
Networking
Domain Objectives
• 2.1 Compare and contrast TCP and UDP ports, protocols, and their purposes
• 2.2 Compare and contrast common networking hardware devices
• 2.3 Given a scenario, install and configure a basic wired/wireless SOHO network
• 2.4 Compare and contrast wireless networking protocols
• 2.5 Summarize the properties and purposes of services provided by networked hosts
• 2.6 Explain common network configuration concepts
• 2.7 Compare and contrast Internet connection types, network types, and their features
• 2.8 Given a scenario, use appropriate networking tools

Objective 2.1 Compare and contrast TCP and UDP ports, protocols, and their purposes
The Transmission Control Protocol (TCP) and User Datagram Protocol (UDP) are two key components of a TCP/IP network. Although both are used to transport information, they differ in several important ways, as you will learn in this objective.
Ports and Protocols
Protocols handle data transfer details, such as how to pack and unpack data with protocol-specific packet formats. The most famous protocol is the Transmission Control Protocol/Internet Protocol (TCP/IP) used by most modern networks, including the Internet—though TCP/IP is technically a big group of protocols. Let’s look at a simple example.
TCP and UDP both use port numbers to identify the type of connection being used. Table 2.1-1 provides a quick reference to application protocols and the TCP port numbers they use. Table 2.1-2 provides a quick reference to utility protocols (protocols that are hidden “behind the scenes” protocols) and the TCP and UDP port numbers they use.
TABLE 2.1-1 Application Protocols
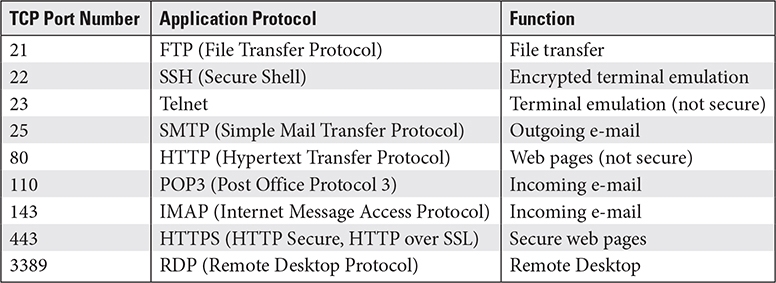
TABLE 2.1-2 Utility Protocols
TCP vs. UDP
TCP accomplishes the reliable transfer of data with communication rules that require both machines to acknowledge each other to send and receive data. Thus, TCP is referred to as a connection-oriented protocol.
UDP is much faster because it lacks these checks—which is fine if your data can tolerate some errors or the chance of errors is low. For example, speed might be more important than a few dropped packets for a Voice over IP call or video chat. Because UDP simply sends data without checking to see if it is received, it is referred to as a connectionless protocol.
When data moving between systems must arrive in good order, we use the connection-oriented Transmission Control Protocol (TCP). If it’s not a big deal for data to miss a bit or two, then the connectionless User Datagram Protocol (UDP) is the way to go. Most TCP/IP applications use TCP (that’s why we don’t call it UDP/IP) because it transfers data reliably.
REVIEW
Objective 2.1: Compare and contrast TCP and UDP ports, protocols, and their purposes
• Application protocols use TCP ports to perform functions such as file transfer, terminal emulation, web page transfers, and remote desktop connections.
• TCP ports are connection-oriented, meaning that both ends of a connection must acknowledge the connection. TCP connections are more reliable but slower than UDP connections.
• Utility protocols use primarily UDP ports, as well as some TCP ports, to perform functions such as file and directory services, folder sharing, and services discovery.
• UDP ports are connectionless, meaning that a service using UDP does not verify that the connection is working. UDP connections are faster but less reliable than TCP connections.
2.1 QUESTIONS
1. An incorrect firewall setting results in port 110 being blocked. Which of the following services will not work until the port is unblocked?
A. Secure web pages
B. Receiving POP3 e-mail
C. Remote desktop
D. Upgrading to Windows 10
2. A computer that uses automatic IP addressing relies on which of the following ports?
A. 21
B. 25
C. 143
D. 67, 68
3. All information is transmitted over the Internet in which of the following?
A. Frame
B. Archive
C. Packet
D. Zip file
4. Sometimes, for greater security, e-mail providers change the default ports used for sending and receiving e-mail. If an e-mail provider changes from port 143 to a different port, which of these services would need to be configured to use the new port?
A. POP3
B. SMTP
C. IMAP
D. HTTP
C. Zip file
5. A user reports that she can connect to normal websites (HTTP://), but not to secure websites (HTTPS://). Which port is being blocked by a firewall?
A. 80
B. 445
C. 25
D. 443
2.1 ANSWERS
1. B The default port used by POP3 to receive e-mail is 110.
2. D The ports used by the DHCP service for automatic IP addressing are 67 and 68.
3. C All Internet traffic is broken into packets that are reassembled at the destination.
4. C IMAP normally uses port 143.
5. D 443 is the port used for HTTPS (secure HTTP).

Objective 2.2 Compare and contrast common networking hardware devices
Networks are all about interconnecting computing devices (also called hosts) so they can communicate. More specifically, your local host can communicate with remote hosts in order to access the resources (such as printers, files, web pages, and so on) those systems share, and to share its own resources. In a given exchange, the system providing a resource is the server, and the system using the resource is the client; when we call an entire system a server, what we really mean is that the system’s primary job is serving some resource(s) to clients.
In order for a variety of different devices to share resources over a network, the network components need a shared connectivity standard, an addressing method clients and servers can use to find and communicate with each other, and shared software protocols that each system in an exchange understands. Let’s look at many of the concepts and components that come together to form a network.
Ethernet
The dominant shared connectivity standard on modern networks, Ethernet, defines everything needed to get data from one system to another. Ethernet has evolved through hundreds of Ethernet flavors over the years—and most modern network speeds are expressed as 10BaseT, 100BaseT (Fast Ethernet), and 1000BaseT (Gigabit Ethernet), which respectively run at 10, 100, and 1000 Mbps. Individual hosts have a network adapter that connects to a central switch with a segment of unshielded twisted pair (UTP) cable (see Figure 2.2-1), which is limited to 100 meters for most cable types.

FIGURE 2.2-1 A switch and two laptops connected by UTP cable
Cross-Reference
Routers
A router is a device that connects LANs to a WAN (see Figure 2.2-2). Hosts send signals for destinations outside of the LAN to the router, which routes traffic between networks.
FIGURE 2.2-2 Two broadcast domains connected by a router—a WAN
Switches
Switches connect hosts on a local area network (LAN) and pass signals between them. Switches memorize the MAC address of each device to smartly repeat signals to the appropriate host. A group of computers connected by one or more switches is a broadcast domain (see Figure 2.2-3).

FIGURE 2.2-3 Two broadcast domains—two separate LANs
Managed
A managed switch is a switch in which each port can be configured with different settings. For example, you can set a single managed switch to function as two or more virtual LANs (VLANs), control quality of service (QoS) settings on a per-port basis, and more.
Unmanaged
An unmanaged switch is the type of switch sold for small office/home office (SOHO) use, such as the one shown in Figure 2.2-1. It has no management features, and all devices connected to it are in the same LAN.
Hub
An Ethernet hub resembles a switch, but takes a signal from one port and blindly broadcasts it out the others. This slows down traffic, and to make matters worse, hubs subdivide the total bandwidth of the network by the number of connected devices. Take, for example, a 100Base-T (Fast Ethernet) network. Use a switch, and you get the full 100-Mbps speed to each port. Replace that switch with a hub, and if you have four devices connected, the effective speed per port is only 25 Mbps. Don’t use Ethernet hubs (USB hubs, on the other hand, are very useful.)
Cross-Reference
Access Points
An access point (AP) centrally connects wireless network nodes into a wireless LAN (WLAN) in the same way a switch connects wired devices into a LAN. Many APs also act as high-speed switches and Internet routers (see Figure 2.2-4). APs are sometimes referred to as wireless APs (WAPs).

FIGURE 2.2-4 Device that acts as access point, switch, and router (inset shows ports on back side)
Cloud-based Network Controller
A cloud-based network controller is a network appliance that enables the creation and management of a wireless mesh network, such as a private or public network in a hotel, convention center, shopping mall, or apartment complex. A typical cloud-based network controller has onboard storage for caching and uses compatible gateways and repeaters and cloud-based management software.
Firewall
Firewalls generally protect an internal network from unauthorized access to and from the Internet at large with methods such as hiding IP addresses and blocking TCP/IP ports, but firewalls at internal boundaries can also help limit the damage a compromised node can do to important resources. Hardware firewalls are often built into routers (or standalone devices), whereas software firewalls run on individual systems.
Hardware firewalls protect your LAN from outside threats by filtering packets before they reach your internal machines. You can configure a SOHO router’s firewall from the browser-based settings utility (see Figure 2.2-5). Hardware firewalls use stateful packet inspection (SPI) to inspect individual packets and block incoming traffic that isn’t a response to your network’s outgoing traffic. You can even disable ports entirely, blocking all traffic in or out.
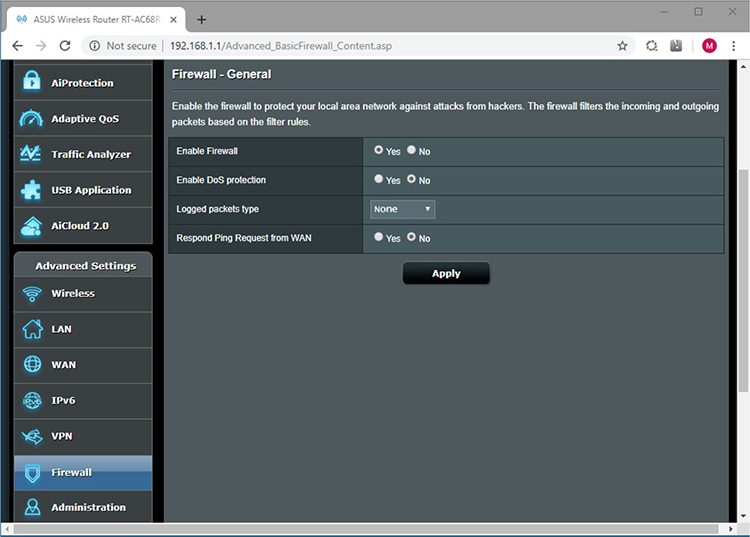
FIGURE 2.2-5 The firewall settings in an ASUS router
Network Interface Card
A network interface card (NIC) was originally an add-on card that connected a computer to an Ethernet or other wired network. Although most computers and network devices use integrated wired or wireless network connections instead of a card, the term NIC is used for both network cards and integrated network adapters. Older computers can use PCI-based NICs, while current computers can use PCIe NICs, such as the wireless NIC shown in Figure 2.2-6.

FIGURE 2.2-6 Wireless PCIe add-on NIC
If a computer needs an upgrade to a faster or more capable NIC, it’s usually easier to use a USB NIC, such as the wireless NIC shown in Figure 2.2-7. For tablets or other computers that have USB 2.0, 3.0, or 3.1 ports but no Ethernet ports, use a USB to Ethernet adapter, such as the one shown in Figure 2.2-8.

