CHAPTER 13
TERRORIST OPERATIONS AND TACTICS
How Attacks Are Planned and Executed
… the dialogue of bullets, the ideals of assassination, bombing, and destruction, and the diplomacy of the cannon and machine-gun.
“Military Studies in the Jihad against the Tyrants” (the al-Qaida manual)
CHAPTER OVERVIEW
Ideologies of terrorist groups vary greatly, but their tactics and weapons are often similar. This chapter outlines common ways terrorists organize and conduct their operations. Though the range of potential terrorist activities is vast, typical organizational principles are often used to prepare and conduct operations, whether targeting government buildings with plastic explosives or computer systems with cyberattacks. Understanding these basic principles, tactics, and weapons is a key step toward preventing and responding to terrorist attacks.
Technology plays an important role in analyzing the nature of modern terrorist threats. In ancient times, terrorists struck with daggers, stabbing their victims in public markets to spread fear. The development of modern explosives allowed extremists to attack with far greater impact, a trend being accelerated by the increasing sophistication and availability of automatic weapons, plastic explosives, missiles, and WMD. Terrorists have harnessed evolving technologies, such as mobile phones for communication and remote detonation, to make their operations more efficient and even to launch attacks in entirely new venues: jet airliners opened the way for hijackings, and the Internet created a new battleground in cyberspace. Dissemination of technical knowledge in areas such as microbiology, chemistry and nuclear engineering, combined with the rise of extremist groups bent on achieving mass casualties, raises the specter of new and catastrophic terrorist tactics.
CHAPTER LEARNING OBJECTIVES
After reading this chapter, you should be able to
1. Identify common organizational features of terrorist groups.
2. Explain the major tactical phases of a terrorist operation.
3. Describe considerations used by terrorists in selecting targets.
4. List common terrorist tactics.
5. Define the criteria that might influence a terrorist’s choice of tactics.
TERRORIST PLANNING
Terrorist groups typically exhibit a hierarchy of planning. Each group has a driving ideology—a top-level orientation, such as religious or racial extremism, from which the organization generates strategic objectives. Such objectives have ranged from forcing the withdrawal of the United States from the Middle East to sparking a race war in America. To pursue its goal, the group develops a plan, which allocates resources to achieve specific results. Plans are driven by doctrine, or the basic principles that guide operations. On the level of specific missions, terrorist units use tactics, practiced actions relating to the group and its adversary, which are built upon individual skills possessed by members of the group.
Terrorism by the Book
In the 1980s state sponsors such as the Soviets, Cubans, and Palestinians, who trained large numbers of terrorists during the Cold War, and the Iranians, who influenced terrorist groups in later years, refined terrorism to the realities of a globalizing world. Their students performed on an international stage; interested parties could study the attributes of successful attacks, and learn the lessons of failed ones, from the nearest television or newsstand. Behind the scenes, counterterrorism officials could also trace the spread of sophisticated techniques, such as advanced bomb-making skills, from one group to another.
Soviet and Western military doctrine, detailed in widely available training manuals, provided many groups with a fundamental understanding of military tactics and skills applicable to terrorism. From these and other sources, specific terrorist texts evolved. Minimanual of the Urban Guerrilla, written by a South American revolutionary, detailed tactics for Communist guerrillas attacking U.S.-supported nations. These tactics were emulated by terrorists in the Americas and Europe, among other locations.
