into your network anytime—even on a daily basis. If you schedule software updates and virus scans to run at off-peak hours for your network, you might just find that you have avoided the latest, greatest new virus.
Tip
Can’t decide which antivirus software to buy? Visit www.symantec.com and click on Download. There are several products you can download and use for a 15-day trial period. You’ll find here a trial version of Norton antivirus software. You can also download a trial version of McAfee’s VirusScan software at www.mcafee.com. Click on Download, and then the Evaluate button next to the product version you want to evaluate. These are the two most popular products sold in computer stores today. A quick search of the Internet will bring up many more antivirus software packages. Two important factors for most software applications are ease-of-use and support. Consider support to be the most important factor when choosing an antivirus product. The company should be one you can contact via the telephone should an emergency arise, and one whose product enables you to download updates frequently.
How Infections Occur
Viruses and other computer maladies can travel through various routes to get to your computer. One of the most common methods is through the use of email. How many times did you hear on the news last year, “Don’t open the attachment if the subject line says...”? Because of the macro capabilities and newer features of modern email clients, it is easy to trick users into launching a program without realizing what they are doing. Many email macroviruses that you receive go through your address book first and mail a copy of themselves to all your friends. Then they go about doing their dirty work on your system. So, as a method of transport, email can be a very lucrative path for a virus to take. If an email offers a link that appears to lead to something that is just too good to be true, it probably isn’t true. The old saying “There ain’t no such thing as a free lunch” applies here. Anyone who has been on the Internet for a month or more will start receiving spam messages. Although most of these are harmless and can be deleted and ignored, there are always those that just seem to tempt the user in such a way that it must be further pursued. There are many companies that offer antispam software.
Tip
Many good antivirus software products on the market today not only can check the files on your computer’s disk drives, but also can intercept incoming emails and flag them as candidates for viruses. For example, Norton AntiVirus will query you to “quarantine” a suspect email attachment. You can view it later to decide whether it is actually a virus, or an attachment you need to view. Many products even can warn you if you try to copy a file from a floppy disk to your system. When purchasing an antivirus product, be absolutely sure to define what your needs are, and determine whether they can be met by the software you purchase.
If you set a policy to prevent users from making use of company email for personal purposes, you can prevent a lot of this spam. In this way you also might be able to keep harmful emails from causing you a problem in the first place. Many modern email servers can be configured to check for attachments and prevent suspect attachments from being delivered to the end user. Even Microsoft Outlook Express enables you to set a security level to protect against this threat if your firewall does not. Yet this functionality is usually based on a good antivirus program associated with the email server or firewall, or a content filter that screens known suspicious content.
Still other avenues into the systems on your network exist. For example, as discussed earlier, shareware, freeware, and other demo software downloadable from the Internet can seem a bargain at first. And maybe now and then you find a program that actually fits a business use. However, some programs contain viruses, and the writers of the viruses are just waiting for you to download the program and execute it. The results can show up right away or can be triggered by a signal, such as a certain date, before springing into action.
A good security policy for any site will require that users submit requests to a security team before using software that isn’t currently approved. The security team can first run the program through standard antivirus software and otherwise evaluate the security potential of the program. Never allow users to bring floppy disks (or other removable media) from home. This should be spelled out clearly in your company’s network security policy.
One of the most useful functions that antivirus software provides is the capability to update itself. For example, Norton antivirus software provides a Live Update function that downloads newer versions of the software components, as well as newer virus definitions. It is a good idea to use this function for a known virus vendor.
Yet, for software vendors that provide the same functionality, can you trust this feature? When it comes to shareware programs, or other small vendors, be wary of automatic updates. If given the choice whether to enable automatic download and installs, select instead to have a choice to review the download before installing it. In this manner you can experiment with the results of such an update in a laboratory setting before deploying it to your network clients.
Your Network Under Fire—Common Attacks
If all you had to worry about were virus and Trojan horse programs, life would be so much simpler. Just deploy a good antivirus application and monitor the alerts or log files the application produces. When a virus does creep into your network, use the appropriate software to remove it. In some situations in which time is of the essence and you don’t have time to wait for a vendor to come up with a fix for a newly discovered virus, you can reconstruct the server by either re-creating it on another system or restoring data from backups. You also can reformat the hard disk of the infected system and reinstall your operating system and applications.
However, after the Internet becomes an important part of your business’s bottom line, there are other potential problems you need to worry about in addition to virus and Trojan horse programs.
