
Operational Procedures
Domain Objectives
• 4.1 Compare and contrast best practices associated with types of documentation
• 4.2 Given a scenario, implement basic change management best practices
• 4.3 Given a scenario, implement basic disaster prevention and recovery methods
• 4.4 Explain common safety procedures
• 4.5 Explain environmental impacts and appropriate controls
• 4.7 Given a scenario, use proper communication techniques and professionalism
• 4.8 Identify the basics of scripting
• 4.9 Given a scenario, use remote access technologies

Objective 4.1 Compare and contrast best practices associated with types of documentation
Accurate documentation is a great aid to managing and troubleshooting devices, peripherals, and networks. Inaccurate documentation is frustrating because you never know which parts are accurate and which aren’t. That being said, many networks and individual workstations have no documentation at all. This objective helps you understand the best practices needed to create accurate and useful documentation.
Network Topology Diagrams
A network topology diagram provides a visual guide to the hardware on the network, from routers and switches to workstations, printers, and WAPs. A simple diagram is useful for showing how the components connect, while more complex diagrams provide connection types, speeds, and specific component brand/model information. Figure 4.1-1 illustrates a simple network diagram created with Microsoft Visio and Cisco network diagram icons.

FIGURE 4.1-1 A simple network diagram
Knowledge Base/Articles
A network topology diagram is just the beginning of your company’s knowledge base—a collection of documents that identifies the equipment and software in use, problems detected, and solutions to those problems; along with links to vendors and third-party websites with relevant information. Every time a technology-related event happens in an organization, there’s an opportunity to build up your knowledge base. Ideally, an organization’s knowledge base should start with the official documentation for each computer, component, and peripheral. These days, if the paper manual isn’t available, it’s no big deal because product manuals are almost always available for download.
Add documentation for the operating systems and apps used, supplemented by third-party e-books and patch and update information. To track down the information you need, make sure you have searchable PDF or e-book versions of your documentation.
Your knowledge base is not complete until you capture information as covered in the CompTIA six-step best practice methodology. Make sure you identify the device(s) or software affected, the theories that were discarded and the one that was accurate, how the solution was applied, and how to avoid similar problems in the future.
Cross-Reference
To summarize, here’s what your organization needs in its knowledge base:
• Official documentation, including patch and update information
• Third-party resources (websites, forums, e-books)
• Documentation of the organization’s own troubleshooting solutions
Incident Documentation
Incident documentation should include
• Devices or software involved
• Event logs when appropriate
• Symptoms and solutions
Cross-Reference
Regulatory and Compliance Policy
Larger organizations, such as government entities, benefit greatly from organizing their data according to its sensitivity and minimizing surprises by keeping computer hardware and software as uniform as possible. This also helps maintain compliance with government and internal regulations; common examples are rules on approved software and regulations on how you must handle personally identifiable information (PII) such as health or academic records. Templates for regulatory and compliance policies are widely available online.
Cross-Reference
Acceptable Use Policy
Most organizations require employees to sign an Acceptable Use Policy (AUP) that defines what actions employees may or may not perform with company equipment and systems, including computers, phones, printers, and the network itself.
The AUP covers the handling of passwords, e-mail, and many other issues, and it guides what actions or content should be identified as prohibited.
Password Policy
Organizations need a password policy. Why? In an ideal world, all of the users in your organization would have impossible-to-guess passwords that they change often and never write down or reuse elsewhere. In reality, users often choose passwords that are easy to hack—often including the name of a relative or pet—and practice poor security hygiene that exposes the organization’s systems and networks to risk, such as leaving their passwords on sticky notes next to their keyboards.
Cross-Reference
Inventory Management
Computers and common peripherals are relatively inexpensive, but when a computer or printer is misplaced, the cost of the hardware is trivial compared to other questions:
• What information is stored on the device?
• Where is it?
• Is it being stored?
• Was it stolen?
• Is it being used for unauthorized tasks?
The use of asset tags and barcodes can help organizations to track their technology inventory in an inventory management system.
Barcodes
A barcode asset tag contains a barcode that can be scanned. A barcode asset tag might be a vendor-applied tag or could be applied by the equipment owner. The use of a barcode asset tag makes tracking equipment faster and easier than with a strictly manual system because the barcode can be scanned rather than the asset tag code number being recorded manually or by typing.
Asset Tags
An asset tag with RFID capabilities provides much more equipment management capabilities than a barcode system. With an RFID-based system, it’s easier to update inventory and update location and other information, and RFID tags don’t need to be scanned individually.
REVIEW
Objective 4.1: Compare and contrast best practices associated with types of documentation Elements of documentation best practices include
• Creating network topology diagrams
• Creating a knowledge base from vendor and third-party documentation of hardware and software along with in-house troubleshooting information
• Gathering incident documentation
• Developing regulatory and compliance policy
• Developing an Acceptable Use Policy
• Creating a password policy
• Using asset tags and barcodes as part of inventory management
4.1 QUESTIONS
1. At a minimum, a network topology diagram should record which of the following?
A. Connections between network components such as routers, switches, and WAPs
B. Usernames and accounts
C. Routing details
D. DHCP address ranges
2. You have been tasked with creating a knowledge base for the Windows-based equipment in your department. Some of the computers were hand-built by a computer shop and you need to find out the motherboard, chipset, CPU, and RAM information. Which of the following will enable you to find the most information about each system?
A. Contacting the computer shop
B. Dismantling each custom-built PC
C. Running a third-party system information app
D. Viewing the System Properties dialog box
3. Which of the following is not likely to be covered in an Acceptable Use Policy?
A. Password handling
B. Keyboard lighting
C. Using e-mail
D. Personal print jobs
4. You are creating an asset tag design for your employer, which plans to use a hand-held scanner as part of the company’s inventory system. Which of the following must be on the asset tag?
A. Company slogan
B. Barcode
C. Company logo
D. Asset number
5. You visit a department to prepare for a training class that will deal with issues you observe. As soon you open the door to the department, you see sticky notes on each computer display. Which of the following topics do you need to address in training?
A. Decluttering the office
B. Shutdown procedures
C. Choosing sticky note colors that harmonize with the décor
D. Security
4.1 ANSWERS
1. A A network topology diagram must record the network’s physical layout. The other items are desirable to know, but not essential.
2. C A third-party system information app can provide much more information than the System Properties dialog box in Windows.
3. B Keyboard lighting is a feature found mainly on gaming keyboards and some laptops and won’t affect typical operations covered in an AUP.
4. B An asset tag that will be used with a hand-held scanner needs a barcode.
5. D The sticky notes are almost certainly used for passwords, so security training is top priority.

Objective 4.2 Given a scenario, implement basic change management best practices
“Change” is a frightening word to most organizations. Whether it’s a change from one brand of printer to another, from an old Windows version to the latest Windows 10, or a change from local to cloud-based apps, people are usually comfortable with the status quo and resist change. Managing change helps ease the shock of the new and makes it easier for an organization to cope when the inevitable happens.
Change Management Best Practices Overview
Change management best practices include
• Documented business processes
• Purpose of the change
• Scope the change
• Risk analysis
• Plan for change
• End-user acceptance
• Change board
• Approvals
• Backout plan
• Document changes
Documented Business Processes
Step 1 is to document existing business processes that will be affected by the change. For example, how users back up files, print documents, share documents, and so forth. The specific business processes to analyze depend on the changes being considered.
Purpose of the Change
The next step is to determine and document the purpose of the change. Some examples might include
• Improve compatibility with the latest software
• Make backups more reliable
• Standardize hardware platforms
Scope the Change
Scope the change means to identify who and what will be affected by the change. Specifically, which personnel will be affected by the change, which systems will be replaced, what software will be replaced, how long the change will take, and how much the change will cost (including support staff, training, and other indirect costs).
Risk Analysis
What are the risks of the proposed change? Some of the questions to consider in creating a risk analysis include
• Will existing data backups be compatible post-change?
• How much time will employee training require?
• Will proprietary software or systems continue to work or will they need to be updated?
• What are the security risks of the change?
Plan for Change
Planning for change should include
• Creating a timeline for the process
• Developing a transition strategy
• Running old and new procedures in parallel if appropriate (for example, for accounting or database changes)
• Building in time for training and practice
• Determining where to store surplus equipment
End-user Acceptance
End users sometimes are the last to be consulted about proposed changes, although their acceptance is critical to the success of any change. To help promote end-user acceptance, consider
• Having end-user involvement in the planning process
• Making sure end-users are properly trained
• Asking for feedback and carefully considering it
• Addressing concerns over proposed changes
Change Board
A committee known as a change board or change control board is typically in charge of evaluating a proposed change to the organization’s technology, particularly software. It should include technical experts and subject matter experts.
Approvals
The change board should consider a range of possible alternatives to any suggested change. Some possibilities might include
• Change approved
• Further study needed
• Reschedule change to (specify date)
• Reject change
• Modify change to (specify modifications)
Backout Plan
Some people believe that change = improvement, but in the real world, changes don’t always improve a situation. Having a backout plan, sometimes referred to as a rollback plan, is a change management best practice. Its purpose is to be able to return to the pre-change condition if needed.
Some parts of a backout plan might include
• Backing up the operating system, apps, and data before applying a change
• Using restore points, versioning, snapshots, or other options to capture the state of the system before and during changes.
• Creating a checklist of expectations for the change; if the change doesn’t meet expectations, the checklist also needs to establish at what point changes should be backed out
Document Changes
After a change has been implemented successfully, the change should be documented in its final form. This should incorporate the documentation generated throughout the change process, as previously discussed, as well as receipts, overtime records, systems, users, and so on.
REVIEW
Objective 4.2: Given a scenario, implement basic change management best practices Elements of basic change management best practices include
• Document business practices
• Identifying the purpose of the change
• Scoping the change
• Developing a risk analysis
• Planning for the change
• Working to get end-user acceptance
• Submitting a proposed change to the change board for approval
• Creating a backout plan
• Documenting the changes made
4.2 QUESTIONS
1. A backout plan is used to perform which of the following tasks?
A. Gain change board approval
B. Analyze the effects of change
C. Return to pre-change conditions
D. Aid end-user acceptance
2. You are helping to choose the members of the change board for a technology upgrade to the art department. Which of the following do not need to be involved? (Choose two.)
A. IT
B. Human resources
C. Executive management
D. End users
3. Which of the following is a good example of change management?
A. End users are introduced to a new technology without training
B. The change board is not consulted during the process
C. Rumors abound about the reasons for the change
D. Risk analysis is performed
4. Six months after a software change was made in a department, you are asked to troubleshoot a problem. The only related information you can locate refers to the old software system. Which of the steps in change management was not performed?
A. Document changes
B. End-user acceptance
C. Risk management
D. Plan for change
5. Your organization is proposing a change that will have a big impact on its salespeople in the field. Which of the following steps is most likely to enable the field reps to provide input about the proposed change?
A. Plan for change
B. Risk management
C. End-user acceptance
D. Document changes
4.2 ANSWERS
1. C A backout (rollback) plan is designed to help an organization return to pre-change conditions if a change has an adverse impact.
2. B C Neither human resources nor executive management are directly involved in the department’s day-to-day operations.
3. D Risk analysis is a necessary part of change management.
4. A Without documenting changes, the knowledge of what has changed will fade over time.
5. C End-user acceptance should include the opportunity for end users to address potential changes.