At home, The Anarchist’s Cookbook—with its detailed instructions on topics such as explosives, lock picking, and document fraud—has been associated with numerous extremists. Right-wing radicals closely studied The Turner Diaries, a novel in which racists take over the United States. The book, with detailed descriptions of terrorist operations, was cited as an inspiration by Timothy McVeigh, who bombed Oklahoma City’s Murrah Federal Building in 1995, and other domestic terrorists.1
Among primary terrorist documents today is “Military Studies in the Jihad against the Tyrants,” also known as the al-Qaida manual. Found in the British residence of a suspect in al-Qaida’s 1998 bombing of U.S. embassies in Africa, it was translated and introduced into evidence at a federal court. Reflecting lessons from decades of jihadist combat in the Middle East, it likely also represents the influence of a burly al-Qaida terrorist named Ali Mohamed. Trained by the U.S. military in Special Forces tactics while an Egyptian military officer, Mohamed served as a sergeant in the U.S. Army during the late 1980s, teaching troops at Fort Bragg, North Carolina, about the Middle East. During this time Mohamed was also an al-Qaida operative, and before his eventual capture, he translated U.S. military manuals and provided advanced special operations–type training for the group.2
Terrorist Skills and Weapons
Successful terrorist operations require a broad range of talents. Most members of a terrorist group have limited capabilities; none has all the skills needed. These competencies include ideology/religious knowledge; weapons; explosives; small unit tactics; intelligence techniques or tradecraft such as clandestine communication and disguises; counterintelligence; codes and ciphers; map reading; sabotage; surveillance and countersurveillance; photography; document counterfeiting; foreign languages; psychological warfare, information operations, and propaganda; cyber skills; interrogation and torture; medicine/first aid; the operation of powered aircraft, gliders, automobiles, motorcycles, and watercraft; target selection and assessment; hand-to-hand combat; and for highlyselect personnel, WMD expertise.
Modern terrorist groups include personnel capable of using a range of weapons. In the case of domestic and international terrorist groups that threaten the United States, this arsenal may include automatic weapons such as the M-16, M-60, AK-47, G-3, and Uzi; handguns; shotguns; man-portable air defense systems (MANPADS); rocket-propelled grenades (RPGs); explosives such as dynamite, C-4 and other plastic explosives, improvised explosives, including those made from munitions such as mortar or artillery rounds (often used for stand-alone and vehicular improvised explosive devices, or IEDs), detonation cord and various detonators, and explosive suicide belts and vests; grenades; knives and other edged weapons; clubs; garrotes; martial arts weapons; mace; fire bombs; and improvised poisons and chemical agents.
THE TERRORIST ORGANIZATION
Dramatic offensive operations get terrorists the publicity they desire, but it is secrecy that allows them to survive. U.S. intelligence officials have noted that in the Cold War, threats such as Soviet armored divisions were easy to find but hard to kill, while today’s terrorist adversaries are easy to kill, but hard to find. Because they usually operate in hostile environments against more powerful conventional forces, terrorist groups must maintain security. For a terrorist, detection usually means defeat.
Leadership
Security often begins with a command-and-control organization and a group leader located far from the field of operations. Modern technology such as satellite and mobile phones and the Internet have made it easier for commanders in a relatively secure area to direct operations in a more dangerous one (though to be sure, lack of electronic communications discipline can prove deadly when operating against sophisticated opponents such as the United States). Often led by a charismatic individual with extensive training, the group may also use committees and subcommands to coordinate action.
In some cases, terrorist movements may even forgo centralized leadership. Operatives in related groups, or even individual freelancers, may initiate attacks on behalf of the larger group. Individual radicals may adopt “leaderless resistance,” forming tiny independent cells and conducting their own attacks in response to inspirational messages and strategic guidance conveyed via websites, e-mail, and books. Both al-Qaida and right-wing domestic extremists have focused on fomenting homegrown violent extremism (HVE), as discussed in Chapters 10 and 12.
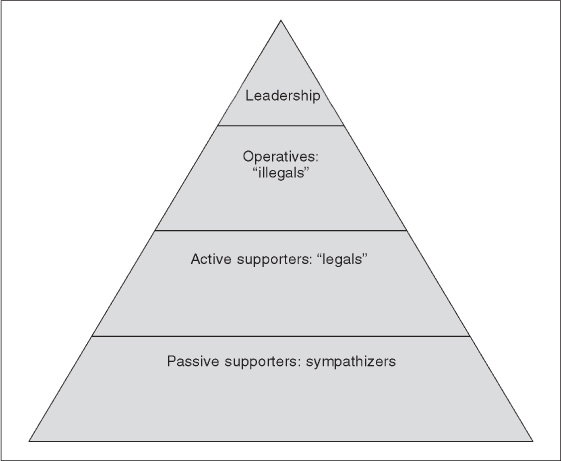
Types of Followers
Participants in the terrorist organization may fall into several categories as depicted in the figure. Hardened operatives known as cadre carry out terrorist operations and train others. Those who can be termed active supporters may not participate in attacks or other operations, but do knowingly provide intelligence and logistical support. Passive supporters are sympathizers to the cause but restrict their support, perhaps by joining and contributing to legal front groups. The Turner Diaries divides terrorists into “illegals,” who are known to the authorities as operatives and operate underground with the mission of conducting direct attacks, and “legals,” who may portray themselves as law-abiding activists while at the same time supporting a terrorist group by providing propaganda, legal defense, funding, intelligence, and initial identification and screening of potential recruits. Terrorists often move through these categories, starting by joining legal extremist groups and gradually becoming more radical until they are selected for membership in the terrorist organization. Overlap between the far fringes of legal extremist organizations and the ranks of terrorist groups can create special challenges for law enforcement officers, who must monitor and prevent terrorist activity without violating the civil liberties of legitimate protestors.
