2.3 The Vigenère Cipher
A variation of the shift cipher was invented back in the sixteenth century. It is often attributed to Vigenère, though Vigenère’s encryption methods were more sophisticated. Well into the twentieth century, this cryptosystem was thought by many to be secure, though Babbage and Kasiski had shown how to attack it during the nineteenth century. In the 1920s, Friedman developed additional methods for breaking this and related ciphers.
The key for the encryption is a vector, chosen as follows. First choose a key length, for example, 6. Then choose a vector of this size whose entries are integers from 0 to 25, for example . Often the key corresponds to a word that is easily remembered. In our case, the word is vector. The security of the system depends on the fact that neither the keyword nor its length is known.
To encrypt the message using the in our example, we take first the letter of the plaintext and shift by 21. Then shift the second letter by 4, the third by 2, and so on. Once we get to the end of the key, we start back at its first entry, so the seventh letter is shifted by 21, the eighth letter by 4, etc. Here is a diagram of the encryption process.
A known plaintext attack will succeed if enough characters are known since the key is simply obtained by subtracting the plaintext from the ciphertext mod 26. A chosen plaintext attack using the plaintext will yield the key immediately, while a chosen ciphertext attack with yields the negative of the key. But suppose you have only the ciphertext. It was long thought that the method was secure against a ciphertext-only attack. However, it is easy to find the key in this case, too.
The cryptanalysis uses the fact that in most English texts the frequencies of letters are not equal. For example, occurs much more frequently than . These frequencies have been tabulated in [Beker-Piper] and are provided in Table 2.1.
Table 2.1 Frequencies of Letters in English
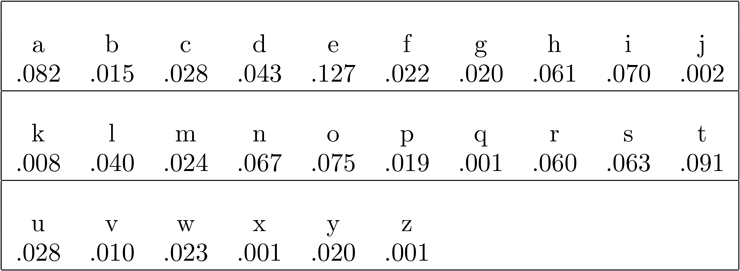
Of course, variations can occur, though usually it takes a certain amount of effort to produce them. There is a book Gadsby by Ernest Vincent Wright that does not contain the letter . Even more impressive is the book La Disparition by George Perec, written in French, which also does not have a single (not only are there the usual problems with verbs, etc., but almost all feminine nouns and adjectives must be avoided). There is an English translation by Gilbert Adair, A Void, which also does not contain . But generally we can assume that the above gives a rough estimate of what usually happens, as long as we have several hundred characters of text.
If we had a simple shift cipher, then the letter , for example, would always appear as a certain ciphertext letter, which would then have the same frequency as that of in the original text. Therefore, a frequency analysis would probably reveal the key. However, in the preceding example of a Vigenère cipher, the letter appears as both and . If we had used a longer plaintext, would probably have been encrypted as each of , , , , , and , corresponding to the shifts 21, 4, 2, 19, 14, 17. But the occurrences of in a ciphertext might not come only from . The letter is also encrypted to when its position in the text is such that it is shifted by 4. Similarly, , , , and can contribute to the ciphertext, so the frequency of is a combination of that of , , , , , and from the plaintext. Therefore, it appears to be much more difficult to deduce anything from a frequency count. In fact, the frequency counts are usually smoothed out and are much closer to 1/26 for each letter of ciphertext. At least, they should be much closer than the original distribution for English letters.
Here is a more substantial example. This example is also treated in Example 4 in the Computer Appendices. The ciphertext is the following:
VVHQWVVRHMUSGJGTHKIHTSSEJCHLSFCBGVWCRLRYQTFSVGAHW KCUHWAUGLQHNSLRLJSHBLTSPISPRDXLJSVEEGHLQWKASSKUWE PWQTWVSPGOELKCQYFNSVWLJSNIQKGNRGYBWLWGOVIOKHKAZKQ KXZGYHCECMEIUJOQKWFWVEFQHKIJRCLRLKBIENQFRJLJSDHGR HLSFQTWLAUQRHWDMWLGUSGIKKFLRYVCWVSPGPMLKASSJVOQXE GGVEYGGZMLJCXXLJSVPAIVWIKVRDRYGFRJLJSLVEGGVEYGGEI APUUISFPBTGNWWMUCZRVTWGLRWUGUMNCZVILE
The frequencies are as follows:
| A | B | C | D | E | F | G | H | I | J | K | L | M |
| 8 | 5 | 12 | 4 | 15 | 10 | 27 | 16 | 13 | 14 | 17 | 25 | 7 |
| N | O | P | Q | R | S | T | U | V | W | X | Y | Z |
| 7 | 5 | 9 | 14 | 17 | 24 | 8 | 12 | 22 | 22 | 5 | 8 | 5 |
Note that there is no letter whose frequency is significantly larger than the others. As discussed previously, this is because , for example, gets spread among several letters during the encryption process.
