
Software Troubleshooting
Domain Objectives
• 3.1 Given a scenario, troubleshoot Microsoft Windows OS problems
• 3.2 Given a scenario, troubleshoot and resolve PC security issues
• 3.3 Given a scenario, use best practice procedures for malware removal
• 3.4 Given a scenario, troubleshoot mobile OS and application issues
• 3.5 Given a scenario, troubleshoot mobile OS and application security issues

Objective 3.1 Given a scenario, troubleshoot Microsoft Windows OS problems
Microsoft Windows is, by far, the most common family of desktop operating systems you will be working with. Keeping Windows working is essential to knowledge workers, SOHO workers, and gamers alike. This objective helps you discover common symptoms and solutions.
Common Symptoms of Windows Problems
The following sections review the common symptoms of Windows problems that you are expected to know for the CompTIA A+ 220-1002 exam.
Slow Performance
Some of the causes for slow performance of Windows include
• Applications and processes consuming high CPU, RAM, or disk resources
• Running a system with limited RAM, requiring swapping of RAM contents to and from a hard drive
• Malware infestation
Limited Connectivity
The default IP addressing method used by Windows is to get an IP address from a DHCP server on the network. In a SOHO network, for example, the DHCP server is normally built into the router. When the DHCP server can’t be reached:
• Windows generates a random APIPA IP address (169.254.x.y, where x.y is the computer’s ID).
• An APIPA IP address enables local networking only.
An APIPA address isn’t routable, so computers cannot access the Internet.
Failure to Boot, No OS Found
If the system powers on and the POST succeeds, the computer will try to load an OS. Failure to boot can be caused by hardware, BIOS/UEFI firmware configuration, or Windows faults. The challenge is to determine which of these is the actual cause.
• If you’re staring at a dire error message such as Operating System not found or No boot device detected, keep in mind that the hard drive might not have proper connectivity and power.
Cross-Reference
• There are a variety of ominous messages that are less clear: a critical boot file or component is missing, corrupt, damaged, invalid, can’t be found, and so on. The specific critical files and components you should know for the exam are bootmgr and Boot Configuration Data (bcd), but this is far from a comprehensive list.
• Another possible cause is that the boot order in the UEFI/BIOS firmware is not configured correctly.
Cross-Reference
If simple hardware and system settings don’t appear to be the cause, it’s time to roll up your sleeves and use the repair and recovery tools that come with Windows.
Application Crashes
Some programs, often games rushed to market near the winter holidays, are released with code errors that render them unstable. These errors can produce symptoms such as a crash to desktop (CTD), freeze, or even an unexpected shutdown or restart. These improper shutdowns can cause other problems, including damage to open files and folders. Keep an open mind, because hardware or driver problems could also be the cause; think in terms of what the system is using.
Think about what could cause this scenario: your whole system freezes while you’re playing a huge, graphically intensive game that eats RAM like candy. For starters, it could be an error in the game code, an overwhelmed video card, a problem with the video card driver, a hardware problem on the video card, or a bad section of RAM. But what if the system didn’t freeze; what if it was just slow and jerky? After checking for malware, check other possibilities such as poor programming, or hardware that just isn’t powerful enough to run the game properly.
Blue Screens
A blue screen is a classic sign of a non-maskable interrupt (NMI), better known as the Blue Screen of Death or Stop error in Windows (see Figure 3.1-1). The BSoD appears only when something causes an error from which Windows can’t recover.

FIGURE 3.1-1 The Blue Screen of Death (BSoD) in Windows 10
Although this is a Windows error report, that doesn’t mean the cause is Windows itself. To find out the reason for the error, look up the error code.
Black Screens
A black screen (or blank screen) can have several causes:
• Lost connection to display; check display cable connections. On a laptop or tablet, try toggling between displays.
• Peripherals preventing proper startup; a reversed IDE cable on a system drive can stop the boot process before the display is working, as can a loose or missing video card.
• Graphics driver problems; try booting in Safe Mode or WinRE. If the system boots correctly in these modes, update the graphics driver.
• System in sleep mode; wake up the system.
Printing Issues
Some typical printing issues that have an operating system component include
• No connectivity
• Backed-up print queue
• Color prints in wrong print color
• Access denied
Cross-Reference
Services Fail to Start
Windows uses a wide variety of services, some of which start automatically when Windows starts, while others are started only when they are called upon to start by a specific application or circumstance.
When Windows services fail to start, the feature provided by the service fails. Depending upon the service, you might see an error message at system startup or the problem might not be noticed until you attempt to use a service. For example, if the services used for wireless networking don’t start, you can’t connect to a wireless network. Services might fail to start if they depend upon other services that didn’t start, if a specific user account is used to run the account has a different password than when the service was set up, or for other reasons.
Slow Bootup
Different Windows systems boot at different speeds, due to variables such as Windows version installed, the number of startup apps, processor type and speed, onboard RAM, and hard drive speed. This is normal. What isn’t normal is for a Windows system to boot up more slowly than usual. Some of the causes for slow bootup include
• Outdated drivers
• Lack of free space on system drive
• File fragmentation on system drive
• Faulty antivirus
• Malware
• Fast startup (ironic, isn’t it!)
• Programs with high startup impact running at startup
Slow Profile Load
When you select a user and log into that profile with Windows, the startup process runs at about the same speed on the same system. However, if it runs much more slowly than usual, consider one or more of the following possible causes:
• Malware
• System file corruption
• Profile corrupted
Common Solutions for Windows Problems
The solutions in the following sections can be used to solve multiple symptoms. Use the best practices troubleshooting methodology covered in Objective 5.1 of Domain 5.0 in Part I to evaluate the symptoms and choose the best solution(s) to try. Be sure to try one solution at a time until you find the answer.
Windows Repair and Recovery
Windows needs two critical files to boot: bootmgr and bcd. If they are damaged, you can fix them with a tool called bcdedit. But bcdedit isn’t just hanging out in Control Panel, so first we need to take a step back and look at where bcdedit lives and how you get there.
Windows Recovery Environment
The Windows Preinstallation Environment (WinPE or Windows PE) supports booting a limited graphical OS directly from the Windows installation media—one that includes troubleshooting and diagnostic tools alongside the installer. These troubleshooting, diagnostic, and repair tools are collectively (and confusingly) called the Windows Recovery Environment (WinRE or Windows RE) or the System Recovery Options (see Figure 3.1-2).

