
Virtualization and Cloud Computing
Domain Objectives
• 4.1 Compare and contrast cloud computing concepts
• 4.2 Given a scenario, set up and configure client-side virtualization

Objective 4.1 Compare and contrast cloud computing concepts
Cloud computing has become omnipresent, from online storage services and e-mail providers to integrated business apps. In this section, you learn about the different types of cloud services and how to choose the most appropriate cloud model for the work you client or organization needs to do.
Common Cloud Models
Most people associate “The Cloud” with friendly file-storage services such as Dropbox and Google Drive—but cloud computing is about simple interfaces to a vast array of on-demand computing resources sold by Amazon (see Figure 4.1-1), Microsoft, Google, and many other companies over the open Internet. We use the servers and networks of the cloud through layers of software that add great value to the underlying hardware by making it simple to perform complex tasks and manage powerful hardware.
FIGURE 4.1-1 Amazon Web Services Management Console
As end users, the web applications such as Dropbox that we associate with the cloud are actually just one of three layers of cloud services that support web applications and their developers.
As we examine the various cloud services, you should note that all of them have these features in common:
• Cost Cloud services cost less than purchasing hardware, operating systems, and software.
• Flexibility Cloud services are able to cope with big swings in demand.
• Security Cloud services enable security to be centralized, but can also put more information at risk if best practices are not followed.
• Administration Cloud services are easier to administer than traditional servers and computers.
Let’s start by looking at the basis for cloud services: Infrastructure as a Service.
IaaS
Large-scale global Infrastructure as a Service (IaaS) cloud service providers combine virtualization’s ability to minimize idle hardware, protect against data loss and downtime, and respond to spikes in demand with the power of vast data centers and massive networks. Cloud service providers (CSPs) such as Amazon Web Services (AWS) enable everyone from you to large multinational corporations to launch new virtual servers using a given OS, on demand, for pennies an hour. AWS and other CSPs provide many of the services needed to drive popular, complex web applications—unlimited data storage, database servers, caching, media hosting, and more—all billed by usage. IaaS frees us from managing hardware, but we’re still responsible for configuring each virtual machine (VM) and keeping its software up to date.
PaaS
A Platform as a Service (PaaS) provider such as Heroku (see Figure 4.1-2) gives programmers all the tools they need to deploy, administer, and maintain a web application. The PaaS provider starts with some form of infrastructure, which could be provided by an IaaS, and on top of that infrastructure the provider builds a platform: a complete deployment and management system to handle every aspect of a web application. The infrastructure underneath the PaaS is largely invisible to the developer—a PaaS service saves you even more time on setup, configuration, and maintenance (at the expense of flexibility).

FIGURE 4.1-2 Heroku’s management console
SaaS
Software as a Service (SaaS) is the top layer of web services, accessible as web applications. Users of these web apps don’t own the software—there’s no installer. They use a web app through its website or native device apps. This may sound like a disadvantage, but the SaaS model provides access to necessary applications (such as word processing, presentations, spreadsheets, e-mail, flowcharting, and more) wherever you have an Internet connection, often without having to carry data or install regular updates. The monthly or yearly subscription model of many SaaS offerings makes it easier to budget and keep hundreds or thousands of computers up to date. The tradeoff to using SaaS is giving control of your data to the SaaS provider.
Public vs. Private vs. Hybrid vs. Community
Giving control of data to an SaaS provider is a major security concern for many companies, because their sensitive intellectual property or business secrets may be traveling through untrusted networks and being stored on servers they don’t control. When it comes to security concerns like these (among other factors), different organizations come to different conclusions. The result is a number of terms we use to describe who owns and controls given cloud resources:
• Out on the open, public Internet, cloud services that anyone can access are the public cloud. When we talk about the cloud, we mean the public cloud. The public doesn’t own it—companies such as Amazon, Google, and Microsoft do—but any individual or company can use public IaaS, PaaS, and SaaS offerings.
• Organizations that want some of the flexibility the cloud offers but need complete ownership of their data (and can afford both) can build (or contract a third party to build) an internal private cloud. A business could build a private IaaS that departments use to create and destroy VMs as needed, and a private PaaS to support the quick development of internal web apps such as private SaaS to meet the collaboration, planning, or time management needs of their employees.
