Cloud security ecosystem
Ryan K.L. Koa; Kim-Kwang Raymond Choob a University of Waikato, Hamilton, New Zealand
b Information Assurance Research Group, School of Information Technology and Mathematical Sciences, University of South Australia, Adelaide, Australia
Cloud computing (Ko, 2010) may be the most important information technology (IT) innovation of the twenty-first century, and it is now common to see individuals and organizations using online computing services that classify themselves as “cloud services.” While cloud is becoming mainstream, several aspects of cloud security and privacy concerns are still in development or unaddressed.
1 How it all started—the story of an online bookstore
It is not clear when the term “cloud computing” was first coined (Choo, 2010). However, cloud computing started to become prevalent in 2008 on the back of the USA presidential election, and some mentioned the success of the campaigns were hinged to the scale and elasticity brought forth by cloud computing.
To most cloud industry practitioners, the concept of cloud computing started from an online book shop—Amazon.com in 2003. That year, the world was still counting its losses from the Dotcom bubble burst, and the world’s largest online bookstore was facing a critical economical decision-making problem—resource utilization versus capital investment.
Werner Vogels, then Amazon’s Chief Technology Officer (CTO), said “From experience we knew that the cost of maintaining a reliable, scalable infrastructure in a traditional multi-datacentre model could be as high as 70%, both in time and effort, and requires significant investment of intellectual capital to sustain over a longer period of time.”1
Hence, the company’s goal was “to deliver services that could reduce that cost to 30% or less.”2 In other words, Amazon was trying to grow their infrastructure while finding out a method to offload the operational costs to others. While Amazon’s servers are up 24 hours a day, 7 days a week, there are constantly ups and downs in terms of demand for the utilization of the servers, at different time zones around the world. It would be great if the “wastage” of utilization can be offloaded to some other customers who may need it. When the folks in Asia are sleeping, wouldn’t it be great that the related underutilized servers serving them can be sold for usage by the businesses in the Americas?
In the meantime, Chris Pinkham and Benjamin Black, another Amazon engineer, wrote a short paper outlining the ideas for Amazon's chief executive officer (CEO) Jeff Bezos, who liked it and followed up by asking for more details on a “virtual cloud-provisionable server.”
However, Pinkham and his wife had a baby on the way and, after talking with other people at Amazon, left to set up a satellite development office in South Africa—Amazon's first in the region—where he and some other engineers, including Christopher Brown and Wiljem Van Biljon, worked on designing the Amazon EC2 service.
In 2006, the cloud services for computing (EC2), storage (S3), and outsourcing of tasks only achievable by humans (Mechanical Turk) were launched. The rest, as they say, is history.
Since that movement, several IT companies have “embraced” cloud computing. Google positioned themselves as a public cloud service provider. Microsoft quickly joined the fray by offering its Azure services. Startups such as Foursquare, DropBox, Quora, and many young IT companies were started quickly over the Amazon cloud services—without the need to invest in hardware up front.
Even the large IT companies (such as Oracle and SAP) that initially dismissed cloud computing as a “buzzword” has come to accept its business model and have entered the market to offer what is known as a “hybrid cloud.” This brings us to the next and very necessary section (Section 2).
2 Consolidation of terminologies and perspectives
As with many IT paradigms, cloud computing has its fair share of overlapping terminologies. If you are coming into this field as a professional or a student in the recent year(s), you would be heartened to know that the concept of cloud computing has consolidated to the following perspectives.
2.1 Perspective 1: essential characteristics
Essentially, cloud computing offers the following characteristics as defined by NIST (NIST, 2011):
• On-demand self-service: Consumers are able to help themselves and decide which services to subscribe to, and how much to invest—all at the swipe of a credit card or using an online payment system. An IT department can now quickly purchase more resources on-demand to cater to sudden spikes in user load.
• Ubiquitous network access: Cloud services hinge on the Internet’s infrastructure, and as such provide a ubiquitous availability of services as long as there is an Internet connection. An USA-based executive can perform his roles during business travel, accessing his company’s online resources hosted in Ireland via the Internet connection in Singapore.