FIGURE 3.1-2 Windows 7 Recovery Environment main screen
In case your installation media is lost or damaged, create a system repair disc before you have problems. In Windows 7, go to Control Panel | System and Security | Backup and Restore and select Create a system repair disc.
Depending on your Windows version, a few different paths lead to WinRE:
• In any version, boot from the Windows installation media, recovery drive, or repair disc, and select Repair.
• Select Repair Your Computer on Windows 7’s Advanced Boot Options (F8) menu (see Figure 3.1-3).
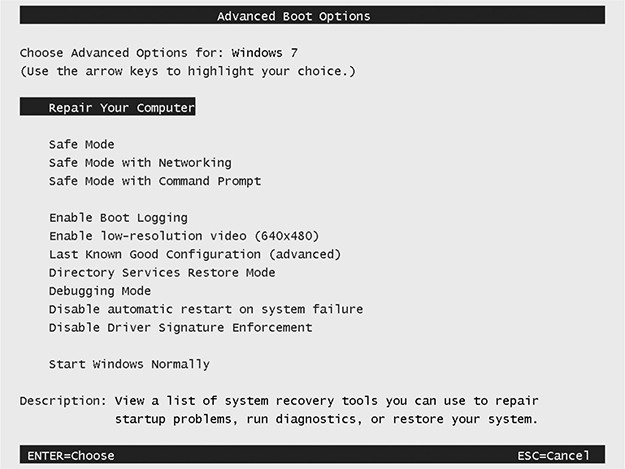
FIGURE 3.1-3 Selecting Repair Your Computer in the Advanced Boot Options menu
I recommend you access WinRE from the installation media because it works in each OS, doesn’t require an administrator password, and isn’t vulnerable to interference from malware or hard drive issues. No matter how you choose to access the Windows Recovery Environment, you have a few options:
• Startup Repair Performs a number of repairs on the Registry, critical boot, system, and driver files. Rolls back or uninstalls incompatible drivers and patches. Runs chkdsk and a RAM test. Saves diagnostic and repair details to srttrail.txt.
• System Restore Provides a simple way to return to an earlier restore point or snapshot.
• System Image Recovery Enables you to select and restore from a full system image. It includes an option to format and repartition disks so the restored system will get the same partitions that the backed-up system had.
• Windows Memory Diagnostic During the next reboot, the diagnostic tool checks your RAM for the sorts of problems that can cause Blue Screens of Death (BSoDs), system lockups, and continuous reboots. After the tool runs and your system reboots, you can use Event Viewer to see the results.
• Command Prompt A true 32- or 64-bit command prompt with useful recovery and repair tools (though it lacks a number of commands you would have at a regular Windows command prompt).
Windows 8 and above not only introduce a new look (the Metro/Modern UI) to WinRE, but offer some significant changes. First, a new Troubleshoot menu is now available with two new options:
• Refresh your PC Rebuilds Windows; preserves user files, settings, and Microsoft Store apps (but deletes all other applications)
• Reset your PC Removes all apps, programs, files, and settings and freshly reinstalls Windows
The Troubleshoot menu also has an Advanced options button, which is where you’ll find most of the utilities from the earlier version of WinRE (the Memory Diagnostics option is available from the command line). The Advanced options menu includes a link to your UEFI firmware settings if you have a UEFI motherboard.
With Windows 8/8.1/10, you can start WinRE from the logon screen:
1. Hold down either SHIFT key and click/tap the onscreen power button.
2. Continue to hold down the SHIFT key and click/tap Restart (Figure 3.1-4).
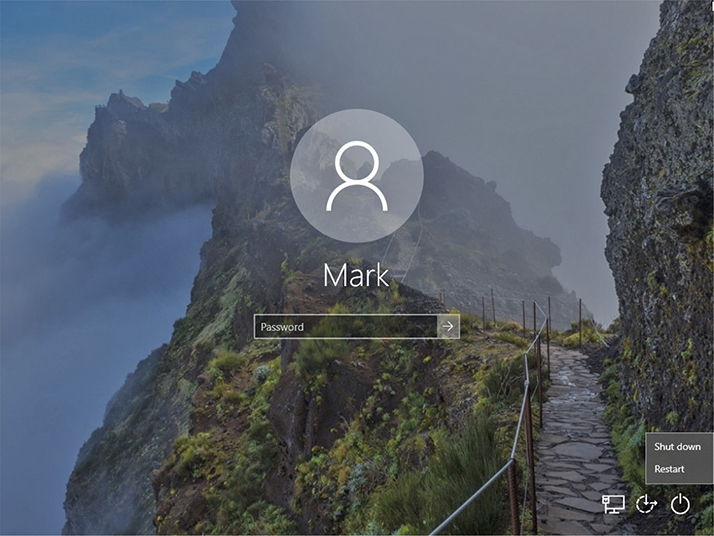
FIGURE 3.1-4 Selecting the Restart to WinRE option in Windows 10
3. Continue to hold down the SHIFT key until the WinRE dialog opens.
4. Click/tap Troubleshoot (Figure 3.1-5).

FIGURE 3.1-5 Selecting the Troubleshoot option in Windows 10 WinRE
5. Click/tap Advanced options (Figure 3.1-6).
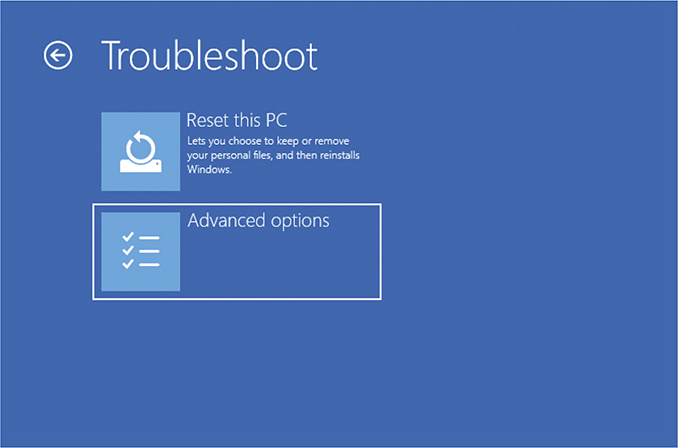
FIGURE 3.1-6 Selecting the Advanced options setting in Windows 10 WinRE
6. Click/tap Startup repair (Figure 3.1-7).

FIGURE 3.1-7 Running Startup Repair in Windows 10 WinRE
You can also create a recovery drive as well as a repair disc in Windows 8 and above.
In Windows 8 and up, go to Control Panel | Click large or small icons view | Recovery | Create a recovery drive. (Connect an empty USB flash drive with at least 16 GB capacity before continuing.) With Windows 8.1, you have the option to copy the files in the hidden recovery partition (if present) to the media as well.
Command-Line Recovery and Repair Tools
The CompTIA A+ exams won’t expect you to know everything about these utilities—the goal is for you to use them with higher level support—but you should know roughly what the tools listed in Table 3.1-1 do, how to access them, and some of the basic switches. Keep in mind that these commands are in addition to basic CLI commands such as copy, move, del, format, and so on.
TABLE 3.1-1 Useful Recovery and Repair CLI Commands