• A community cloud is basically a private cloud paid for by a “community” of organizations in the same industry or with similar challenges. Imagine, for example, a community cloud for hospitals that meets the special regulatory requirements of dealing with patient data, or a cloud for military contractors that enables them to share the burden of defending against attackers sponsored by foreign states. This could be as simple as an SaaS application for tracking patient charts, or as complex IaaS and PaaS offerings.
• A hybrid cloud isn’t really a type of cloud—it just describes blending IaaS, PaaS, and SaaS resources from the other types. For example, you could maintain your own private cloud to satisfy average demand, then launch new VMs in the public cloud as you approach your own cloud’s capacity—called cloud bursting. Hybrid cloud can also mean integrating specific services across cloud types—a hotel chain, for example, could build a private/internal SaaS app to enable each manager to predict which bookings will likely miss because their flights got delayed or cancelled. To accomplish this, they could integrate with a third-party weather forecasting app in the public cloud and a flight-tracking app in a community cloud for the aviation industry.
Shared Resources
One of the benefits of cloud computing is how it enhances the concept of shared resources. All networks feature shared resources such as storage and servers, but with cloud computing, these resources can be accessed via the Internet, not just those connected to the same LAN.
Internal vs. External
One of the keys to sharing resources is understanding what you can do with internal and external cloud resources. Often, internal resources start with a virtual machine. The primary requirement for a VM you intend to use as a server is network connectivity, and one of the coolest features of VMs is the many different ways you can “virtually” network them. This doesn’t mean just connecting them to the Internet—every hypervisor (described later under objective 4.2) has the capability to connect each of its VMs to a network in a number of different ways.
The combinations are infinite, but here are the basic options:
• Virtual machines on the same hypervisor can be internally networked (see Figure 4.1-3)—connected to a virtual switch (see Figure 4.1-4) inside the hypervisor—with none of their network traffic leaving the host machine.

FIGURE 4.1-3 Configuring a VM for an internal network in VirtualBox

FIGURE 4.1-4 Hyper-V’s Virtual Switch Manager
• You can bridge the VM’s NIC to the host system’s NIC (connecting it to the Internet, if the LAN is connected), enabling it to get an IP address on the LAN from DHCP. By connecting the VM to the Internet, you can share resources with a cloud computing environment, IaaS, PaaS, or SaaS.
• Just because you make a VM doesn’t mean you need any kind of network. A no-network VM can be a simple place to test something quickly—or to test software that may pose a risk to your network.
The ability to network these servers on the fly means you can create a virtual LAN (VLAN) with a whole team of servers performing different jobs or sharing a workload. Need to add new servers, or rearrange the network to try something new? No problem—you don’t even have to re-cable—just reconfigure the virtual network settings.
Resource Pooling
Resource pooling refers to cloud computing providers’ ability to provide different amounts of storage, server, or other shared resources to multiple clients, transparently. A cloud computing provider’s resource pooling enables it to provide a higher level of server and storage capacity at peak periods and lower levels of server and storage capacity for client A (Eastern Time Zone, USA), client B (Greenwich Time, UK), and client C (Tokyo, following day) automatically with the peaks and valleys of demand.
Measured Service, Metered
A measured service model is what a CSP uses when it monitors the cloud resources that customers use and bills them accordingly. Thus, if a company needs extra servers during the workweek but not on weekends, it can use cloud computing–based servers Monday through Friday and pay only for the time, capacity, or bandwidth (pricing models vary) that it uses. That way, the company avoids purchasing physical servers that would be idle part of the time. Measured services are also known as metered services or “pay per use.”
On-demand, Rapid Elasticity
The nature of cloud services provides greater flexibility and much more rapid provisioning of resources than is possible with on-premises infrastructure: the ability to use cloud resources and services on demand empowers customers to scale up or down rapidly to handle spikes or sags in their own demand, which is known as rapid elasticity.
For example, with traditional in-house resources, adding servers would require purchasing them, installing them, and configuring them before use, a process that can take days. By contrast, cloud services can add servers or other resources in just a few minutes.
Off-site E-mail Applications
Google Mail (Gmail) and Microsoft Outlook.com are two examples of popular cloud-based off-site e-mail applications. They can be used as web-based e-mail services or can be used with popular e-mail clients such as Microsoft Office Outlook, Mozilla Thunderbird, and others. Gmail and Outlook.com are examples of SaaS.