Denial-of-Service Attacks
A denial-of-service attack is characterized by the goal of the attack. The attack’s purpose is to cripple routers, servers, or other computers by consuming resources at a pace that makes them effectively unavailable for the ordinary user to perform required functions.
A denial-of-service attack can use different common methods to accomplish its purpose. For example, flooding a server or network with a huge amount of network traffic results in a slow response for all nodes connected to the network. When bogus packets (usually created by an application designed specifically to produce large numbers of packets) are coming into a network or server at a very fast rate, ordinary users will have a hard time getting their legitimate network packets delivered. Indeed, if a router becomes overwhelmed with enough traffic, it might simply start dropping packets because it cannot keep up with the pace. Another method commonly used is to send malformed packets that can cause problems such as buffer overruns and take advantage of other shortcomings in the operating system of the router or server.
Other resources can be targets also. For example, a Trojan horse program can be designed to do nothing except consume CPU cycles as fast as possible when it is activated. Thus, other programs running on the server will slow to a crawl, or possibly not function, if they cannot obtain CPU cycles. Most operating systems allow for the concept of prioritizing certain processes. For example, the operating system itself must have access to the CPU and can interrupt a user process when needed because the operating-system component runs at a higher priority than an ordinary user process. If a destructive program has been planted in your network, and if your password file has been decrypted, it’s easy to run a process at a high priority by using an administrative account that has the necessary privileges.
Another method of denying access to resources can take the form of changing configuration information so that the resource will not function properly. Changing router table information, for example, can make sites unreachable. Changing user account information can make it impossible for users to log on to a server. Changing configuration files (or Registry key values, in the case of an operating system such as Windows 2000/2003) can render applications or services unavailable.
Distributed Denial-of-Service Attacks
In the preceding section we talked about denial-of-service attacks. When you have to worry about only one computer trying to overload your system, you can usually block the particular incoming address at the router and then start the process of tracking down the criminal who has damaged your network.
But what do you do if you suddenly find yourself under attack by not one computer but several hundred or several thousand computers? This sort of attack is known as a distributed denial-of-service attack because the “attackers” are multiple computers that can be coming at you from anywhere on the Internet. This is almost the worst thing that can happen to your network from the Internet.
Several years ago a program called Trin00 was developed, and it has been followed by newer versions, such as the Tribe Flood Network (TFN) and Tribe Flood Network 2000 (TFN2K). These are not the only tools that can be used for a distributed denial-of-service attack, but they have been used many times to cause problems on the Internet.
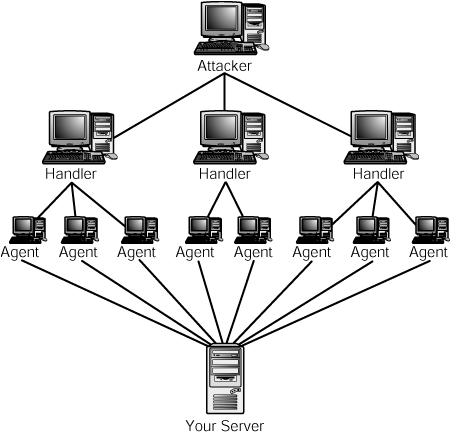
As you can see in Figure 44.1, a distributed denial-of-service attack is an organized attack that uses a central controlling computer to direct other computers to perform the actual attack on your network.
Figure 44.1. A distributed denial-of-service attack can overwhelm your network by using hundreds, if not thousands, of computers to simultaneously launch an attack.
In Figure 44.1 you can see that setting up this sort of attack is not necessarily an easy thing to do. Several steps are involved:
1. The perpetrator first infiltrates other innocent, unprotected computers and plants a program on them to be used later.
2. To make it difficult to track down the source of the original machine that sets off the attack, these infected computers are usually organized into a hierarchy. In Figure 44.1 you can see that a single attacker plants a “handler” program on some of the computers that have been infiltrated and “agent” programs on others.
3. The attacker sends a command to the handlers, who in turn send a command to the computers that actually perform the attack on your network.
4. You suffer! And, of course, you stay up all night with your staff trying to remedy the situation.
The reason this type of attack is becoming more prevalent is that more and more people are connecting to the Internet—home users as well as businesses. In a business network, you take precautions to secure your computers. Home users rarely secure their computers, not because they’re stupid but because they simply are not aware that dialing up to an Internet connection exposes their computers to intrusion from anywhere in the world. With broadband connections such as cable and DSL modems providing an “always online” connection, innocent home computer users might have no idea that while they are peacefully sleeping, some hacker is downloading a program to their computer that’s still online.