Defragment the Hard Drive
A fragmented system drive can slow down many aspects of Windows, including boot, user profile loading, and application loading. Fragmentation takes place when a file cannot be stored in a single contiguous location on a drive but must be stored in sections at different locations on the drive. A drive that stores frequently changed files or temporary files, such as the system drive used by Windows, is more likely to be fragmented than a drive that has few changes to its contents.
Although Windows automatically defragments drives as needed, you can run defragmentation manually if necessary.
Cross-Reference
Reboot
One of the simplest solutions to any type of Windows—or hardware—problem is rebooting the system. If Windows or application code is corrupt, devices are incorrectly set, or memory is being filled up, rebooting the system provides a clean workspace to use after restart.
• Be sure to close all apps before rebooting.
• If an app is still open, this prevents the system from rebooting. Windows displays a warning if there are open files when you select the reboot option, so you can choose to close them (recommended) or force a reboot.
• Forcing a reboot could cause the app to become corrupted, or you could lose unsaved data.
Kill Tasks
If too many tasks (including apps and services) are open, Windows can slow down. To speed up Windows and important tasks, shut down tasks you don’t need. If you cannot shut down an app normally, or if you need to close a task, use the Task Manager in the Windows GUI or use taskkill from the command line.
Cross-Reference
Restart Services
If a service has stopped running or is not working properly, open Services, select the service you want to restart, stop it, and restart it. You can also use the Services dialog to start a service that failed to start automatically.
Update Network Settings
To force Windows to check for an IP address from a DHCP server, open a command prompt and run ipconfig /release, followed by ipconfig /renew. If a DHCP server is now available, Windows will receive a normal IP address and you will be able to connect to the Internet as well as to other computers on your network.
To enable Windows to have connectivity without an IP address, you can set up an Alternate Configuration in the Local Area Connections properties for the connection. The default is to use Automatic Private IP Addressing (APIPA). Click the User configured radio button instead and enter the information needed:
• IP address
• Subnet mask
• Default gateway
• Preferred DNS server
• Alternate DNS server
• Preferred WINS server
• Alternate WINS server
Be sure to use an IP address that is not normally assigned by the DHCP server. Each computer in the network needs a unique IP address. This information will be used to set up a network connection if the DHCP server cannot be reached.
Cross-Reference
Reimage/Reload OS
The ultimate solution for a defective Windows installation is to restore the original Windows image from an image backup. This step should be held back as a last resort, as it results in all system updates, application updates, and user data on the system being wiped out. If it isn’t backed up, it’s gone!
Before restoring the original Windows image, use other methods to install a fresh copy of Windows. These include
• Repair installation (reload OS); preserves your apps as well as data
• Reset this PC (Windows 10); choose Keep Your Personal Files to keep your data
• Windows refresh (Windows 8/8.1); keeps your personal files
With these options, you can keep your existing data and, in some cases, apps.
Cross-Reference
Roll Back Updates
If Windows malfunctions can be traced back to right after an update was installed, the update is almost certain to be the cause. System Restore is the key to rolling back updates that don’t work, as it records the system configuration as part of a restore point so you can go back to it if an update fails.
Cross-Reference
Roll Back Device Drivers
Device drivers are the “glue” that connects your hardware with Windows. Faulty device drivers can prevent devices from working or can affect Windows in other ways. Device drivers are installed as part of initial device setup, and might be updated by Windows or manually by the user.
If Windows starts malfunctioning after a device is installed or its drivers are updated, the device drivers might be at fault. To roll back device drivers, open Device Manager, right-click the device and choose Properties, click the Driver tab in the Properties dialog box, and click Roll Back Driver (if available). The previous version of the device driver will be installed.
If the device is newly installed or has not had a driver update, the Roll Back Driver button won’t be available. In that case, use Update Driver to check for updated drivers that might work better.
Cross-Reference
Apply Updates
Although updates can cause problems, more often than not, updates can resolve problems with Windows or drivers. Windows Update is the place to check for updates.
Cross-Reference
Repair Application
Windows apps can become corrupt for a variety of reasons, including disk errors, poor coding, errant updates, or apps left open when Windows is shut down or restarted. To get a faulty application working again, repair the application.
You can repair an application through Control Panel’s Programs and Features applet. To start the process, click the application, then click Uninstall/Change. If a repair option is available, select it to repair the app. If an app lacks a repair option, uninstall the app and reinstall it instead.
In Windows 10, you can also open Apps & features in Settings, choose an app, and click Modify to start the process.
Update Boot Order
If Windows can’t boot, the problem might be the boot order in the system UEFI/BIOS firmware.
• Check your external ports (USB, Thunderbolt, eSATA, and so on) for errant drives.
• Check optical drives and flash card readers as well.
• Disconnect, eject, or unplug drives you don’t need for booting.
• Confirm your boot sequence is correct, and check settings to boot from USB or other sources.
• Check power and data cables for the OS drive.
• Check the appropriate settings if your system uses RAID or multiboot.
If you want the fastest boot possible, put your system drive as the first boot device. However, keep in mind that if you occasionally boot from an OS disc or USB drive or run other self-booting drives, you need to change the boot order again to use them.
Cross-Reference
Disable Windows Services/Applications
Sometimes, Windows services and applications can slow down your system or interfere with other apps you’re using. Services run in the background and are used for network connections, printing, encryption, device installation, and many other tasks. To view Microsoft and third-party Windows services and disable unwanted services, open Services.msc or open the Services node from the Microsoft Management Console.
To disable unwanted third-party services, use the Services tab in the System Configuration utility (aka MSConfig and msconfig). First, check the Hide all Microsoft services checkbox, then click Disable all, then clear the checkboxes for the services you want to keep (see Figure 3.1-8). When you restart, the checked services won’t run.

FIGURE 3.1-8 Disabling third-party services with MSConfig
Windows features are optional components such as Hyper-V virtualization service, Windows Subsystem for Linux, Internet Information Services, and more. To disable unwanted Windows features, open Windows Features from Control Panel (see Figure 3.1-9) and clear the checkboxes for the features you don’t need. Click OK, and restart the system if prompted.

FIGURE 3.1-9 Selecting Windows features
Disable Application Startup
Apps that run at startup can eat up memory and processor cycles, and sometimes can interfere with other apps. To disable application startup in Windows 7, start MSConfig, click the Startup tab, and clear the checkbox for each startup app you want to disable.
To disable a startup app in Windows 8 or later, open the Task Manager, click the Startup tab, right-click the app, and choose Disable (see Figure 3.1-10). Disabling apps that have a High status in the Startup impact column has the biggest potential to improve startup time.

FIGURE 3.1-10 Disabling a startup app in Windows 10
Safe Boot
Safe boot, better known as Safe Mode, offers a way to fix a lot of problems that prevent a system from booting normally…by loading only essential services. If you can boot your system in Safe Mode, but not normally, it means that at least one startup app or service that is normally run is causing your startup headaches. In Safe Mode, you can use Device Manager and other tools to locate and fix problems. You can also choose to start your system in Safe Mode with Networking services enabled or to start your system in Safe Mode with the command prompt rather than the Windows GUI.
To choose from these or other startup options with Windows 7, press the F8 key repeatedly after the POST messages but before the Windows logo screen until the Advanced Boot Options menu appears (see Figure 3.1-11). To go directly to Safe Mode, press the F5 key at boot up.
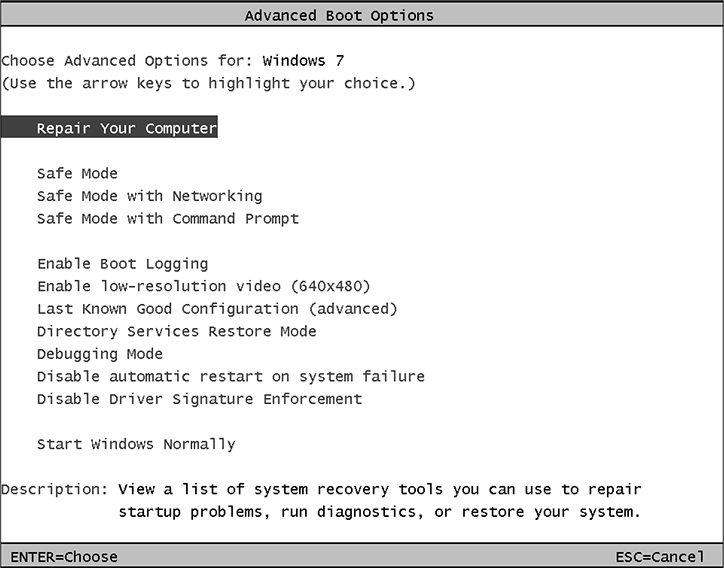
FIGURE 3.1-11 The Advanced Boot Options menu in Windows 7 provides access to Safe Mode and related startup modes.
To start your system in Safe Mode with Windows 8/8.1/10, boot the computer. At the login screen:
1. Hold down the SHIFT key.
2. Click the Power button on the login screen.
3. Click Restart.
4. Click Troubleshoot | Advanced Options | Startup Settings.
5. Click Restart, and then the Startup Settings menu appears (see Figure 3.1-12).