Cell Structure
In order to maintain security, groups often organize themselves into cells, small units of several individuals with specific missions. The members of one cell may never meet those in another. This prevents a single individual from knowing the identities or operations of the larger group, limiting damage if the individual is captured.
Cells can be divided into a number of categories:
• Operational: Carries out missions
• Intelligence: Collects information through surveillance and other methods
• Logistics/auxiliary: Supports operations with funds, supplies, weapons, housing, and other needs
• Sleeper: A common term most often used to describe cells of trained operatives waiting underground for orders to carry out a mission
FIGURE 13.1
CLASSIC CATEGORIES OF TERRORIST GROUP AND SUPPORT MEMBERSHIP. IN MODERN TERRORISM, LOOSELY AFFILIATED SUPPORTERS MAY TAKE DIRECT ACTION AS PART OF “LEADERLESS RESISTANCE.”
Operational Security
One essential tool for terrorists is preventing intelligence and law enforcement from uncovering information about their organization and operations. “Married brothers should observe the following,” instructs the al-Qaida manual, “not talking to their wives about Jihad work…” The manual also includes detailed instructions on the use of countersurveillance, codes, and cover stories to avoid detection. Iyman Faris followed many of these precepts of operational security. While his wife and neighbors in Ohio knew him as a family man and truck driver, the naturalized U.S. citizen with a gleaming smile was actually an al-Qaida operative. Born Mohammad Rauf in Kashmir in 1969, Faris—who reportedly held a license to transport hazardous materials—drove his rig across the country delivering cargo to businesses and airports. He also found time to visit Pakistan and Afghanistan, where he met Usama bin Ladin, joined the jihad against America, and began working with al-Qaida’s top operational leaders, according to court documents filed by U.S. authorities.
Along with a scheme to bring down the Brooklyn Bridge and an alleged role in supporting a plot to bomb an Ohio shopping mall, Faris was asked to obtain tools to derail trains. These tools were code-named “mechanics shops” in e-mail messages between Faris and al-Qaida, according to court documents. The plans hit a roadblock during a 2003 reconnaissance operation in New York, when Faris spotted tight security surrounding the Brooklyn Bridge. He e-mailed his leaders that “the weather is too hot,” indicating the plot could not succeed because of the bridge’s security and structure. But in this case, al-Qaida security procedures were not strong enough. Before he could launch a different attack, Faris was arrested, reportedly tripped up when his e-mail messages to al-Qaida were found in the computer of a captured terrorist. He ultimately pled guilty to terrorism-related charges.3
TERRORIST SUPPORT OPERATIONS
A horrific explosion is over in seconds. A hostage situation usually lasts days at most. But the activities needed to generate and support such terrorist operations require months or years of effort. These tasks include recruitment and indoctrination; network building; training; logistics, supply, and communication; and propaganda and psychological operations. They are what make the group an ongoing enterprise and provide the foundations for actual attacks.
PHASES OF A TERRORIST ATTACK
Most terrorist attacks involve common phases that take an operation from the first steps of target selection to the final phases of reviewing a completed mission and determining lessons learned for future operations.
Target Selection
Terrorist groups have thousands of potential targets. Based on their strategy, they identify and strike specific ones. While each attack is unique, common factors inform the target selection process. Because their general aim is to attack one group of people in order to influence others, their objectives are often selected for symbolism or other factors that make them high-value targets.