As you can see, no matter what you do to secure the servers and workstations inside your network, there’s nothing you can do about the millions of home users who are connected to the Internet with no firewall protection. It’s really a horrifying thing to consider that innocent users connected to the Internet can be unwilling participants in an attack on your network!
Another factor that makes this type of attack so deadly is that the attacker doesn’t have to be in any hurry. I can only assume that someone who would perform this attack is doing it for some sick form of pleasure. The hacker can spend hours, weeks, or even months breaking into unprotected computers and planting the seeds of destruction that will be activated later.
SYN Flooding
As you may recall, the SYN (synchronization) bit is used during the initial setup of a TCP/IP connection. It’s part of the three-way handshake. When a computer receives a request to open a new TCP session, the initial packet has the SYN bit set. The computer receiving this packet will set aside buffers in memory and create data structures that will be used to manage the TCP session. However, computers are limited in memory and can handle only so many sessions simultaneously.
The SYN-flooding attack just sends the first SYN packet that is intended to begin the setup of a TCP connection. The perpetrator ignores the responses received from the server, leaving half-open connections on the server that is under attack. The SYN-flooding attack sends a constant stream of packets with the SYN bit set. The targeted computer creates the necessary data structures in memory until finally it runs out. Again, the behavior of the computer will depend on the operating system. It might crash, it might hang, or it might simply just slow down and try to keep handling the incoming packets. Even if the system continues to run, the odds of a legitimate user being able to establish a TCP connection become almost impossible. The server is overwhelmed by these half-open connections it is trying to create at a rapid rate.
Whatever the target computer )does, however, there will come a point where no memory is available to run user programs or even to run the operating system itself efficiently.
Note
The SYN flooding is but one of the many denial-of-service attacks that can consume resources on your servers. This type of attack does not have to come from a single computer, however. As you will learn elsewhere in this chapter, a distributed denial-of-service attack can be set up by infiltrating a large number of unprotected computers, and then triggering them to start sending the SYN flooding, or other attack methods, to a single site.
The best defense against this sort of attack is to have a good firewall in place that can detect an odd stream of SYN packets coming in at a rapid rate and simply discard them. In addition, newer versions of most operating systems have been patched or modified to detect this rapid incoming flood of SYN packets and alert the administrator.
ICMP Redirects
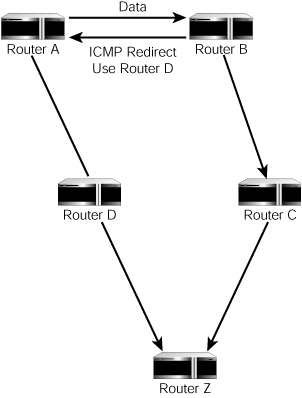
The Internet Control Message Protocol (ICMP) is used for many purposes, but one important function is to send a message to a router (or a server acting as a router) to tell the router to change entries in the routing table. Once again, if your router doesn’t have the correct routing information, it won’t be able to deliver network packets. ICMP redirects were created with the best of intentions. Suppose, for example, in Figure 44.2, that Router A sends a packet to Router B as the first hop the packet needs to take to eventually get to Router Z. If Router B knows there is a more direct route (using Router D), it uses an ICMP redirect to tell Router A the more efficient route.
Figure 44.2. An ICMP redirect message is used to tell a router of a better path to use.
This can happen under many different circumstances. In the simple example shown in Figure 44.2, it’s possible that Router A has just been brought back online and knows about Router B, but hasn’t yet updated its table to include Router D. In this situation, Router B, which has been up and running for some time, knows of the more direct path, so it sends the ICMP redirect message to Router A telling it to update its routing table.
![]() ICMP is covered in Chapter 24, “Overview of the TCP/IP Protocol Suite.”
ICMP is covered in Chapter 24, “Overview of the TCP/IP Protocol Suite.”
Unfortunately, it’s easy to download tools from the Internet that can be used to generate ICMP packets, and this can be used against you to wreak havoc on your routing tables. For this reason, many administrators use filtering rules on routers that connect to external networks to drop any incoming ICMP redirect packets. ICMP redirect messages can be very useful within your network, but you shouldn’t trust this information from routers that are not under your control.