FIGURE 3.1-12 The Startup Settings menu in Windows 10. Press the F10 key to switch to the second screen of choices (inset).
Choose one of the following:
• Safe Mode Starts Windows with basic/default drivers, settings, and services. Screen resolution is limited to 800 × 600 (7) or 1024 × 768 (8/8.1/10). If the system is repeatedly and unintentionally booting into Safe Mode, you may need to deselect the Safe boot or Boot to Safe Mode check box (see Figure 3.1-13) in the System Configuration utility.
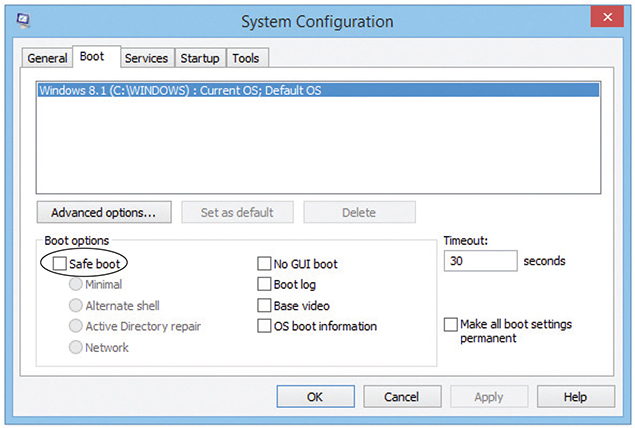
FIGURE 3.1-13 Uncheck Safe boot if the system is repeatedly and unintentionally booting into Safe Mode.
• Safe Mode with Networking Identical to Safe Mode, but with networking support. If your system boots into regular Safe Mode fine but fails to boot into Safe Mode with Networking, check network devices for driver issues.
• Safe Mode with Command Prompt Boots directly to a command prompt instead of the Explorer GUI, which may succeed even if you can’t successfully boot into regular Safe Mode due to buggy video drivers or corrupt Windows GUI files such as explorer.exe. You can load other GUI tools that don’t depend on Explorer. All you have to do is enter the correct command. For instance, to load Event Viewer, type eventvwr.msc at the command prompt and press ENTER.
Rebuild Windows Profiles
A corrupted user account profile prevents you from logging in to your system. There are two ways to fix this problem:
• Fix the user profile settings in the Registry with Regedit
• Create a new user account and copy the files from the corrupt one to the new one
REVIEW
Objective 3.1: Given a scenario, troubleshoot Microsoft Windows OS problems Common symptoms indicating Windows OS problems include
• Slow performance
• Limited connectivity
• Failure to boot
• No OS found
• Application crashes
• Blue screens
• Black screens
• Printing issues
• Services fail to start
• Slow bootup
• Slow profile load
Common solutions to Windows OS problems include
• Defragment the hard drive
• Reboot
• Kill tasks
• Restart services
• Update network settings
• Reimage/reload OS
• Roll back updates
• Roll back device drivers
• Apply updates
• Repair application
• Update boot order
• Disable Windows services/applications
• Disable application startup
• Use Safe boot (Safe Mode)
• Rebuild Windows profiles
3.1 QUESTIONS
1. To change the boot order, which of the following is necessary?
A. Start Windows in Safe Mode
B. Restart the system and open the UEFI/BIOS firmware setup
C. Use the Task Manager
D. Use MSConfig
2. Which of the following is the best way to recover from a bad device driver update?
A. Roll back the system
B. Restart the system and open UEFI/BIOS firmware setup
C. Roll back the device driver
D. Restart in Safe Mode
3. Your client needs to restart her system to solve a problem. Which of the following should she do first?
A. Create a registry backup
B. Run System Restore
C. Create a full system backup
D. Unplug USB drives
4. Your personal computer used to load your desktop in about ten seconds. Now it takes ten minutes. Which of the following is not a likely cause?
A. Too many tasks running
B. Malware
C. System file corruption
D. User profile corrupted
5. You need to start your computer in Safe Mode. Which of the following do you need to know to do this?
A. Your APIPA network address
B. Your screen resolution
C. The version of Windows you use
D. The location of the temporary files
3.1 ANSWERS
1. B You must use the UEFI/BIOS firmware dialog to change the boot order.
2. C Rolling back the device driver will not affect other parts of the system, so it is the preferred method.
3. D USB drives that are plugged in could prevent the system from restarting.
4. A The other items listed are likely causes; the number of tasks running has a small impact on load time, but not as much impact as the others.
5. C You need to know the version of Windows so that you can choose the proper method of starting in Safe Mode.

Objective 3.2 Given a scenario, troubleshoot and resolve PC security issues
Security issues, regardless of the effectiveness of e-mail filters and anti-malware apps, are likely to be around for a long time. In this objective, you will learn about common symptoms of PC security issues, from pop-ups and slow performance to invalid security certificates and access denied errors. This objective sets the stage for the upcoming Objective 3.3, where you learn how to remove malware, a frequent cause of security issues.
Common Symptoms of PC Security Issues
The following sections describe how to identify common PC security problems.
Pop-ups
Pop-ups, or browser windows that pop up when you visit a site or click elements, used to be very common on websites. Many of these are simple ad windows, but others are malware that emulate alerts from the OS in an attempt to infect your system, sometimes with drive-by downloads, and often attempt to circumvent efforts to close them.
Abuse of automatic pop-ups led to the use of pop-up blockers, which have since been integrated directly into browsers; sketchy modern pop-ups need to trick the user into clicking something to open the pop-up.
Browser Redirection
Browser redirection, in which an incorrect URL is opened when the user clicks a legitimate link, is a common sign of a malware infection that has overwritten your hosts file. A variation on browser redirection is when your normal home page is changed to a different home page, a malware action known as home page hijacking.
To stop browser redirection, use anti-malware apps. Keep your browser updated and check whether your browser has an option to lock your home page.
Security Alerts
Systems with real-time protection from malware can display security alerts when malware is detected. However, false security alerts are caused by malware embedded in a website. Some of these alerts can look remarkably like actual security alerts, so how can you tell the difference?
• Actual security alerts use the anti-malware app installed on your system; fake security alerts use names that are similar to, but not the same as, actual anti-malware apps such as Windows Defender, AVG Antivirus, and so on.
• Fake security alerts look like malware scans, but are displayed in a web browser window. Actual malware scans run in their own window.
• Actual real-time security alerts don’t take over your screen.
Figure 3.2-1 shows a fake security alert in a browser tab. If you were to click the alert, the next step would prompt you to pay for the full version of the app to “clean” your system. Actually, only your wallet would be cleaned (of money)—the system was not infected and there’s nothing to clean up.
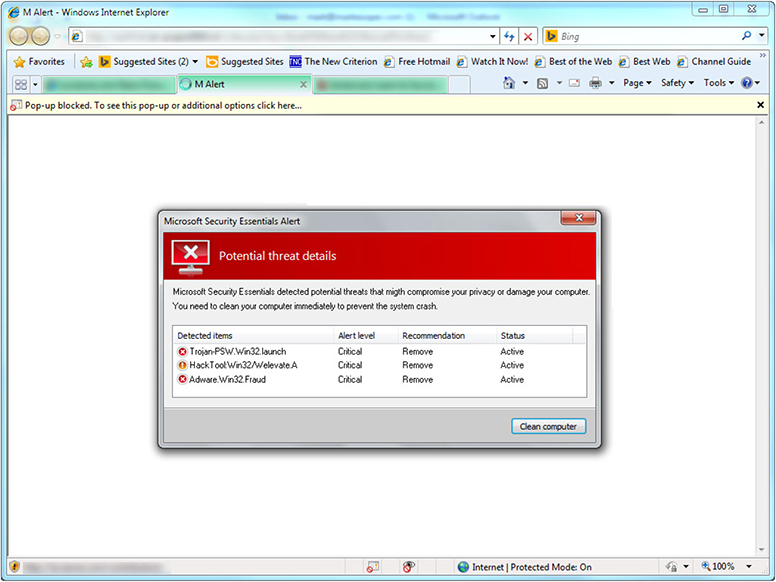
FIGURE 3.2-1 Fake security alert in a browser tab
Figure 3.2-2 shows an actual malware scan performed using Windows Defender that found actual malware. You would need to click the Show details link to see the malware discovered.