FIGURE 2.2-7 External USB wireless NIC

FIGURE 2.2-8 External USB to Ethernet adapter
Each network adapter (or NIC) has a 48-bit built-in binary media access control (MAC) address that uniquely identifies it; before a NIC sends data out, it chunks it into transmission-friendly frames (see Figure 2.2-9) that are tagged with the MAC address of the sender and recipient and include information the receiver can use to detect errors. A switch uses the MAC address to send frames to the correct host.
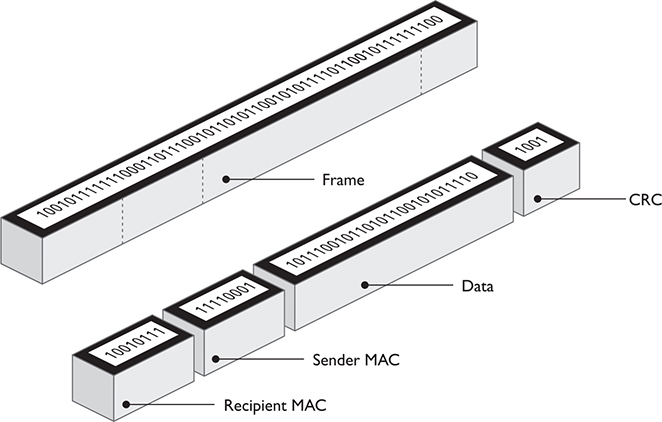
FIGURE 2.2-9 Generic frame
Repeater
To increase the range of a wireless network, you can install extra APs for devices to roam between, replace stock antennas with higher-gain versions, use a signal booster, or use wireless repeaters/extenders to receive and rebroadcast the Wi-Fi signal. Wireless mesh networks include two or more repeaters.
Cable/DSL Modem
The most common type of broadband connection for a SOHO network is either a cable modem or a DSL modem. Read on to discover the differences.
DSL Modem
A digital subscriber line (DSL) modem connects to a standard RJ-11 telephone line, enabling the conversion of high-speed digital signals to and from the telephone line. DSL modems frequently are combined with wireless routers and are referred to as DSL gateways.
DSL speeds vary widely from location to location because the greater the distance from the DSL modem to the telephone company’s central switch, the slower the performance.
Cross-Reference
Cable Modem
Cable uses regular RG-6 or RG-59 cable TV lines to provide upload speeds from 1 to 20 Mbps and download speeds from 6 Mbps to 1+ Gbps. Cable Internet connections are theoretically available anywhere you can get cable TV. The cable connects to a cable modem that itself connects (via Ethernet) to a small home router or your NIC. Some cable modems also include support for VoIP telephony, such as the one shown in Figure 2.2-10.

FIGURE 2.2-10 Cable modem with VoIP telephone support
Bridge
A bridge connects two different media types (such as UTP and fiber optic) and converts signals between them.
Patch Panel
A patch panel (shown in Figure 2.2-11) has a row of permanent connectors for horizontal cables on the back and a row of female port connectors on the front, enabling you to use short stranded-core UTP patch cables (shown in Figure 2.2-12) to connect the patch panel to the switch. Premade patch cables make it simple to get multiple colors for organization and often come with booted (reinforced) connectors.

FIGURE 2.2-11 Typical patch panels

FIGURE 2.2-12 Typical patch cable
Power over Ethernet (PoE)
Most network hardware—including APs—draw power from an electrical outlet. Advanced APs and networked devices such as security cameras can instead run on electricity supplied by a Power over Ethernet (PoE) injector or PoE switch. Both types of devices enable a standard Ethernet cable to carry power as well as signals.
Injectors
A PoE injector (also known as a midspan) is plugged into a standard Ethernet cable coming from a switch and a source of AC power. The injector adds the power to the Ethernet cable running from the injector to the PoE device.
Switch
A PoE switch detects whether connected devices are standard Ethernet devices or PoE devices. It supplies power to PoE devices, but does not supply power to standard Ethernet devices.
Ethernet over Power
An Ethernet over Power (EoP) bridge connects UTP cable to your building’s power infrastructure, enabling you to have wired connections where it would be difficult to run new cable. EoP devices are used in pairs: connect one to each end of the connection, such as one near a switch and the other near a workstation. Figure 2.2-13 illustrates a typical EoP bridge connected to an AC power outlet.

FIGURE 2.2-13 An EoP bridge plugged into an AC power outlet
REVIEW
Objective 2.2: Compare and contrast common networking hardware devices
• Network hardware devices are based on Ethernet, which is available in several speeds ranging from 10 Mbps to 1000 Mbps or more.
• A router connects a local area network (LAN) to a wide area network (WAN).
• A switch transfers data directly between the transmitting and receiving devices on the network.
• A managed switch allows each port to be configured with different settings, including different LAN settings, while an unmanaged switch has no settings. Switches have replaced hubs, which broadcast data to all devices and are much slower.
• An access point (AP) is the wireless counterpart to a switch. A wireless router typically incorporates the features of an AP and a switch.
• A cloud-based network controller enables existing wireless networks to be managed and used as a single wireless mesh network.
• A firewall is a device or app that examines network traffic and blocks unwanted traffic.
• A network interface card (NIC) enables a device to connect to a network. Many devices have built-in NICs.
• A repeater relays wireless signals to devices outside the range of the current AP or router.
• Cable and DSL modems are popular broadband Internet connection technologies. DSL can use phone lines.
• A bridge connects two different media types so they can work together.
• A patch panel is used for wired Ethernet cable connections to a single location. A patch cable is used to run patch panel wires to a switch.
• Power over Ethernet (PoE) is used to provide power to Fast Ethernet devices that need power but don’t have power at their locations. An injector is used to add power, and a PoE switch is used to provide power only to PoE devices.
• An Ethernet over Power (EoP) bridge sends Ethernet signals over power lines in a building, and EoP devices are used in pairs.
2.2 QUESTIONS
1. Company A wants to create two separate networks in a building but only wants to use a single point of connection. Which of the following does the company need?
A. Unmanaged switch
B. Router
C. Hub
D. Managed switch
2. To avoid the expense of adding network cable or the uncertainty of wireless signals in a building with brick walls, which of the following would you use to add a network connection?
A. Router
B. PoE
C. EoP
D. Hub
3. Company B has just moved into a new building and has found an existing Internet connection that use RG-6 wiring. Which of the following is being used?
A. Cable
B. DSL
C. PoE
D. Router
4. Your client is a company that has two locations in the same city, both of which locations get their Internet service from the same provider in the same city. Both locations use the same type of service, but one location has service that is about three to five times faster than the other. What type of service is most likely being used?
A. Cable
B. Satellite
C. DSL
D. PoE
5. What feature of all network adapters can be used to determine which device a frame is sent from or going to?
A. IP address
B. MAC address
C. Switch port
D. Router
2.2 ANSWERS
1. D A managed switch can be used to create multiple networks.
2. C Ethernet over Power (EoP) sends Ethernet signals over power lines in a building.
3. A RG-6 is a type of wiring used for cable Internet and cable TV.
4. C DSL service varies widely in speed because its speed is dependent upon the distance from a client site to the central switch (central office) used by the phone company; longer distances have slower connections.
5. B Every network adapter, including those built into other devices, has a unique 48-bit MAC address.

Objective 2.3 Given a scenario, install and configure a basic wired/wireless SOHO network
Setting up a small office/home office (SOHO) network is a great way to learn how networking works while also bringing the benefits of networking, such as easy file sharing and more flexible printing, into your home or small office. The principles and methods you learn in this section will work on any workgroup network.
Router/Switch Functionality
The heart of most SOHO networks is a wireless router, such as the one shown earlier in Figure 2.2-4. Wireless routers actually combine three functions into a single device: a router, switch, and AP. Simply plug your computer into any of the LAN ports on the back and then plug the cable from your Internet connection into the port labeled Internet or WAN.
After the wireless router is connected to a computer and to the Internet, you can configure it as discussed in the following sections. We will discuss each of the functions separately, beginning with the AP.
Access Point Settings
Each AP includes a web server that hosts a browser-accessible configuration utility (see Figure 2.3-1) at the AP’s default IP address (often 192.168.1.1). The configuration utility prompts you to log in with an administrator password, which you create during installation or find in the AP’s documentation.
FIGURE 2.3-1 ASUS wireless router setup screen
Current APs come with web-based utilities that guide you through the initial setup, but manual setup isn’t too hard. Here’s a checklist:
• Install available firmware updates.
• Give the configuration utility a secure administrator password.
• Configure a unique SSID and consider disabling SSID broadcast.
• Modern WAPs should select a channel/frequency (also known as a control channel) automatically (see Figure 2.3-2), but you may still need to configure it to match other WAPs or use a quieter, less congested channel, based on a survey with a wireless analyzer.

FIGURE 2.3-2 Changing the channel
Cross-Reference
Cross-Reference
• Dual-band WAPs can separately enable or disable the 2.4-GHz and 5-GHz networks. Most setups use both bands for compatibility, but you can disable one band if interference makes it unreliable and all of your devices support the other band.
• Configure MAC filtering (see Figure 2.3-3) if you have known MAC addresses to allow or deny. Some routers support MAC filtering on both wired and wireless connections, while others, such as the one shown in Figure 2.3-3, support this feature only for wireless networks.
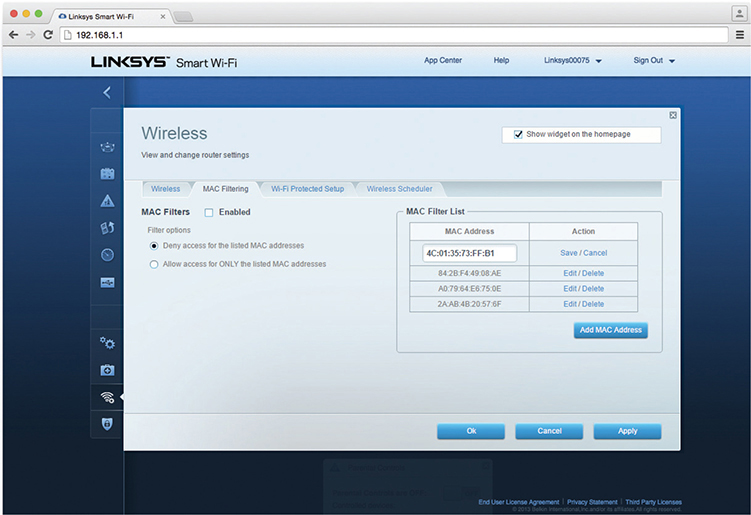
FIGURE 2.3-3 MAC filtering configuration screen for a Linksys AP
• Enable the best available security/encryption mode on the AP and generate or enter the security key or password (see Figure 2.3-4).
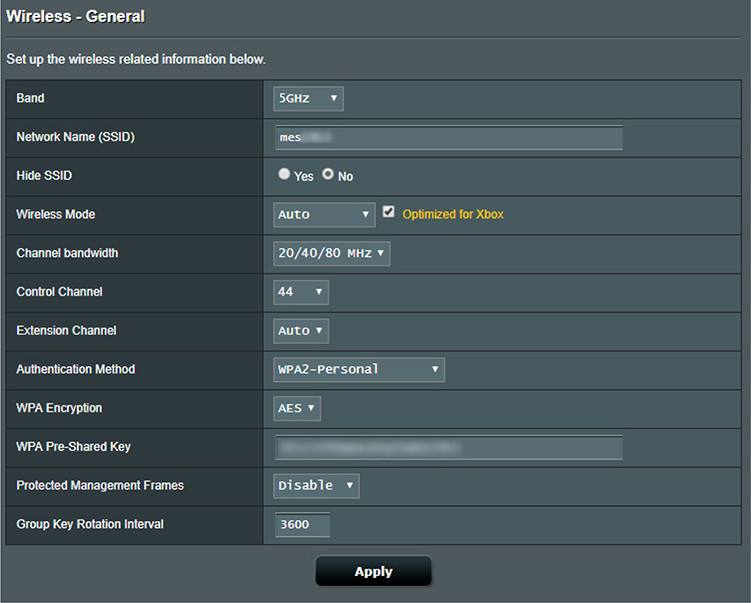
FIGURE 2.3-4 5-GHz properties panel for an ASUS AP with WPA2 Personal with AES selected
• If you absolutely must use older equipment that only supports WEP, it should have an option to generate encryption keys; select the highest available encryption level, enter a unique passphrase, and click the Generate button or its equivalent. Document these settings and either export the encryption keys to removable media or write them down as well; wireless clients will need this information to connect.
• WPA and WPA2 are configured similarly. Use WPA/WPA2 Personal for SOHO networks. WPA/WPA2 Enterprise requires a special server (called a RADIUS server) for serious security in larger business environments. Mixed network mode supports WPA clients on a WPA2-encrypted WAP; only use it if you must support WPA devices.
IP Addressing
There are two IP address settings you need to make on your router: First, make sure your router is configured with the correct IP address setting from your ISP. In most cases, your router will receive an IP address automatically. However, if the ISP has provided a static IP address, enter it in your WAN configuration. Next, unless the devices connecting to your router will have manual IP addresses, enable the DHCP server built into your router (see Figure 2.3-5). You can specify what range of IP addresses to assign automatically.