Cloud File Storage Services
Microsoft OneDrive, Dropbox, and Google Drive are three examples of popular cloud-based file storage services. These and similar services can be used for file backup, for file transfer, as an alternative to FTP or SFTP, and for file synchronization.
Synchronization Apps
File synchronization apps such as Google Drive Backup and Sync, Mozy Sync, and KeepItSafe Online Backup go beyond file storage services by enabling users to sync, either on-demand or automatically, copies of files that are stored both locally on their computers and mobile devices, and remotely in the cloud. MultCloud is a cloud storage manager that performs sync and file transfer between leading cloud services such as OneDrive, Google Drive, Dropbox, Amazon Cloud Drive, and many others.
Virtual Application Streaming/Cloud-based Applications
Virtual application streaming is a technology that enables a workstation or mobile device to run cloud-based applications as if they are installed locally. Virtual application streaming enables only the relevant parts of an application to be run from cloud storage, automatically swapping program components in and out as needed. Virtual application streaming licensing is typically less expensive per user than standard software licenses, as a license is used only when the app is streamed. For example, if ten users at a time out of a fleet of 100 computers need access to program ABC, a ten-seat streaming license for ABC is likely to be much less expensive than 100 standard licenses for program ABC. Virtual application streaming is a virtualization technology rather than an example of SaaS.
Applications for Cell Phones/Tablets
Smartphone/tablet virtual app streaming enables these mobile devices to run apps originally developed for Windows desktop operating systems. Users work with apps on their smartphone or tablet just as if they were using a desktop or laptop computer with those same apps. Some vendors also offer virtual desktops so that a Windows desktop can appear on a mobile device.
Depending upon the specific solution, users might connect via a website or by running an app on their client devices to access virtual app streaming. Examples of software that supports virtual app streaming on mobile devices include Citrix Virtual Apps (formerly XenApp) and Parallels Remote Application Server (RAS).
Applications for Laptops/Desktops
Virtual application streaming is also useful for laptops and desktops, as it enables these devices to run software that is stored, managed, and secured remotely. One example is Microsoft Application Virtualization (App-V) for Windows 7 and later, running Win32 apps from App-V servers. Another is VMware ThinApp, supporting Windows, Terminal Server, and Citrix.
Virtual Desktop
CompTIA uses the term virtual desktop in an odd way; we’ve used it the same way here, to describe a simple desktop environment on a virtual machine. In practice, a virtual desktop more commonly refers to the multiple desktop environments you can access in modern operating systems, such as clicking the Task View icon in Windows 10 and going to a second desktop.
Virtual NIC
Virtual machines connect to physical networks by using a virtual network interface card (virtual NIC). A virtual NIC is a bridge created by a virtualization app to connect to a physical NIC on the host device. Whenever the VM needs to connect to another device on the network or the Internet, the request is sent to the virtual NIC, which in turn sends it to the physical NIC. Responses come back to the physical NIC, which sends them back to the virtual NIC for the appropriate VM.
When apps that display hardware configuration, such as Windows Device Manager, are run within a VM, the virtual NICs and other virtual devices are displayed (see Figure 4.1-5). Note that the network adapter listing is the virtualized NIC; the host computer uses a different brand and model of NIC. When apps that display network connections are run from an OS that is hosting a VM, both physical and virtual NICs are displayed.
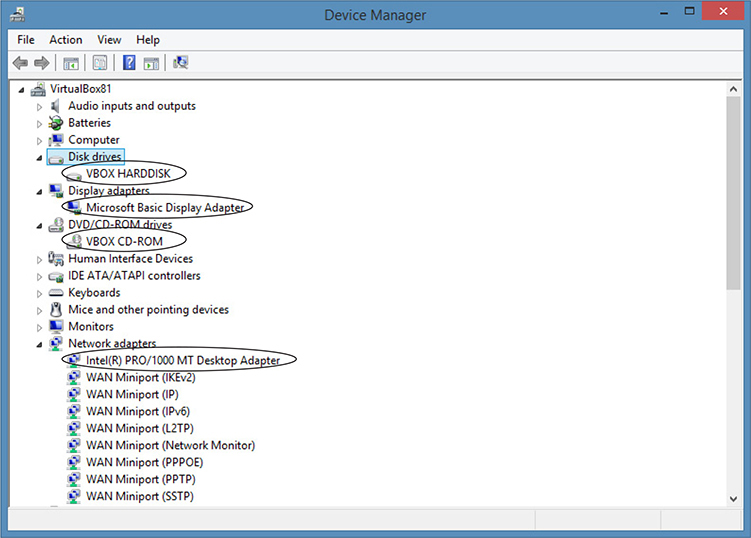
FIGURE 4.1-5 VirtualBox (VBOX) virtual drives and other virtualized devices shown in Device Manager
REVIEW
Objective 4.1: Compare and contrast cloud computing concepts
• The major types of cloud services include Infrastructure as a Service (IaaS), Platform as a Service (PaaS), and Software as a Service (SaaS).