The principle of symbolic value accounts for the disproportionate number of attacks on: American citizens, who represent a system hated by a wide range of terrorists; on embassies, which symbolize the nations whose diplomats they house; against national airlines, which bear flags, crews, and passengers of target nations; on mosques of different sects, whose adherents may be considered apostates; and against mass transit systems, which play an important role in daily life (and are highly vulnerable). Among domestic terrorists, government offices—such as the Oklahoma City building that represented the federal government Timothy McVeigh so detested—are often on target lists. In the 9/11 attacks, al-Qaida believed the World Trade Center represented the U.S. economy; the Pentagon, the U.S. military; and the Capitol, U.S. support for Israel.
Once terrorists have identified potential high-value targets, they assess their vulnerabilities, such as lack of defensive measures, and tactical characteristics, such as the ease of escape offered by nearby roads. Locations with limited defenses are called soft targets. Some locations are both high-value and soft targets. For example, in 2003 terrorists, apparently acting independently, attacked McDonald’s restaurants across the globe. Assailants from various different groups but with a common aversion to this American icon threw a hand grenade at a Greek restaurant, tossed a Molotov cocktail into a Norwegian outlet, left a time bomb under the table in one Turkish McDonald’s and bombed two others, hurled a fire bomb at a Saudi restaurant, used TNT to blow up the men’s room in a Lebanese restaurant, set fires outside restaurants in Germany and France, and exploded a bomb near an Argentine restaurant.4
Many other factors influence target selection, such as timing. The periods before elections, or during important holidays and anniversaries, may add psychological value. The previous history of a target may be important: terrorists failed to destroy the World Trade Center on their first try in 1993 and so returned to finish the job in 2001. In other cases, such as 9/11, the symbolic value of a target may be combined with its functional value, as attackers seek to inflict not just psychological but also economic or military damage.
Operational Phases
Once the target is selected, the attack is planned and conducted through a series of phases. First, the group gathers intelligence and conducts reconnaissance activities. This is followed by operational planning, recruitment specialized personnel, surveillance on the target, countersurveillance to ensure the plotters have not been detected, rehearsals and dry runs, training for specific elements of the attack, movement to the attack, the attack itself, escape and/or exfiltration from the site, exploitation of the attack through propaganda or intelligence techniques, and after-action reviews (for example, the al-Qaida manual includes detailed critiques of botched attacks).
TERRORIST OPERATIONS
The variety of terrorist operations is limited only by the imagination and resources of terrorists. Al-Qaida operatives’ brainstorms for the 9/11 attacks included hijacking up to 10 planes and crashing some of them into nuclear reactors.5 But certain operations have become especially frequent and successful components of the terrorist repertoire.
Ambushes
The ambush, a surprise attack from a concealed position on a moving or temporarily halted target, is a common military tactic often used by terrorists abroad. In early 2003 a Kuwaiti civil servant ambushed a vehicle carrying U.S. civilian contractors outside Camp Doha, Kuwait. The attacker, who claimed inspiration from al-Qaida, killed one American and wounded another.6 The al-Qaida manual includes instruction on ambushes and suggests blocking the victim’s car in traffic and then opening fire.
Sabotage
By disrupting normal activities, terrorists can spread fear in uniquely insidious and effective ways. Attacks on infrastructure such as power lines can foster widespread feelings of vulnerability. The terrorists may also see symbolic value in subverting their adversary’s technology. For example, monkeywrenching, a tactic used by environmental extremists, includes placing spikes in trees that saboteurs do not want felled. Loggers who accidentally hit the hidden spikes with their chain saws can be badly injured. A far more destructive example is the derailment of trains, plotted on more than one occasion by al-Qaida after 9/11 and employed by other groups in years past. In October 1995 one person died and dozens more sustained injuries after a group calling itself the Sons of the Gestapo used sophisticated techniques to derail a 12-car Amtrak passenger train in Arizona. In 1986 someone removed a 39-foot-long section of rail along tracks used to transport spent nuclear fuel through Minnesota. A train carrying lumber hit the sabotaged section and derailed before the train with the nuclear waste arrived. Near the site, authorities found a sign reading STOPRAD-WASTESHIPMENTS.
A related type of attack seeks to create environmental damage. For example, an al-Qaida prisoner claimed the group had planned to use timed devices to ignite wildfires across western America.7 (The Japanese military hoped to do the same with “balloon bombs” launched during World War II.)