FIGURE 2.3-5 DHCP server settings in an ASUS router
NIC Configuration
Although both wired and wireless NICs offer many configuration options, most of them are not needed in a typical network. The available settings vary according to the network type.
Wired
Generally, wired networks should be configured to use auto-negotiation (see Figure 2.3-6) for network speed and duplex settings. Auto-negotiation enables the NIC to cope with any network settings without the need to reconfigure the NIC.

FIGURE 2.3-6 Viewing speed/duplex settings for a Gigabit Ethernet NIC
Wireless
At one time, wireless clients needed to know the wireless channel and encryption type used by the AP. However, this is no longer necessary. To connect to a wireless network using Windows, open the network icon in the taskbar, select (or enter, in the case of a hidden wireless network) the correct SSID, and enter the password (encryption key) as prompted (see Figure 2.3-7). The channel and encryption type are set automatically. With macOS, open the AirPort status icon, click Turn AirPort On, select the correct SSID, and enter the password as prompted. With Linux, use the ifconfig, iwconfig, and dhclient command-line utilities to set up your connection.

FIGURE 2.3-7 Connecting to a wireless network using Windows 10
End-user Device Configuration
Devices that you connect to a SOHO network, such as external drives, IP cameras, mobile devices, printers, scanners, multifunction devices (printer/scanner/fax/copier), need the following configuration settings:
• Wired network Select Wired Network or Ethernet as the connection type.
• Wireless network Select Wireless or Wi-Fi as the connection type, and provide the SSID and encryption key (if any).
After the device is configured, it should appear on the network and be selectable for printing, scanning, and so on.
Cross-Reference
IoT Device Configuration
The Internet of Things (IoT) is a broad category of devices that are used to monitor and control HVAC, security, and home entertainment, such as thermostats, light switches, security cameras, door locks, and voice-enabled, smart speakers/digital assistants. To communicate via the Internet, these devices also need to be configured. Here are the basic configuration methods for these devices (other than smart speakers/digital assistants, discussed separately next) after they are installed:
• Wi-Fi devices After installation, connect the device to your Wi-Fi network, install the companion app on your smartphone, set up an account, and use the app to configure your device. On some devices, you might need to temporarily connect to a Wi-Fi network on the device during the installation process.
• Z-Wave devices After installation, set up the device category on your Z-Wave controller, then follow the vendor’s procedure to connect the device to your controller. Install the companion app on your smartphone and use it to configure the device.
• Bluetooth low-energy devices After installation, install the companion app on your smartphone. Pair the device and use the app for initial configuration.
Voice-enabled, Smart Speaker/Digital Assistant
Smart speaker/digital assistant technology can be incorporated into operating systems or into hardware. These devices respond to voice commands and, using an Internet connection, can answer questions, activate lights, play music, play video, and more.
To use a digital assistant installed on a computer or mobile device, the computer or device must be connected to the Internet, and the user must enable the digital assistant app.
To use a smart speaker, the speaker must be paired to a computer or mobile device using its host app. If the smart speaker will be used with other hardware, such as home automation products, you need to choose compatible home automation products, set up the speaker to work with each specific device (a process known as “enabling the skill” with Alexa), and pair the speaker with the device.
Cable/DSL Modem Configuration
The basic configuration process for a cable or DSL modem is relatively simple:
1. Make sure you know the MAC (hardware) address for your modem; check the side, back, or bottom of the unit.
2. Make sure you know your ISP account information.
3. Connect the modem to the appropriate signal cable (coaxial cable for cable modem, phone cable for DSL).
4. Connect an Ethernet cable from the modem to a computer.
5. Connect the power cable for the modem to AC power and to the modem.
6. Turn on the modem.
7. After the signal lights on the modem indicate that the connection is live, go to the vendor’s web page to test and/or register your modem or account. Depending upon your ISP, you might need to call the ISP to register your modem.
If the modem also includes a wireless gateway or router, that must also be configured.
Firewall Settings
Although larger business networks and enterprise networks have separate firewall appliances, routers used for small-office/home-office (SOHO) uses have built-in firewalls. Just like a software firewall, a hardware firewall is designed to block unwanted inbound traffic. However, because the router’s firewall is designed to work with different devices that might require different types of access, it has many additional options. These are covered in the following sections.
DMZ
The incredibly dangerous demilitarized zone (DMZ) setting excludes specific devices from firewall protection, enabling all incoming traffic (and any attacks therein). Don’t use it. If you need to provide a different level of access to a particular device, set up the device with a static IP address and use port forwarding.
Port Forwarding
Port forwarding (see Figure 2.3-8) enables you to open a port in the firewall and direct incoming traffic on that port to a specific IP address on your LAN.

FIGURE 2.3-8 Port forwarding configured to pass HTTP traffic to a web server
NAT
Routers use Network Address Translation (NAT) to present an entire LAN of computers to the Internet as a single machine. All anyone on the Internet sees is the public IP address your ISP gives you—not private addresses assigned to devices on your LAN—effectively firewalling LAN nodes from malicious users on the vast untrusted WAN that is the Internet.
UPnP
A lot of networking devices designed for the residential space use a feature called universal plug and play (UPnP) to find and connect to other UPnP devices. This feature enables seamless interconnectivity at the cost of somewhat lower security, so disable it if you don’t need it.
MAC Filtering/Whitelist/Blacklist
Most APs support MAC address filtering to limit access to your wireless network using the physical, hard-encoded MAC address of each wireless network adapter. A table stored in the WAP—the access control list (ACL)—lists MAC addresses permitted (white list) or excluded (black list) from the wireless network.
QoS
You can configure Quality of Service (QoS) on your router (see Figure 2.3-9) to prioritize or limit access for certain users, applications, or services when there isn’t enough bandwidth to go around.

FIGURE 2.3-9 QoS configuration
Wireless Settings
The essential settings needed for an AP, a wireless router, or a wireless gateway include encryption type and channels (QoS, another important setting, is covered in the previous section).
Encryption
Encryption is used to protect wireless data from eavesdropping. Currently, there are three encryption standards supported by Wi-Fi: WEP, WPA, and WPA2. WPS is a setup method that makes it easier to use WPA or WPA2 encryption.
WEP
Wired Equivalent Privacy (WEP) encryption was meant to secure wirelessly transmitted data with standard 40-bit encryption; many vendors also support 104-bit encryption (which some advertise as 128-bit). Unfortunately, WEP contains some serious security flaws. Shortly after it was released, hackers demonstrated that WEP could be cracked in a matter of minutes using readily available software. It’s better than nothing, but it only stops casual snooping; it will not deter a serious attacker. Because WEP uses one key for all clients, other members of the network can read your packets.
WPA
Wi-Fi Protected Access (WPA) is a sort of interim security protocol upgrade for WEP-enabled devices. WPA uses the Temporal Key Integrity Protocol (TKIP) to protect from many attacks WEP was vulnerable to by providing a new encryption key for every packet sent. Other security enhancements include encryption key integrity-checking and user authentication through the industry-standard Extensible Authentication Protocol (EAP).
WPA2
The full IEEE 802.11i standard, WPA2, is the preferred way to lock down wireless networks. WPA2 uses the Advanced Encryption Standard (AES), among other improvements, to secure the wireless environment. Current WAPs and wireless clients support (and require) WPA2, and most access points have a “backward compatible” mode for the handful of devices that still need WPA.
WPS
The developers of Wi-Fi created Wi-Fi Protected Setup (WPS) to make secure connections using WPA or WPA2 easier for novice users to configure with a button (see Figure 2.3-10), password, or code. For example, you could connect a WPS-capable WAP and wireless printer by pressing the WPS button on the printer and then on the WAP within a set time. Sadly, WPS codes are very easy for a program to guess. The only protection is disabling WPS; check the WAP manufacturer’s website for instructions.