The Ping of Death
Almost anyone who has ever dealt with networks has heard of this famous method of attack. The Ping of Death is basically a method of crashing your system by sending a packet that is excessive in size. The ping program is an extremely useful tool and is one of the first tools you should use when trying to determine whether connectivity exists between two machines. However, to sum up the information here, the ping utility sends a small packet (typically 64 bytes in size) to a remote IP address. The packet is an ICMP ECHO packet. The server that receives this packet normally responds with an ICMP REPLY packet. This simple exchange of packets proves that, although you might be having other problems communicating with the remote machine, the network path between the two systems does exist and is working.
However (keeping in mind that TCP/IP was not originally designed with security as a main issue), once again mean people found a way to exploit this utility by simply modifying the ping program to send extremely large packets (say, 65,536 bytes). Most networks won’t transmit a packet this large as a single unit. For example, most Ethernet packets range up to around 1,500 bytes. However, larger packets can be sent, using a process in which the original packet is fragmented into smaller packets that can pass through the network devices that connect one computer to another. When packets get fragmented, the receiving end usually stores the information as the fragments come in, and when the last fragment arrives, the data is reassembled into the original packet size. Operating systems typically use registers or set aside memory locations that are sized according to their expected use. If the receiving system knows that it’s illegal to create a packet in excess of a certain size, the variable that is set aside (and the buffer space to store the packet) can’t hold a number larger than it was created to hold. For example, a single byte (8 bits) can be used in binary to store a number of up to 255. The Ping of Death takes advantage of this by sending a packet (fragmented into manageable chunks) to the target system. When the target system attempts to reassemble the packet, lots of things can happen, depending on the operating system. If a variable overflows (that is, it’s not large enough to hold the size of the packet that’s being reassembled) or if the buffer space set aside for the packet is not large enough to hold the entire reassembled packet, it is possible for the incoming packet data to cross the buffer boundary and write over other important data.
When this happens, the behavior of the operating system is hard to predict. What area of memory was overwritten? What happens when the variable that stores the size of the packet can’t hold the value that the local component of the ping program is trying to store there? Well, usually the computer will hang, crash, or behave in some other undesirable way.
Users have known about this attack method for several years, and most operating systems have been fortified to prevent this attack from succeeding. However, there are still legacy systems (Windows 95, older versions of Unix, and so on) out there performing useful functions. Older systems are extremely vulnerable to this type of attack.
If you are worried about the Ping of Death, check with your vendor to determine whether any patches or firmware upgrades are available to remedy this problem.
Forged Email
Email is probably the most popular application used on the Internet. All people can have an email account, whether or not they have a computer at home. You can sign up for email accounts at several sites, such as Microsoft’s Hotmail or Yahoo’s email service, and use a computer at your school, at a library, or even at work to access the account.
Email messages, like Trojan horse programs, aren’t always what they seem to be. Just because the FROM line contains the name of someone you know doesn’t mean that the email actually came from that person. It’s a simple matter when configuring an email account to use any name you want. And with the online email services that don’t require you to use an email client (these services typically use an HTML interface—a Web browser), it can be difficult to determine where an email actually originated.
There are even programs freely available on the Net that allow you to create bogus email messages that appear perfectly normal in all respects. Although any intelligent person would probably not, in this day and age, open an email attachment from someone they do not know, they most likely would open an attachment from a friend. After all, if you can’t trust your friends...
The problem is that email is easily forged and can be used to get a program into your network. As a rule, delete spam and other email from sources you don’t recognize.
One of the more insidious things that can be done through email has occurred with alarming frequency in recent years. Worm viruses spread through email can read your address book, replicate themselves by mailing a copy of the virus code to everyone in your address book, and then start wreaking havoc on your system! About the only thing you can do in this situation is to disconnect the computer (or computers) from the network and clean out the mail store with a good virus program. If you have a mail server in your network, disconnect it and do the same. Until you’ve assured yourself that every computer in your network is free of such worm viruses, don’t reconnect to the Internet, or any other part of your corporate network.
Password Protection and SecurID and Smart Cards
Passwords and usernames have been the traditional method for authenticating a user to a computer operating system. There are much better methods you can use for environments that demand a high degree of security, such as smart cards and SecurID cards.
Smart card devices are synchronized with software that runs on the host computer. To log on, the user simply consults the password code, which changes at regular intervals, generated by the smart card. Because the application on the host computer is operating to change the account password using the same algorithm as the smart card, a user’s account password can be different every time she logs in. As long as the smart card and the application on the computer are kept in sync, it becomes very improbable for someone to “steal” your password. And most smart cards have passwords that can be used only one time. This means that even if someone happens to glance at the current password on your smart card, after you’ve used the password to log in, it can’t be reused and abused.