Objective 4.3 Given a scenario, implement basic disaster prevention and recovery methods
Ready for a disaster? If you haven’t made preparations, the answer is “No.” When a disaster that affects IT resources occurs, data is the most critical asset to recover. In this objective, you review the basic processes needed to preserve and recover user data.
Backup and Recovery
System maintenance starts with preparation. Conducting regular backups of critical system files and personal data protects the system and its users from accidents and hardware failures. Having backups available also protects you from losing data if problems happen during maintenance. It’s best if you’re always positioned to restore both the OS and personal data quickly, but you can ultimately reinstall Windows and programs; personal data, on the other hand, is often irreplaceable.
Image Level
An image-level backup stores the entire contents of the specified drive in one or more files in a different location (local drive or network drive). Contents include the operating system, apps, data files, settings, boot sector, and so on. An image-level back is also known as a drive clone. Image-level backup software is included in Windows 7, 8/8.1 and early releases of Windows 10 (Backup and Restore [Windows 7]). For current versions of Windows 10, third-party image backup apps can be used. For Apple systems running macOS or OS X Lion or later, Time Machine can be used as an image backup, using Recovery Mode to restore. For Linux, the built-in dd utility can be used.
File Level
File-level backup creates copies of data files in a different location (local drive, network drive, or cloud service). File-level backups can be performed as part of image backup, but are most often performed by file backup utilities. File backups typically support versioning, enabling users to restore the latest or earlier versions of specific files or folders.
The Backup and Restore applet in Windows 7 orients the options (see Figure 4.3-1) around the automatic Let Windows choose (recommended) and manual Let me choose. If you let Windows do the picking (and your backup location has enough space), it will back up each user’s data and create a full system image. Alternatively, you can use granular controls to include or exclude any of these system-level and account-level options (see Figure 4.3-2). Backup and Restore is also included in Windows 8/8.1 and early releases of Windows 10. Current releases of Windows 10 support restoring from a Backup and Restore backup, but not the creation of a new backup using this tool.

FIGURE 4.3-1 Who chooses what to back up?

FIGURE 4.3-2 Granular backup options include libraries/folders for each account.
Windows 8/8.1/10 all have the File History applet (see Figure 4.3-3), where you can enable continuous backup of any personal files in your user account’s libraries (both the default libraries and any custom libraries you add) to another storage volume. File History doesn’t replace full-system backups, but it does link to the Backup and Restore tool in Windows 8/8.1 and early releases of Windows 10.

FIGURE 4.3-3 File History in Windows 10
Critical Applications
Obviously, backing up user data is the most important first step in backups, but a great deal of time is also consumed if critical applications must be reinstalled manually after a drive failure or other data-loss scenario takes place.
Image backups back up the operating system and installed applications as well as the current state of user files. For complete protection, consider a two-step backup process:
• Periodic image backup of the entire system (monthly if the OS and apps don’t change much)
• File-by-file backups of data files daily to weekly
If an image backup isn’t feasible, be prepared to reinstall apps. Have ready license keys, account information or credentials, and app sources (application installers or physical media).
What about restore points in Windows? A restore point records a snapshot of the operating system, drivers, and app configuration as of the date and time of the restore point. You can use a restore point to recover from a bad software or driver update, but it should be used along with image backups, not in place of them.
Backup Testing
A data-loss event is highly stressful, but it becomes disastrous if you discover that the backups you’ve been counting on to “save the day” can’t be recovered or don’t include the files needed.
The easiest way to test a backup is to use an option to restore the backup to a different folder. This feature is included in most backup apps. To test a backup that stores different versions (such as File History or Time Machine), look for an older version of a file and restore it to a different folder.
UPS
An uninterruptible power supply (UPS) protects your computer from brownouts and blackouts, which can cause data loss in addition to shutting down computers. A UPS (see Figure 4.3-4) has built-in batteries that supply power to your system when the electricity traveling through the power line drops below a certain level. Most UPS devices have an integrated alarm that tells you when your computer is running on battery power. Many techs call a UPS a battery backup. Note that a UPS does not provide unlimited power to keep working while the city lights are out; it simply gives you a short window of opportunity to save your data and shut down the system properly.

FIGURE 4.3-4 A typical UPS has some battery-backed AC outlets (right two outlets) and some outlets that are surge protected only: use these for printers.
The different types of UPS are explained in Table 4.3-1.
TABLE 4.3-1 UPS Battery Backup Types

Surge Protector
Surge protectors (also known as surge suppressors) help to absorb power surges so that your computer does not feel their effects (data corruption, lockups, crashes). They come either as separate modules or integrated into the UPS. Good surge protectors come with a long-term or lifetime guarantee against damage to your computer. Avoid purchasing or using cheap surge protectors. These are usually little more than power strips and provide virtually no protection against power surges or spikes.
Cloud Storage vs. Local Storage Backups
Both cloud storage and local storage backups can be used to back up users’ data files. Cloud storage offers easier backup than local storage: as long as your device is connected to the Internet and you have synchronization enabled, your backup takes place.
Some cloud storage vendors combine cloud and local backup into a single service so that you can recover data instantly from local backup while having cloud backup provide offsite backup as well.
Cloud storage is the default backup for iOS and Android users. However, the amount of free backup space is limited, and may need to be supplemented by purchasing more space, especially for users with 32-GB or larger-capacity storage devices.
• Cloud storage offers easier backup and a wide variety of capacities. However, restoring all of your files from cloud storage can take weeks.
• Local backups require the purchase of a backup drive and present the risk of backup loss if the backup drive fails. However, restoring files from local backup is very speedy.
Account Recovery Options
Account recovery has become a new concern with the rise of mobile devices and the increasing use of non-local accounts on laptops and desktops. Here are some typical account recovery options to set up before a device is lost or stolen:
• Set up security questions. In case of a lost password, you might need to provide the answers to several security questions to get access to your account or reset the account to a temporary password. Make sure you choose questions and answers that may be difficult for others to guess. Rule of thumb: If info is posted on social media, it’s not safe to use for a question or answer!
• Use your mobile phone as part of two-factor authentication (also known as two-step verification). If you are unable to use your normal authentication process via e-mail or login, having your mobile phone as a second authentication method prevents you from being locked out of your account.
• Have a secondary e-mail address as part of two-factor authentication. If you are unable to use your normal authentication process and if you lose your phone, having a secondary e-mail address can be a lifesaver for your account.
• For local accounts, create a password recovery disk (you can use either a small flash drive or recordable CD).
REVIEW
Objective 4.3: Given a scenario, implement basic disaster prevention and recovery methods Elements of basic disaster prevention and recovery methods include
• Performing scheduled image- and file-level backups
• Identifying and backing up critical applications
• Testing backups to verify that they are usable
• Using power protection devices such as UPSs and surge protectors
• Using cloud storage and/or local storage backups depending on requirements
• Configuring account recovery options before a device is lost or stolen
4.3 QUESTIONS
1. You need to restore a proprietary app that was lost in a system crash. Which type of backup will enable you to restore this information?
A. Time Machine/File History
B. Cloud backup
C. Restore point
D. Image backup
2. Which of the following statements most correctly describes power protection devices and issues?
A. A surge protector provides protection against brownouts.
B. A battery backup does not include surge protection.
C. A battery backup also incorporates surge protection.
D. A power surge is a type of ESD.
3. Which of the following is an example of a bad account recovery option?
A. Using the name of your high school as a security question when you have a complete Facebook profile
B. Using your mobile phone as part of two-factor authentication
C. Using the name of your first-grade teacher as a security question when you don’t use social media
D. Having a secondary e-mail address
4. SPS and UPS are examples of which type of solution?
A. Delivery couriers
B. Cloud-based backups
C. Battery backups
D. Image backups
5. You are helping a user running the latest edition of Windows 10 to recover from the loss of archive information stored with the Windows 7 Backup and Restore app. What should you tell the user?
A. You must roll back to an early edition of Windows 10 to restore the backup.
B. You can restore the backup from your current Windows 10 system.
C. You must roll back to Windows 7 to restore the backup.
D. The backup can’t be recovered.
4.3 ANSWERS
1. D An image backup stores app information as well as the operating system.
2. C Battery backups also include surge protection hardware.
3. A This is a poor choice for a security question because anyone with access to the Facebook account can learn the answer.
4. C Standby power systems and uninterruptible power supplies are terms for battery backups.
5. B All editions of Windows 10 include restore support for Windows 7 Backup and Restore, but backup support was dropped in recent and current editions.