FIGURE 3.2-2 Windows Defender preparing to clean a PC of malware
Figure 3.2-3 shows a malware warning displayed by Window Defender’s real-time protection module.
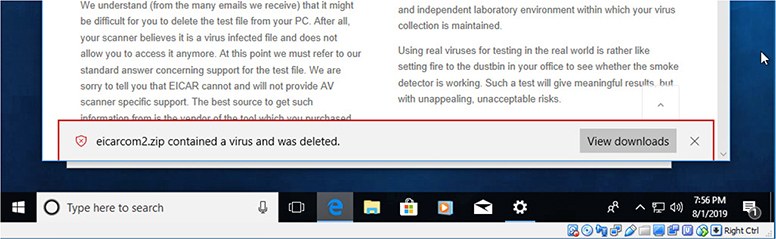
FIGURE 3.2-3 Windows Defender’s real-time protection stops malware from infecting a system.
To get rid of a fake security alert like the one shown in Figure 3.2-1, close the browser window/tab, and if you can’t close it the normal way, use the Task Manager or a similar tool.
Slow Performance
Computers can slow down as more programs are opened, especially if you have marginal amounts of RAM installed for the workload. However, if a system is abnormally slow, sluggish, or prone to crashes and lockups given the programs you have open, especially if it persists after you close busy programs or reboot, it’s time to scan for malware.
Internet Connectivity Issues
If a system loses its Internet connection but the network itself and the network hardware appear to be working, malware may be the culprit. To prevent users from accessing anti-malware apps, online scanning, or updates, malware often disables a system’s Internet connection.
PC/OS Lockup
Computer or operating system lockups can have many causes, but if you rule out potential causes such as overheating, power quality, file corruption, or user error, suspect a malware infection.
Cross-Reference
Application Crash
Similar to lockups, application crashes can have many causes, but if you rule out potential causes such as overheating, power quality, file corruption, or user error, suspect a malware infection. Before assuming a malware infection, try to repair the application.
Cross-Reference
OS Updates Failures
Operating systems are actually the first line of defense against malware, and many of the updates to Microsoft Windows in particular are rolled out to patch weaknesses to help stop malware. Thus, it’s not surprising that malware can interfere with OS updates.
If you are unable to run Windows Update or other OS update routines and are unable to repair those routines, it’s time to check for malware.
Rogue Antivirus
So-called “rogue antivirus” apps are a sinister development of the fake security alerts discussed earlier in this objective. Like them, they pretend to be antivirus apps. The difference is that some of them directly threaten data by encrypting user information and demanding a ransom payment. Malware that appears or pretends to be beneficial while attacking your system or data is a Trojan horse.
Spam
Attackers and scammers send tens or hundreds of millions of spam e-mails (often from a botnet or compromised servers) just to exploit the fraction of a fraction of a percent of recipients who fall for the bait. Some of these are simple ads for real products of questionable value, but many are outright attempts to scam, steal personal information, or deliver malware. Limit spam by not posting your e-mail address on the Internet and by using an e-mail service with robust spam filtering. Also consider blocking senders, unsubscribing from mass e-mails, reporting spam, and manually moving unwanted e-mail to your spam folder.
File Issues
Renamed system files, disappearing files, and files that have unexpected file permission changes may indicate that malware is modifying or destroying files and data.
E-mail Issues
If you receive an e-mail (CompTIA refers to this as email) response from a contact who you haven’t e-mailed or receive an undeliverable mail notification referencing a message you didn’t send, that indicates someone’s e-mail account has been hijacked. CompTIA describes these symptoms of hijacked e-mail accounts with two unwieldy phrases: responses from users regarding e-mail and automated replies from unknown sent e-mail. When either of these takes place, it’s time to change your e-mail password.
Access Denied
Malware might prevent you from accessing its files to prevent file deletion. If you get an “access denied” message when trying to delete malware-infected files, you could try to take over ownership of the files. However, it is usually easier to bypass the normal file management processes to delete those files.
In Windows, open a command prompt and use the attrib command to remove the attributes from the file (replace infected_filename.ext with the actual filename):
attrib -r -s -h infected_filename.ext
Or, boot the system with a malware-removal disc or USB drive that includes a file manager.
Invalid Certificate (Trusted Root CA)
Digital certificates are used by web browsers and operating systems to validate websites and applications (in other words, to prove that the alleged owner or developer is actually valid). Digital certificates are issued by a certificate authority (CA), such as Symantec, Comodo, IdenTrust, and others.
A digital certificate error can be caused by various issues, but one possible cause is that malware has attempted to sneak a bad certificate onto your system or has changed the system date (a date mismatch is the cause of many certificate errors).
System/Application Log Errors
Windows creates various types of logs that can be viewed in Event Viewer. To see errors that might be caused by malware, open Event Viewer from the Microsoft Management Console (MMC) and filter for errors.
In macOS, open the Console app and use it to filter for errors and faults. In Linux, open a terminal session and use dmesg to view kernel messages.
Cross-Reference
REVIEW
Objective 3.2: Given a scenario, troubleshoot and resolve PC security issues Common symptoms indicating PC security problems include
• Pop-ups
• Browser redirection
• Security alerts (real vs. fake)
• Slow performance
• Internet connectivity issues
• PC/OS lockups
• Application crash
• OS updates failures
• Rogue antivirus
• Spam
• Renamed system files
• Renamed or disappearing files
• Unexpected file permission changes
• Hijacked e-mail
• Access denied
• Invalid certificates
• System/application log errors
3.2 QUESTIONS
1. If your browser is displaying pop-up windows, what should you do first?
A. Run a scan with your anti-malware app
B. Update the OS
C. Check browser settings
D. Use a different browser
2. You have just returned from a business trip during which you temporarily misplaced your smartphone and laptop. You also used a public library’s computer to check e-mail. You can’t log in to your e-mail now that you’re back in the office. What should you do?
A. Contact your e-mail vendor for a new password
B. Scan for malware
C. Quarantine your system
D. Restart your system in Safe Mode
3. You have received an urgent e-mail from a casual acquaintance stating they need $500 to get home after a serious car breakdown. What should you do?
A. Wire the money
B. Unfriend your friend
C. Reply to the e-mail
D. Assume it’s spam
4. Your browser is displaying a security alert that there are several malware apps running on your system. Which of the following should you do?
A. Note the name of the malware and then scan for it
B. Close the browser window
C. Follow the instructions on-screen
D. Panic
5. Your favorite application has stopped working. After investigation, you have determined that your system was infected with malware. How can you get your application working after you remove the malware? (Choose two.)
A. Update your OS
B. Reboot
C. Repair the application
D. Restart in Safe Mode
3.2 ANSWERS
1. C Your browser’s built-in pop-up protection is probably turned off, so turn it on.
2. A Change your password so others can’t use your e-mail.
3. D It’s probably spam. Use other means of contact to check with anyone before sending them money or confidential information.
4. B A security alert in a browser window is a fake, so close the browser window.
5. B C Rebooting might get your app working again. If not, use the repair application feature in your operating system.

Objective 3.3 Given a scenario, use best practice procedures for malware removal
CompTIA recommends a seven-step process for malware removal. This objective covers the process.
Best Practice Malware Removal Process
Despite your best efforts, your computer or a computer you are responsible for is likely to become infected with malware. To get rid of computer viruses or other malware infections, follow the best practice steps in this section.
Step 1: Identify and Research Malware Symptoms The first step is to recognize (identify) that a potential malware outbreak has occurred and act swiftly to keep it from spreading. Network monitoring, security event logs, and user reports may all tip you off to the malware symptoms described in the previous objective. Many networks employ software such as the open source PacketFence to monitor network traffic and automatically isolate systems that start sending suspicious packets.
Step 2: Quarantine the Infected Systems To quarantine a computer, take it off the network by disconnecting the network cable or disconnecting/disabling its Wi-Fi radio. Depending on how the malware spread, you may need to take additional steps to keep other systems from contracting it. For example, don’t allow removable drives or media from that system to be connected to other systems unless the drives or media are scanned for malware first.
Step 3: Disable System Restore (in Windows) Once you’re sure the machine isn’t capable of infecting other systems, disable System Restore to keep the malware from being included in (and potentially restored later from) saved restore points. To turn off System Restore in Windows, go to Control Panel | System applet | System protection. In the Protection Settings section, you’ll need to individually select each drive, click Configure to open the System Protection dialog, and select Turn off system protection.
Step 4: Remediate the Infected Systems Follow these best practices to remediate a system:
• Update the anti-malware software If you have removed the system from the network, you need to use different methods to update the anti-malware software than usual. Most providers have downloadable files that can be copied to media and then used on the infected system.
• Scan and use removal techniques (Safe Mode, Windows Preinstallation Environment) Once you get to a clean boot environment, update your anti-malware software and definitions, run its most comprehensive scan, and remove any malware it discovers. Next, repeat this process for all removable media exposed to the system, and any other machine that might have received data from it.
Remediation sometimes requires a third step: Repair any damage done to the system.
If you can’t start Windows after the malware scan is finished, you need to boot to the Windows Preinstallation Environment and use the Windows Recovery Environment/System Recovery Options.
These recovery options include useful remediation utilities such as Startup Repair, System Restore, System Image Recovery, Refresh, and Command Prompt. Run the appropriate option for the situation, and you should have the machine properly remediated in a jiffy.
Step 5: Schedule Scans and Run Updates One of the reasons that systems become infected is because anti-malware updates and scans were disabled or never set up. Set up a schedule for scans and run updates.
Step 6: Enable System Restore and Create a Restore Point (in Windows) By creating a restore point after re-enabling System Restore, you establish a new baseline to return to after cleaning up the system.
Step 7: Educate the End User Even the best anti-malware suite is imperfect—ideally it forms a rarely tested second line of defense. The first line of defense is educating your users—nobody wants their system infected with malware. Teach users to be cautious with e-mail from senders they don’t recognize and to never click an attachment or URL in an e-mail unless they are 100 percent certain of the source. Explain the dangers of questionable websites (for example, warez websites distribute illegal copies of software that are often laden with malware) and teach your users how to react when a site is trying to manipulate them or triggers their browser’s built-in attack site warning (see Figure 3.3-1).