Kidnappings
Kidnappings require extensive planning and logistical capabilities, but they have proven an effective fund-raising and propaganda tactic for terrorists across the globe. The Revolutionary Armed Forces of Colombia (FARC) and the Colombian National Liberation Army (ELN) abducted numerous Americans for money. The Abu Sayyaf group in the Philippines, an al-Qaida ally, also specialized in this technique, in one case demanding $10 million and the release of prisoners in exchange for a kidnapped American. The captive managed to escape. Another American prisoner, Guillermo Sobero, was beheaded. In some cases, the planned profits of a kidnapping may be counted purely in terms of propaganda. In 2002 terrorists abducted Wall Street Journal reporter Daniel Pearl in Pakistan and then beheaded him and released a video of the crime. A similar fate befell Americans Nicholas Berg and Paul Johnson during 2004. Other spectacular kidnappings have included those of Italian premier Aldo Moro, captured by the Communist Red Brigade and murdered in 1978, and U.S. Marine Corps Lieutenant Colonel William “Rich” Higgins and CIA officer William Buckley, kidnapped and killed in separate incidents during the 1980s, allegedly by Hizballah, the Iranian-backed terrorist group.
Hostage Taking
A term sometimes used synonymously with kidnapping, hostage taking more commonly refers to the seizure of a group of victims in order to gain publicity or concessions. Often conducted as part of a siege or hijacking, hostage taking is highly risky for the terrorist, whose chances of escape are limited. Perhaps the most widely known hostage incident occurred during the Munich Olympics in 1972, when Palestinian terrorists captured Israeli athletes at the games, creating a running standoff that ended in the deaths of the hostages. Another spectacular hostage incident occurred in 2002, when Chechen terrorists occupied a Moscow theater, seizing more than 800 hostages from numerous countries. Russian security forces ended the episode by pumping anesthetic gas through the facility’s ventilation system, allowing them to kill the terrorists, but also poisoning many of the hostages.
Antiaircraft Missiles
Weighing just 40 pounds, these missiles—also known as MANPADS or surface-to-air missiles (SAMs)—can bring down a 100-ton passenger jet from a mile away. While U.S. forces seized large numbers of these systems from al-Qaida and Taliban fighters in Afghanistan, thousands more are in circulation around the world. In recent decades MANPADS are estimated to have downed up to two dozen large and small civilian aircraft, killing hundreds of people. In 2002 two missiles believed fired by al-Qaida followers missed an Israeli Boeing 757 leaving Kenya. This attack reinvigorated efforts to find ways to protect U.S. jetliners from attack.8
Hijackings
In the 1970s hijacking became a staple of terrorist activity. Some significant hijackings include the Entebbe (airport) incident, the 1976 diversion of a passenger plane to Uganda, where the passengers were later rescued by Israeli commandos; and the 1985 hijacking of a TWA Boeing 727 headed from Athens to Rome, during which U.S. sailor Robert Stethem was tortured, killed, and tossed from the plane. As of 2011, the FBI was still seeking some of those accused in the TWA hijacking, including Ali Wata, a Hizballah member believed living in Lebanon for whom the U.S. offered a $5 million reward.
Bombings
Many terrorists have agreed with a philosophy expressed in al-Qaida’s manual: “Explosives are believed to be the safest weapon… Using explosives allows [al-Qaida operatives] to get away from enemy personnel and to avoid being arrested… In addition, explosives strike the enemy with sheer terror and fright.” Bombings may involve elaborate weapons from the crude to the sophisticated and strategies of varying complexity. For example, an attack may involve two bombs, one to breach outer defenses and the other to destroy the location within. An initial bombing may be followed by a second, or “secondary device,” timed to hit rescue workers. In recent decades, the development of suicide bombing has added a grim new dimension to this terrorist tactic (see Chapter 10.)
Leave-Behind Bombs
One of the simplest and most effective terrorist tactics is the time bomb. Left behind by an operative, the hidden bomb escapes detection until it explodes. In early 1975, Puerto Rican nationalists killed four people with a bomb left outside a Wall Street bar. Less than a year later, a time bomb in a locker blasted holiday travelers at New York’s LaGuardia Airport, killing 11 people. Despite a massive investigation of numerous terrorist groups, the case was never solved.