Objective 4.4 Explain common safety procedures
Safety is of paramount importance when working as an IT tech. You need to protect yourself and others from the dangers of high-voltage equipment, toxic materials, and workplace hazards; and you need to protect valuable equipment from electrostatic discharge (ESD) and other environmental risks. Use this objective to learn the basic safety procedures you need to follow to go home safely after a long day in the IT trenches.
Equipment Grounding
Any AC-powered equipment that uses a three-prong cable (hot, neutral, ground) needs to be properly grounded. Surge suppression depends on having a working ground as a safe place to send power surges.
Unfortunately, some three-wire plugs are improperly wired or have no ground at all. To determine which outlets are working and which have wiring faults, use an outlet tester such as the one shown in Figure 4.4-1. Some surge suppressors also feature wiring fault testing in their circuitry.

FIGURE 4.4-1 A typical AC outlet tester indicating the outlet is wired properly
Proper Component Handling and Storage
Even when your computer is not in use, heat, moisture, and dirt are still hazards. Heat causes plastics to fade and become brittle, moisture encourages rust and corrosion, and dirt is, well, dirty. For these reasons, components and peripherals should be stored indoors in a climate-controlled environment.
Antistatic Bags
Antistatic bags have a special coating or contain small filaments that help dissipate any static charge. Always store adapter cards and drives in antistatic bags when they’re not in use and when transporting them—even if you’re just going down the hall or across the room. Antistatic bags dissipate charge most effectively when they’re closed, so it’s a good idea to fold the end over and tape it down with an antistatic sticker if possible.
Do not place components on top of antistatic bags, as charge is directed from the inside of the bag to the outside. Note that regular plastic or paper bags will not protect your components. In fact, plastic baggies conduct static electricity rather than preventing it, so don’t use them!
ESD Straps
Electrostatic discharge (ESD) occurs only when two objects that store different amounts (or potential) of static electricity come in contact. ESD straps, commonly known as antistatic wrist and ankle straps, avoid ESD by keeping you at the same relative electrical ground level as the computer components on which you’re working. An ESD strap consists of a wire that connects on one end to an alligator clip and on the other end to a small metal plate that secures to your wrist (or ankle) with an elastic strap. You snap the alligator clip onto any handy metal part of the computer and place the wrist strap directly on either wrist (not over a shirt sleeve). Figure 4.4-2 shows an antistatic wrist strap grounded to a computer chassis. Others have a prong that you plug into the ground wire of an electrical wall outlet.

FIGURE 4.4-2 An antistatic wrist strap grounded to a computer
By the way, don’t forget to remove your antistatic strap (or at least detach it from the computer) before walking away from your work area!
ESD Mats
Portable antistatic mats (see Figure 4.4-3) provide a work surface that dissipates ESD. They have a small metal clip that you can attach to an antistatic strap to ground out ESD. In addition to helping prevent ESD, these mats help keep your work area organized by giving you a place to put your tools and components while you work.

FIGURE 4.4-3 A typical ESD kit contains a mat and an ESD bracelet.
Antistatic floor mats are basically the same as portable antistatic mats, except much larger. Instead of placing them on top of your work area, you place them on the floor and stand on them while you work.
Self-Grounding
One of the most important steps you can take to prevent the effects of ESD is to ground yourself before you handle computer components. Self-grounding is accomplished by touching a metal surface, such as the exterior of the power supply, before touching any of your system components.
Toxic Waste Handling
Many computer components, such as batteries, CRTs, chemical solvents, and toner kits, contain harmful ingredients. Don’t throw these items in the garbage, as this is wasteful, environmentally damaging, and possibly illegal. Recycle, recycle, recycle! If you can’t recycle an item, dispose of it properly. We all share the same planet.
Different cities and counties have different requirements for safe disposal of materials such as computer components. Always check with the appropriate authorities before tossing that old Pentium 4 on the curb! Proper compliance to local government regulations is essential. Visit your city’s official website for more information.
Batteries
Batteries often contain lithium, mercury, nickel-cadmium, and other hazardous materials. If they are thrown in the garbage and carried off to a landfill, they will contaminate the water and soil. Take batteries to a recycling center or send them back to the manufacturer. Most batteries have disposal instructions printed on them (see Figure 4.4-4). Familiarize yourself with these instructions and follow them.

FIGURE 4.4-4 Typical warning on the label for a lithium-ion battery
Toner
You have a couple of options when dealing with depleted toner and inkjet cartridges. You can refill them yourself, which saves on environmental wear, but an improperly refilled cartridge can wreak havoc on your printer. You can also search the Web to see if commercial toner recyclers service your area. Alternatively, many toner cartridge manufacturers have a recycling program. Check with your vendor and see if this is an option for you.
CRT
Many CRT monitors contain lead and mercury. Both materials are poisonous, so CRTs must be disposed of properly to avoid contamination. To dispose of nonfunctional CRTs, send them to a commercial recycler or contact your city’s hazardous waste management department. They will give you the proper procedure for disposing of them. Don’t be surprised if recycling of CRTs isn’t free—many electronics recyclers charge by the pound.
Cell Phones and Tablets
Cell phones and tablets, although small, should not be thrown away when they have outlived their usefulness. They might contain mercury from their backlights and have rechargeable batteries. Have them recycled by a certified e-waste disposal firm. If a mobile device is still working and is not too old, it may have some trade-in value. Be sure to wipe all data from phones and tablets before recycling or trading them in.
Personal Safety
Whoever told you that IT is a “desk job” didn’t know very much about the actual work of an IT tech. In the course of a typical day, you might find yourself under a desk wrestling with stubborn wiring, plunging into the guts of a malfunctioning PC, cleaning out a computer that looks like the inside of a wet-dry vacuum, or fighting an electrical fire! Here’s how to stay safe at work.
Disconnect Power Before Repairing PC
In the old days, the conventional thinking was that you should leave the computer plugged in while working inside it, to ensure electrical grounding. The opposite is true for modern computers, because modern motherboards always have a small amount of voltage running any time the system is plugged in, even if it’s not running. Therefore, you should completely unplug the system before servicing it or you’ll likely toast something!
Unplugging power supplies does not make them safe enough to work on. The capacitors inside can hold a dangerous electrical charge even when the unit is unplugged, making power supplies extremely risky to open. As the label says, “No serviceable components inside.” With that in mind, the safest method of repairing power supplies is not to repair them at all. It’s better to dispose of them properly and install a brand-new power supply (see Figure 4.4-5).

FIGURE 4.4-5 Typical warning on the label for a computer power supply
Remove Jewelry
Rings, bracelets, necklaces, watches, and other metal adornments can short out devices if they touch the wrong part of a computer. They can also scratch (or be scratched) by scraping against the computer’s surfaces. Remove jewelry and watches before working on or inside of a computer.
Lifting Techniques
It seems that everything we use—computers, printers, monitors—comes to us in heavy boxes. Remember never to lift with your back; lift with your legs, and always use a hand truck if available. If the box says “team lift,” remember: you are not a team—get some help! You are never paid enough to risk your own health.
Weight Limitations
Weight limitations also apply to yourself, carts, and other moving equipment. Take a look at the gross weight on a package or look up the weight of an unboxed device. If it’s beyond your comfort zone, get help. Pay attention to weight limitations on the devices you use to move anything heavy. Also pay attention to weight limitations when wall-mounting monitors. Even relatively light LCD monitors require a mounting arm strong enough to support them.
Electrical Fire Safety
Thankfully, the risk of fire occurring inside your computer is relatively low. If, however, you do experience a computer fire, or any electrical fire for that matter, never try to extinguish it with water. This can cause the electrical current to travel up and straight into you! Instead, use a fire extinguisher certified for fighting electrical fires. These are Class C and Class ABC fire extinguishers (see Figure 4.4-6).

FIGURE 4.4-6 A typical fire extinguisher. Be sure to read the label before using!
Cable Management
A disorderly computing environment invites problems, so successful techs keep it neat. People place computers or peripherals in crazy places: on rickety desks, cardboard boxes, and other places where they could easily fall. Arrange your computer and peripherals safely on the floor or on a sturdy desk. Tape or cover cords (using cable raceways or trays) running along the ground or walls (Figure 4.4-7) to avoid people tripping on them or accidentally ripping a computer off a desk. If you see a potential hazard at a work site—even one that’s not yours—report it or fix it. You’re the expert, so take charge!