FIGURE 2.3-10 WPS button on an e2500 router
Channels
802.11-based wireless networks use one of two radio bands for sending and receiving data: 2.4 GHz and 5 GHz. Each band is comprised of a range of frequencies that are divided up into channels.
2.4-GHz channels range from 1 to 11 in most world areas. Unfortunately, only channels 1, 6, and 11 do not overlap with each other. The combination of a few non-overlapping channels and the crowded 2.4-GHz range can cause 2.4-GHz networks to be slow.
5-GHz channels are more numerous (13) and more widely spaced, enabling all channels to be usable.
As mentioned in the “Access Point Settings” section earlier in this objective, modern WAPs should select a channel/control channel/frequency automatically (refer back to Figure 2.3-2), but you may still want to configure it manually to use a quieter channel, based on a survey with a wireless analyzer.
REVIEW
Objective 2.3: Given a scenario, install and configure a basic wired/wireless SOHO network
• A wireless router is the foundation for a SOHO network, as it combines a router, a switch, and a wireless AP. It is managed through a browser-based interface.
• The router has two IP address settings to configure: enter (or confirm) the IP address used to connect to the broadband Internet device, and enable the DHCP server used to provide IP addresses to connected devices.
• To connect a wireless NIC, select the SSID and enter the encryption key (if used).
• To configure an end-user device such as external drives, IP cameras, mobile devices, printers, scanners, multifunction devices (printer/scanner/fax/copier), select the network type, then enter the SSID and encryption key if you choose a wireless connection.
• IoT device configurations for thermostats, light switches, security cameras, and door locks, vary according to whether they use Wi-Fi, Z-Wave, or Bluetooth for initial configuration.
• You must pair voice-enabled digital assistants and smart speakers with devices as part of their setup.
• During the process of setting up a cable or DSL modem, make sure you have a working connection with the ISP before completing the setup process.
• DMZ, port forwarding, NAT, UPnP, MAC filtering, and whitelist/blacklist firewall settings all affect network security.
• QoS improves network performance for priority data.
• Wireless encryption types from least to most secure are WEP, WPA (TKIP encryption), and WPA2 (AES encryption).
• WPS for easy push-button configuration is not secure and should not be used.
• Channels 1–11 are used for 2.4-GHz wireless networks; however, only 1, 6, and 11 are recommended for normal use.
• 5-GHz wireless networks have non-overlapping channels, making configuration easier than with 2.4-GHz networks.
2.3 QUESTIONS
1. Company C is setting up its own wireless network instead of using a contractor. Which of the following does the company need to configure to provide IP addresses automatically?
A. AES
B. TKIP
C. WEP
D. DHCP
2. The term Internet of Things (IoT) applies to a wide variety of devices. Which of the following categories is not considered an IoT category?
A. Streaming video playback
B. Lighting
C. Security
D. Thermostats
3. Company D is setting up a web server on its network. Which of the following router settings will enable the company to safely host the web server while protecting other devices with the router’s built-in firewall?
A. NAT
B. Port forwarding
C. DMZ
D. QoS
4. A wireless network that is using the old WEP encryption standard because of legacy equipment on the network has a lot of unauthorized use. Until the network can be upgraded to use WPA2-compliant devices, the client wants to allow only authorized devices to use the network by checking their MAC addresses. Which of the following describes what the client wants to create?
A. Blacklist
B. Red flag list
C. Whitelist
D. ACL
5. Your client is confused about how the devices on a network that connects to the Internet receive their IP addresses. Which of the following router functions do you need to explain to help the client understand this process?
A. DNS
B. Port forwarding
C. Blacklist
D. DHCP
2.3 ANSWERS
1. D DHCP supplies IP addresses to connected devices.
2. A Streaming video playback is a function of complex devices such as smart TVs; IoT devices are used to perform low-power and simple tasks.
3. B Port forwarding enables inbound connections of a particular type (such as web page requests on HTTP port 80) to be routed to a particular device.
4. C A whitelist allows only devices with listed MAC addresses to use the network.
5. D DHCP is the router function that provides IP addresses to connected devices.

Objective 2.4 Compare and contrast wireless networking protocols
Wireless networking is dominated by radio frequency (RF) technologies, in particular the 802.11 (Wi-Fi) standards (sometimes also referred to as WiFi, such as in the CompTIA A+ exam objectives), but you still need to be familiar with infrared, Bluetooth, and cellular standards.
802.11 Standards
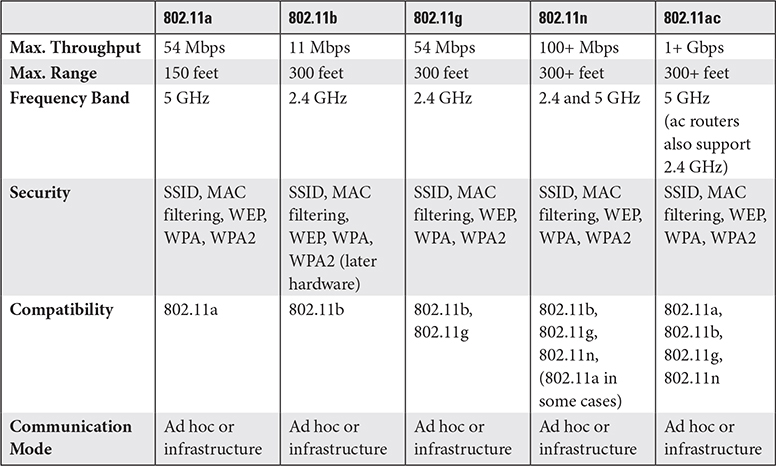
The IEEE 802.11 wireless Ethernet standard, better known as Wi-Fi, defines how devices can communicate with data broadcast in small chunks spread over available frequencies within the 2.4-GHz and/or 5-GHz bands (which are further divided into discrete channels). The original 802.11 standard has been extended to the 802.11a, 802.11b, 802.11g, 802.11n, and 802.11ac variations—newer standards (except for 802.11a) are backward compatible with their predecessors.
802.11a Despite the “a” on the end, it’s newer than 802.11b. It runs in the faster 5-GHz band, but its range suffers compares to 802.11b, and the use of the 5-GHz band makes it incompatible with both older and newer Wi-Fi devices unless they support 5 GHz (802.11n and 802.11ac).
802.11b The first wireless networking standard to take off; its main downside is that it uses the 2.4-GHz band already crowded with baby monitors, garage door openers, microwaves, and wireless phones.
802.11g Achieves the range of 802.11b and the speed of 802.11a, and maintains backward compatibility with 802.11b.
802.11n Introduced two new antenna technologies: multiple in/multiple out (MIMO), which increases speed by requiring all but handheld devices to use more than one of up to four antennas; and transmit beamforming, which adjusts the signal based on each client’s location. Also introduced optional dual-band support for both 2.4 GHz and 5 GHz, which means some 802.11n devices are backward compatible with 802.11a.
802.11ac Expands on 802.11n technology by adding more streams, speed, and wider bandwidth. Technically, 802.11ac only uses the 5-GHz band, but it too includes optional dual-band support. It introduces an updated MIMO called Multiuser MIMO (MU-MIMO) that enables a WAP to broadcast to multiple users simultaneously.
Table 2.4-1 compares the important characteristics of the 802.11 versions.
TABLE 2.4-1 Comparison of 802.11 Standards
Frequencies: 2.4 GHz, 5 GHz
Wi-Fi supports two different frequency bands: 2.4 GHz and 5 GHz (listed as 2.4Ghz and 5Ghz in the CompTIA objectives). These frequencies differ in the number of available channels and, consequently, in ease of configuration.
Channels
The number of channels available in a 5-GHz wireless network is more than the number of channels available in a 2.4-GHz network. A 5-GHz network has the following non-overlapping channels using the standard 40-MHz width (twice the width of 2.4-GHz channels): 38, 46, 54, 62, 102, 110, 118, 126, 134, 134, 142, 151, 159.
When 80-MHz wide channels are used, available non-overlapping channels are 42, 58, 106, 122, 138, 155.
When 160-MHz wide channels are used, available non-overlapping channels are 50, 114.
1–11
If your wireless router or AP supports only channels 1–11 or 1–13 (Japan/Europe), it supports only the 2.4-GHz wireless band. Unfortunately, the frequencies used mean that most channels overlap, causing slowdowns when in use. To avoid congestion, use channels 1, 6, and 11 if you use the standard 20-MHz channel width; 40-MHz channels are available on 802.11n, but channel 3 is the only non-overlapping channel when 40-MHz channels are used.
Bluetooth
Bluetooth creates small wireless networks ideal for wearable devices, audio headsets, and automotive entertainment systems that connect to your smartphone; linking two computers in a quick-and-dirty wireless personal area network (PAN); and input devices such as keyboards and mice (see Figure 2.4-1) as well as mobile device headsets and speakers. Most connections are ad hoc, but Bluetooth access points also exist.

FIGURE 2.4-1 External USB Bluetooth adapter, keyboard, and mouse
Bluetooth has grown faster and more secure over the years, but speed isn’t Bluetooth’s big selling point—reliable low-power communication is. Bluetooth resists interference by hopping between 79 frequencies in the 2.45-GHz range around 1600 times a second. Bluetooth enables wearables and peripherals to save much-needed power with three power-use classes, as shown in Table 2.4-2.
TABLE 2.4-2 Bluetooth Classes