How do we decrypt the message? There are two steps: finding the key length and finding the key. In the following, we’ll first show how to find the key length and then give one way to find the key. After an explanation of why the method for finding the key works, we give an alternative way to find the key.
2.3.1 Finding the Key Length
Write the ciphertext on a long strip of paper, and again on another long strip. Put one strip above the other, but displaced by a certain number of places (the potential key length). For example, for a displacement of two we have the following:
| V | V | H | Q | W | V | V | R | H | M | U | S | G | J | G | ||
| V | V | H | Q | W | V | V | R | H | M | U | S | G | J | G | T | H |
| * | ||||||||||||||||
| T | H | K | I | H | T | S | S | E | J | C | H | L | S | F | C | B |
| K | I | H | T | S | S | E | J | C | H | L | S | F | C | B | G | V |
| * | ||||||||||||||||
| G | V | W | C | R | L | R | Y | Q | T | F | S | V | G | A | H | |
| W | C | R | L | R | Y | Q | T | F | S | V | G | A | H | W | K | |
| * |
Mark a each time a letter and the one below it are the same, and count the total number of coincidences. In the text just listed, we have two coincidences so far. If we had continued for the entire ciphertext, we would have counted 14 of them. If we do this for different displacements, we obtain the following data:
| displacement: | 1 | 2 | 3 | 4 | 5 | 6 |
| coincidences: | 14 | 14 | 16 | 14 | 24 | 12 |
We have the most coincidences for a shift of 5. As we explain later, this is the best guess for the length of the key. This method works very quickly, even without a computer, and usually yields the key length.
2.3.2 Finding the Key: First Method
Now suppose we have determined the key length to be 5, as in our example. Look at the 1st, 6th, 11th, ... letters and see which letter occurs most frequently. We obtain
| A | B | C | D | E | F | G | H | I | J | K | L | M |
| 0 | 0 | 7 | 1 | 1 | 2 | 9 | 0 | 1 | 8 | 8 | 0 | 0 |
| N | O | P | Q | R | S | T | U | V | W | X | Y | Z |
| 3 | 0 | 4 | 5 | 2 | 0 | 3 | 6 | 5 | 1 | 0 | 1 | 0 |
The most frequent is , though are close behind. However, would mean a shift of 5, hence . But this would yield an unusually high frequency for in the plaintext. Similarly, would mean and , both of which have too high frequencies. Finally, would require , which is unlikely to be the case. Therefore, we decide that and the first element of the key is .
We now look at the 2nd, 7th, 12th, ... letters. We find that occurs 10 times and occurs 12 times, and the other letters are far behind. If , then , which should not occur 12 times in the plaintext. Therefore, and the second element of the key is .
Now look at the 3rd, 8th, 13th, ... letters. The frequencies are
| A | B | C | D | E | F | G | H | I | J | K | L | M |
| 0 | 1 | 0 | 3 | 3 | 1 | 3 | 5 | 1 | 0 | 4 | 10 | 0 |
| N | O | P | Q | R | S | T | U | V | W | X | Y | Z |
| 2 | 1 | 2 | 3 | 5 | 3 | 0 | 2 | 8 | 7 | 1 | 0 | 1 |
The initial guess that runs into problems; for example, and have too high frequency and has too low. Similarly, and do not seem likely. The best choice is and therefore the third key element is .
The 4th, 9th, 14th, ... letters yield as the fourth element of the key. Finally, the 5th, 10th, 15th, ... letters yield as the final key element. Our guess for the key is therefore
As we saw in the case of the 3rd, 8th, 13th, ... letters (this also happened in the 5th, 10th, 15th, ... case), if we take every fifth letter we have a much smaller sample of letters on which we are doing a frequency count. Another letter can overtake in a short sample. But it is probable that most of the high-frequency letters appear with high frequencies, and most of the low-frequency ones appear with low frequencies. As in the present case, this is usually sufficient to identify the corresponding entry in the key.
Once a potential key is found, test it by using it to decrypt. It should be easy to tell whether it is correct.
In our example, the key is conjectured to be . If we decrypt the ciphertext using this key, we obtain
themethodusedforthepreparationandreadingofcodemessagesis
simpleintheextremeandatthesametimeimpossibleoftranslatio
nunlessthekeyisknowntheeasewithwhichthekeymaybechangedis
anotherpointinfavoroftheadoptionofthiscodebythosedesirin
gtotransmitimportantmessageswithouttheslightestdangeroft
heirmessagesbeingreadbypoliticalorbusinessrivalsetc
This passage is taken from a short article in Scientific American, Supplement LXXXIII (January 27, 1917), page 61. A short explanation of the Vigenère cipher is given, and the preceding passage expresses an opinion as to its security.