FIGURE 3.3-1 Attack site warning
Remind users to
• Install, use, and update anti-malware programs regularly.
• Enable automatic updates for anti-malware programs.
• Install apps only from trusted sources.
• Avoid untrusted software sources (warez, registry cleaners from obscure websites).
• If a malware attack takes place, analyze weaknesses in prevention and work to improve user education.
REVIEW
Objective 3.3: Given a scenario, use best practice procedures for malware removal Removing malware involves a seven-step process:
1. Identify and research malware symptoms.
2. Quarantine the infected systems.
3. Disable System Restore (in Windows).
4. Remediate the infected systems:
a. Update the anti-malware software.
b. Scan and use removal techniques (Safe Mode, Windows Preinstallation Environment).
5. Schedule scans and run updates.
6. Enable System Restore and create a restore point (in Windows).
7. Educate the end user.
3.3 QUESTIONS
1. After updating anti-malware software and scanning/using removal techniques, what is another step that might be necessary in remediation?
A. User education
B. Repairing damage from malware
C. Re-enabling system restore
D. Creating a restore point
2. Which of the following is a reason to use a clean boot environment in removing malware?
A. Makes computer run faster
B. Makes user education easier
C. Prevents reinfection
D. Helps prevent malware from interfering with removal
3. When should you enable System Restore and create a restore point?
A. Before removing malware
B. Before scheduling scans and running updates
C. After scheduling scans and running updates
D. As the last step in the process
4. As part of user education, you have taught your users to install apps only from trusted sources. Which of the following is not a trusted source?
A. A website offering warez
B. Valve’s Steam service
C. Apple App Store
D. Microsoft Store
5. Determining that a system has probably been infected with malware is which step in the malware removal process?
A. Step 7
B. Step 2
C. Step 3
D. Step 1
3.3 ANSWERS
1. B Software can be damaged by malware, so repairing it may be a part of remediation on some systems.
2. D Clean booting or booting from a USB or optical disc before running malware removal helps prevent malware from running and interfering with the removal process.
3. C The restore point needs to remember the system configuration after it’s been remediated and protected against threats.
4. A Warez is untrustworthy, illegal, and may be filled with malware.
5. D Determining that a malware infection is present is included in Step 1. Identify and research malware symptoms.

Objective 3.4 Given a scenario, troubleshoot mobile OS and application issues
Mobile operating systems and applications have some issues in common with desktop and laptop operating systems and applications, but because of how mobile devices work, some OS and application issues are unique. In this objective, you learn how to deal with them.
Common Symptoms of Mobile OS and Application Issues (with Solutions)
The following symptoms commonly plague mobile devices, operating systems, and applications. After each symptom is provided, you will also learn some typical solutions.
Dim Display
Mobile devices have a brightness control that you set to auto mode or control manually. A dim display might be a panel problem, but you need to rule out display settings. Follow these steps:
1. Disable auto-brightness and manually change from the dimmest to brightest setting.
2. If adjusting the setting doesn’t cover an appropriate range, suspect the display panel.
3. If it does cover an appropriate range, suspect auto-brightness and try the following:
a. Ensure front-facing sensors and cameras are clean and unobstructed.
b. Check the environment for bright lights that may confuse the sensor.
c. Perform a soft reset to clear up issues with apps that tinker with system brightness.
Intermittent Wireless
The biggest wireless connectivity problem for mobile devices is a weak signal caused by distance or interference; symptoms are dropped connections, delays, slow transmission speeds, and frequent no-signal indicators. There’s not much you can do on the device end except move. Cellular signal boosters exist, but they’re best in a fixed low-signal location.
Some tricky connectivity problems can occur despite a good signal:
• An overloaded network is common when large public events or emergencies cause a surge in network use, leaving users with a good signal unable to place calls, send texts, or transfer data.
• You may experience slow data speeds while roaming just because the carrier of the network you are roaming on limits data rates for nonsubscribers.
• Exceeding data usage limits your carrier sets can lead to slow data speeds, overage charges, or a hard data cap. To resolve this last problem, which CompTIA calls data transmission over limit, either pay your carrier to raise the data limits or monitor data use and disable cellular data (see Figure 3.4-1) as needed.
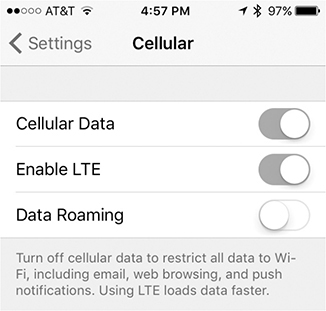
FIGURE 3.4-1 Option to disable cellular data in iOS
Symptoms depend on how the carrier handles the overage, so check these limits when dealing with unexplained good-signal connection problems.
No Wireless Connectivity
If you have no cellular or Wi-Fi connectivity, regardless of your location relative to cell towers or Wi-Fi APs, the problem might be with your mobile device itself: Airplane mode, when enabled, turns off all wireless connections. Airplane mode, developed originally to enable fliers with mobile devices to keep them on without interfering with navigation systems, can be easily triggered on some mobile devices.
To determine if your device is in Airplane mode, look at the status bar on your smartphone, tablet, or laptop for an airplane icon. To restore connection, turn off Airplane mode and reconnect to a Wi-Fi AP (cellular reconnection is automatic).
No Bluetooth Connectivity
Bluetooth connectivity is also affected by Airplane mode, but Bluetooth can also be turned off manually.
To restore connection with Bluetooth devices, turn off Airplane mode (if applicable), turn on Bluetooth, and see if your previous pairing is still active. If not, re-pair your mobile device with the other device (headset, speaker, keyboard, mouse, and so on).
Cannot Broadcast to External Monitor
Here are a few tried-and-true things to check when your mobile device cannot broadcast to an external monitor:
• Is your input source correct on the external monitor?
• Do you have the right adapter for your device? Make sure you have an adapter known to work for your device.
• Does your adapter need its own power source?
• For HDMI: Did the HDMI recognize your device and your external monitor? Try resetting one or both devices to give the HDMI time to see connections and set up.
• For laptops: Did you use the correct key combination to switch to the external display or to mirror the built-in display to an external display? There is no standard keystroke, and some systems require the user to press the FN key along with the function key toggle, while others don’t.
• For HDTVs: Did you make sure the display is set to the correct port? Most HDTVs have two or more HDMI ports.
Touchscreen Nonresponsive or Responds Inaccurately
If the touchscreen is nonresponsive or responds inaccurately, consider the following:
• Touch sensors can register an accidental touch, often where you grip the device. Show the user how the sensors pick up an accidental touch, and how to hold the device to avoid them.
• Sometimes you can restore responsiveness by cleaning the touchscreen with a dry microfiber cloth to get rid of fingerprints, dust, dirt, grease, and so on.
• Performance issues can make a touchscreen inaccurate, sluggish, or inoperable. Clues include incorrect time, jumpy lock screen or wallpaper animations, out-of-date weather or stock widgets, slow or no response to hardware buttons, failure to receive texts or calls, and so on. If you can’t regain control after a few minutes, perform a soft reset and see if the touchscreen works.
• If a soft reset doesn’t work, look online to see if the device has a hidden diagnostics menu or service menu. You reach these by typing a code into the device’s dialer or by holding specific buttons while the device boots. A touchscreen diagnostic makes hardware problems obvious. Some Android and Windows Phone devices may have a touchscreen calibration routine in either the primary OS settings menu or a hidden device menu.
• If the touchscreen is still not responding properly, look for signs it has physical damage and needs service or replacement. You can ask the device user whether it was dropped or exposed to liquid, but don’t expect much; the cause is often embarrassing. Even if the glass is fine, impacts can break internal connections, so check for scuffs and dings. Liquid can cause shorts and disorient sensors, so check for liquid contact indicator (LCI) stickers (see Figure 3.4-2) on the battery or in the battery compartment and external ports; look up additional locations online.