Let’s look at what has changed over the years:
• The first generation (versions 1.1 and 1.2) supports speeds around 1 Mbps.
• The backward-compatible second generation (2.0 and 2.1) increases speed to around 3 Mbps with Enhanced Data Rate (EDR).
• With the optional High Speed (+ HS) feature, the third generation (3.0) tops out at 24 Mbps by transferring data over an 802.11 Wi-Fi connection after initial Bluetooth negotiation.
• Called Bluetooth Smart, the fourth generation (4.0, 4.1, 4.2) focuses on better support for “smart” devices by reducing cost and power use, and improving speed and security. The most interesting addition is IP connectivity so Bluetooth devices can skip the smartphone and talk directly to a Bluetooth-enabled AP.
• Bluetooth 5 (fifth-generation Bluetooth) is optimized for IoT devices such as smart speakers, lights, and so on. Bluetooth 5 provides options for trading greater speed for reduced range or changing packet sizes.
NFC
Near field communication (NFC) uses chips embedded into mobile devices that create and communicate with tiny electromagnetic fields, limiting range between NFC-enabled devices to a few inches. NFC can exchange contact information, small files, and even payment transactions with stored credit cards using systems such as Apple Pay and Google Pay.
RFID
Radio frequency identification (RFID) is used to identify and track the location of objects. It combines RFID scanners that use electromagnetic fields with RFID tags that respond when moved through a scanner field. RFID tags consist of a microchip and antenna; they are often used for theft prevention and inventory tracking.
Zigbee
Zigbee (also known as ZigBee) is a popular IoT standard for home automation and security. It is based on the IEEE 802.15.4 wireless networking standard, but unlike Wi-Fi, Zigbee is designed for short-range interchange of sensor data at a data rate of about 250 Kbps, using 2.4 GHz or lower frequencies. A Zigbee network must include at least one Coordinator and one or more Zigbee devices. Zigbee devices support mesh networking, and many of them are battery powered, thanks to the low voltage needed to run Zigbee. To connect complex Zigbee networks such as cluster tree or mesh networks together, Zigbee routers are used. Zigbee works with Amazon Alexa.
Z-Wave
Z-Wave is a home automation and security standard developed by Zensys and currently managed by the Z-Wave Alliance. Z-Wave runs in the 908.42-MHz frequency and uses a wireless hub to connect to Z-Wave devices. Z-Wave also supports mesh topologies.
Up to 232 Z-Wave devices can be in a single Z-Wave network. Z-Wave uses very little power, so some Z-Wave devices run on battery power, while others plug into AC outlets. The Z-Wave Alliance certifies Z-Wave compatible devices.
Cellular Standards: 3G, 4G, LTE, 5G
3G is the general term for third-generation cellular data services. 3G hit the market in the early 2000s, and typically offers maximum data rates of at least 144 Kbps. However, most implementations of 3G run at much faster speeds. Although most wireless networks now support its successor, 4G, 3G is still in use in some areas.
4G is the general term for fourth-generation cellular data services. 4G began to roll out during the early 2000s. Originally, there were several competing 4G standards, but Long Term Evolution (LTE), also known as 4G LTE, is the current standard. Although LTE claims to run at up to 300 Mbps download and 75 Mbps upload, real-world performance is typically lower, as shown in Figure 2.4-2.
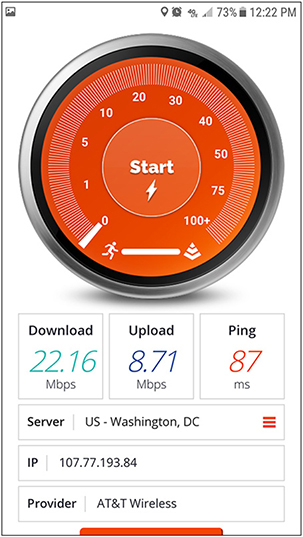
FIGURE 2.4-2 Real-world LTE speed test
5G is short for fifth-generation cellular data services. 5G is much faster than 4G (up to 20-Gbps peak speeds), offers lower latency for gaming, and uses small short-range wireless antennas on buildings rather than the large antenna towers used by 4G LTE and older networks. Note that the so-called 5GE network from AT&T is actually a new name for their gigabit-class 4G LTE network. True 5G networks require users to get new smartphones.
REVIEW
Objective 2.4: Compare and contrast wireless networking protocols
• Wi-Fi standards from slowest to fastest include 802.11b, 802.11a, 802.11g, 802.11n, and 802.11ac. 802.11a and 802.11ac are 5-GHz standards, and 802.11n has an optional 5-GHz feature. All others are 2.4 GHz. 802.11ac is backward compatible with 2.4-GHz networks.
• 2.4-GHz Wi-Fi networks use channels from 1 to 11, but only channels 1, 6, and 11 don’t overlap.
• 5-GHz Wi-Fi networks can use 13 non-overlapping channels.
• Bluetooth is a short-range network used for data interchange or connections with keyboards, mice, and headsets.
• NFC is used for touchless payments and data interchange with smartphones.
• RFID is used for inventory tracking and theft prevention.
• Zigbee is a popular IoT standard for home automation and security. Z-Wave is also aimed at this market, but differs in several ways.
• 3G, 4G, and 5G are the most recent cellular data services, with 4G LTE being the dominant one. 5G is available in only a few cities at present.
2.4 QUESTIONS
1. Company E is replacing its aged 802.11g wireless network with newer hardware. Which of the following would provide the fastest speed and also support older devices?
A. 802.11a
B. 802.11ac
C. 802.11n
D. 802.11b
2. Company F is installing Bluetooth mice and keyboards in its meeting room, which is about 8 meters from front to back. The computer will be at the back of the room. Which Bluetooth standard is the minimum needed to have the range necessary?
A. Bluetooth Class 2
B. Bluetooth Class 1
C. Bluetooth 4.2
D. Bluetooth Class 3
3. Company G is having a huge problem with theft in its warehouse. Which of the following technologies does it need to implement to track inventory and help prevent theft?
A. NFC
B. Z-Wave
C. RFID
D. 4G LTE
4. Your client wants to use multiple devices that can relay radio signals to and from each other as part of their smart home. What is this category of technology called?
A. Wi-Fi
B. Hotspot
C. Bluetooth
D. Mesh
5. A co-worker wants to use a smartphone to make payments instead of digging through a wallet or purse for a credit card. What feature needs to be enabled?
A. NFC
B. Z-Wave
C. Wi-Fi
D. Mesh
2.4 ANSWERS
1. B 802.11ac is the fastest wireless standard in use and is also backward compatible with older hardware.
2. A Bluetooth Class 2 devices have a maximum range of up to 10 meters.
3. C RFID chips on merchandise and scanners at entrances, exits, and restrooms will help reduce theft.
4. D A mesh network uses multiple devices that can wirelessly connect directly with each other. Several smart home technologies use mesh networking, including Zigbee and Z-Wave, among others.
5. A Near field communication (NFC) is used for cardless payment systems such as Apple Pay or Google Pay.

Objective 2.5 Summarize the properties and purposes of services provided by networked hosts
Network hosts can be used as servers to provide file, print, and other types of services; as network appliances, to provide security and network protection features; and as embedded and legacy devices to provide ATM, traffic light, machine control, and other specialized services.
Server Roles
A server is any computer or device that provides services to connected devices. Depending on the size and types of networks in use, some servers are built into devices such as routers, and computers on the network perform server roles. The following sections describe these roles.
Web Server
A web server runs software designed for serving websites. For example, the Microsoft Internet Information Services (IIS) functionality is available as an optional feature of Windows Server and business-oriented editions of Windows 7, Windows 8/8.1, and Windows 10. Most Linux distributions include Apache or Nginx web servers. Apache can also be used on macOS.
File Server
A file server stores files that are used by other computers or devices on a network. For SOHO or small business networks, you can enable file sharing on Windows, Linux, or macOS computers. However, larger networks use dedicated file server computers. File servers generally feature very large high-speed storage devices and high-performance network adapters.
Print Server
A print server manages a network print queue for printers that are attached to the server or are connected directly to the network. Depending on the network, a single physical server might be used for both file and print server tasks or separate servers might be used.
DHCP Server
A Dynamic Host Configuration Protocol server (DHCP server) provides IP addresses, default gateways, and other network settings such as DNS server addresses to connected devices. Typically, a DHCP server’s function is incorporated into a device such as a router on a SOHO network. However, larger networks might use dedicated DHCP servers.
DNS Server
A Domain Name Service server (DNS server) maintains a database of IP addresses and their matching host names. When a host name, such as www.totalsem.com, is entered into a web browser, the DNS server used by that system matches www.totalsem.com to the appropriate IP address.
DNS servers are provided by ISPs as well as by public DNS services such as Google DNS or OpenDNS. Although your device typically is configured with DNS servers by the DHCP server, it is possible to manually configure the DNS servers you prefer.
Proxy Server
A proxy server is an intermediary between its users and the resources they request. Applications send requests to the proxy server instead of trying to access the Internet directly, and the proxy server fetches the resources on behalf of the users. This enables the proxy server to monitor usage; restrict access to or modify insecure or objectionable content; cache, compress, or strip out resources to improve performance; and more. Enterprise proxy servers are usually implemented as software running on a multipurpose server.
Mail Server
A mail server sends or receives mail. Incoming servers (where you check for new mail) typically use Post Office Protocol version 3 (POP3) or Internet Message Access Protocol version 4 (IMAP4), while outgoing servers (where you send mail) use Simple Mail Transfer Protocol (SMTP). These addresses come from your e-mail provider (usually your ISP, company, school, or other organization).
Authentication Server
An authentication server is used to verify the identity of a user after the user has logged in to a network. Some examples of authentication servers include RADIUS servers used by WPA and WPA2 encryption on corporate networks and servers that inspect RSA tokens provided by users with RSA key fobs.
Syslog
Syslog is a protocol that network devices use to send event messages to a server that logs them for viewing. The syslog server can send alerts that can be reviewed by network administrators. Syslog is not natively supported on Windows, but third-party software can be used to convert messages from Windows apps into syslog-compatible messages.
Internet Appliance
Internet appliances are special-purpose devices that are incorporated into networks, typically to provide various types of network security. The following sections provide a brief overview of the types of Internet appliances you need to know for the CompTIA A+ 220-1001 exam.
IDS
An intrusion detection system (IDS) inspects packets from within the network to look for active intrusions or threats (such as viruses, illegal logon attempts, or a disgruntled employee running a vulnerability scanner) that are already behind the firewall. If it finds something suspicious, it will do some combination of the following: log it, contact an administrator, and enlist help from other devices such as a firewall.
IPS
The more powerful intrusion prevention system (IPS) sits directly in the flow of traffic, enabling it to stop an ongoing attack dead in its tracks (or even fix packets on the fly), but network bandwidth and latency take a hit. Additionally, if the IPS goes down, it may take the network link with it.
UTM
Modern dedicated firewall/Internet appliances are built around providing unified threat management (UTM), which bundles other security services such as IPS, VPN, load balancing, anti-malware, and more.
End-point Management Server
An end-point management server centralizes the management of all types of end-user devices, including desktops, laptops, and mobile devices. It can provide security, access to enterprise apps for mobile devices, and a consistent user interface for managed devices.
Legacy/Embedded Systems
Networked devices don’t necessarily look like computers. Many are, but you can find narrow-purpose computers or servers embedded in all sorts of machines and other equipment—CompTIA calls these legacy/embedded systems. It can be easy to overlook networked devices embedded in this equipment, but they may represent massive investments your network must remain compatible with. Some examples of legacy/embedded systems include machine controllers, digital watches, digital music players, traffic light controllers, aviation equipment, bank ATMs, and so on. If these systems are running operating systems that are no longer supported with security or other patches (such as Windows XP), they represent a significant security threat.
REVIEW
Objective 2.5: Summarize the properties and purposes of services provided by networked hosts
• Web servers run software that serves websites.
• File servers store files and folders for use on the network.
• Print servers manage network print queues.
• DHCP servers provide IP addresses to connected devices.
• DNS servers handle DNS/IP address lookups.
• Proxy servers reroute requests for Internet content to their own copy of that content or block requests.
• Mail servers send and receive mail.
• Authentication servers verify a user’s identity.
• The syslog protocol is used to send event messages to a server where they can be logged and viewed.
• Internet appliance categories include IDS, IPS, UTM, and end-point management servers, all of which can be used to protect the network.
• Legacy/embedded systems such as ATMs and machine controllers represent a significant security threat if their operating systems are no longer being patched.
2.5 QUESTIONS
1. Microsoft IIS and Apache are examples of which type of server?
A. DHCP server
B. File server
C. Web server
D. Print server
2. Company H is setting up a RADIUS server as part of its wireless network. This server will perform which of the following tasks?
A. Mail server
B. Authentication server
C. Proxy server
D. Print server
3. Company J wants to install an Internet appliance that will provide protection as well as load balancing and VPN services. Which of the following categories has the device they need?
A. IPS
B. DLP
C. IDS
D. UTM
4. Your client’s network is able to receive mail but unable to send it. Which of the following is not working?
A. SMTP
B. UTM
C. Authentication server
D. DNS server
5. Your department is considering an Internet appliance. Which of the following is the most likely reason to get one?
A. Print serving
B. Security
C. Wireless AP
D. Web server
2.5 ANSWERS
1. C These are examples of web servers.
2. B A RADIUS server is used for authentication on a WPA or WPA2 Wi-Fi enterprise network.
3. D UTM is unified threat management, which includes broad protection against threats and bundles network security services
4. A SMTP (Simple Mail Transfer Protocol) is used to send e-mail messages. If this protocol is disabled or blocked, e-mail cannot be sent.
5. B Internet appliances are used to provide additional security features to an Internet connection.