SecurID cards are based on digital certificates and require the user to enter a PIN for their use.
Network Back Doors
One of the best reasons I can think of for not allowing noncommercial shareware on a network is that if you can’t trust the vendor, you can’t trust the application. There are literally thousands of useful programs you can download from the Internet that can be used productively on a network. However, isn’t it better to simply purchase a commercial product from a reliable, known vendor who has a good technical support staff?
A back door into a network can be an application that was downloaded by an innocent user who is unaware that the program, in addition to doing what it says it does, also does other things, such as mailing out your user authorization files to some other computer on the Internet.
Shareware programs are not the only method used to create a back door into your network or host computer. Once again, you must consider the amount of trust you have in your users and use good judgment when granting privileges and access permissions to users. Delegating authority to others to make management easier is a great concept. Delegating these privileges to an unhappy employee is not a good idea. The problem is that it’s not always easy to tell a happy employee from one who is not. Suppose you have a technician who performs router maintenance activities. You have to trust that the employee is correctly programming the access control lists and other items on the routers.
However, there is an easy solution to this type of problem. Delegate the ability to manage the routers in your network to more than one person and establish a process of regularly reviewing router configurations. Trust no one! But maybe you can trust several people!
TCP/IP and UDP Ports
Ports are used along with an IP address to create a “socket” that uniquely identifies an end point in an IP connection. Whereas the IP address provides a unique identifier for the host computer, the port identifies the specific application for which the connection is to be used. When configuring routers, proxy servers, and other similar devices, use this simple rule: Disable all ports, and then enable only those you actually need to use. In most cases it’s easy to disable a port in one direction or in both directions. That is, you can restrict incoming or outgoing network traffic by port. That’s why you need to turn off all ports except the ones you specifically use. You don’t just lock one door in your house, do you? You lock them all. Even if a particular door is rarely used, it should be locked because you never know when someone is going to try to enter. This analogy holds true for TCP and UDP port numbers.
Using Modems in a Secure Manner
One reason you need a modem on a computer in your network today is to provide remote access capabilities for users who work from remote locations and need access to the corporate network. Allowing individual employees to have a modem on their desktop computer is just asking for trouble. Instead, use a separate server to set up a remote access service, using a reasonable number of modems to satisfy the needs of your remote clients. Remote access servers are typically very configurable—that is, you can provide additional authentication mechanisms, such as callback. With most operating systems, you also can grant dial-in access only to those users who need it. Finally, regularly review any log files created by remote access server modem banks to be sure that you have indeed configured the server correctly and that no unknown users are getting in.
Another solution for remote users is to use Virtual Private Networking (VPN) services. Windows 2000 Advanced Server and Windows 2003 Servers can be set up to allow users to create an encrypted communication tunnel through the Internet. Many routers also provide this functionality. The days of the modem are numbered. Home users in the near future will most likely demand broadband access, using cable or DSL modems rather than the typical modem that connects to the public switched-telephone network.
![]() In Chapter 15, “Dedicated Connections,” you can find out more about using a digital connection instead of an analog modem for remote users.
In Chapter 15, “Dedicated Connections,” you can find out more about using a digital connection instead of an analog modem for remote users.
Network Probes
A network probe or sniffer is a very useful tool for troubleshooting network problems. You can find software and hardware network sniffers that collect data packets from the network and allow you to examine them to determine what is causing a problem on your network.
Because the purpose of a network probe is to intercept packets and examine them, you can easily see how this could be very damaging when used for purposes other than troubleshooting.
Remember that the less information known about your network by outsiders, the more difficult it is to infiltrate your network. However, when someone has broken in, it’s a simple task to plant a program that does nothing except listen to the network and send information back to the person who planted the program in the first place. Using a network sniffer for this purpose enables an outsider to find out all sorts of useful information about your computers, users, and network configuration. For example, you already know it’s a bad idea to use FTP, Telnet, and other utilities that use clear-text to send usernames and passwords. However, you might think it’s safe to use these inside your network. Well, that’s not so. If someone has planted a program in a server on your network and is “probing” the packets that pass around your network, they’ll find it very easy to further infiltrate your network by obtaining more user account information, and thus be able to compromise one computer after another. Use safe utilities inside your network as well as for communications on the Internet. An example of this would be to use the Secure Shell utilities.