Before proceeding to a second method for finding the key, we give an explanation of why the procedure given earlier finds the key length. In order to avoid confusion, we note that when we use the word “shift” for a letter, we are referring to what happens during the Vigenère encryption process.
We also will be shifting elements in vectors. However, when we slide one strip of paper to the right or left relative to the other strip, we use the word “displacement.”
Put the frequencies of English letters into a vector:
Let be the result of shifting by spaces to the right. For example,
The dot product of with itself is
Of course, is also equal to .066 since we get the same sum of products, starting with a different term. However, the dot products of are much lower when , ranging from .031 to .045:
| 0 | 1 | 2 | 3 | 4 | 5 | 6 | |
| .066 | .039 | .032 | .034 | .044 | .033 | .036 | |
| 7 | 8 | 9 | 10 | 11 | 12 | 13 | |
| .039 | .034 | .034 | .038 | .045 | .039 | .042 |
The dot product depends only on . This can be seen as follows. The entries in the vectors are the same as those in , but shifted. In the dot product, the th entry of is multiplied by the th entry, the st times the st, etc. So each element is multiplied by the element positions removed from it. Therefore, the dot product depends only on the difference . However, by reversing the roles of and , and noting that , we see that and give the same dot products, so the dot product only depends on . In the preceding table, we only needed to compute up to . For example, corresponds to a shift by 17 in one direction, or 9 in the other direction, so will give the same dot product.
The reason is higher than the other dot products is that the large numbers in the vectors are paired with large numbers and the small ones are paired with small. In the other dot products, the large numbers are paired somewhat randomly with other numbers. This lessens their effect. For another reason that is higher than the other dot products, see Exercise 23.
Let’s assume that the distribution of letters in the plaintext closely matches that of English, as expressed by the vector above. Look at a random letter in the top strip of ciphertext. It corresponds to a random letter of English shifted by some amount (corresponding to an element of the key). The letter below it corresponds to a random letter of English shifted by some amount .
For concreteness, let’s suppose that and . The probability that the letter in the 50th position, for example, is is given by the first entry in , namely .082. The letter directly below, on the second strip, has been shifted from the original plaintext by positions. If this ciphertext letter is , then the corresponding plaintext letter was , which occurs in the plaintext with probability .020. Note that .020 is the first entry of the vector . The probability that the letter in the 50th position on the first strip and the letter directly below it are both the letter is . Similarly, the probability that both letters are is . Working all the way through , we see that the probability that the two letters are the same is
In general, when the encryption shifts are and , the probability that the two letters are the same is . When , this is approximately , but if , then the dot product is .
We are in the situation where exactly when the letters lying one above the other have been shifted by the same amount during the encryption process, namely when the top strip is displaced by an amount equal to the key length (or a multiple of the key length). Therefore we expect more coincidences in this case.
For a displacement of 5 in the preceding ciphertext, we had 326 comparisons and 24 coincidences. By the reasoning just given, we should expect approximately coincidences, which is close to the actual value.
2.3.3 Finding the Key: Second Method
Using the preceding ideas, we give another method for determining the key. It seems to work somewhat better than the first method on short samples, though it requires a little more calculation.
We’ll continue to work with the preceding example. To find the first element of the key, count the occurrences of the letters in the 1st, 6th, 11th, ... positions, as before, and put them in a vector:
(the first entry gives the number of occurrences of , the second gives the number of occurrences of , etc.). If we divide by 67, which is the total number of letters counted, we obtain a vector
Let’s think about where this vector comes from. Since we know the key length is 5, the 1st, 6th, 11th, ... letters in the ciphertext were all shifted by the same amount (as we’ll see shortly, they were all shifted by 2). Therefore, they represent a random sample of English letters, all shifted by the same amount. Their frequencies, which are given by the vector should approximate the vector where is the shift caused by the first element of the key.
The problem now is to determine . Recall that is largest when , and that W approximates . If we compute for , the maximum value should occur when . Here are the dot products:
The largest value is the third, namely .0713, which equals . Therefore, we guess that the first shift is 2, which corresponds to the key letter .
Let’s use the same method to find the third element of the key. We calculate a new vector W, using the frequencies for the 3rd, 8th, 13th, ... letters that we tabulated previously:
The dot products for are
The largest of these values is the fourth, namely .0624, which equals . Therefore, the best guess is that the first shift is 3, which corresponds to the key letter . The other three elements of the key can be found similarly, again yielding as the key.
Notice that the largest dot product was significantly larger than the others in both cases, so we didn’t have to make several guesses to find the correct one. In this way, the present method is superior to the first method presented; however, the first method is much easier to do by hand.
Why is the present method more accurate than the first one? To obtain the largest dot product, several of the larger values in W had to match with the larger values in an In the earlier method, we tried to match only the , then looked at whether the choices for other letters were reasonable. The present method does this all in one step.
To summarize, here is the method for finding the key. Assume we already have determined that the key length is .
For to , do the following:
Compute the frequencies of the letters in positions mod , and form the vector W.
For to , compute .
Let give the maximum value of .
The key is probably .