Objective 2.6 Explain common network configuration concepts
To enable a network to work properly, an IP address must be assigned to each device on the network, a mechanism must be available for translating between website names and IP addresses, and methods must exist for connecting different networks to each other. This objective explains these features.
IP Addressing
A network address must uniquely identify the machine, and it must locate that machine within the larger network. In a TCP/IP network, an IP address identifies a device and the network on which it resides.
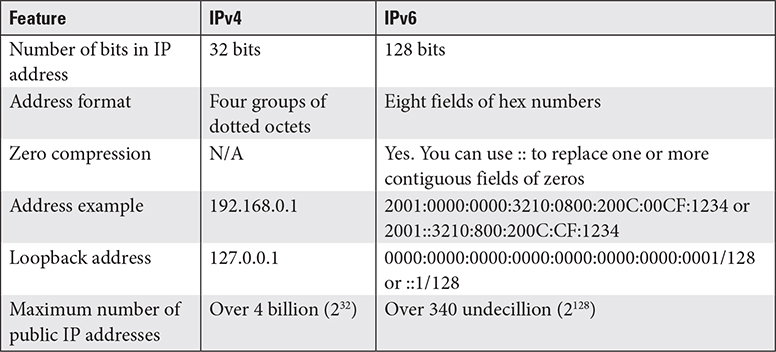
There are two versions of Internet Protocol (IP): IPv4 and IPv6. The following sections cover their essentials features and differences.
An Internet Protocol version 4 (IPv4) address is expressed in dotted-octet notation—four sets of eight binary numbers (octets) separated by periods. The binary form (11001010.00100010.00010000.00001011) isn’t human-friendly, so we usually use a decimal form (202.34.16.11).
Cross-Reference
An IPv4 loopback address is the address assigned to the adapter inside a computer or device. Each device has the same loopback address (127.0.0.1) because it is used for testing, not for routing data. If you cannot ping your computer’s loopback address, you have a problem with your IP configuration.
The 32-bit IPv4 standard offers 4 billion addresses; this seemed like plenty in the beginning, but the Internet Engineering Task Force (IETF) had to develop a replacement, Internet Protocol version 6 (IPv6), to support enough addresses for the foreseeable future. IPv6 notation uses up to eight colon-separated groups (unofficially called fields or hextets), each containing a hexadecimal number between 0000 and FFFF.
IPv6 has “up to” eight groups because there are two ways to shorten the written form:
• Leading zeros can be dropped per group, so 00CF becomes CF and 0000 becomes 0.
• Once per address, you can omit any number of consecutive all-zero groups, leaving just the two colons at either end.
Here’s a full IPv6 address followed by a shorter form applying these rules:
2001:0000:0000:3210:0800:200C:00CF:1234
2001::3210:800:200C:CF:1234
OS developers have two options for the last 64 bits of an IPv6 address. The method Windows uses is to generate a random value when you activate a NIC and never change it. Linux and macOS use the other method: build it from the MAC address of the NIC (called the Extended Unique Identifier, 64-bit, or EUI-64).
IPv6 adapters also have a loopback address that can be used for testing. The full address is 0000:0000:0000:0000:0000:0000:0000:0001/128. It is usually abbreviated as ::1/128 (using the two-colon abbreviation for consecutive all-zero groups).
IPv4 vs. IPv6
As you have seen, IPv4 and IPv6 differ in many ways. Table 2.6-1 helps you compare the differences.
TABLE 2.6-1 IPv4 vs. IPv6
Dynamic
In DHCP, which Windows uses by default, systems receive their IP address, subnet mask, default gateway address, and DNS address from the DHCP server automatically. This is also known as dynamic IP address assignment. To see the current IP properties sheet:
1. Open the Control Panel and select Network and Sharing Center.
2. Click Change Adapter Settings.
3. Click the Local Area Connection link.
4. Click Properties.
5. Click Internet Protocol Version 4.
6. Click Properties.
See Figure 2.6-1 for a typical example of dynamic IP addressing.
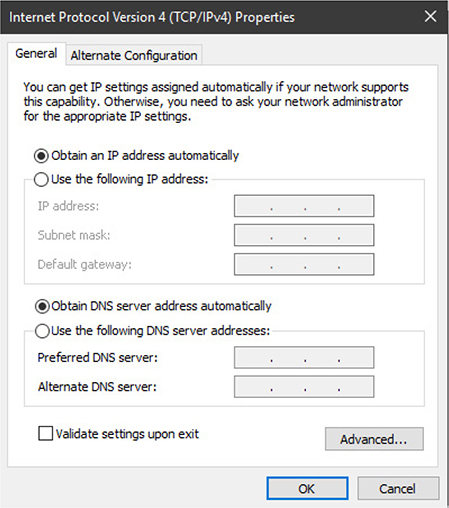
FIGURE 2.6-1 Network adapter configured to get IP address from DHCP server
APIPA
If the system is configured to obtain an address automatically but can’t do so, the OS will use Automatic Private IP Addressing (APIPA) to set a 16-bit subnet mask (255.255.0.0) and randomly choose an address from 169.254.0.1 to 169.254.255.254. The system will broadcast this random address on the subnet and use it if no other system responds. An APIPA address cannot be used for Internet access.
Link Local
When a computer running IPv6 boots, it gives itself a link-local address, the equivalent to IPv4’s APIPA address. Because APIPA is a fallback in IPv4, the use of an APIPA address can indicate a loss of network connectivity or a problem with the DHCP server; IPv6 systems always have a link-local address. The first 64 bits of a link-local address are always FE80:0000:0000:0000 (which shortens to FE80::).
Static
A static IP address is an IP address that is manually assigned. Typically, static IP addresses are used in networks for systems that must always have the same IP address because they are used as servers or because they use different protocol settings than other devices on the network. When a static IP address is used, the IP address, subnet mask, default gateway, and DNS servers must also be assigned. See Figure 2.6-2 for a typical example.
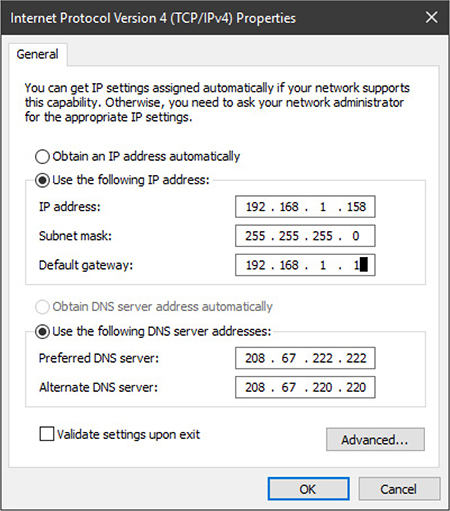
FIGURE 2.6-2 Network adapter configured with a static IP address
DNS
The Domain Name Service (DNS) matches IP addresses to host names. Each device on an IP network must have access to at least one DNS server to be able to connect to host names. DNS values are typically assigned by the DNS server, but can also be manually entered (refer to Figures 2.6-1 and 2.6-2 for examples).
DHCP
The Dynamic Host Configuration Protocol (DHCP) assigns unique IP addresses to each device on a network. The default setting for Windows and macOS devices is to use DHCP-assigned IP addresses.
Reservations
A DHCP reservation is a DHCP-supplied IP address that never changes. It is meant for devices whose IP address needs to remain constant; for example, a print server. DHCP reservations are created on the DHCP server. This feature is available in DHCP servers as well as in some SOHO routers.
Subnet Mask
Part of an IPv4 address identifies the network (the network ID), and the rest identifies the local computer (the host ID, or host). NICs use a subnet mask to indicate which part identifies the network ID and which identifies the host by blocking out (masking) the network portion. A 255 group is in the network ID, and zeros are in the host ID. Because the first three subnet mask octets in the following example are 255, the network ID is 192.168.4 and the host ID is 33:
IP address: 192.168.4.33
Subnet mask: 255.255.255.0
Computers on the same LAN must have the same network ID and unique host IDs. Two computers with the exact same IP address create an IP conflict; they won’t be able to talk to each other, and other computers won’t know where to send data. An IPv4 address can’t end with 0 or a 255, so our sample network supports 254 addresses from 192.168.4.1 to 192.168.4.254.
Originally, subnet masks fell into A, B, or C “classes,” where Class C was 255.255.255.0, Class B was 255.255.0.0, and Class A was 255.0.0.0. One Class B network ID left two full octets (16 bits) for 64,534 unique host IDs (216 – 2). This system is long gone, but it’s still common to see subnet masks expressed in one to three groups of 255.
The current Classless Inter-Domain Routing (CIDR) system works well in binary—where you make subnets with any number of 1s in the mask—but these octets tend to look odd to new techs when presented in decimal (see Table 2.6-2).
TABLE 2.6-2 CIDR Subnets

IPv6 still has subnets, but we append the “/x” from CIDR with the IP address itself: FEDC::CF:0:BA98:1234/64.
Gateway
A gateway is a link connecting two networks. When a computer uses DHCP for its IP address, it receives the default gateway’s IP address as part of its settings. However, if you configure a device’s IP address manually, you must provide the default gateway’s IP address yourself. The default gateway on most private networks is an address such as 192.168.0.1 or 192.168.1.1.
To see the current IP address, subnet mask, default gateway, and DNS servers in Windows, open a command prompt and use the command ipconfig /all. Scroll to the current Local Area Connection after running the command (a typical example is shown in Figure 2.6-3). The comparable command in Linux and macOS is ifconfig.
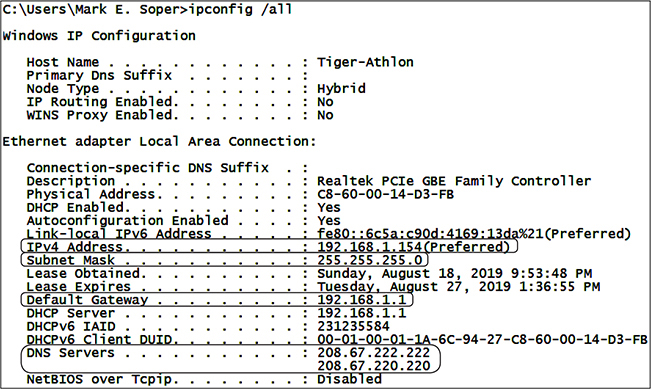
FIGURE 2.6-3 Using ipconfig /all to display the current IP address, subnet mask, default gateway, and DNS servers on the author’s PC
VPN
A virtual private network (VPN) sets up endpoints at each end of an encrypted tunnel between computers or networks to join them into a private network as if they were on a directly connected LAN (though they obviously won’t perform like it). In order to pull this trick off, the endpoint on each LAN gets its own LAN IP address and is responsible for handling traffic addressed to and from the remote network (see Figure 2.6-4).