In more recent years, mobile phone technology has provided an effective way to detonate bombs remotely, such as the device that killed five U.S. citizens at Jerusalem’s Hebrew University in 2002. Also in 2002 a terrorist bombing at a Bali nightclub claimed 202 lives. In 2004 terrorists killed almost 200 people during a coordinated set of bombings aboard Spanish commuter trains. Terrorists hit the London subway the next year, killing dozens.
Phone and other transmission devices such as garage-door openers were often used in IED attacks against U.S. and allied troops in Iraq and Afghanistan, as discussed below.
Letter Bombs
From the American Unabomber to suspected Islamic extremists, terrorists have long used the mail system to deliver death to the doorsteps of their enemies. The mail has also been used to deliver chemical and biological elements such as anthrax mailed to U.S. targets in 2001 and the toxic agent adamsite sent to U.S. and foreign embassies in Europe in 2003.
Booby Traps and Improvised Explosives
Booby traps may serve as the primary tool of operations, such as for assassinations, or to support other objectives. For example, they may protect weapons caches or be left behind at the scenes of kidnappings or other operations to impede investigators. The al-Qaida manual includes detailed instructions on creating booby traps, including one devised to blow up a victim’s television set. “However,” the manual cautions, “a brother [terrorist] should not be allowed the opportunity to work with setting booby traps until after he has mastered the use of explosives … because the first mistake a brother makes could be his last mistake.”
Terrorists may also create IEDs. According to U.S. authorities, al-Qaida planned to blow up U.S. high-rise complexes by sealing apartments, filling them with natural gas, and detonating them with timers.
IEDs were used in devastating attacks on the mass transit systems of Spain and Great Britain.
During the wars in Iraq and Afghanistan, IEDs took a deadly toll among coalition forces and civilians, becoming increasingly sophisticated as the United States developed effective countermeasures. American efforts included extensive data collection and analysis of mechanical and operational characteristics of IED attacks, along with forensic exploitation of evidence left behind in order to identify and track the bombers (including if they and/or their tactics surfaced in the U.S. homeland).
While improvement in U.S. tactics, vehicle armoring, and countermeasures foiled an increasing number of IED attacks, the insurgents adjusted their techniques, aided by the Iranian government, which was repeatedly accused of providing them with advanced technology and training
Grenade Attacks
Deadly, preassembled, and requiring little skill to use, grenades are an effective weapon, especially for poorly skilled or supported operatives. A 2002 grenade attack by suspected Islamic militants against a Protestant church in Pakistan killed two Americans and wounded many more.
Aircraft Bombings
Midair bombings have killed hundreds of passengers in recent decades. Major attacks include an Air India Boeing 747 downed in 1985 with more than 300 people aboard; a TWA plane ripped open by a 1986 bomb that sucked four victims, including an eight-month-old baby, to their deaths thousands of feet below; a (South) Korean Airlines plane bombed by North Korean agents in 1987; a French UTA flight destroyed in 1989; and the bombing of Pan Am Flight 103.
Terrorists keep developing technology in the hopes of evading bomb detection procedures and equipment. A terrorist with a bomb in his shoe failed to destroy a 2001 flight when his fellow passengers subdued him. The U.S. government warned of far more advanced “teddy bear bombs,” or explosive-impregnated fabrics such as coats or pillows that could be smuggled aboard aircraft without being detected by X-ray machines.10 In 2006 terrorists in Britain planned to smuggle liquid explosives aboard numerous airplanes and explode them in flight, prompting regulations on the amount of fluids U.S. air passengers could carry aboard. The Christmas bomber successfully wore an “underwear bomb” aboard a U.S.-bound flight in 2009 and failed to destroy the airliner only because of a malfunction in the device. Another failed Islamist terrorist plot involved sending explosive printer cartridges aboard cargo jets.
Car Bombs
The lethality of a conventional bomb is linked to its size. The use of cars or trucks allows terrorists to deliver larger payloads. Many Americans learned of this tactic from the Beirut bombings of the 1980s and the 1993 World Trade Center attack. A huge truck bomb destroyed the Oklahoma City federal building in 1995. The next year, an explosives-laden fuel truck detonated outside a U.S. military facility in Saudi Arabia.
For years, insurgents in Iraq and Afghanistan played a deadly game of cat-and-mouse with coalition forces as they sought to defeat evolving American defenses against vehicle-borne improved explosive devices (VBIEDs). In a number of cases, individual VBIEDs killed more than 100 people. Chlorine gas was even included in some vehicles with the hope of causing chemical casualties. (Propane gas was the deadly cargo in a truck detonated by terrorists outside a Tunisian synagogue in 2002.)