• Resource pooling: The combined computational power of large amounts of physical and virtual servers provides a cost-effective pooling of resources. Multitenancy solutions have enabled several organizations to share the same cloud computing resources without worrying about data spilling into each other’s logical boundaries.
• Rapid elasticity: Cloud services leverage on technologies such as server and storage virtualization to rapidly meet the rise and fall of user load and service demand. A newly launched business expecting 10,000 customers will be able to handle an unexpected load of 1 million customers without worrying about the need to purchase or set up new servers in short notice. Elasticity also improves the utilization of the cloud resources.
• Measured service with pay-per-use: Given the above characteristics, it works for both service providers and consumers to have an easy-to-measure payment scheme mimicking the power utilities and cable television model—pay-per-use. At the appropriate price point, pay-per-use has the potential to alleviate the need for forecasting and planning of resources, and reduce wastage of overheads.
The eagle-eyed reader will observe that the above five points do not point to a new technology paradigm, but an Internet-empowered, high-utilization business concept that simply works.
It replaces the awkwardness of predecessor technologies, such as utility computing and grid computing, as it comes with an easy-to-implement and easy-to-understand business and revenue model. Cloud also reduces the expectations on businesses to forecast demand correctly—which like weather forecasting, is rarely achieved successfully.
Currently, most stakeholders reference the NIST Definition of Cloud Computing (NIST, 2011). Recently, ISO/IEC 17788 (Information technology—Cloud computing—Overview and vocabulary) started defining the cloud computing definitions, but the uptake of the fresh set of definitions remains to be seen.
2.2 Perspective 2: layers and scope
With the characteristics, many cloud services are often categories by their “layers” (NIST, 2011):
• Applications of Software-as-a-Service (SaaS): Highly scalable software services such as e-mail software, accounting software, software engineering and deployment tools, and Web site creation tools. Examples include Outlook.com, Gmail, Salesforce.com, etc.
• Applications of Platform-as-a-Service (PaaS): Elastic provision of integrated cross-platform software such as combinations of databases, software development environments with operating systems. An example would be Microsoft Azure.
• Applications of Infrastructure-as-a-Service (IaaS): Elastic provision of computation (servers) and storage. An example would be Amazon Web Services’ EC2.
This method of layering and naming has also given rise to the popularity of using “as-a-service” to describe cloud-delivered services, for example, security-as-a-service (SecaaS), which will be covered in Chapter 9.
Another way to look at cloud services would be to look at the scope. If a particular cloud service is run entirely on-premise, and within your own organization’s physical boundaries, it is generally known as the private cloud (note: some vendors may have varying understandings depending on their sales pitch). If it is run entirely outside of your organization’s physical boundaries, it will be generally referred to as a public cloud. If it is a mix of both public and private cloud, it is commonly referred to as a hybrid cloud.
At the time of writing, the hybrid cloud approach is the most common approach by both vendors and consumers mainly due to data sovereignty and data governance considerations. Roles of the cloud, such as the role of a so-called “cloud broker,” are still under much debate and have not witnessed consolidation. Hence, it is not the interest of this book to discuss this, and we take a simple approach—cloud vendors/service providers versus cloud consumers/users.
It is important to note that regardless of public, private, or hybrid boundaries, the service consumer technically provides the data and mostly owns the data. However, that may change when they upload their data into the respective cloud services. For example, in some free social media sites, the copyright of user-uploaded pictures technically belongs to the social media site after the upload. Important issues such as legal implications for cloud service providers and users if the data is breached or users suffer an economic loss resulting from the provider’s negligent act have also remained unanswered (Choo, 2014a, 2014b).
There will always be some percentage of a loss of control over how their data are managed or processed. In other words, we always have to depend on a trusted administrator or provider to handle the processing of our data.
This brings us to the crux of what this book is about—the complications caused by the dependency of a trust relationship between a service provider and a service consumer.
3 The achilles’ heel—depending on a trust relationship
The root of the perennial cloud security and privacy problem stems from the basis of a trust relationship.