FIGURE 2.6-4 Typical VPN tunnel
To create a VPN connection in Windows 7, click Start, type VPN in the Search bar, and press ENTER. In Windows 8/8.1/10, type VPN at the Start screen and select Manage virtual private networks (VPN) on 8/8.1 or VPN settings on 10. Enter your VPN server information, which your network administrator will most likely provide, in the resulting dialog box (see Figure 2.6-5). This creates a virtual NIC that gets an IP address from the DHCP server back at the office.
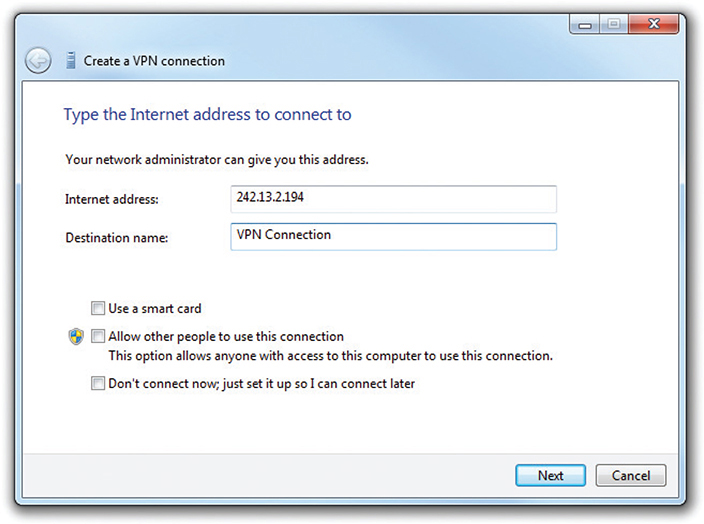
FIGURE 2.6-5 VPN connection in Windows
To set up a VPN connection in macOS, open System Preferences | Network, click Add, choose VPN, select the VPN type, the server address, account name, and authentication settings, and click OK. Click Connect to connect.
To set up a VPN connection in Linux, check the distro’s documentation.
VLAN
A virtual local area network (VLAN) is a subsection of a physical network that is partitioned from the rest of the physical network at the Data Link layer (OSI Layer 2) and is used as a separate physical network. VLANs can be created with managed switches. For example, a 48-port managed switch could be subdivided into six eight-port VLANs.
NAT
Network Address Translation, which conceals private IP addresses connecting to a route and displays only a public IP address on the Internet, is a standard router feature.
Cross-Reference
REVIEW
Objective 2.6: Explain common network configuration concepts
• A dynamic IP address is received from a DHCP server by a device on the network.
• An APIPA address is generated if the DHCP server cannot be reached.
• A link-local address is IPv6’s equivalent to an APIPA address.
• A static IP address is an address that is manually assigned.
• If a static IP address is assigned, a DNS server must also be assigned.
• A DHCP reservation is a DHCP-supplied IP address that doesn’t change.
• IPv4 uses dotted-octet notation and a subnet mask.
• IPv6 uses up to eight groups of numbers and supports methods to shorten its address.
• NICs use a subnet mask to indicate which part of an IP address identifies the network ID and which identifies the host by blocking out (masking) the network portion.
• A gateway is a link connecting two networks.
• A VPN is a virtual private network. It enables secure connections over an unsecure network such as the Internet.
• A VLAN is a collection of ports that act as a separate physical network; it requires a managed switch.
• NAT protects private network addresses from being revealed to the Internet.
2.6 QUESTIONS
1. A user cannot connect to the Internet. When you ask her for her current IP address, she tells you it is 169.254.0.18. Which of the following is not working?
A. APIPA
B. Static IP
C. Link-local
D. DHCP
2. You are reconfiguring up a system using IPv4 and a static IP address after its original settings were deleted. The subnet mask was recorded using the CIDR shorthand of /24. Which of the following decimal subnet masks should you enter when entering the IPv4 address?
A. 255.255.255.0
B. 192.168.1.1
C. 255.255.0.0
D. 2001::3210:800:200C:CF:1234
3. Company K has a sales force that typically uses insecure hotel and coffee-shop wireless networks. Which of the following should you advice they start using to enhance security?
A. VLAN
B. VPN
C. NAT
D. IPv6
4. A DHCP-provided IP address that never changes is known as which of the following?
A. IP permanency
B. IP reservation
C. Link-local
D. APIPA address
5. Your client wants to buy a single switch to create three separate wired networks. What type of networks does the client want to create?
A. VPN
B. Link-local
C. VLAN
D. IPv6
2.6 ANSWERS
1. D A 169.254.x.x address is generated when the DHCP server cannot be reached.
2. A /24 is the CIDR shortcut for 255.255.255.0.
3. B A VPN is a virtual private network, which creates a secure “tunnel” for carrying network traffic through insecure connections.
4. B An IP reservation is an address set up by a DHCP server that doesn’t change.
5. C A VLAN is a group of ports on a managed switch that performs as if it’s on a separate network from other ports on the switch.

Objective 2.7 Compare and contrast Internet connection types, network types, and their features
There are many different methods for connecting to the Internet and many different network types. They work together to connect devices into networks ranging in size from small LANs to worldwide networks.
Internet Connection Types
Objective 2.2 earlier in this domain briefly discussed the concept of a bridge that translates signals from one network media to another. When you want to connect a LAN to the Internet, what you’re looking for is a bridge between that LAN and one of the data transmission media available in your house or building. No matter how you slice it, you need hardware that can connect your computer, LAN, or WLAN to this other media and you need software that speaks to this hardware—but where these components are located varies.
In general use we call this hardware a modem, even though vanishingly few of them are true modulator/demodulators that create a bridge to analog transmission media. Sometimes we install the hardware and software both into a host computer (in which case the computer itself serves as part of the bridge); other times, the software is built into the hardware device, which itself connects directly to a standard RJ-45 jack on our computer or router. The following sections explain the many types of Internet connections.
Cable
Cable uses regular RG-6 or RG-59 cable TV lines to provide upload speeds from 5 to 35+ Mbps and download speeds from 15 to 1000+ Mbps. Cable Internet connections are theoretically available anywhere you can get cable TV. The cable connects to a cable modem that itself connects (via Ethernet) to a small home router or your network interface card (NIC).
DSL
Digital subscriber line (DSL) connections to ISPs use standard telephone lines, but special equipment on each end creates always-on Internet connections at much greater speeds than dial-up. To set up a DSL connection, connect a DSL receiver (shown in Figure 2.7-1) from the ISP to the telephone line. A tech or knowledgeable user then configures the DSL modem and router with settings from the ISP.

FIGURE 2.7-1 A DSL receiver
Service levels for DSL can vary widely. At the low end of the spectrum, speeds are generally in the single digits—less than 1 Mbps upload and around 3 Mbps download. Where available, more recent xDSL technologies can offer competitive broadband speeds measured in tens or hundreds of megabits per second.
Dial-up
Dial-up Internet links use the first ubiquitous data network—the telephone system. In traditional dial-up, connection software on a computer uses an analog modem. An internal version for desktop computers is shown in Figure 2.7-2.

FIGURE 2.7-2 An internal modem
An external modem is shown in Figure 2.7-3. With either type, the modem is used to dial (as in, dial a phone) the ISP, where it begins translating between digital information and analog sound to negotiate a connection. At 56 Kbps download and up to 48 Kbps upload, dial-up is glacial when compared to the newest connection standards.

FIGURE 2.7-3 An external USB modem
You can create a new connection from within the OS. You’ll need to provide one or more dial-up telephone numbers for the ISP as well as your user name and password; the ISP should give you this information along with any configuration options specific to their system. In Windows 7, for example, you can click Set up a new connection or network from the Network and Sharing center applet, select Connect to the Internet, and enter the dial-up connection details (as shown in Figure 2.7-4).