FIGURE 4.4-7 A cable raceway in use in a small office
If you are responsible for running network cable, make sure that plenum-grade (aka plenum) cable is used when routing cables through airspace such as a suspended ceiling. Plenum cable doesn’t produce noxious fumes when burned. Standard network cable, by contrast, has a PVC jacket that burns easily, producing a lot of noxious fumes.
Safety Goggles
If you need to cut a bit of aluminum to rig up a part for an old PC or use compressed air or a vacuum cleaner to clean out an old PC, put on safety goggles. A tiny shard of metal or bit of dust can ruin your day—and if your eyes are damaged, a lot of upcoming days will also be ruined.
Air Filter Mask
You need to protect yourself (and your coworkers) from dust and debris when servicing, storing, or disposing of equipment. Everyone in the work area should wear an air filter mask that is designed to handle appropriate environmental risks.
Compliance with Government Regulations
Be sure to follow applicable OSHA or other safety regulations when building, repairing, cleaning, or dismantling equipment. These regulations might address issues such as ventilation, protection against dust, cable management, and other issues. Proper compliance with government regulations is essential.
REVIEW
Objective 4.4: Explain common safety procedures Common safety procedures include
• Equipment grounding
• Proper component handling and storage through the use of antistatic bags, ESD straps, and ESD mats
• Using proper handling and disposal procedures for anything containing toxic waste, such as batteries, toner, CRTs, and mobile devices
• Taking personal safety precautions, which include (among others) disconnecting power before repairing a PC, removing jewelry before working inside a computer case, using safe lifting techniques, noting weight limitations of moving equipment, using Class C or ABC fire extinguishers for computer equipment fires, practicing good cable management, and wearing safety goggles and an air filter mask when appropriate
• Complying with government regulations regarding occupational health and safety
4.4 QUESTIONS
1. An electrical fire has broken out in an old laser printer. Which of the following should be used to put out the fire?
A. Class A fire extinguisher
B. Water
C. Class ABC fire extinguisher
D. Sprinkler system
2. What are two environmental threats found in CRT displays? (Choose two.)
A. Lead
B. Lithium-ion batteries
C. Mercury
D. MSDS
3. Which of the following is not recommended before working on a PC?
A. Disconnecting the power supply from the AC outlet
B. Using an ESD strap
C. Using an ESD mat
D. Spraying antistatic spray on the PC
4. You are walking through a work area where computers and components are being prepared for storage. You notice that a network interface card has been placed on top of an antistatic bag. What should you do?
A. Connect an ESD strap to the bag
B. Move the card to a piece of paper
C. Place the card inside the bag after self-grounding
D. Nothing; it’s OK to use an antistatic bag this way
5. A network cable running across the floor of a busy hallway is an example of which of the following:
A. ESD grounding
B. Poor cable management
C. Cable testing
D. A practical joke setup
4.4 ANSWERS
1. C An electrical fire is a Class C fire, so a Class ABC fire extinguisher is the best choice.
2. A C Lead and mercury are contained in typical CRTs as well as more recent technology.
3. D Spraying the hardware can damage it.
4. C The ESD bag can only protect a NIC placed inside it.
5. B This is an example of poor cable management, because the cable presents a tripping hazard.

Objective 4.5 Explain environmental impacts and appropriate controls
Environmental impacts are the results of any changes in the environment that can affect computer equipment such as heat, humidity, and lightning; or can be caused by servicing, using, or disposing of technology. This objective covers the details of how to have minimal environmental impact when using technology.
MSDS Documentation for Handling and Disposal
All batteries, chemicals, and other hazardous materials come with a material safety data sheet (MSDS) that documents any safety warnings about the product, safe methods of transportation and handling, and safe disposal requirements. If you have any doubts or questions about how to handle or dispose of chemicals or compounds, check the applicable MSDS. If the MSDS for a product or substance is missing, you can obtain a copy from the manufacturer or locate it on the Internet.
Temperature, Humidity Level Awareness, and Proper Ventilation
Good techs keep up with weather conditions. The temperature and humidity level outside can dramatically affect the risk of ESD inside. If the weather is cold and dry, the potential for a computer-killing zap is greatly increased. Take extra precautions to prevent ESD when the weather calls for it.
Proper environmental controls help secure servers and workstations from the environmental impact of excessive heat, dust, and humidity. Such environmental controls include air conditioning, proper ventilation, air filtration, and monitors for temperature and humidity. A CompTIA A+ technician maintains an awareness of temperature, humidity level, and ventilation so that he or she can tell very quickly when proper levels or settings are out of whack.
Dust and debris aren’t good for any electronic components. Equipment closets filled with racks of servers need proper airflow to keep things cool and to eliminate dusty air. Make sure that the room is ventilated and air-conditioned and that the air filters are changed regularly. This provides protection from airborne particles as well as heat and humidity.
Power Surges, Brownouts, and Blackouts
Your computer needs power to run properly, but various factors can turn what should be a steady stream of electricity from the wall socket into either a trickle or a fire hose. Power fluctuations can wreak havoc on an unprotected system. Surges and sags can damage power supplies and components and cause file corruption. It’s important that you know how to protect your computing environment from electrical power spikes, power sags, and power losses. Related issues that CompTIA doesn’t specifically list as environmental impacts—but that might appear on the exam—are lightning strikes and electromagnetic interference, which are discussed separately after the specified impacts.
Power spikes or power surges occur when the voltage on your power line rises suddenly to above-normal levels. Power spikes are extremely dangerous and can destroy computers, monitors, and any other component plugged into the affected power line.
A brownout occurs when the supply of electricity drops dramatically but does not go out completely. During a brownout, you’ll notice lights flickering or growing dim. When the power rises back up to its original level, your computer might not be able to handle the drastic change, and damage may occur.
Blackouts occur when power goes out completely. The danger of a blackout is twofold. First, you may have data loss or corruption when the power goes out. Second, the power surge when the electricity comes back on may damage your system’s electronics.
As you learned in the “UPS” and “Surge Protector” sections in Objective 4.3 of this domain, uninterruptable power supplies (battery backups) are the solution to brownouts, sags, and blackouts, while high-quality surge suppressors (surge protectors) help mitigate the damage that can be caused by power surges. The cost of a good UPS or surge suppressor is nothing compared to the cost in time and money caused by lost components or corrupted files that you may have to endure if you don’t use either one.
Lightning
Lightning storms are an underrated hazard. Leaving a computer plugged in during a lightning storm is asking for trouble. A surge suppressor won’t protect your plugged-in computer (or any other electronic device) from the massive electrical discharge of a lightning strike.
EMI
A magnetic field interfering with electronics is electromagnetic interference (EMI). EMI isn’t nearly as dangerous as ESD, but it can cause permanent damage to some components and erase data on some storage devices. Long cable runs tend to pick up EMI, especially if a power cable is running alongside a data cable. You can prevent EMI by keeping magnets away from computer equipment.
EMI can be controlled by using cables with a Mylar coating and through the use of special EMI and RFI noise filters, typically built into better quality surge suppressors, UPS units, or available as stand-alone products. You can also minimize EMI by moving data cables away from power cables and by shortening the cables you use.
Protection from Airborne Particles
When you use canned air to blast dust and hair from air vents and other openings in a computer or peripheral, you’re helping keep the hot air flowing out and cool air flowing in to maintain the appropriate temperature inside the computer or peripheral. This will extend the life of your computer. When you’re using canned air, remember the words of Corporal Hicks from the Aliens movie, and use “short, controlled bursts.” If you haven’t dusted the computer or peripheral in a while, take it outside before spraying. Otherwise, you’ll spread dust everywhere.
However, you want to prevent the dust, dirt, and grime inside the computer or peripheral from winding up where it doesn’t belong—your lungs, nose, and mouth, for example. Here’s how.
Enclosures
Ensuring proper protection from airborne particles encompasses devices and people. Put your electronics into the right enclosures with good air filters. When you’re cleaning very dirty equipment, if you have an enclosure with a built-in vacuum, consider using that to catch the dust you shake loose.
Air Filters/Mask
When shopping for air filters/masks, be sure to look for masks and air filters with appropriate ratings. Masks with N95 ratings are designed to filter out 95 percent of particles of at least 0.3 microns in size (N97 = 97 percent, N100 = 100 percent). Note that most dust particles that you might encounter in technology or buildings (such as copier toner, fiberglass, sawdust, asbestos) have particle sizes in excess of 0.3 microns. N-series masks do not provide any protection against oil, however.
Dust and Debris
Dust and debris are bad news for electronic components. Ideally, you’d like to stop dust and debris from getting into systems because they can clog air intakes and air exhausts, cause overheating, and in some cases, “kill” a system.
Compressed Air
You can use canned air to loosen dirt and dust from delicate components. Canned air comes in a couple of forms: the liquid propellant kind and the kind that uses small cartridges of compressed CO2. You can find both at computer stores, office supply stores, camera shops, and big-box stores that sell electronics (see Figure 4.5-1).

FIGURE 4.5-1 Typical canned air with extension tube attached
Follow three rules when using canned air:
• Never breathe this stuff in. It’s not that kind of air, and inhaling it can, quite literally, kill you!
• With regard to the liquid propellant type of canned air, always keep the can upright. Tilting or turning the can upside down causes the liquid inside to come squirting out. This liquid can cause frostbite to the tech and irreparable damage to any computer components that it touches.
• Don’t shake canned air cans. They don’t need to be shaken to work, and you run a small but real risk of the can exploding in your hand.
Vacuums
Small, hand-held vacuums designed specifically for use on electronics (such as shown in Figure 4.5-2) suck up dirt and dust loosened by a brush or canned air. Note that you should definitely not use a common household vacuum cleaner. These create static electricity and can toast your computer! Some computer vacuums can also act as blowers. Some stand-alone blower products go by names such as “electric dusters.” They can be used as alternatives to canned air and do not create condensation or contain harmful liquid propellants.