• The public cloud refers to cloud services available to anyone.
• Private cloud services are used internally by companies.
• A community cloud is a private cloud paid for by a group of organizations or individuals.
• A hybrid cloud blends IaaS, PaaS, and SaaS resources.
• Shared resources such as VMs, cloud storage, and others can be shared via LANs (internally) or with cloud computing (externally).
• Resource pooling enables organizations to move and run VMs between different hardware as needed.
• Measured service bills cloud computing users based on bandwidth, time, or capacity used.
• The ability to add or drop cloud services as needed (on-demand self-service) enables organizations to have rapid elasticity.
• Metered service enables CSPs to offer unlimited resources to its clients but charges them only for what is used.
• Popular cloud-based services include e-mail, file storage, and file synchronization.
• Virtual application streaming enables cloud-based apps to be run locally as if they’re installed locally.
• Virtual desktops (VDI) bundle an operating system, apps, and data storage for quick delivery to desktop computers as either customized (persistent VDI) or standard (non-persistent VDI) images.
• Virtual NICs connect VMs to physical networks.
4.1 QUESTIONS
1. Company A uses several SaaS products such as Gmail and Google Docs along with a customized private cloud for its proprietary apps. Which of the following best describes the Company A’s cloud computing strategy?
A. Public cloud
B. Hybrid cloud
C. Community cloud
D. VMM
2. Company B is planning to make the same applications available via cloud or network services to desktops and tablets. Which of the following is Company B planning to implement?
A. Virtual application streaming
B. Private cloud
C. SaaS
D. Measured service
3. Your company is going to use cloud services to develop software, and the software will then be available as a cloud service. Which pairing accurately reflects what services will be used, in the correct order?
A. IaaS, PaaS
B. PaaS, SaaS
C. SaaS, IaaS
D. SaaS, PaaS
4. Which of the following in a community cloud scenario is the grouping of servers and infrastructure for use by multiple customers?
A. Virtual desktop
B. Synchronization apps
C. Resource pooling
D. Virtual application streaming
5. Your company needs access to unlimited resources to promote rapid elasticity and on-demand swings in requirements, but wants to pay only for the resources it actually uses. What arrangement is your company looking for?
A. Measured service
B. IaaS
C. Hybrid cloud
D. Metered service
4.1 ANSWERS
1. B A hybrid cloud combines public cloud (in this case, SaaS) and private cloud solutions.
2. A Virtual application streaming makes apps available to a variety of platforms via cloud or network services.
3. B Platform as a Service (PaaS) is the use of a complete cloud-based software development environment. Software as a Service (SaaS) makes the software available for use via the cloud.
4. C In a community cloud scenario, the cloud service provider typically implements resource pooling, which is the grouping of servers and infrastructure for use by multiple customers but in a way that is on-demand and scalable.
5. D Metered service provides unlimited access to resources on a pay-for-what-you-use basis.

Objective 4.2 Given a scenario, set up and configure client-side virtualization
Virtualization enables a single physical host computer running specialized software to create virtual machines (saved in separate files), also known as guests, that replicate other computers, each with its own operating system, settings, apps, and data. Client-side virtualization refers to running a VM on your local system (in contrast to VMs run elsewhere) regardless of whether the VM file itself might be stored locally or on a central server accessed via the network. The software used to create and manage VMs is known as a hypervisor.
Cross-Reference
Purpose of Virtual Machines
If you aren’t familiar with virtualization, the idea can seem a little pointless at first. Why would you need to run an OS inside an OS? Here are a few of the biggest benefits:
• Going virtual enables companies to combine multiple servers onto fewer machines than in traditional computing. This offers tremendous savings on hardware purchases, electricity use, and the space used for computing.