By signing up for the use of a cloud service—whether it is private, public, or hybrid—we are explicitly placing our trust into the people running the services to observe the highest ethical principles. This may not always be the case.
3.1 Case study 1: breach of trust by a public cloud system administrator
In 2010, Google fired its site reliability engineer, David Berksdale, for breaking Google’s internal privacy policies (Chen, 2010). Berksdale was found to have misused his position to break into the Google’s cloud e-mail service (Gmail) and Internet phone service (Google Voice) accounts of several children. Particularly, he spied on four teenagers for months before the company was notified of the abuses. Some of the abuses include the accessing of contact lists and chat transcripts. Notice that Google did not know about these abuses, and reportedly “it was unclear how widespread Barksdale’s abuses were” (Chen, 2010).
In one of the incidents in Spring 2010, Barksdale tapped into the call logs of a 15-year-old boy’s Google Voice after the boy refused to tell him the name of his new girlfriend. After accessing the boy’s account to retrieve her name and phone number, Barksdale taunted the boy and threatened to call her.
These incidents not only highlight the dangers of “trusting” a third party but also reveal the lack of technical solutions, legal guidelines, and business management controls for preventing and identifying the risks. We also cannot be assured that there will not be other “Berksdales” in other cloud providers.
This book attempts to highlight, discuss, and address these types of issues in Chapters 2–4.
3.2 Case study 2: liability of a liquidated cloud business
In 2011, storage cloud company Iron Mountain announced its liquidation, shocking several of its customers. In a statement released by Gartner in 20113:
On 8 April 2011, Iron Mountain confirmed that it is sunsetting its public cloud storage business. The company said that the official end date for the service would be “no sooner than the first half of 2013,” but said it stopped accepting any new customers as of 1 April 2011. Iron Mountain says it will continue to offer services to its current cloud storage customers, help them migrate to another provider or return the data. Virtual File Store customers that stay with Iron Mountain will be transferred to a higher-value offering, File System Archiving (FSA) in 2012. The new offering will be a hybrid that leverages policy-based archiving on site and in the cloud with indexing and classification capabilities. Archive Service Platform customers have no migration path and are being terminated or moved to an alternative service provider.
Many consumers who entrusted their data into Iron Mountain’s storage servers have not previously planned alternative storage. This case also raised the awareness that even large cloud service providers can fold, and consumers should never take their availability for granted. What if public cloud giants such as Google, Amazon, or Microsoft fold? What will happen to the customers’ massive amounts of data and our cloud-dependent lives?
If a company liquidates, what happens to the data stored in the cloud? Who can be held accountable for the state of affairs? What powers do cloud consumers have? These are the questions we will further explore in this book.
3.3 Gatekeepers—governments versus technology creators
In 2011, at the University of the West of England (UWE) in Bristol, UK, Ko attended an interesting symposium which placed legal professionals and computer scientists in the same room—to discuss about the upcoming technical and legal challenges of cloud computing.
At the symposium, the concept of the two “gatekeepers” of technology was proposed—technology creators and the governments. Due to its high concentration of high-tech startups and companies, many view Silicon Valley as the gatekeeper of sorts for several technological advances.
Why was this raised? This is because when one understands the gatekeepers’ concept, we understand the state of the art of our cloud security ecosystem. At the time of writing, the technology creator gatekeepers are currently almost exhausting their capabilities to push the security agenda. Further, Choo (2014a,b) noted that a legitimate need exists for cooperation between the different gatekeepers, but there are also legitimate concerns about cloud service providers being compelled to scan or hand over user data of interest that reside in the cloud or to report on/monitor particular types of transactional data to government agencies without the user’s knowledge or consent due to territorial jurisdiction by a foreign government. In addition, overseas cloud service providers might not be legally obliged to notify cloud users (i.e., the data owners) about such requests.
It is now time for the legal echelons and governments in the international community to take lead. For example, we are starting to see the gradual release of international standards and criteria for cloud security, and development of certified cloud security professionals (CCSP).