In 2010 an operative of Tehrik-E Taliban Pakistan (TTP), aka the Pakistani Taliban, placed a large bomb in an SUV and ignited it in Times Square. Due to an error in production, the device failed to explode.
Suicide Attacks
Starting in the 1980s, many of the car bombers described above added an effective component to their attacks—suicide. With no need for escape, bombers could deliver explosives directly into the heart of the target. Eventually suicide attacks grew to include strikes by pedestrians and even boats loaded with bombs. Finally, on 9/11 the terrorists mastered the use of airplanes as suicide weapons. (The dynamics of suicide attacks are discussed in chapter 10.)
Suicide Bombing by Boat
Al-Qaida members piloting a small boat crammed with explosives blew up the USS Cole in 2000, killing 17 sailors aboard the ship in Yemen (the group had failed in an earlier attempt against a U.S. Navy ship when the suicide boat sank under the weight of explosives). Two years later, an explosive-filled boat rammed a French oil tanker off the coast of the same country.
Suicide Bombing by Individual
U.S. and allied forces in Iraq and Afghanistan faced many attacks by individual suicide bombers, who also targeted civilians. Israel has also been a major target of such attacks. Numerous U.S. citizens have died in suicide attacks by Palestinian terrorists, including during 2003, 2002, and 1995. Palestinian extremists pioneered many suicide bombing techniques, including the indoctrination of bombers and the production of suicide belts filled with explosives and engineered to allow easy detonation by the bomber. Other groups also focused on suicide attacks, most notably the Liberation Tigers of Tamil Eelam, or Tamil Tigers.
Suicide Bombing by Aircraft
A natural evolution in the progression of suicide terrorist techniques, the use of airplanes for suicide bombings had already been developed by Japan’s kamikaze pilots, who rammed their explosives-packed aircraft (and suicide torpedoes and boats) into U.S. ships during the waning days of World War II. (The Turner Diaries, the novel that served to inspire a number of domestic terrorists, includes a suicide flight into the Pentagon by the protagonist.)
In 1994 an emotionally disturbed American crashed a small plane onto the White House grounds. That same year, Algerian hijackers planned to ram a French airliner into the Eiffel Tower or explode it over Paris but were thwarted when commandos seized the aircraft on the ground. Intelligence reports indicated other terrorists had also considered this tactic before it was employed to such devastating effect on 9/11.
Sieges
A low-tech but effective tactic is to seize a building or other location with symbolic value and/or occupants. The world witnessed this during November 2008 as Islamist extremist terrorists attacked numerous locations across the city of Mumbai, India. The terrorists, reported to be from Pakistan’s Lashkar e-Tayyiba group, marauded through the city, striking a train station, Jewish center, café, and luxury hotels. The attacks killed more than 170 people, including 6 Americans, according to the Department of State. Some terrorists holed up at the luxurious Taj Mahal Palace and Hotel, where they murdered guests and fought to their deaths against Indian security forces—all while the world watched on live television. (Pakistani-American businessman David Headley later pled guilty to helping plan the Mumbai attack.)
Hoaxes
Just the threat of attack can achieve terrorist goals, from creating fear to generating intelligence. Bomb threats can disrupt airline flights and, when repeated, engender complacency among security personnel and the public. Terrorists may also stage hoaxes in an effort to study the response of authorities in order to plan more effective attacks. In some cases, such as the 2001 anthrax attacks, a terrorist tactic can spawn hundreds or even thousands of imitation hoaxes. After the anthrax attacks, authorities wasted untold amounts of time and money in so-called “white powder” incidents, responding to suspicious materials sent via the mail by extremists and even unthinking practical jokers.
Psychological Warfare and Information Operations
Seeking to affect one group of people by attacking another, terrorist groups greatly value psychological operations. These can range from broad policy announcements and threats by group leaders to the distribution of videos featuring the beheading of captives (video of attacks on U.S. troops are also widely distributed by Islamist extremists). After 9/11 al-Qaida and associated groups invested significant resources in propaganda efforts, harnessing international television and the Internet as prime outlets, and sometimes using American citizens as spokesmen. Such messages performed several functions, including recruiting and impacting policy deliberations by targeted nations.