FIGURE 3.4-2 Pristine LCI sticker (top) and LCI sticker after absorbing a drop of water (bottom)
• A poorly applied protective cover can affect touchscreen responsiveness. If the protective cover is peeling away or has air bubbles, remove it and use a different one.
Apps Not Loading
If a mobile device app is not loading, try these steps:
1. Start with a soft reset.
2. If the app still won’t load, it may be incompatible with some combination of the mobile device’s hardware, OS version, or vendor/carrier customizations to the OS.
3. Confirm the device meets the app’s hardware requirements, including RAM, storage space, processor type, specific sensors or radios, required camera features, and so on.
Slow Performance
Add the following to what you already know about poorly performing mobile devices:
• A mobile device with performance issues will often be running hot, but a hot device could be using thermal throttling to protect the device’s CPU from heat damage; see if performance picks up as it cools.
• Performance issues can be caused by storage space being almost filled up on a mobile device, making it struggle to efficiently save data or install apps; free some space and see if the problem resolves.
• Performance can also suffer when there are too many apps running at the same time, eating up RAM.
• A soft reset often resolves the immediate symptoms, and you can use the device settings or third-party apps to measure the device’s performance, separate hardware from software causes, and decide whether you should take the device to an authorized repair facility.
Unable to Decrypt E-mail
Securing an e-mail requires encrypting it—scrambling it with a unique key using some standard, such as Pretty Good Privacy (PGP) or Secure/Multipurpose Internet Mail Extensions (S/MIME)—so that only the recipient can decrypt or unscramble it with software and a related unique key. Each key is a string of bits that software uses to encrypt or decrypt data.
In practice, the most common reason a mobile device is unable to decrypt an e-mail is that the e-mail client or app doesn’t support the encryption standard used to encrypt the message. The fix is a plugin or a new e-mail client or app:
• Download a plugin or e-mail client or app that supports this encryption method and follow any steps to configure the client to use it.
• Provide the e-mail client with a decryption key. Some standards require manual key exchange; contact the sender to exchange keys. Other standards may exchange keys automatically if you meet certain criteria, such as being part of the same organization.
Extremely Short Battery Life
Modern mobile devices use Li-ion batteries, and it’s important to manage them well to ensure the device lives a long life. Before good management can help, you need to meet the user’s power needs. Know how long a given user’s device needs to last on a charge, and try to provide a device that can last at least 20 percent longer, to account for dwindling capacity over the battery’s lifetime.
Mobile devices are rated in terms of how long their battery should power the device during “normal” use, how long the device can go between battery charges, and how much power the battery provides and needs to charge. Start with the device maker’s numbers, and follow up with benchmarks on mobile device review sites. If no devices meet the user’s needs, make sure they have a removable battery and spares, or a portable external battery recharger. You can plug a mobile device into a portable battery recharger (also called an external battery, power pack, or portable charger) to recharge.
There are two ways to think about battery life: how long it will last on each charge, and how long the battery can meet your needs before you have to replace it. When you waste battery life on unused device features, you shorten both. Here’s a list of power-hungry components with tips for managing them, but there’s no need to guess; check your device’s battery usage monitor (see Figure 3.4-3).
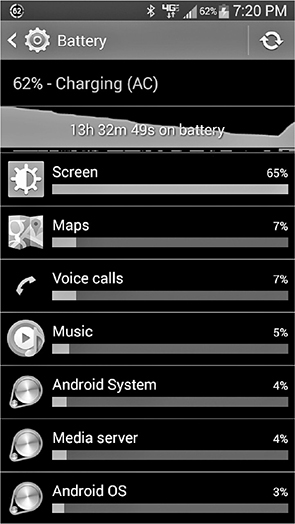
FIGURE 3.4-3 Battery usage for a smartphone
• Display The fastest way to drain most modern mobile devices is leaving the screen on. Keep the display off when you can, and use the lowest acceptable brightness setting or automatic brightness. Other settings control how soon the screen turns off without input and whether notifications turn it on. Enable power-saving modes—some of which can even go grayscale. OLED displays, which use less power for darker colors, can reduce drain with black wallpapers and dark app themes.
• Wireless communication Cellular voice, cellular data, Wi-Fi, Bluetooth, NFC, and so on, all have a radio inside the device, and each draws power while enabled. Additionally, searching for a signal is expensive, and some apps will do more work when a radio is available. You may be able to dodge signal-search drain with settings to limit or disable device roaming and searching for new wireless networks. You can likewise restrict drain from overeager apps with app or OS settings.
• Location services The power drain caused by these services can vary widely between an app that occasionally checks low-accuracy location based on nearby cellular or Wi-Fi networks in the background, and an app that constantly requests high-quality GPS updates. The simple solution is keeping location services off unless needed, but you may find a happy medium with per-app restrictions. An app should prompt you to turn location services on when it needs them.
Overheating
Some mobile devices, such as laptops or some tablets, have cooling vents or fans; make sure these fans and cooling vents are not blocked. With smartphones, avoiding overheating is trickier because they are usually turned on, carried in our hands or pockets, and might be inside a hard or semi-hard case for protection against impact. Tips to avoid overheating include
• Avoid very hot environments or turn the device off.
• If the device is hot to the touch in a cool environment, put it into airplane mode, close all running programs, and see if it cools. If not, turn it off until it cools and try again.
Beware if the device overheats for no obvious reason, or gets hot enough to burn someone. These problems are usually caused by a defective battery or other power circuit within the device. There’s not much you can do other than turn it off to protect the device from further damage; keep it out of pockets, away from people, and take it to a service center.
Frozen System
A mobile device that won’t respond to key or screen presses is a frozen system. The immediate goal is getting it to a usable state:
• If the device isn’t responding, follow the manufacturer’s steps for performing a soft reset.
• If the device is partially responsive, close the offending app, save work in other open apps, and perform a soft reset. When the device is usable again, look for a solution.
• If the device froze when you opened a new or updated app, use a soft reset, then try the app one more time. If the device freezes up again, uninstall it and wait for an update or find a replacement app.
• OS issues can also cause a freeze, especially after an update; look for follow-up OS patches. If you haven’t recently updated and the device starts freezing when you use any app that activates a component (such as the GPS or camera), your device needs service.
• If the device is unusable after the soft reset, find documentation on how to boot into any special modes that enable you to remove an offending app, repair the OS installation, or reset the device to factory default. If this too fails, send it to a service center.
No Sound from Speakers
If your mobile device has no sound, check the following:
• If a headset or external speaker is plugged in, unplug it if you want to use the device’s internal speakers.
• Check volume and mute settings in the OS and apps as well as hardware controls. Expect the OS to have multiple settings for calls, music, notifications, and so on.
• Try a soft reset.
• If none of these steps works, the speakers have likely been damaged or disconnected inside the device; it needs service.
System Lockout
System lockout occurs when too many consecutive login attempts fail, to protect the device from brute-force attempts to guess the password. Differing lockout mechanisms may prevent further login attempts for some period of time, require login with full account credentials, or even wipe user data. Configure options like this on the device itself, or through the organization’s central mobile device management (MDM) software, but advise users not to exceed a certain number of login attempts and to keep their devices away from anyone (e.g., children) who might trigger the mechanism.
The company should securely store PINs and maintain current backups of all its own mobile devices, and instruct those with their own devices to keep backups. The MDM software can unlock the device, but it won’t help if it has already been wiped. If no one can unlock a device, you’ll have to restore from a backup or perform a reset to factory default.
App Log Errors
Mobile device operating systems track app errors in a log that you can check to help track down system problems:
• Windows mobile devices use the Event Viewer available from the Microsoft Management Console (MMC).
• Use the Console app on macOS to read logs for connected iOS devices. Logs for iOS devices are also synced to iTunes.
• On Android, use third-party developer tools to see Android logs.
REVIEW
Objective 3.4: Given a scenario, troubleshoot mobile OS and application issues Common symptoms of mobile OS and application issues include
• Dim display
• Intermittent or no wireless connectivity
• No Bluetooth connectivity
• Can’t broadcast to external monitor
• Touchscreen nonresponsive or responds inaccurately
• Apps not loading
• Slow performance
• Unable to decrypt e-mail
• Extremely short battery life
• Overheating
• Frozen system
• No sound from speakers
• System lockout
• App log errors
A common solution for some of these problems is a soft reset.
3.4 QUESTIONS
1. Which of the following would not be affected by airplane mode?
A. Wi-Fi connections
B. Cellular connections
B. Display brightness
D. Bluetooth connections
2. You have connected an HDTV with your laptop and you can’t see your desktop on the HDTV. You have set your display properties to mirror. What should you do next?
A. Restart in Safe Mode
B. Check the HDTV input setting
C. Restart in normal mode
D. Set your display properties to HDTV
3. Your client is afraid that her smartphone has come in contact with water. Which of the following should you have her check?
A. LCI
B. Moisture sensor in Settings
C. Bluetooth
D. Airplane mode
4. Which of the following issues can be helped by performing a soft reset of a mobile device? (Choose two.)
A. Extremely short battery life
B. Frozen system
C. Moisture
D. No sound from speakers
5. Your smartphone is down to 10 percent battery life but you’re expecting an important phone call. Which settings can you safely change to improve battery life? (Choose two.)
A. Enable airplane mode
B. Disable NFC
C. Disable GPS
D. Enable navigation
3.4 ANSWERS
1. C The other settings are disabled by airplane mode, but it has no effect on screen brightness.
2. B The HDTV must be set to use the correct HDMI input before it can be used with the laptop.
3. A A liquid contact indicator (LCI) is a moisture-sensitive sticker used by many vendors to determine if a device has come in contact with liquid.
4. B D A frozen system and no sound from speakers are two of the many problems that can be solved by performing a soft reset.
5. B C Disabling NFC and GPS will save power without affecting your ability to make and receive phone calls.