Most recently, we witnessed the launch of a new professional certification—the (ISC)2-CSA CCSP (which Ko is one of the pioneer group of subject matter experts developing the curriculum and exam).
4 Top threats and vulnerabilities of cloud security
Given the above scenarios and context, it is timely to cover some of the top threats and vulnerabilities of cloud computing security. Understanding the top threats in this chapter sets the scene for all readers when they approach the remaining chapters.
4.1 Cloud security alliance’s top threats to cloud computing research
In 2009 and 2010, the Cloud Security Alliance (CSA) published two relevant publications, namely, (1) Security Guidance for Critical Areas of Focus in Cloud Computing v2.16 (Cloud Security Alliance, 2009) and (2) Top Threats to Cloud Computing (Cloud Security Alliance, 2010). In the Top Threats article, seven threats were listed as the top threats to cloud computing (Table 1).
Table 1
Overview of CSA Top Threats to Cloud Computing v1.0 (Cloud Security Alliance. 2010)
| No. | CSA Top Threat |
| 1 | Abuse and nefarious use of cloud computing |
| 2 | Insecure interfaces and APIs |
| 3 | Malicious insiders |
| 4 | Shared technology issues |
| 5 | Data loss or leakage |
| 6 | Account or service hijacking |
| 7 | Unknown risk profile |
The CSA list is seminal in cloud security as it brought much-needed awareness to the flip side of cloud computing in 2009. For example, because of the low price and availability of cloud services, it is easy for a malicious attacker to use the cloud for nefarious uses. Some news articles have mentioned about the use of cheap cloud servers to crack Wi-Fi access points’ passwords via sheer brute force.4
It is also interesting to note that all threats have elements of technical, legal, and management aspects involved. The focus has always been on the technologies but this view has to broaden to take a holistic ecosystem view for true risk management. It is not surprising and cyber security is no longer the preserve of any single country, entity, (industry) sector, or disciplinary field because of the nature and extent of an increasingly connected and sophisticated technological and user bases (Choo, 2014a,b). There is, therefore, a need to bring together perspectives and approaches from different disciplines and countries and investigate what we can do singularly and collaboratively to secure our cyber space and future.
However, while these pioneering CSA documents raised the awareness of the threats, the documents depended on initial expert opinion but were unable to gather ample empirical support for the justification of the top threats—which is extremely difficult to achieve without participation from all stakeholders. Empirical data enable the research and practitioner industry to focus on addressing the “true” reported top threats. While the Top Threats report highlighted the potential risks cloud users and service providers face, debates about whether opinion-based lists such as the CSA top threats (and the latest version—the so-called Notorious Nine) stand to hold against the test of time.
For example, the CSA top threat “Shared technology issues” highlights the potential for a company A to look into company B’s data while sharing the same cloud technologies via multitenancy software controls. At the time of writing, it is a common view among the cloud security research and practitioner communities that this is a relatively remote risk, and this has been the subject of various research initiatives.
4.2 Statistics of common vulnerabilities faced by cloud service providers
This calls for the need for empirical data to study the “real” situation. Given cloud computing is still in its early stages, and the general reluctance for companies to release public data on cloud security-related outages, it is very difficult to achieve full empirical analysis on the top threats and vulnerabilities of cloud security.
The closest empirical study was perhaps the 2013 study conducted by Ko et al. (2012, 2013) of the Cyber Security Researchers of Waikato (CROW) at the University of Waikato in New Zealand, and Nanyang Technological University and Cloud Security Alliance’s Asia Pacific region in Singapore. This study looked at 11,491 news articles on cloud computing-related outages from 39 news sources (e.g., CNet, TechTarget, CNN, etc.) between January 2008 and February 2012—effectively covering the “first 5 years” of cloud computing’s boom in a best effort fashion. Through a strict definition and qualification process for what constitutes a “cloud outage” incident, 172 unique incidents were identified from the overlapping, duplicated news articles (note: this also shows the state of today’s news dissemination). While it does not necessarily cover the entire cloud security ecosystem, it is the “best one can get” given the nature of security incident disclosures.