FIGURE 4.5-2 A non-static vacuum
Compliance to Government Regulations
Whether you are disposing of unwanted equipment or supplies or cleaning equipment, follow the rules! Specifically, use cleaners that are approved for the job and follow government regulations for ventilation, filters, air masks, and the like. Don’t let a visit from OSHA or the EPA ruin your day.
REVIEW
Objective 4.5: Explain environmental impacts and appropriate controls To control environmental impacts, understand the following methods:
• Consulting MSDS documentation for proper handling and disposal of chemicals and other substances
• Maintaining temperature and humidity level awareness and proper ventilation to avoid ESD, equipment overheating, and other issues
• Protecting computer equipment from the dangers of power surges, brownouts, and blackouts by using battery backups and surge suppressors
• Protecting people and equipment from airborne particles by using enclosures, air filters, and air masks
• Protecting computer equipment from dust and debris by using compressed air and an electronics vacuum
• Complying with government regulations regarding environmental issues
4.5 QUESTIONS
1. You are helping to clean out an office that has a chemical you are unfamiliar with stored in a closet. Which of the following is most useful in determining safe disposal and handling procedures?
A. Government regulations
B. MSDS
C. Product labeling
D. Guesswork
2. As a member of the environmental controls team, you are helping to set up an unfinished building as a hot site for IT use in case of a disaster affecting the primary IT location. Which of the following does not fit into your team’s responsibilities?
A. Networking
B. Ventilation
C. Air filtration
D. Temperature monitoring
3. A client is reporting problems with her computer. Using a multimeter, you determine that the electricity available at the client site is about 87-V AC (the standard for the location is 115-V AC). Which of the following conditions most accurately describes the electrical problem?
A. Power surge
B. Blackout
C. Brownout
D. EMI
4. While working on a motherboard with an overheating processor, you decide to clean the fan and heat sink on top of the CPU. Which of the following should you do while using canned air for this job?
A. Shake the can before using
B. Turn the can to get a better angle
C. Sniff the air coming from the can
D. Keep the can upright
5. You are considering whether to remove components from a working PC on a day that is cold and very dry. You feel a spark when you touch the doorknob to go into the workroom. Which of the following would be the best move to make?
A. Wait for a day with more humidity
B. Keep touching metal as you move around the room
C. Use an ESD mat
D. Use an ESD wrist strap
4.5 ANSWERS
1. B The material safety data sheet (MSDS) for the chemical has the most information about proper handling and disposal procedures.
2. A Networking is not an environmental control issue.
3. C Low electrical voltage is considered a brownout.
4. D Keeping the can upright is the only recommended procedure of the ones listed.
5. A Because the choice of when to remove equipment is up to you, waiting for a day with more humidity (and thus less risk of ESD) is the best option.

Objective 4.6 Explain the processes for addressing prohibited content/activity, and privacy, licensing, and policy concepts
Sooner or later, you’ll probably come face-to-face with a user who is misusing their computer or network access. Maybe they’re storing pornography or running a BitTorrent server, or cranking out posters of their children’s favorite bands on the company color printer. In this objective, you learn how to deal with prohibited content or activity. And, you also learn about privacy, licensing, and policy concepts that can help to keep users and companies out of trouble.
Incident Response
The incident response process is a series of guidelines that help you properly deal with prohibited content or activity.
First Response
As a tech, you’ll need to deal with people who use company computers in prohibited ways. Because you’re not a police officer, in most you cases you should not get involved, but if you encounter something bad—really bad—on a system or device you support, everyone may turn to you for action if you’re the first tech person on the scene. For the most part, avoid reading any personal information, whether confidential or not, on a user’s computer or device—but if you identify an obvious felony or dangerous behavior in the course of your job duties, you’ve just become the first line of defense and need to act accordingly.
Depending on the type of incident, you might detect it yourself by examining log files, by servicing a computer, or by listening to talk around the office coffee maker. No matter how you determine there’s a problem, the incident response process needs to start right away.
Identify
When confronted with a potential incident, you need to determine if it’s really an incident. Use common sense, but keep in mind that most organizations have an Acceptable Use Policy (AUP) that employees must read and sign that defines what actions employees may or may not perform on company equipment. Remember that these polices aren’t just for obvious issues such as using a computer for personal use. These policies cover use of computers, phones, printers, and even the network itself. The AUP will define the handling of passwords, e-mail, and many other issues.
Report Through Proper Channels
You report violations through the proper channels: directly to a security officer or incident response leader if your organization has one, and to your supervisor otherwise. Do not speak to the person making the infraction unless your supervisor approves it.
Data/Device Preservation
To prevent changes to a system after a violation has been detected, you must isolate the system: take it off the network and store it in a secure location.
Use of Documentation/Documentation Changes
When an incident is detected or reported, be sure to document the relevant facts, such as
• What account was used?
• What devices were used?
• What software was used?
• What types of content were discovered?
• When did the violation take place?
Chain of Custody
The chain of custody depends, in part, upon careful documentation of the computer’s location before the violation was detected, who had access to it after the violation was detected, and what steps were taken to isolate it.
A device’s data must be preserved in case it becomes evidence, so the device’s location and who has touched it needs to be recorded to prove the data hasn’t been tampered with; you need to establish a chain of custody documenting this history. You should have a legal expert to guide you, but the following are fairly common rules:
1. Isolate the system. Shut down the system and store it in a place where no one else can access it.
2. Document when you took control of the system and the actions you took: shutting it down, unplugging it, moving it, and so on. Don’t worry about too much detail, but you must track its location.
3. If another person takes control of the system, document the transfer of custody.
Tracking of Evidence/Documenting Process
Record information that indicates the illegal or unauthorized use of the computer or device. Some clues to look for include
• Dates of illegal files
• Event logs
• Dates unauthorized software was installed or updated
• Browser cache
• Recently visited IP addresses
• Dates of and contents of deleted files
• Print server logs
• Proxy server logs
Licensing/DRM/EULA
Software compliance is simple enough if you have an explicit list of allowed software and strict controls on who can install programs, but less restrictive regimes require more effort to stay in compliance with software licenses.
Like other creative acts worthy of copyright protection, software developers are granted copyright to software they create, enabling them to decide how or if others can obtain a license to use the software. The licensing can be commercial or noncommercial, personal or enterprise. The software can be closed source or open source. You have a legal obligation to use the software in compliance with its license, which typically entails the following:
• Paying money for software released under a commercial license and complying with terms that indicate whether the license supports personal or private use.
• Complying with any End User License Agreement (EULA) you agree to when you open or install software, which typically specifies how you may use the software and whether you may share it. If the software uses digital rights management (DRM) techniques to protect the application or its files, the EULA typically forbids you from breaking, reverse-engineering, or removing these protections (or helping anyone else do so).
• Observing stipulations in noncommercial software licenses that specify whether the software is free for all uses, free only for personal/educational use, or requires a special commercial license for commercial use.
• Complying with additional stipulations in open-source software licenses that specify how you may use the source code. These licenses commonly give you the right to modify the source, but may require you to release your modifications for free as well.
Open-Source vs. Commercial License
Generally, Windows, iOS, and macOS operating systems and apps are closed-source software and require a commercial license. Android and Linux, by contrast, are open-source operating systems. Although most Android apps are closed source and require a commercial license, Linux apps are typically open source and free to use.
Observe stipulations in closed-source software licenses regarding whether you may modify the software and whether you may include it in or distribute it with one of your own products.
Personal License vs. Enterprise Licenses
Software that is licensed to an individual for a single computer cannot be used on multiple computers: it’s a violation of the license agreement. Enterprise licenses may (depending on the specific license agreement) permit individuals to use company-licensed software on their personal systems.
Given the high potential penalties for pirated software, it just makes sense to make sure that users understand what the license on a particular program permits and use it per that agreement.
Regulated Data
Larger organizations, such as government entities, benefit greatly from organizing their data according to its sensitivity and minimizing surprises by keeping computer hardware and software as uniform as possible. This also helps maintain compliance with government and internal regulations; common examples are rules regarding approved software and regulations on how you must handle personally identifiable information (PII) such as health or academic records.
A common data classification scheme that flags documents as public, internal use only, highly confidential, top secret, and so on, helps employees (including techs) know what to do with documents and hardware containing them (such as using different rules to recycle hard drives that hold top secret data). Your strategy for recycling a computer system no longer being used, for example, will differ a lot if the data on the drive is classified as internal use only or top secret.
Table 4.6-1 identifies different types of regulated data.
TABLE 4.6-1 Types of Regulated Data

Follow All Policies and Security Best Practices
As you can see from Table 4.6-1, different industries must protect different types of information about their clients. The one key to follow consistently is this: whatever the regulations are in your industry, follow them—and maintain the specific security best practices for that industry.
REVIEW
Objective 4.6: Explain the processes for addressing prohibited content/activity, and privacy, licensing, and policy concepts The incident reporting process includes the following steps:
• First response—Identifying whether an incident has occurred and, if so, reporting it through proper channels and securing any data or devices related to the incident
• Use of documentation/documentation changes—Documenting the details about the incident (where, when, equipment, account, and so on)
• Chain of custody—Tracking what happens to a system after an incident is reported, including the evidence/documenting process: looking for clues without affecting the system’s contents
Licensing issues include
• Understanding the details of a specific program’s licensing agreement
• Understanding the differences between open-source, closed-source, and commercial licenses and the differences between personal and enterprise licenses
Be prepared to identify the following types of regulated data and how they are regulated:
• PII (personally identifiable information)
• PCI DSS (Payment Card Industry Data Security Standard)
• GDPR (General Data Protection Regulation that applies to any organization that handles PII of EU citizens)
• PHI (protected health information regulated by HIPAA)
Make sure you follow all policies and security best practices.
4.6 QUESTIONS
1. You are evaluating a program’s source code to see if it can be modified for your company’s needs. The program is free for personal use but must be licensed with a fee for company use. Which of the following phrases best describes its company licensing arrangement?
A. Free open source
B. Closed source
C. Commercial open source
D. Noncommercial
2. You are attempting to determine if an incident involving company IT resources qualifies as a violation. Which of the following should you consult?
A. PII
B. AUP
C. HIPAA
D. GDPR
3. You are attempting to determine if illegal websites were accessed by an employee. Which of the following would be the most useful source to discover this information?
A. Browser cache
B. Event logs
C. Print server logs
D. Windows installation logs
4. Which of the following is an example of PII?
A. ZIP code
B. Phone number
C. Gender
D. Citizenship
5. A U.S.-based healthcare company has operations in the UK and France. It accepts credit and debit card payments. Which of the following types of regulated data must it protect?
A. PHI
B. GDPR
C. PCI DSS
D. All of the above
4.6 ANSWERS
1. C The software has a licensing fee (making it commercial), but the source code can be modified (open source).
2. B The Acceptable Use Policy is an organization’s guide to unacceptable IT resource use.
3. A The browser cache should be checked. Although it can be deleted, it can be recovered to see which websites were visited.
4. B A phone number is PII because it can be used to identify an individual.
5. D The company is involved in health care (PHI), has business dealings in the UK and France (GDPR), and handles payment cards (PCI DSS).