• Because a VM is only a single file or two, a hacked system can rapidly be replaced with a snapshot (a backup) taken of the properly working VM. This is especially useful for getting critical servers back up quickly. Likewise, the minimal file numbers make it easy to duplicate a VM.
• The capability to run many operating systems on a single physical machine makes multiplatform testing and research easier and cheaper than with traditional setups.
Resource Requirements
Any computer running Windows, Linux, or macOS will support a hypervisor, but the hypervisor will run better if your computer has hardware virtualization support. If your computer’s CPU and UEFI/BIOS have this support, you can turn it on or off inside the system setup utility (see Figure 4.2-1).

FIGURE 4.2-1 UEFI firmware settings for CPU virtualization support on AMD (top) and Intel (bottom) CPUs
The other big hardware requirements are RAM and storage space. Each virtual machine needs just as much RAM as a physical one, and the host machine needs enough left over to run the hypervisor and any other software it needs to run. How much RAM is needed takes some research to figure out. Likewise, VM files eat up tons of storage space because they include everything installed on the VM—anywhere from megabytes to hundreds of gigabytes. Various online calculators for server-class virtualization are available to help you right-size physical hardware to your virtualization needs.
Emulator Requirements
Instead of writing drivers so that every imaginable guest can use the hypervisor’s virtual hardware, the hypervisor often emulates popular, widely supported hardware—devices every OS already has drivers for. For example, Oracle VM VirtualBox emulates the Intel PRO/1000 MT desktop NIC for networking and the (Southbridge) PCI to ISA bridge chip. What is the difference between virtualization and emulation?
Virtualization takes the hardware of the host system and segments into individual virtual machines. If you have an Intel system, a hypervisor creates a virtual machine that acts exactly like the host Intel system. It cannot act like any other type of computer. For example, you cannot make a virtual machine that acts like a Nintendo 3DS on an Intel system. Hypervisors simply pass the code from the virtual machine to the actual CPU.
An emulator is software or hardware that converts the commands to and from the host machine into an entirely different platform. In emulation performed by a hypervisor, the commands given to the virtual desktop NIC are converted into the appropriate commands used by the physical NIC. You can also use a console game emulator to run console games on a computer, such as a Super Nintendo Entertainment System emulator like Snes9X to run games made for SNES on a Windows PC.
Security Requirements
A virtual machine should be kept as secure as a physical computer. After all, with network and Internet connections present on almost any VM, it can be used (or misused) in the same way as a physical computer. Different users with different levels of access should be set up on a VM that will be used by multiple users. Strong passwords should be implemented. Antivirus and anti-malware apps should be deployed and kept updated. OS updates should be performed as needed.
Network Requirements
The easiest way to network a computer that will be hosting one or more VMs is with the fastest wired Ethernet supported. If you want to use wireless, a wireless NIC that uses a PCIe slot would also be suitable. Using a USB network adapter is not recommended, because of the limited support that USB devices have on most VM software.
Hypervisor
A hypervisor, also known as a virtual machine manager (VMM), creates, runs, and manages VMs. There are two types of hypervisors: Type 1 and Type 2.
A Type 1 hypervisor such as Hyper-V, VMware ESXi, and Citrix Hypervisor (formerly known as Citrix XenServer) runs directly on computer hardware in place of a standard operating system. A Type 1 hypervisor is also known as a “bare metal” hypervisor because there’s no other software between it and the hardware. VMs running server operating systems are run on Type 1 hypervisors.
A Type 2 hypervisor such as Oracle VM VirtualBox or VMware Workstation is run on a standard operating system (Linux, Windows, or macOS). Thus, Type 2 hypervisors have an additional layer of software compared to Type 1 hypervisors (see Figure 4.2-2 for an example). Most types of client-side virtualization use Type 2 hypervisors.