![]() The Secure Shell utilities are covered in Chapter 42, “Basic Security Measures Every Network Administrator Needs to Know.”
The Secure Shell utilities are covered in Chapter 42, “Basic Security Measures Every Network Administrator Needs to Know.”
Spoofing and Impersonation
Just as it’s a simple matter to create a program that can construct a steady stream of SYN packets and send them rapidly to your server, it’s also easy to create network packets that have false information in other fields of the IP header. For example, you might have a firewall set up to reject packets from known sources of trouble, based on the source IP address found in the header. However, there’s nothing to stop the hacker, cracker, or attacker from simply putting in another source address so that your firewall lets the packet through.
IP address spoofing is very easy to do. It’s also very hard to detect. One thing a firewall can do, however, is guard against packets that contain a spoofed address, making it appear that the packet originated inside your network. Think about it. If the source address of a network packet falls within the address range of your internal network, it shouldn’t be coming in through a firewall interface that’s connected to the Internet. It should be the other way around! All good firewalls can be configured to drop packets that arrive from the outside world with an address that makes it look like the packet came from your network.
If It’s Too Good to Be True, It Isn’t
One of the more prevalent scams that has proliferated on the Internet in the past two years is the claim that you can make a fortune by helping out a civil servant, or the wife of an ex-legislator of a foreign country, usually Nigeria. When you get these emails, don’t even try to respond. The scam involves your helping the sender transfer his secret funds to another bank outside the originating country. For a small fee, you can receive a few million in return. Yet, after you get involved, the person encourages you to open an account at a bank he uses (which is simply a Web site, not a bank) and transfer funds to that bank. In this manner he can (1) keep your cash and (2) in some cases gain access to your real account information from your own bank.
This is just one example. Again, if it appears too good to be true, it isn’t (true)! The Internet can be a great place to learn about new ideas, to get involved in e-commerce, and so on. It can also be a great place to get fleeced.
Another similar scam is an email that appears to come from a reputable company. Recently, emails from a site that appeared to be Microsoft was passed through the Internet. When you receive a suspicious email, look closely at the address of the email. Check the properties page of the email to see where it was sent from. You shouldn’t get emails, for example, from Microsoft.com, or Ebay.com, unless you have granted them the right to send you emails. Yet, if you get an email from, say, Microsoft-readnow.com, don’t open it! Check those emails carefully.
Preventative Measures
There are many standard techniques typically used to keep a network up and running. One of these preventative measures is regular backups. If your system becomes infected with virus programs or if you find that data has been corrupted, you’ll understand the importance of regular, frequent backups. In addition, it’s a good idea to keep offline copies of important data files for an extended period. Simply doing a backup each night and overwriting the tape or tapes the next night will provide you with very little protection. Damage to your system might not become evident until weeks or, in some cases, months after the initial intrusion.
There are also commercial and noncommercial products you can use to help safeguard your system. These include intrusion-detection mechanisms, antivirus programs, and programs that can monitor changes on important servers.
So where should you start when defining the defensive mechanisms needed to protect your network? Let’s start at the edge of the network—the router.
Protecting Routers
Routers typically can be configured in several ways. You can attach a serial cable and terminal directly to most routers and perform configuration tasks. Another method is Telnet. Most modern routers allow you to Telnet into the router to perform configuration tasks. Turn this functionality on only when it is needed, and then turn it back off. The same goes for unnecessary protocols and services. In a manner similar to deciding what services you want to allow through a firewall (and in what direction), you should turn off all unnecessary services on a router. You’ll have to consult your documentation to find out the particular commands you’ll need to use. However, a good document on router security can be found at the following URL:
www.cisco.com/warp/public/707/21.html
You might want to check vendor Web sites for other router products that are in use on your network to look for similar advice. Additionally, be sure to stay informed of router firmware updates and operating-system updates and patches. As new threats are discovered, a responsible vendor will release information or code that can be used to help improve the security of the routers that stand guard at the edge of the network.
The Network As Target
There are some problems for which there is currently no easy solution. The distributed denial-of-service attack discussed earlier in this chapter is one of those. When the entry points into your network are saturated with an overload of network traffic, there’s not much you can do about it. The best tactic you can use when such an attack occurs is to try to block out the address ranges from which the attack is coming. But when your network is being singled out by several hundred other compromised computers, it’s rather difficult to quickly program routers to block all of these network addresses. The fact that many large Internet sites have been taken down during the past few years by these kinds of attacks should be indicative of how serious this attack can be. What can you do? Gather all the information you can, and, when the attack is over, try to backtrack to find out where the attack initiated. At this time it might not be possible to do this because one computer can set off others to do the dirty work for them. If you don’t have access to the actual computers that perform a distributed denial-of-service attack, you can use the information on those other systems to further research the problem.