Of the 172 reported cloud vulnerability incidents, 129 (75%) declared the cause(s) while 43 (25%) incidents did not. It was observed that the top three cloud providers, Amazon, Google, and Microsoft, account for about 56% of all nontransparent incidents of cloud vulnerability. It was also reported that beginning in 2010, cloud providers became more transparent with their reports of cloud vulnerability incidents, most likely because Amazon became more open about the causes of their incidents. As is to be expected with the growth of cloud vulnerability, over the years, the number of cloud vulnerability incidents has risen (see Figure 1). In fact from 2009 to 2011, the number of cloud vulnerability incidents more than doubled—from 33 to 71, most likely due to the phenomenal growth in cloud services.
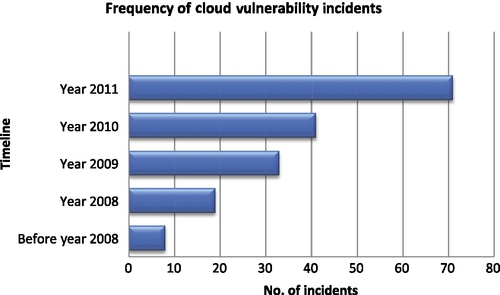
The statistics collected from actual news reports not only validated CSA’s top threat categories but also empirically revealed five newly discovered categories of vulnerabilities in cloud security. Five new threat categories (T8—Hardware Failure, T9—Natural Disasters, T10—Closure of Cloud Service, T11—Cloud-Related Malware, and T12—Inadequate Infrastructure Design and Planning) are needed for a more accurate representation of cloud outage threats and vulnerabilities. The new CSA revised threat list encompassing reported outages is listed in Table 2.
Table 2
Vulnerability Classification Derived from Reported Cloud Outages
| No. | Top Cloud Vulnerability Classification Based on Outages Reported in the News (2008–2011) |
| T1 | Abuse and Nefarious Use of Cloud Computing |
| T2 | Insecure Interfaces and APIs |
| T3 | Malicious Insiders |
| T4 | Shared Technology Issues |
| T5 | Data Loss or Leakage |
| T6 | Account or Service Hijacking |
| T7 | Unknown Risk Profile |
| T8 | Hardware Failure |
| T9 | Natural Disasters |
| T10 | Closure of Cloud Service |
| T11 | Cloud-Related Malware |
| T12 | Inadequate Infrastructure Design and Planning |
Figure 2 shows the frequency of occurrence of the existing seven CSA threats and five new threats proposed by the authors of the vulnerability statistics report. The three most frequent incidents are (Ko et al., 2012, 2013):
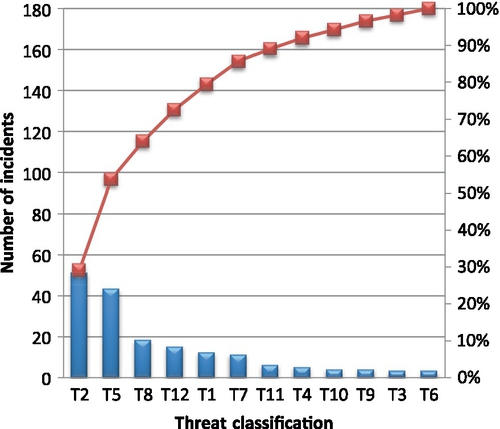
– CSA Threat 2 “Insecure Interfaces & APIs” with 51 incidents accounting for 29% of all threats;
– CSA Threat 5 “Data Loss & Leakage” with 43 incidents accounting for 25% of all threats reported;
– CSA Threat 8 “Hardware Failure” with 18 incidents accounts for 10% of all threats reported.
All other threats have 15 or fewer cloud vulnerability incidents each, accounting for 8.5% or less. A Pareto analysis reveals that the first three threats, CSA Threat 2, CSA Threat 5, and New Threat 8, account for 64% of all cloud vulnerability incidents, although collectively they make up only 25% of total threats (see Figure 2).