Objective 4.7 Given a scenario, use proper communication techniques and professionalism
You will encounter all sorts of people as a tech. Emotions will run from anger, to fear, to frustration. You’ll find bluster, smiles, patience, impatience, and much more. Treat the customer with respect. This objective helps you focus on the specifics to make that happen.
Communication Techniques
Knowing how to communicate with customers is a key “soft skill” for anyone who works with the public. For IT workers in particular, communicating with customers is vital to solving their problems and developing a good long-term professional relationship. Here are some tips to help you achieve these goals.
Use Proper Language and Avoid Jargon, Acronyms, and Slang, When Applicable
We live in a vulgar and informal age, but that’s no excuse for sounding like you’ve overdosed on reality programs when you are speaking with your customers. Slang is out, and proper language is in.
You’re the technology expert, but if you don’t avoid jargon and acronyms when speaking with your customers, you’ll sound like an arrogant jerk, not an expert, and your customers won’t understand your tech speak. Make sure you understand technology well enough to translate it into ordinary language—if you don’t, you’re not as knowledgeable as you think you are. Practice effective communication. The best techs know both technology and how to talk with users.
Maintain a Positive Attitude/Project Confidence
Maintain a positive attitude when dealing with a difficult customer or situation. Project confidence that you can solve the problem efficiently and get the user back to work. Don’t argue with the customer or get defensive if he or she implies that the computer problem is somehow your fault. It happens!
Actively Listen (Taking Notes) and Avoid Interrupting the Customer
Effective communication in “computerese” requires active listening to get to the heart of the problem, which in turn calls for the proper use of language. You know and speak tech. Chances are that your customer doesn’t. Getting through this language barrier is essential for solving problems.
Actively listening means focusing your attention on the customer’s words. They might not make sense at first, so take notes. The customer might say something like, “I was working away, but a clock started ticking inside the CPU, then my screen went blue and I can’t get the computer to start at all.” Oy! Don’t interrupt the customer. Let him or her tell you the story. Because you wrote it down, you likely can interpret the non-technical language into something that potentially makes sense.
Many users call the case or system unit a CPU. A ticking sound inside a case often points to a dying hard drive. A blue screen is a classic sign of a non-maskable interrupt (NMI), better known as the Blue Screen of Death (a term you don’t want to use in front of a customer, by the way!) in Windows (see Figure 4.7-1). The user’s hard drive might have just died. If the user has burned his hand on the case, that could point to an overheating issue that caused the problem—and potentially a lot more than just a dying drive.
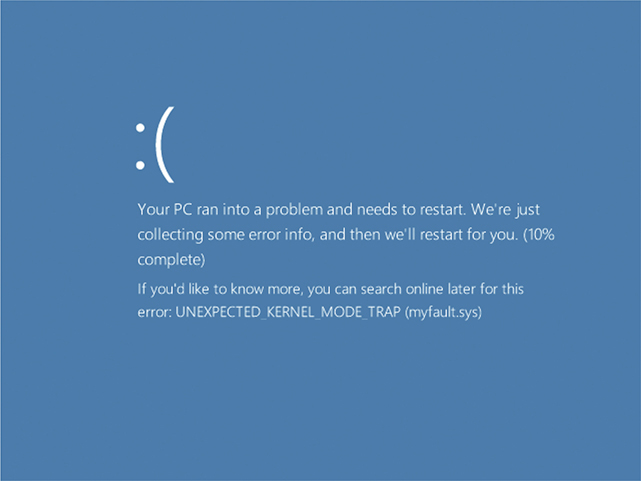
FIGURE 4.7-1 The Blue Screen of Death (BSoD) in Windows 10
Be Culturally Sensitive
With a diverse population needing help from tech experts like you, you need to deal graciously with cultural differences. If a customer’s religious holiday conflicts with your work schedule, the customer wins. If the customer wants you to take off your shoes, take them off. If the customer wants you to wear a hat, wear one. If a person’s title happens to be in a language you don’t speak, figure out how to say it before arriving on the scene. That’s what Google Translate is for! Be culturally sensitive. Always use the appropriate title, personal or professional. Never assume that using a customer’s first name establishes rapport. In fact, you shouldn’t use a customer’s first name unless the customer requests that you do so.
Professionalism
Professionalism is a way to describe someone who is in control of an unexpected situation. From traffic jams to customer frustrations, you are likely to encounter less-than-ideal situations. Here are some ways to defuse potential trouble spots so you can solve customer problems.
Be on Time (if Late, Contact the Customer)
Be on time, whether making a scheduled phone call or arriving at a job site. If you are driving, plan ahead to ensure you know the route to the customer’s premises, and build in extra time for traffic congestion or other unforeseen issues. If you are running late, contact the customer immediately, apologize, and provide an estimated time of arrival. We live in the future: call, text, or alert your dispatcher to notify the customer. This is more than common courtesy; it’s an essential skill for the professional tech.
Avoid Distractions
Avoid distractions that take your focus away from the user and addressing his or her computer problem.
• Don’t take a personal call when interacting with a customer.
• Don’t text or tweet or respond to messages on other social media sites.
• Don’t chat with coworkers; keep your focus on interacting with the customer.
• Avoid any kind of personal interruption that doesn’t deal directly with fixing the computer; it will only irritate the customer.
Dealing with Difficult Customers or Situations
Inevitably, you’re going to encounter difficult customers in difficult situations. Computer issues tend to cause stress, and some people become difficult to deal with when they are stressed out. As a professional tech, you need to know how to defuse the tension and get the job done.
Do Not Argue with Customers and/or be Defensive You want to fix the customer’s problem—and the customer really wants it fixed. You have the same goal. Don’t argue or be defensive. Assure the customer that you’re here to help—and be helpful!
Avoid Dismissing Customer Problems What might be an easy, five-minute fix to you might be the potential “end of the world” for the customer. Don’t dismiss their problems, no matter how many times you’ve seen a similar problem before. Remember, this one might be different!
Avoid Being Judgmental Customers would fix their problems themselves if they knew how. They don’t—and that’s why they call you. If you discover that a customer caused the problem, don’t be judgmental about how the device was damaged or files were deleted. Keep an even, nonaccusatory tone. You’ve probably made a few mistakes in your professional life too. Fix the problem and be thankful the customer called you—and not somebody else—for help. It’s good job security.
Clarify Customer Statements (Ask Open-Ended Questions to Narrow the Scope of the Problem, Restate the Issue, or Question to Verify Understanding) Customers with technology problems are likely to be long on fear and frustration and short on clarity when you first talk to them. So, it’s up to you to clarify customer statements. Ask open-ended questions, such as “What other strange or unusual things about the computer have you noticed recently?” A “nothing, really” response from the customer has a wildly different meaning than “I burned my hand on the CPU a couple of days ago.” Open-ended questions help narrow the scope of the problem.
Also, restate the issue or question to verify your understanding, but use proper, simple language. Avoid jargon and acronyms. Definitely skip the silly computer guy slang, like calling a Windows PC “the comp” or a motherboard a “mobo.” That stuff just makes customers defensive. Once you think you understand both the scope and nature of the problem, go back to your notes and you might find a good explanation.
Do Not Disclose Experiences via Social Media Outlets After you finish a job (or even during one in progress), never share any “funny” stories about the customer or the activities around you. Certainly share professional and technical details with coworkers and any personal issues with your supervisor, but definitely do not disclose experiences via social media outlets such as Facebook and Instagram. Someone knows someone without fail, and your words will come back to haunt you.
Set and Meet Expectations/Timeline and Communicate Status with the Customer
Expectations management means to give a customer as accurate an estimate as possible regarding how long it will take you to fix the computer problem. Plus, it means providing status updates if you expect to finish more quickly than your initial estimate or if things seem to be taking longer than first predicted. Also, many times with a computer issue, you can fix the problem and avoid a similar problem in the future in several ways. These options boil down to money.
Offer Different Repair/Replacement Options, if Applicable If applicable, offer different repair/replacement options and let the customer decide which route to take.
Provide Proper Documentation on the Services Provided At the completion of work, provide proper documentation of the services provided. Describe the problem, include the time and day you started work and completed work and the number of hours you worked, provide a list of parts you replaced, if applicable, and describe the solution.
Follow up with Customer/User at a Later Date to Verify Satisfaction Follow up with a customer/user at a later date to verify satisfaction. This can be a simple follow-up, usually just a phone call, to confirm that the customer is happy with your work.
Deal Appropriately with Customers’ Confidential and Private Materials (Including Those on Computers, Desktop, Printers, etc.)
You have a lot of power as a tech at someone else’s computer. You can readily access files, browsing history, downloads, and more. Don’t do it! You need to deal appropriately with customers’ confidential and private materials. This includes files on the computer, items on a physical desktop, and even pages sitting in a printer tray. If you are caught violating a customer’s privacy, you not only will lose credibility and respect, but you could also lose your job.
REVIEW
Objective 4.7: Given a scenario, use proper communication techniques and professionalism The keys to effective communications with customers include
• Using proper language
• Avoiding jargon, acronyms, and slang
• Maintaining a positive attitude and projecting confidence
• Actively listening, taking notes, and avoid interrupting the customer
• Being culturally sensitive, including using professional titles when appropriate
Maintaining professionalism as an IT tech at all times requires
• Being on time or contacting the customer before you’re late
• Avoiding distractions such as personal calls, texting, social media sites, talking to coworkers while interacting with customers, and personal interruptions
• Dealing with difficult customers or situations by following these practices:
• Don’t argue or be defensive
• Avoid dismissing customer problems
• Avoid being judgmental
• Clarify customer statements by asking open-ended questions
• Don’t disclose experiences on social media
• Setting and meeting (or exceeding) expectations/timeline and communicating status with the customer, including
• Offering different repair/replacement options when applicable
• Providing proper documentation on the services provided
• Following up to verify satisfaction
• Dealing appropriately with confidential and private materials, including print jobs, material on desktops, data on computers, and so on
4.7 QUESTIONS
1. You allowed plenty of time to reach your destination, but a massive traffic jam caused by a couple of accidents has disrupted your schedule. You will be late to your next appointment. What should you do?
A. Don’t worry about it. The customer listens to traffic reports every ten minutes and will know why you’re late.
B. Abandon your vehicle and call a taxi to pick you up from the service drive.
C. Call your supervisor and ask her to call the customer.
D. Call the customer yourself and explain the situation, apologizing for being late.
2. You open the customer’s computer, a four-year-old system running a Core i3 that is no longer being produced, only to find that smoke is coming from the motherboard. What should you do?
A. Quote the customer a price for replacing the entire computer
B. Offer the customer the option to repair or replace the system
C. Find out if a similar motherboard is available and order it
D. Try to replace the burnt chip
3. You are planning a date with your spouse and haven’t heard back about what time you are meeting. You get a text message while you are discussing repair options with your client. What should you do?
A. Check the message while trying to conceal the phone from your client
B. Ask your client if you can excuse yourself while you view the message
C. Check the message after the meeting with the client is over
D. Tell your client you can’t stay late because you’re going out to dinner that night
4. You have just heard another technician’s phone conversation with a client. It went like this: “Dude, your mobo is shot and your distro is dead! Your burner is burned up. Howzabout I get you a deal on a sweet little laptop! Is that OK, Doc?” Which of the following did you hear? (Choose all that apply.)
A. Use of slang
B. Use of jargon
C. Proper use of titles
D. Customer offered options to repair or replace computer
5. You have just completed a diagnostic test on your client’s computer, identified a defective memory module, replaced it, and removed three of the most dangerous current malware threats. You now need to provide documentation on the services you provided. Which of the following best describes the work you did?
A. Fixed your PC
B. Broke RAM, replaced with good RAM
C. Turned your frown upside down
D. Diagnostics, defective memory replaced, malware removed
4.7 ANSWERS
1. D Always call the customer yourself if you’re going to be late. If you don’t have the right contact information, get it from your supervisor.
2. B Even if you think it’s cheaper to replace the computer, offer a repair option. For example, some older systems must be maintained because of compatibility issues with newer hardware or operating systems.
3. C The message can wait. If necessary, excuse yourself after the meeting and head to the restroom to read it.
4. A B Slang and jargon abounded, not good communication techniques!
5. D This represents a professional, accurate, concise description of services rendered.