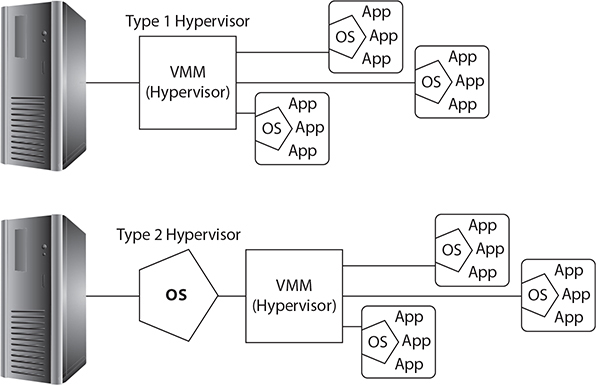
FIGURE 4.2-2 Type 1 hypervisors (top) compared to Type 2 hypervisors (bottom)
Installing a Hypervisor and Creating a Virtual Machine
Installing a third-party hypervisor is like installing any other software—download and execute the hypervisor software and follow its setup wizard. On a Windows 8/8.1/10 system that includes Hyper-V, you can enable it in the Windows Features dialog box (see Figure 4.2-3), which you reach via Control Panel | Programs and Features applet | Turn Windows features on or off. After enabling Hyper-V, reboot the system.

FIGURE 4.2-3 Enabling Hyper-V in Windows
After you’ve installed the hypervisor of choice, you’ll have a virtual machine manager that acts as the primary place to create, start, stop, save, and delete guest virtual machines. On pretty much any VMM, you create a new VM by clicking New | Virtual Machine and completing the wizard it opens (see Figure 4.2-4). Most hypervisors have presets to ensure your guest OS has the virtual hardware it needs.

FIGURE 4.2-4 Creating a new VM in Oracle VirtualBox
Installing the Guest Operating System
Once you’ve created the new guest VM, it’s time to install a guest operating system. Would you like to use Microsoft Windows in your virtual machine? No problem, but know that Windows (and any other licensed software you install) requires a valid license.
If you don’t already have installation media, most VMMs can just treat any ISO file (such as the one you’d use to make your own installation media) as the virtual machine’s optical drive. If the VMM recognizes your installation media (see Figure 4.2-5), it may configure the virtual hardware settings (amount of RAM, virtual hard drive size, and so on) automatically; otherwise, you need to set sensible values for these (you can still change them after the VM is created). Next, set the size of the virtual drive (see Figure 4.2-6).
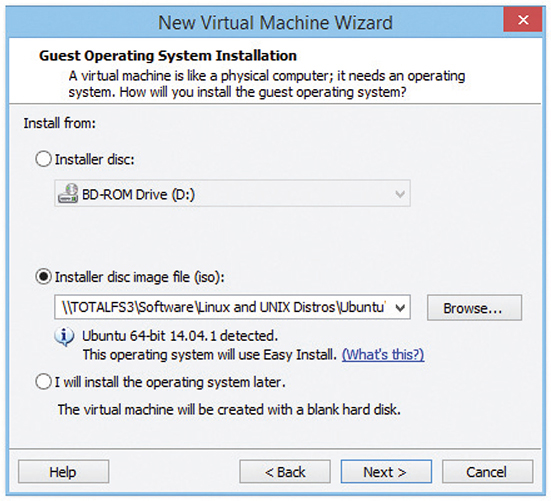
FIGURE 4.2-5 Installer recognizing selected installation media
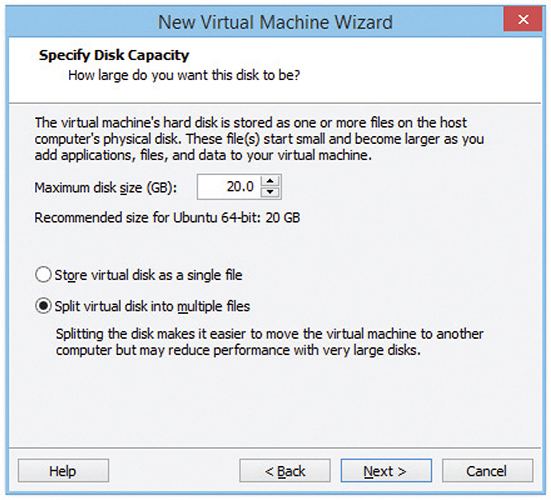
FIGURE 4.2-6 Setting the virtual drive size
You’ll also be prompted to name the VM and indicate where to store its data files. If you specified installation media, you’ll also have some time to burn while the OS installs. After configuration and installation, you can stop, start, pause, or delete the VM, add or remove virtual hardware, or just interact with the OS and other software inside it.