This study also reported that most vulnerabilities (except two, namely, Insecure Interfaces & APIs and Data Loss or Leakage) are decreasing by the year, showing an improvement and stability of cloud computing services. However, the top three culprits (Insecure Interfaces & APIs, Data Loss or Leakage, Hardware Failure) form about 60% of the incidents! If we can reduce them, the cloud security ecosystem will definitely be very reliable. The study also shows there are still lots of room for accountability to the users. Prominent cloud service providers with large market shares have to take the lead and show increased transparency.
It is our hope that readers and organizations using the cloud or developing cloud services take note of these top risks, so that they can identify and manage them in advance of a catastrophic event. This leads us to Section 5.
5 Managing cloud security risks with the deming cycle
One way to manage the risks well is to adopt the Plan-Do-Check-Act (or Plan-Do-Check-Adjust) (PDCA) cycle, also known as the Deming Cycle as it was proposed by Dr. W. Edwards Deming. The Deming Cycle mimics the rigorous scientific method without being tied to the different departmental constraints of an organization. This is also the reason why we chose to structure our book according to the Deming Cycle—to integrate the technical, legal, and management aspects of the cloud security ecosystem.
No one can expect full security, but one can expect high assurance from doing their due diligence with the breadth and depth of a full Deming Cycle implementation.
The Deming Cycle has been adopted by the best practices in the security field, including the ISO/IEC 27001 standard, which recommends the PDCA cycles for every institution’s Information Security Management System (ISMS)—a thorough set of policies concerned with information security management or IT-related risks, primarily found in the ISO 27000 series of standards.
In the context of the cloud security ecosystem, let us dive into the details of each step in the following sections.
6 Plan—threats, risk, and requirements landscape
This book is divided into four main parts, guided by the PDCA stages. We have chosen to organize the technical, business, and legal aspects of cloud security into these stages to remove the current siloed view of the cloud. It is our hope that the PDCA approach extends into the multidisciplinary field of cloud security.
Part 1 of this book focuses on providing an overview of the threats, risks, and requirements landscape in the global cloud computing industry.
Chapter 2 introduces us to the cyber crime landscape in two Asian economical superpowers—Singapore and Hong Kong. The factors shaping the response to these criminal threats are also discussed.
Chapter 3 introduces taxonomies of the cloud attacks and provides an insight into the threat vectors, targets, actors, countermeasures, and the impact of the attacks. After which, this chapter introduces a conceptual risk assessment framework and describes an example scenario of a distributed denial of service and account hijacking (one of the top threats of cloud computing mentioned earlier).
Chapter 4 introduces the Multitiered Cloud Security Model (MTCS), a world-leading government-led cloud service provider evaluation model implemented by the Singapore government as a standard SS 584. The SS 584 is the world’s first cloud security standard that covers multiple tiers and can be applied by cloud service providers to meet differing cloud user needs for data sensitivity and business criticality. The model has three tiers ordered by data sensitivity and criticality. Tier 1 is designed for nonbusiness critical data and system, with baseline security controls to address security risks and threats in potentially low-impact information systems using cloud services (e.g., Web sites hosting public information). Tier 2 is for organizations running business critical data and systems through a set of more stringent security controls to address security risks and threats in potentially moderate impact information systems using cloud services to protect business and personal information (e.g., Confidential business data, e-mail, CRM—customer relation management systems). Tier 3 is designed for regulated organizations with specific requirements and more stringent security requirements. Industry-specific regulations may be applied in addition to these controls to supplement and address security risks and threats in high impact information systems using cloud services (e.g., highly confidential business data, financial records, medical records).
7 Do—cloud security approaches and challenges
After understanding the Plan stage of the Cloud Ecosystem, it is key to understand the current and emerging technologies to uphold the security and privacy of cloud consumers and service providers. The trust relationship discussed in Section 3 is neither sustainable nor long term. This calls for novel techniques which will empower better security and privacy for data owners in the cloud, covered in Part 2 of this book.
Chapter 5 presents an introduction to a much-talked about, but seldom understood holy grail of cloud security—homomorphic encryption. Intentionally written in plain English and with easy-to-follow examples, it provides an overview of the partial and fully homomorphic encryption techniques and discusses the open issues surrounding this area of cloud security.