FIGURE 2.7-4 Creating a dial-up connection in Windows 7
If you have to troubleshoot a traditional modem, keep in mind what it is and how it works. The user needs a dial tone, and they may need to configure a prefix to “dial out” if they’re in an office or hotel. They may not be able to test their connection while they speak with you. They can manually dial the number (or listen in) and confirm another computer answers it. If you’ve double-checked everything, including connection numbers and user credentials, it’s time to call the ISP to troubleshoot Dial-up Networking settings.
Fiber
DSL providers have developed very popular fiber-to-the-node (FTTN) and fiber-to-the-premises (FTTP) services that provide Internet (and more). FTTN connections run from the provider to a box in your neighborhood, which connects to your home or office via normal coaxial or Ethernet cable. FTTP runs from the provider straight to a home or office, using fiber the whole way.
AT&T Internet FTTN services start with download speeds up to 100 Mbps and upload speeds up to 20 Mbps. AT&T also offers 300 Mbps and 1 Gbps FTTP services.
Verizon’s Fios FTTP service provides upload and download speeds from 100 Mbps to 500 Mbps and its Fios Gigabit connection runs at up to 940 Mbps download and 880 Mbps upload. Google Fiber offers a 1 Gbps upload/download service in a few cities nationwide.
Cable TV providers are also using fiber to push speeds to 1 Gbps.
Satellite
Satellite connections beam data to a professionally installed satellite dish at your house or office (with line-of-sight to the satellite). Coax connects the satellite to a receiver or satellite modem that translates the data to Ethernet, which can connect directly to your router or the NIC in your computer.
Real-world download speeds in clear weather run from a few to about 25 Mbps; upload speeds vary, but are typically a tenth to a third of the download speed. They aren’t stunning, but satellite can provide these speeds in areas with no other connectivity.
ISDN
On all-digital telephone lines, you may be able to get integrated services digital network (ISDN) dial-up, which uses a terminal adapter (TA) that closely resembles a dial-up modem. ISDN uses 64-Kbps channels in two common configurations: basic rate interface (BRI), which combines two channels for 128-Kbps bandwidth, and primary rate interface (PRI), which combines 23 channels for 1.544 Mbps. Most ISPs that formerly offered ISDN are now offering some form of DSL, which is substantially faster.
Cellular
Cellular Internet connections are available in 3G, 4G, and, in a few locations, 5G, as discussed in the “Cellular Standards: 3G, 4G, LTE, 5G” section in Objective 2.4, earlier in this domain. In addition to being available in smartphones, cellular connections are also available for tablets and laptops as an additional wireless feature alongside the usual Wi-Fi and Bluetooth connections.
Mobile Hotspot/Tethering
A mobile hotspot device creates a Wi-Fi network to share its cellular data connection (3G, 4G, 4G LTE, or 5G) with other Wi-Fi devices. Wireless providers sell standalone hotspot devices for their network, but many smartphones and tablets can act as hotspots. Just enable the cellular data connection and toggle the hotspot setting to broadcast the Wi-Fi network and serve as a router between it and the cellular network (see Figure 2.7-5); configure a password to limit access.
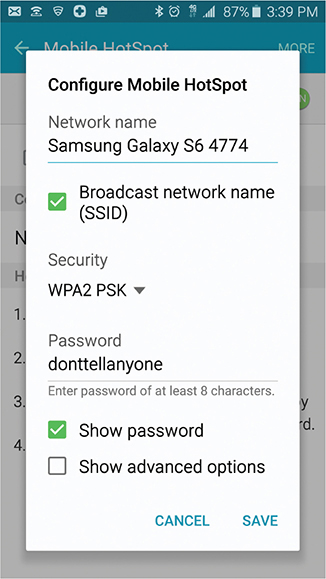
FIGURE 2.7-5 Configuring an Android phone as a portable hotspot
Sharing a smartphone or tablet’s data connection is also called tethering when a USB cable is used, a term you’ll see carriers use to indicate different rules, rates, and restrictions on data consumed this way.
Line-of-sight Wireless Internet Service
Line-of-sight wireless Internet service (also known as fixed wireless) is a popular choice in some smaller cities and nearby rural areas where cable or DSL Internet services are not available. This type of service uses high-powered, directional antennas to connect to fixed locations up to about eight miles away. Speeds can vary from as little as 256 Kbps to as much as 20 Mbps or more, depending upon distance and your ISP.
Network Types
With more network types than ever before, the CompTIA A+ 220-1001 and 220-1002 exams expect you to know the differences between LANs, WANs, and many more. See the following sections for a brief introduction to the types you need to know.
LAN
A local area network (LAN) is a group of networked computers within a few hundred meters of each other. LAN connections typically use wired Ethernet or Wi-Fi.
WAN
A wide area network (WAN) is a group of computers on multiple LANs connected with long-distance technologies. The Internet is a WAN.
PAN
A personal area network (PAN) is a short-range network typically using Bluetooth. It is used to interchange data between personal devices such as smartphones, tablets, and laptops.
MAN
A metropolitan area network (MAN) is a network larger than a LAN but smaller than a WAN. The term MAN is often used to refer to city-wide or campus-wide networks that use fiber optic or fixed-base wireless networks.
WMN
A wireless mesh network (WMN) connects wireless access points or network adapters to each other in such a way that each access point can forward data to the next access point or adapter. WMN technology is now available for use in homes and small offices to enable wireless coverage without dead spots or the use of conventional wireless repeaters.
REVIEW
Objective 2.7: Compare and contrast Internet connection types, network types, and their features
• Cable uses RG-59 or RG-6 cable and runs faster than DSL or dial-up.
• Traditional DSL uses phone lines, but newer types also incorporate cable or fiber optic lines for greater speed.
• Dial-up works over any conventional phone line and is by far the slowest Internet connection type.
• Fiber is used by many DSL and cable TV providers to improve speed and carry more information.
• Satellite Internet can provide service to remote locations outside the reach of other Internet service types, but it is much slower and can be affected by weather conditions.
• ISDN is largely outdated for Internet service, although it is still used for telephone service.
• Cellular connections work anywhere a smartphone is used but have data caps. A mobile hotspot or a smartphone with mobile hotspot support can share its connection with others wirelessly. A tethered connection is similar but uses USB.
• Line-of-sight wireless Internet uses directional antennas for connections, and is popular in rural and suburban areas outside the reach of DSL or cable.
• LAN = local area network
• WAN = wide area network
• PAN = personal area network
• MAN = metropolitan area network
• WMN = wireless mesh network
2.7 QUESTIONS
1. You are working with a client who needs Internet access but lives too far away from the city to use DSL or cable TV. They live on top of a hill. They need quick response and expect to use 15 GB or more of data per month. Which of the following Internet services would you recommend investigating?
A. Satellite
B. Cellular
C. FTTP
D. Line-of-sight fixed wireless
2. Your client has an old laptop with an RJ-11 port and an RJ-45 port built in. It does not have wireless capabilities. Without buying or renting another component, which of the following Internet connection types is this laptop ready to use?
A. DSL
B. Dial-up
C. Cable
D. Fiber
3. You are at a client’s location preparing to install an update to Windows. Their Internet connection goes down. Which of the following is the best choice to use to install the update immediately?
A. DSL
B. Dial-up
C. Mobile hotspot/tethering
D. ISDN
4. Your client wants to build a network that will connect locations in various parts of a medium-sized city with each other. Which type of network does the client want to create?
A. MAN
B. WAN
C. LAN
D. PAN
5. Your company is considering upgrading its DSL service to a faster service. Which of the following types of services is likely to be the fastest?
A. Cable
B. FTTN
C. Satellite
D. FTTP
2.7 ANSWERS
1. D Line-of-sight fixed wireless, if available, is the best choice because it has no data caps and, unlike satellite, has quick response (fast ping rate).
2. B The RJ-11 port indicates the laptop has a dial-up modem. Dial-up requires no additional equipment, only an account with a dial-up ISP.
3. C The mobile hotspot/tethering option supported by many smartphones would enable you to perform the update on-site.
4. A A metropolitan area network (MAN) connects locations in a single city that might be separated by some blocks of distance.
5. D Fiber to the premises (FTTP) will be the fastest, since the fiber is connecting directly to the home or office.

Objective 2.8 Given a scenario, use appropriate networking tools
Whether you build, repair, or troubleshoot wired or wireless networks, you need to understand how to use the networking tools covered in this section.
Crimper and Cable Stripper
For a patch cable, use stranded UTP cable matching the Cat level of your horizontal cabling. If you use cable with a lower Cat level than your existing cable, the network might run more slowly. The basic tool is a RJ-45 crimper (see Figure 2.8-1) with built-in cable stripper (also known as a wire stripper) and wire snips. Stranded and solid-core cable require different crimps; make sure you have the right kind. First, cut the cable square with the RJ-45 crimper or scissors; then use the built-in cable stripper to strip a half inch of plastic jacket off the end of the cable (see Figure 2.8-2). Once the cable is stripped, you’re ready to wire the connector.

FIGURE 2.8-1 Crimper

FIGURE 2.8-2 Properly stripped cable
Multimeter
The CompTIA A+ 220-1001 exam objectives include multimeters in networking tools. Multimeters are a bit of a Swiss Army knife for testing anything that carries a current. You can certainly use a multimeter to test whether a dead switch is connected to a good outlet, for example. In a pinch, you can use one to test cables you don’t have a regular tester for—but this is often tedious; a multimeter should be your last resort for testing network cable.
Tone Generator and Probe
Even in well-planned networks that don’t turn into a rat’s nest of cable, labels fall off and people miscount which port to label. In the real world, you may have to locate or trace cables and ports to test them.
Network techs use a tone generator and probe (see Figure 2.8-3). The tone generator connects to the cable with alligator clips, tiny hooks, or a network jack, and it sends an electrical signal along the wire. The tone probe emits a sound when it is placed near the cable carrying this signal.

FIGURE 2.8-3 Fox and Hound, a tone generator and probe made by Triplett Corporation
Cable Tester
A cable tester (shown in Figure 2.8-4) is used to verify the individual wires in TP cable are properly located and connected. When testing cables, be sure to test patch cables as well as cable runs in the walls. To do so, unplug the patch cable from the PC, attach a cable tester, and go to the communications room. Unplug the patch cable from the switch and plug the tester into that patch cable.

FIGURE 2.8-4 Typical cable tester
A specialized device used for cable testing is a time-domain reflectometer (TDR) tester such as the Fluke MicroScanner. A TDR measures impedance (resistance) in network cabling. If the tester measures any impedance, something is wrong with the cable.
Loopback Plug
A bad NIC can cause a length of network cable to appear to have failed. However, the NIC’s female connector is easy to damage. To determine if the card is bad, diagnostics provided by the OS or NIC manufacturer may include a loopback test that sends data out of the NIC to see if it comes back. A loopback plug (see Figure 2.8-5) is attached to the NIC’s RJ-45 cable port and it loops transmit lines back to receive lines. If the same data is received as sent, the NIC port works. If not, the NIC needs repair or replacement

FIGURE 2.8-5 Loopback plug
Punchdown Tool
With a typical horizontal cabling run, you’ll connect the work-area end to the back of a wall outlet with a female connector, and the telecommunications-room end will connect to the back of a patch panel’s female connector. You typically use a punchdown tool (see Figure 2.8-6) to connect the cable to a 110 block (also called a 110-punchdown block), which is wired to the female connector. The punchdown tool forces each wire into a small metal-lined groove (shown in Figure 2.8-7), where the metal lining slices the cladding to contact the wire.

FIGURE 2.8-6 Punchdown tool

FIGURE 2.8-7 Punching down a patch panel (left) and modular jack (right)
A work-area wall outlet (see Figure 2.8-8) consists of one or two female jacks, a mounting bracket, and a faceplate.

FIGURE 2.8-8 Typical work area outlet
Wi-Fi Analyzer
Which Wi-Fi channels are currently in use? How strong are the signals? To find out, you can use your Android or iOS smartphones with a free or paid Wi-Fi analysis app, available from many vendors on the Google Play or Apple App stores. Figure 2.8-9 illustrates how a typical Wi-Fi analysis app (Wifi Analyzer app for Android from Farproc) shows activity on 2.4- and 5-GHz bands. After you review the information, you might want to change the channel(s) used by your router.

FIGURE 2.8-9 Typical 2.4-GHz (left) and 5-GHz (right) router activity as captured by Wifi Analyzer from Farproc
REVIEW
Objective 2.8: Given a scenario, use appropriate networking tools
• A crimper is used to attach a connector to a UTP cable.
• A wire/cable stripper is used to remove the outer sheath from the cable to expose the UTP wires.
• A multimeter can be used to test individual cable strands.
• A tone generator and probe (also known as a toner or toner probe) is used to find the specific cable for labeling or testing.
• A cable tester tests specific wires in a cable.
• A loopback plug checks the condition of a NIC port.
• A punchdown tool is used to connect the wires in a cable to a 110-punchdown block.
• Wifi Analyzer is an app you can run on Android smartphones to display signal strength and network usage for Wi-Fi networks.
2.8 QUESTIONS
1. Your client is reporting problems with some of their network cables. Unfortunately, none of the cables are labeled and the client’s wiring closet is a mess. Which of the following should you use to help label the client’s cables?
A. Multimeter
B. Tone generator and probe
C. Crimper
D. Loopback plug
2. After labeling the cables for your client, you discover that one of the cables is connected to a workstation that can’t connect to the Internet. To help determine if the problem is actually the NIC, which of the following would you use?
A. Loopback plug
B. Multimeter
C. Cable tester
D. Tone generator and probe
3. Your client’s 2.4-GHz network once ran very quickly. However, several new houses have been built nearby and network performance is now very poor. Which of the following would help determine if different settings are needed?
A. Mobile hotspot
B. Cable tester
C. Punchdown tool
D. Wi-Fi analyzer
4. You are preparing to build some network patch cables for a Gigabit Ethernet network. Which of the following do you not need to use for this task?
A. Punchdown block
B. RJ-45 crimper
C. Wire stripper
D. Connector matching cable type
5. After an office remodeling project, some segments of your client’s wired network are slow. The exiting computers, switches, and routers were retained, but additional patch panels were installed. What might have gone wrong during the process? (Choose two.)
A. Incorrect Cat level in patch panels
B. Loopback plugs left connected to some workstations
C. Incorrect Cat level in patch cables
D. Hub used on some network segments
2.8 ANSWERS
1. B A tone generator and probe helps determine which wire is which.
2. A A loopback plug is attached to the NIC’s RJ-45 cable port and it loops transmit lines back to receive lines. If the same data is received as sent, the NIC port works. If not, the NIC needs repair or replacement.
3. D A Wi-Fi analyzer displays the activity on the 2.4-GHz band by channel and router name.
4. A A punchdown block is not used for patch cables. It is used for cables wired into a wall.
5. A C Using patch cables or punchdown blocks with Cat levels lower than the previous network hardware could slow down the network; for example, using Cat 5 (100 Mbps) instead of Cat 5e (1000 Mbps) hardware.