So for now, the best solution is to hope that this doesn’t happen to you and to use an Internet service provider that has a good technical team that can respond quickly to help block sites that are generating this type of attack. And by all means, if you are targeted, get the authorities involved.
Protecting Host Computers—Encryption and Virus-Protection Software
After an intruder gets past a router, it’s usually pretty easy to intrude further by gaining access to host computers on the network. Again, it is so easy to simply put up a router and firewall configuration and assume that your network is safe. However, even if these methods do protect you from outsiders, you still must worry about users who are allowed on the network. A disgruntled employee can do more damage (and probably do a good job of hiding the evidence) than many network intruders. Host security is a very important topic.
You should first start by becoming intimately familiar with the resource-protection and user-authentication schemes used by your computers. For example, many Unix variants provide for a shadow password file that is not easily accessible. When someone breaks into a Unix server, it’s a simple matter to download the contents of the /etc/passwd file and spend a few minutes or hours using an automated program to encrypt words in a dictionary, check to see whether they match the encrypted password in the stolen file, and then simply log back into your Unix box using a valid password!
The applications you run on servers or workstations can also make the host computer an easy target. For example, if you are using older versions of FTP or Telnet, you’re sending usernames and passwords about your network in clear, easy-to-read ASCII text. A network sniffer (which can be something as simple as a Trojan horse program planted somewhere in your network) can watch for these and transmit them back to the intruder. Because secure versions of these and other related utilities are available, you should always be sure to use the secure versions, even if it means purchasing additional software that already comes with your operating system.
![]() You can find more information about standard TCP/IP applications that are particularly vulnerable by reading Chapter 25, “Basic TCP/IP Services and Applications.”
You can find more information about standard TCP/IP applications that are particularly vulnerable by reading Chapter 25, “Basic TCP/IP Services and Applications.”
If you have an important server that is absolutely critical to your business operations, you might want to consider keeping a “hot spare” around. That is, create another server that is virtually a clone of the important server. If the original server is compromised, place the hot spare into service. This might involve a little time if you have data that needs to be restored to the hot spare before it can be used. However, for servers that contain data that doesn’t change often, such as some Web servers, you can have an exact duplicate sitting around just waiting to be used in case the operational Web server becomes compromised.
In this case, however, you need to be sure that the “hot spare” itself has not been compromised. Some malicious code can remain around for many months before causing problems. This is another good reason to use updated antivirus software on a regular, frequent basis.
Another way to protect servers is to use the tools that the operating system provides to protect some services. For example, you’d be a fool to place a directory on your system disk for use as an anonymous FTP site. The last thing you want is to have someone filling up all the space on your system disk. Most operating systems allow you to set quotas that define how much space a particular user account can use on a server’s hard drives. Enforcing quotas can help prevent an attack that consists of consuming all the available space on a disk. In addition, you can set alarms to notify you when quotas are being used up at a rate that is faster than what you see during normal operations. It’s then an easy matter to track down the source of the data coming into the server and to terminate the user process.
Additionally, protecting computers should also involve software that detects malicious code. Even home PC users are aware of the value of antivirus programs. There are so many vendors of this software that it would be pointless to attempt to list them here. However, when you do choose an antivirus program, there are some things you should consider when making a purchasing decision. For example, does the vendor respond quickly with updates to the software as new viruses are discovered? Does the software have the capability to remove the virus after it has been discovered? Does the software have the capability to scan floppy disks and files transferred to the computer through the network? Of these, the capability to quickly respond to new threats is perhaps the most important. However, your situation might dictate other factors that are more important. Note also that many firewall products now contain some type of virus-detection mechanism.
Using Tripwire
There are many programs you can use to help determine whether your system has been compromised. Tripwire is a very popular host-based DOS (HDOS) program that can be used for this purpose. Tripwire was originally developed in 1992 by Gene Kin and Dr. Eugene Spafford. The Academic Source Release (ASR) version of Tripwire can be downloaded for noncommercial use from Tripwire’s Web site. In addition, Tripwire has created commercial versions of the software, including an enterprise manager program (Tripwire Manager) that uses SSL for communications and simplifies management of multiple servers and workstations.