Chapter 6 looks at the general pitfalls and advantages of protection via isolation techniques. The chapter introduces the isolation techniques in virtualization hypervisors and networking architectures, and provides an in-depth overview of the known attacks and protection strategies.
Chapter 7 then takes a legal perspective on the protection of digital identity in the cloud. It highlights the difficulties of identity protection given the nature of cloud computing handling cross-border data. The chapter also discusses the strategies recommended for the uphill task of protecting the digital identity in the era of cloud computing.
On the topic of cross-border data, Chapter 8 looks at another key question commonly asked of cloud data—provenance or “what has happened to the cloud data?” The chapter discusses about the use of provenance for data accountability and the challenges of conducting provenance reconstruction from environments which lack prior provenance tracking. A provenance-based model for cloud data accountability is also introduced in this chapter.
Chapter 9 covers the emerging security deliver model—Security-as-a-Service (SecaaS). It addresses the current lack of review of the SecaaS industry and identifies gaps after the SecaaS categories are classified. Chapter 10 talks about the technical, legal, and management issues of secure migration to and from the cloud.
Chapter 11 introduces readers to another emerging security challenge related to the cloud—the Internet of Things. Chapter 12 talks about knowledge management concepts to manage the scalability and privacy of business networks, while leveraging the capabilities of the cloud.
Chapter 13 takes a unique technical aspect—the utilization of psychological and communication theories to promote safer cloud security behaviors. Humans are always seen as the weakest links to an organization, and readers can learn from the communication theories and related psychological theories toward enhancing safer security behaviors.
8 Check—forensics and incident response
Malicious cybe activities are no longer a matter of if but of when (Quick et al., 2014), and when such an incident is detected, we need to be able to respond and investigate—the focus of Part 3.
Chapter 14 presents an evidence collection and analysis methodology for Android devices. Chapter 15 demonstrates the utility of the methodology using seven popular Android apps (i.e., Dropbox, OneDrive, Box, ownCloud, Evernote, OneNote, and Universal Password Manger) as a case study. Various information were recovered and using the information obtained, the investigators could access the cloud service’s servers as the user (and access their files) on the device for five of the six apps examined that communicated and authenticated with their servers. Similarly, findings from the forensic investigations undertaken in Chapters 16 and 19 contribute to an up-to-date understanding of cloud data artifacts that could be recovered from mobile and other computing devices.
Chapter 17 introduces a conceptual cloud incident handling model by integrating digital forensic practices in cloud incident handling and presents a case study implementation using the open-source OwnCloud solution.
Using a higher education organization as a case study, Chapter 18 reviews the cloud security and forensic readiness of the IaaS provider. Findings from the case study echoed several of the concerns identified in this and other chapters such as a lack of clarity with regard to the requirements for specific IaaS security, digital evidence collection, and digital investigation.
9 Act—governance and auditing
Part 4 focuses on long-term actions and adjustments for higher security postures of the cloud.
It starts from an IT auditor’s point of view, with Chapter 20 introducing the steps for planning, scoping and executing the auditing of cloud service providers. Chapter 21 introduces a computational trust method for quantifying security capabilities, so that capabilities can be effectively communicated.
Chapter 22 introduces a tool-based risk assessment of cloud infrastructures as social-technical systems, using model-based, attack-based, and combined techniques.
10 Summary
Cloud computing challenges the concept of boundaries. It is common for a consumer to use a cloud e-mail service offered by a company located in country A, while this service runs on infrastructure hosted by another company at country B located in another continent. Our vision is that cloud service providers should be data processors and not data owners (Ko et al., 2011).
This is the beginning of a new era where computing is increasingly expected to be hosted on the cloud. Hence, to embark on this book, we invited several experts in their own fields to contribute the several aspects of this. As expected by security professionals, we have organized our chapters into a Plan-Do-Check-Act cycle. We hope that you will enjoy reading the rest of this book. One thing for sure, the cloud is here to stay, and it is to our best interest that we secure it.