Objective 4.8 Identify the basics of scripting
A script is a small program used to help automate computing tasks. Scripts are written in a text editor and executed from a command prompt. Scripting, which is a kind of programming, has the power to make complex or repetitive data manipulation and machine configuration easier. For purposes of the CompTIA A+ 220-1002 exam, you don’t need to be a scripting expert, but you do need to be able to identify the basic scripting concepts covered in this objective.
Script File Types
Scripts are stored as text files using the extensions discussed in the following sections. Because they are stored as text files, scripts can be created using a text editor such as Notepad. However, some scripting languages include some type of integrated development environment (IDE) or integrated scripting environment (ISE) that can be used to edit and run scripts.
.bat
The .bat file extension is used by the simple scripting language originally developed for MS-DOS and still used from the command prompt in Windows. In addition to running commands in sequence, a .bat file (also known as a batch file) can also display each command as it runs (using echo) and include remarks that explain the purpose of the file (using REM).
Use Notepad or a word-processing program that can save files as plain-text files to edit a .bat file. There are no restrictions on .bat files, so a potentially harmful .bat file can be run without being blocked by Windows. Be sure to view the contents of an unfamiliar .bat file before running it.
This simple batch file creates a list of subfolders of C: drive’s root directory (folder) after pausing and redirects the output to a text file:

Figure 4.8-1 is a typical example of the folders.txt file being opened in Notepad.
FIGURE 4.8-1 Notepad viewing the directory list file created by sample.batBatch
.ps1
The .ps1 file extension is used by PowerShell scripts. PowerShell is an object-oriented scripting language built into Windows 7 and later. Windows 10 can be configured to use PowerShell instead of cmd.exe as its default command interpreter. You can also run PowerShell from within its ISE (integrated scripting environment).
PowerShell includes support for variables, looping, cmdlets (small .NET-based apps), and consistent syntax using a verb-noun command structure. To make transition easier to PowerShell, it supports aliases. Users can enter commands from cmd.exe or a Linux terminal and PowerShell will run its matching command.
The following script displays the aliases for various cmd.exe commands, counts the number of cmdlets available on the author’s computer, displays the number of cmdlets available, and displays Windows version and hardware information obtained with the command-line systeminfo program.

.vbs
The .vbs file extension is used for Visual Basic Script, also known as VBScript. This is a Microsoft scripting language derived from Visual Basic. The macro functions of Microsoft Excel and other Office apps with macro support refer to it as Visual Basic for Applications (these use the .vba file extension). VBScript can also be run outside of Microsoft Office by using Windows Script Host, and it supports HTML applications such as Internet Explorer and Microsoft IIS. You can use Notepad or another plain-text editor to create VBScript files.
Here’s a simple VBScript that adds the total of the numbers from 1 to 34 and displays the answer in a GUI message box. After you close the first message box, the script multiplies the result by 2.3 and displays the answer in another GUI message box.

Alternatively, you can use document.write (as in JavaScript, covered a bit later) to display the messages in a normal display.
Figure 4.8-2 illustrates the output from this script along with the icon used by File Explorer for Visual Basic Script files.

FIGURE 4.8-2 VBScript file as shown in File Explorer and second output windowVBScript
If you incorporate VBScript into HTML (supported by Internet Explorer 11 and earlier versions), be sure to place the following at the beginning of the script:
<script language = "vbscript" type = "text/vbscript">
Place this at the end of the script:
</script>
.sh
The .sh file extension is used for Bash shell files, a type of executable file used originally on UNIX systems and now used on Linux or macOS in Terminal mode.
Bash files require execute permission to run. The easiest way to gain access to run a .sh file is to use the sudo command (sudo enables the current user to run as root, or superuser) in front of the bash command:
sudo bash script.sh
Here’s a simple .sh script that includes a statement that prints text onscreen using echo, gets the user’s name, uses comments (#), and performs math:

Figure 4.8-3 illustrates the output from this file as displayed in Ubuntu Linux’s terminal.
FIGURE 4.8-3 Terminal window in Ubuntu Linux running Add_Bash.sh as superuserBash
.py
A .py extension is used for Python scripts. Python is a versatile programming language that is included in macOS and most Linux distros. The current version is Python 3, although Python 2 is still in wide use. Python versions are available for Windows as well as macOS and Linux.
If you are not using a system with Python already installed, you can download the Python IDLE (which combines a text editor with a Python interpreter) from the Python.org website. You can also run Python in your browser at various websites such as Code Academy (www.codeacademy.com) or Code the Blocks (https://codetheblocks.com).
Here’s a simple .py script that includes a statement that prints text onscreen, gets the user’s name, inserts comments (#), and performs math. Compare it to the Bash (.sh) script shown in the previous section.
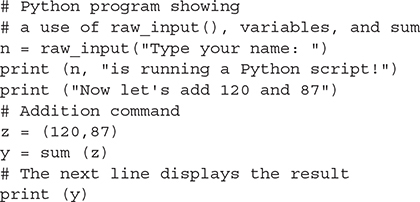
Figure 4.8-4 illustrates how this script appears when entered and run at the Code the Blocks website (the Sandbox tab is used for your own scripts) along with the icon used by File Explorer for Python script files.

FIGURE 4.8-4 Running Adding.py at the Code the Blocks website
.js
A .js extension is used for JavaScript scripts. JavaScript is widely used in web development and web applications, web servers and server apps, smartwatch and mobile apps, and more. It is an object-based, interpreted language that, despite its name, has no connection to Java.
A free JavaScript IDE is available for Windows, macOS, and Linux from Visual Studio Code (https://code.visualstudio.com). You can also run JavaScript in your browser at various websites such as Code Academy or JavaScript Editor (https://js.do). Because JavaScript is used in web development, you can use HTML tags for text enhancement.
Here’s a simple .js script that can be inserted into HTML code. It includes statements that set up variables, print text, and insert comments (//), includes some HTML, and performs math.