Objective 3.5 Given a scenario, troubleshoot mobile OS and application security issues
With mobile devices becoming more and more common as primary computing devices, mobile OS and application security issues are more important than ever. With the rise of BYOD (bring your own device) policies, it can be harder than ever to keep mobile devices working securely.
Common Symptoms of Mobile OS and Application Security Issues (with Solutions)
The following sections discuss common symptoms of mobile OS and application security issues and their corresponding solutions.
Wi-Fi, Wireless Cellular, and Bluetooth Issues
Malware is just software that uses your device against your will, so a simple sign is unexpected resource use. Because many resource issues are benign problems fixed by a soft reset, it’s easy to shrug them off; be suspicious, especially of unexplained patterns such as the following:
• A hot phone, high resource utilization, and excessive power drain might mean your device is doing a malware developer’s bidding, such as uploading recorded audio in real time or smuggling networked files out.
• Slow data speeds might mean your device is busy uploading or downloading data without your knowledge, or might be a clue that it is using an illegitimate WAP or cell tower with less capacity than its official counterpart.
• A device uploading stolen data might unexpectedly exceed cellular data transmission limits.
Unintended Wi-Fi connections and unintended Bluetooth pairing enable malicious people to access, steal, or modify data. Configure your mobile device not to automatically connect or pair; doing these manually is worth the trouble. If the device is centrally managed, MDM software can enforce these protections via profile settings.
In addition to their impact on battery life, power management, and running apps, signal drop and weak signal are some of the few clues you’ll get that your device is interacting with a spoofed cell tower or rogue Wi-Fi access point. If signal quality suddenly changes in either direction, be curious. See if the cellular provider has known tower issues nearby. Fire up a cell tower analyzer and compare nearby signals with what you’ve seen in the past, or with third-party resources online. To prevent automatic connections to a rogue Wi-Fi access point, disable the automatic connection setting for SSIDs. It’s a bit more work to click the SSID you want to connect to, but it helps prevent connecting to a bogus wireless network.
Leaked Personal Files/Data
Device locks and remote wipe can prevent unauthorized users from accessing data on a mobile device—if you wipe the device in time. Data can also leak out through apps and removable storage cards. Encrypt portable devices and removable storage if it contains sensitive data. App and device security and privacy settings can protect personal data, but there’s always risk here.
No matter the source, leaked personal files and data can pose a direct privacy or security risk, indicate an ongoing security issue, and suggest what that issue might be. A full audit of ways an important file could’ve leaked out of a networked environment is beyond what can be expected of a CompTIA A+ tech, but be curious—you may well get the first chance to escalate the issue, or write it off as a compromised login and make the user change passwords.
Unauthorized Account Access
For convenience, mobile devices are often set to automatically authenticate with networks, VPNs, e-mail servers, online services, and so on, granting unauthorized account access to anyone who can unlock the device. To keep sensitive accounts and connections secure, don’t store credentials for automatic entry. When a device is lost, change the user’s credentials. Unauthorized account access can also indicate an attack or malware has compromised a device, creating an ongoing threat to the organization.
Unauthorized Location Tracking
Depending on settings, the OS and geotracking apps may send a user’s location to third parties. Prevent this by disabling GPS or location services until needed; otherwise, configure the OS and geotracking apps to prevent unauthorized tracking. Some apps or specific features won’t work until geotracking is enabled (see Figure 3.5-1).

FIGURE 3.5-1 Android apps prompting the user to enable location services
Both legitimate networks and some of the network attacks listed earlier in this objective can also be used to locate or track a device. Tracking when devices cross invisible boundaries, or geofencing, is used for advertising, customer tracking, and employee tracking.
Unauthorized Camera/Microphone Activation
App features, malware, and unauthorized network connections can potentially be used to toggle device features such as built-in cameras and microphones, enabling attackers to spy on anyone nearby. You can limit risk by restricting camera and microphone permissions in apps or OS settings, preventing unauthorized network connections, and using anti-malware solutions. With camera and microphone permissions, even popular apps (see Figure 3.5-2) by trustworthy developers could have a vulnerability that enables an attacker to watch or listen in.

FIGURE 3.5-2 Apps with permission to access an iPhone’s camera
REVIEW
Objective 3.5: Given a scenario, troubleshoot mobile OS and application security issues
• High resource utilization, power drain, and slow data speeds are all clues that point to a possible malware infection.
• Unintended Wi-Fi connections and unintended Bluetooth pairing can lead to data theft or unauthorized changes.
• Signal drop and weak signal can indicate a spoofed cell tower or rogue WAP is being used.
• To prevent leaks of personal files and data, use encryption and app settings that enforce privacy.
• Avoid unauthorized account access by using manual logins.
• Turn off geotracking when not needed.
• Disable camera and microphone permissions in all apps except those that need them to function.
3.5 QUESTIONS
1. Which of the following mobile features can be set up for use by specified apps only?
A. Wi-Fi connections
B. Browser
C. GPS
D. Airplane mode
2. High resource utilization when no apps are open could be a sign of which of the following?
A. Dying battery
B. Malware
C. Airplane mode
D. GPS enabled
3. A user wants to use Google Maps to navigate to a meeting. Which function does he need to enable to make this possible?
A. Wi-Fi
B. Bluetooth
C. GPS
D. NFC
4. Your CEO is conducting sensitive negotiations with another firm. In addition to using a passcode on his device, which of the following steps can prevent his device from revealing confidential information if lost? (Choose two.)
A. Encrypting the drive
B. Enabling airplane mode
C. Enabling GPS
D. Enabling remote wipe
5. Which of the following common features can be used to snoop on a user’s conversations?
A. Microphone
B. NFC
C. Panorama
D. Browser
3.5 ANSWERS
1. C GPS access can be granted to specific apps.
2. B Malware can use a lot of resources because it captures and sends data without the user’s permission or knowledge.
3. C GPS must be enabled to permit navigation. Without it, you can only view maps.
4. A D Encrypting the drive prevents its contents from being accessed by others, while enabling remote wipe will make the device useless and protect its contents from being decrypted when the wipe command is activated.
5. A A microphone can be used to record conversations.