Using a VM is almost exactly like using a real system, except it’s contained in a window and some hotkeys differ. VMware Workstation, for example, replaces CTRL-ALT-DELETE with CTRL-ALT-INSERT by default (so you can still use CTRL-ALT-DELETE on your desktop). That, and you can adapt your virtual desktop to changing needs without a trip to the store: a good hypervisor can add and remove virtual hard drives, virtual network cards, virtual RAM, and so on. Keep in mind that USB drive support varies between hypervisors, and may require special settings or have limited support for USB 3.0 and faster versions.
REVIEW
Objective 4.2: Given a scenario, set up and configure client-side virtualization
• Virtualization enables companies to use fewer servers to perform tasks, provides for faster backup, and enables multiplatform testing on a single computer.
• For the best performance, enable the processor’s hardware virtualization support in the UEFI firmware setup, and provide enough RAM and disk space for each VM as well as for the host OS or hypervisor.
• Hypervisors emulate popular chipsets, NICs, and GPUs, enabling support for a wide range of hardware without specific drivers.
• VMs require exactly the same levels of security (passwords, updates, and so on) as the physical computers they replace.
• Wired rather than wireless networks are recommended for better performance, especially when Gigabit Ethernet or faster connections are available, and easier configuration.
• Type 1 hypervisors (aka bare-metal hypervisors) are installed directly on the hardware and are typically used for VMs in production applications.
• Type 2 hypervisors are installed on an operating system, and are typically used for experimenting and educational purposes.
• Hyper-V is a Type 1 hypervisor available on business and educational versions of Windows 8 and later and is enabled through Turn Windows features on or off in the Programs and Features Control Panel applet.
• Other hypervisors are available from various vendors. Installing a third-party hypervisor is like installing any other software.
• After a hypervisor (VMM) is installed, the process of creating a new VM is specific to each hypervisor, but the process of installing an OS into a VM is about the same as installing that OS on a physical computer.
4.2 QUESTIONS
1. Company C has set up a computing lab where it plans to install VirtualBox on Linux and Windows workstations and use it to run older versions of Linux and Windows to provide customer support. Which of the following best describes how Company C is using virtualization?
A. Type 1 virtualization
B. Bare metal virtualization
C. VMM
D. Type 2 virtualization
2. When is the size of the virtual hardware (such as RAM and drive size) set during the VM creation process?
A. Set automatically by the hypervisor at the start of the process
B. After installing the OS into the VM
C. Before installing the OS into the VM
D. Before starting the VM creation process
3. Company D has set up virtualization on several late-model Intel and AMD systems running high-performance processors using the recommended settings in the hypervisor for each VM, but the VMs are running very slowly. Which of the following is the most likely cause?
A. Hardware virtualization support is not enabled in the UEFI firmware.
B. VMs are using too much RAM.
C. Hardware virtualization support is not enabled in the OS.
D. VMs are using too much disk space.
4. Customer E is running Windows 10 Pro and wants to install a Linux-based VM in Hyper-V. Which of the following must the customer do for this to work? (Choose two.)
A. Turn on Hyper-V in Windows Features
B. Run Windows Update
C. Scan the host system for viruses
D. Restart the system
5. A customer is having a problem with the network hardware on the host Windows computer for her VMs. Which of the following will help her diagnose the problem?
A. Check Device Manager in each VM
B. Disable/re-enable the virtual NIC in each VM
C. Check Device Manager in the host computer
D. All of the above
4.2 ANSWERS
1. D Type 2 virtualization runs within an installed operating system and relays requests to the hardware to the host operating system, whereas Type 1 virtualization directly interfaces with the computer’s hardware.
2. C This information is used to set up the virtual machine, so it must be provided when the VM is created and before the OS can be installed.
3. A High-end Intel and AMD processors have support for hardware virtualization. However, if it not enabled in the firmware, virtualization will run very slowly.
4. A D For this to work, hardware virtualization support must first be enabled in the UEFI/BIOS. Second, Hyper-V needs to be turned on in Windows Features. Finally, enabling Hyper-V requires the system to be restarted.
5. C To solve a problem with the host’s network hardware, the host’s diagnostic features, such as Device Manager, must be used. The virtual NIC in each VM connects to the physical network, so the VMs can’t work if the physical network connection in the host isn’t working.