Tripwire is based on the concept of taking a “snapshot” of system resources, such as files, directories, and, in the case of Windows NT, Registry settings. The information gathered by Tripwire is stored in a secure database and is used to compare a server later to determine whether changes have been made and what those changes were. A policy file allows the network administrator to control the types of data that Tripwire monitors and to prioritize certain events using a rule base. In addition, Tripwire can produce reports that make monitoring the system easier for administrators.
Currently, Tripwire runs on the following operating-system platforms:
![]() Windows NT 4.0, Windows 2000, Windows 2003, and Windows XP Professional
Windows NT 4.0, Windows 2000, Windows 2003, and Windows XP Professional
![]() Solaris (SPARC) versions 2.6, 7.0, 8.0, 9.0, and 10
Solaris (SPARC) versions 2.6, 7.0, 8.0, 9.0, and 10
![]() IBM AIX 4.3.3, 5.1, 5.2, and 5.3
IBM AIX 4.3.3, 5.1, 5.2, and 5.3
![]() HP-UX 10.20, 11.0, 11ivl, 11iuZ
HP-UX 10.20, 11.0, 11ivl, 11iuZ
![]() Several versions of Linux
Several versions of Linux
Some of the things that Tripwire can monitor are specific to an operating system, whereas others (such as file types and sizes) can be monitored on all platforms. For example, here are a few of the items you can use Tripwire to monitor on Unix systems:
![]() Addition, deletion, or modification of files, along with file permissions, types, and sizes
Addition, deletion, or modification of files, along with file permissions, types, and sizes
![]() Inode number and number of links
Inode number and number of links
![]() Owner and group IDs for files
Owner and group IDs for files
![]() Modification timestamps and access timestamps
Modification timestamps and access timestamps
In addition, hash algorithms can be used to ensure the integrity of the contents of files. Tripwire supports several kinds of hashing algorithms, such as CRC-32, MD5, and the SHS/SHA algorithm, among others.
For Windows NT systems, the list that can be monitored includes the standard file components and things such as these:
![]() File attributes, such as archive, read-only, hidden, or offline
File attributes, such as archive, read-only, hidden, or offline
![]() Create and access times
Create and access times
![]() NTFS Owner SID, NTFS Group SID, and other NTFS attributes
NTFS Owner SID, NTFS Group SID, and other NTFS attributes
![]() Addition, deletion, and modification of Registry keys and the values of those keys
Addition, deletion, and modification of Registry keys and the values of those keys
These lists are not all-inclusive. For more information about acquiring an evaluation copy of Tripwire, visit the Web site www.tripwire.com.
User Awareness and Training
Social engineering is a term used a lot lately to describe an easy method for gaining access into your network. Put quite simply, are the users of your network trained in security measures? A quick test is to simply have someone from your help desk call a user and ask him for his password. I would bet that in at least half of the cases the users will give out their passwords. A help-desk person shouldn’t have to ask this type of question! Instead, if people at your help desk need to access a user account, they can notify the user that they are changing the password temporarily and will notify the user when to reset the password to a value known only to the user.
A password policy should also be in effect to ensure that common names and words are not used. Yet, one must be careful to avoid making passwords so difficult that users have a hard time remembering them. Most operating systems have the capability to keep a history list of passwords to prevent their reuse within a specified amount of time. You’ll also find that you can usually set a minimum and maximum password length.
Social engineering also can involve dumpster diving. How secure are the printouts that you throw in the trash can? Do you have paper shredders (and a security policy dictating their use) in place? Even Hollywood stars know that much useful information can be obtained from a trash can! This goes not just for paper materials. When you decommission old tapes or old computer hard drives, do you take the time to destroy any data that is stored on them? It may be well and good to donate old computers to nonprofit organizations or schools, but it’s also a good idea to reformat the hard drives and reinstall the operating systems before you do so. Tapes can be made useless by various means, including bulk tape erasers that zap the contents in just a few seconds.
Staying on Top of Security Issues
Your network will never be secure unless you make an effort to keep up-to-date with the latest discoveries concerning security issues. There are many good sites on the Web that you can use as resources to help you get the latest information as well as advice on how to better secure hosts and networks. Keep in mind that those who would do harm to your network are usually one step ahead of you. It’s a continual catch-up game. The quicker you find out about a problem, the quicker you can take precautions to protect your network.