Mass media allow terrorists not only to influence large audiences, but also to inflict actual injuries on them. Events such as 9/11 have been shown to cause psychological symptoms in some television viewers. It is theoretically possible that images shared on the Internet, such as the horrendous beheading videos made by Islamist extremists, could cause similar damage to some people.
Finally, terrorists and their supporters are well versed in the uses of misinformation, which can be introduced into policy debates in Western countries (such as news reports and discussions over the treatment of U.S. detainees).
Other Common Tactics
Among other terrorist actions are assassinations; raids, which may target specific individuals such as tourists or critical infrastructures; drive-by shootings, sometimes conducted by motorcyclists; sniping; rocket or mortar attacks; robberies; and fire bombings. If no weapons are handy, al-Qaida has suggested ramming Westerners with cars. The driver of an SUV did just that in a 2006 attack at the University of North Carolina, stating he was avenging the deaths of Moslems overseas. Israel has seen similar attacks, including by operators of heavy machinery.
CHAPTER SUMMARY
Terrorists have a huge number of potential targets and a range of capabilities with which to strike them. While those responsible for securing the homeland must consider all possible terrorist attacks, certain tactics have proven especially common. More than a thousand years ago, knife attacks inspired fear; in the modern world, terrorists have used car bombs to the same effect.
When “new” types of attacks occur, they have often been foreshadowed by earlier incidents, which underscores the importance of U.S. homeland security officials studying “lessons learned” from battlefields in Iraq, Afghanistan, and elsewhere. Yet even new tactics involve traditional operational phases, which offer opportunities to disrupt the terrorists. Stopping terrorists before they strike has a special urgency in the modern era, especially given the threat of WMD.
CHAPTER QUIZ
1. What organizational features do terrorist groups use to maintain their security?
2. What makes an attractive target for a terrorist?
3. Name two major tactical phases of a terrorist operation.
4. Identify three terrorist tactics that have claimed large numbers of victims.
NOTES
1. William Pierce, aka Andrew MacDonald, The Turner Diaries (Fort Lee, NJ: Barricade Books, 1996), p. 98.
2. Alan Feuer and Benjamin Weiser, “Translation: The How-to Book of Terrorism,” New York Times (April 5, 2001), A1.
3. “Iyman Faris Sentenced for Providing Material Support to Al Qaeda” (October 28, 2003), www.usdoj.gov/opa/pr/2003/October/03_crm_589.htm. For wife’s lack of knowledge, see Pierre Thomas, Mary Walsh, and Jason Ryan, “The Terrorist Next Door,” ABCnews.com (September 8, 2003), www.abcnews.go.com/sections/wnt/US/sept11_faris030907.html.
4. U.S. Department of State, Patterns of Global Terrorism 2003 (Washington, DC: Department of State, April 2004), 23, 65.
5. National Commission on Terrorist Attacks Upon the United States, “Outline of the 9/11 Plot,” Staff Statement No. 16, (released June 16, 2004), 13 www.9–11commission.gov/staff_statements/staff_statement_16.pdf
6. Unless otherwise noted, details on terrorist attacks noted in this chapter are from Patterns of Global Terrorism and the State Department’s “Significant Terrorist Incidents, 1961–2003: A Brief Chronology,” http://www.state.gov/r/pa/ho/pubs/fs/5902.htm.
7. USATODAY.com, “FBI: Al-Qaeda Detainee Spoke of Fire Plot” (July 11, 2003), www.usatoday.com/news/washington/2003–07–11-alqaeda-fire_x.htm.
8. The Federation of American Scientists, “MANPADS Proliferation,” www.fas.org/asmp/campaigns/MANPADS/MANPADS.html; Congressional Research Service, “Homeland Security: Protecting Airliners from Terrorist Missiles” (November 3, 2003).
9. Federation of American Scientists, “Missile Watch November 2010,” http://www.fas.org/programs/ssp/asmp/publications/ASMP_Publications_2010/Missile_Watch_Vol3_Issue3.pdf#page=10.
10. John Mintz and Sara Kehaulani Goo, “Pillow Bombs Feared on Planes: U.S. Says Al Qaeda Explosives Could Also Be Stuffed into Coats, Toys,” Washington Post (October 14, 2004), A5.