Figure 4.8-5 illustrates how this script appears when entered and run at the JS.do website along with the icon used by File Explorer for JavaScript files.

FIGURE 4.8-5 Running Adding.js at the JS.do website
Environment Variables
Environment variables are used by all modern operating systems’ scripting languages to provide shortcuts to common locations and features.
Examples of environment variables in Windows include %USERPROFILE%, which can be used to display the current user’s profile folder (directory), and %PATH%, which displays the locations the command interpreter will look for an executable file. Although you can incorporate these and other variables into batch files, you can simply use echo variablename from a command prompt to see the current value:
echo %userprofile%
echo %path%
Examples of similar environment variables in Linux include $HOME, which can be used to display the current user’s Home directory, and $PATH, which displays the locations the command interpreter will look for an executable file.
Additional environment variables can be added by using variable=variable (Linux) and set variable=value (Windows). To create a permanent environment variable in Linux, use export variable to add it to the Linux kernel after creating it.
Comment Syntax
As you have seen in this objective, comment syntax varies between scripting languages. While comments are not essential to script operation, they are extremely important to debugging, maintenance, and documentation. Table 4.8-1 lists the comment syntax used by the scripting languages covered in this objective.
TABLE 4.8-1 Comment Syntax by Scripting Language
Basic Script Constructs
Basic script constructs (CompTIA-speak for the features that scripts have in common) include loops and variables. The following sections introduce you to these concepts.
Basic Loops
Basic loops tell the computer to run the code over and over until the condition is (or is not) met. There are many variations on loops in all of the scripting languages covered on the CompTIA A+ 220-1002 exam.
Here are a couple examples of basic loops:
For/Next (VBScript Example) The logic of this loop is
1. Set up a range of values and the value to change using FOR:
![]()
2. The NEXT statement goes back to the N = N + i statement until i = 34, and then the script moves on:
Next
A For/Next loop must have a counter and runs a specified number of times.
Do/While (JavaScript Example) The logic of this loop is
1. The value of z, since it is not defined, is 0 and it will be incremented by a value of 1 each time the loop runs (z++):

2. The WHILE statement goes back to the z++ statement while z <77, and then the script moves on:
while (z < 77);
A Do/While loop always uses an increment of +1 as it runs and it keeps running as long as the Do statement is true.
Variables
A variable is a value that can be changed by a script, such as a=999 or $a="Mark". With few exceptions, scripting languages must set up, or declare, the meanings of the text or number variables that will be used in a program. By using variables, all that is needed to change a program to work with different data is to change the variable statements. Table 4.8-2 compares how variables are declared in the scripting languages covered in this objective.
TABLE 4.8-2 Variable Syntax by Scripting Language
Basic Data Types
To be able to treat numbers and words differently, computers need a new concept—data types. A data type is a defined category, like number or word. As you have seen in earlier parts of the objective, there are two basic data types used by scripting languages: integers and strings.
Integers
Integers are whole numbers: 5, 22, 37. Integers can have mathematical operations performed upon them, such as adding, dividing, averaging, and so on.
Strings
Strings are text, or numbers being treated as text such as telephone numbers or Zip Codes. Strings are usually surrounded with double quotes (") or, in PowerShell, single quotes ('). A string can be combined textually with other strings. For example, if $a = "Mark Edward " and $b = "Soper", then $a + $b = "Mark Edward Soper".
REVIEW
Objective 4.8: Identify the basics of scripting Script file types include
• .bat (batch files, used by Windows command prompt)
• .ps1 (PowerShell files, used by Windows PowerShell command environment or by the PowerShell ISE)
• .vbs (VBScript [Visual Basic Script] files, used by Windows Script host, CSCRIPT.exe, and Internet Explorer
• .vba (Visual Basic for Applications files, used by Microsoft Office apps from the VBA editor)
• .sh (Bash shell files, used by Linux and macOS in Terminal mode)
• .py (Python files, used by Python interpreters)
• .js (JavaScript files, used by web apps and browsers and by JavaScript IDEs)
Script files use the following features:
• Environmental variables (shortcuts to common locations and features in operating systems)
• Comments (indicated by characters such as REM, #, or '; used to explain program logic and features)
• Loops (such as For/Next, Do/While, and others; used to repeat operations)
• Variables (used to store numeric or text values that can be changed by a script)
The basic data types used in scripting include
• Integers (whole numbers)
• Strings (text, or numbers being treated as text)
4.8 QUESTIONS
1. You are using a Windows computer and need to create a list of files stored on a Linux server. Which of the following scripting languages can you use without special setup or installation?
A. Batch
B. JavaScript
C. PowerShell
D. Shell
2. The fundamental data types used in scripting include which of the following? (Choose two.)
A. Floating point
B. Integers
C. Binary
D. Strings
3. JavaScript script files sometimes contain paired codes such as <br>…</br> or <i>...</i>. What do these represent?
A. Placeholders for HTML code
B. The beginning and end of comments
C. HTML code used in browsers
D. Placeholders for data imported from Python or PowerShell
4. A new tech is puzzled by the # signs at the beginning of several lines in a scripting language. Which of the following most accurately describes what they mean?
A. Comments in a batch language follow.
B. Explanatory notes for a language such as Python or Bash follow.
C. They are placeholders for numbers that are too wide for the current display.
D. Comments in JavaScript follow.
5. Which scripting language uses a $ sign and single quotes for a text variable, such as $value = 'Smith'?
A. Batch
B. JavaScript
C. Shell
D. PowerShell
4.8 ANSWERS
1. A Batch files can be created in Notepad and run from the command prompt; no setup is needed.
2. B D Integers (numbers) and strings (text) are the data types used in scripting.
3. C Paired codes like these and others are HTML code, indicating the script will be used in a web environment.
4. B The hashtag (#) symbol is used for comments in Python, Bash, and PowerShell.
5. D PowerShell uses single quotes for text variables, while other languages use double quotes.

Objective 4.9 Given a scenario, use remote access technologies
Remote access technologies allow technicians to diagnose and fix many computer problems, including malware removal and data recovery, without going to the client site. Understanding the technologies and the potential security issues they pose are important for technicians and their clients.
RDP
Remote Desktop Protocol (RDP) is the protocol that supports Microsoft’s remote desktop software. Remote desktop software enables you to use another system’s GUI as if you were sitting in front of that computer. Microsoft’s Remote Desktop Connection can connect to and control a Windows system with a fully graphical interface (see Figure 4.9-1).

FIGURE 4.9-1 Windows Remote Desktop Connection dialog box with Options displayed
Similar programs enable techs to see what a client sees on their screen and use the client’s system to resolve the issue. Windows Remote Assistance (shown in Figure 4.9-2) enables you to grant or assume control, enabling a user to request support directly from you. Upon receiving the support-request e-mail, you can log on to the user’s system and, with permission, take the driver’s seat.

FIGURE 4.9-2 Remote Assistance in action
In all these methods, the connecting system is a client and the remote system is a server providing access to its desktop. To configure whether your Windows system can act as a Remote Assistance or Remote Desktop server, go to the System applet and select the Remote settings link on the left. The Remote tab in System Properties has checkboxes for both Remote Assistance and Remote Desktop, along with some detailed settings.
To make RDP more secure, find out the IP address or range of addresses of the remote computer(s) connecting with your computer. Then, use Windows Firewall with Advanced Security to restrict access to the RDP port to that IP address or range, a process known as scoping. You can also use a VPN (virtual private network) with RDP connections.
Telnet
Telnet is a terminal (as in CLI) emulation program that enables authenticated users to run commands on a remote system (such as a server or router) that is running the Telnet Server service.
Telnet is an optional feature in Windows. If it is not installed, open the Programs and Features Control Panel applet, click Turn Windows features on or off, and check the Telnet Client checkbox to add it to your system. Telnet is a standard feature of almost all Linux distributions.
SSH
Secure Shell (SSH) has largely replaced Telnet because it encrypts the entire connection to prevent eavesdropping. SSH has one other trick up its sleeve: it supports tunneling files or any type of TCP/IP network traffic through its secure connection, enabling SSH to secure an insecure protocol such as FTP.
Windows 10 includes the OpenSSH client as of the Fall Creators Update (2017). It is enabled by default starting with the April 2018 release. To run it, open a command prompt or PowerShell session and type:
ssh username@hostIP
Replace username with your username on the remote computer and hostIP with its IP address. You will be prompted for your account password on the remote computer. If SSH uses a different TCP port than the default 22, add -p portnumber to the ssh command, replacing portnumber with the actual port number.
If OpenSSH is not installed, open Settings | Apps. From the Apps & features menu, click Manage optional features. Click OpenSSH Client.
Third-Party Tools
Third-party remote access tools offer a number of advantages over the command-line SSH and Telnet clients. These tools might include one or more of the following features:
• Support for Windows, macOS, and Linux clients and remote access (GUI or command line)
• Easier configuration than CLI apps
• Support for remote access to mobile devices running Android or iOS
• Screen sharing
• File sharing
The following are some examples of third-party remote access tools:
• PuTTY (Windows GUI-based Telnet and SSH client; can connect to other OSs via Telnet and SSH; available from www.chiark.greenend.org.uk/)
• GoToMyPC (macOS or Windows GUI from macOS, Windows, Android, iOS; https://gotomypc.com)
• TeamViewer (cross-platform Windows, Linux, macOS, iOS, Android, Blackberry; www.teamviewer.com)
Screen Share Feature
One of the advantages of many GUI-based remote clients is the ability to share screens. Depending on the app, screen sharing can run in either or both directions.
A client who needs help can share their screen with a remote helpdesk worker so that the worker can diagnose and solve the problem far faster than trying to describe the solution to a user who is unfamiliar with the diagnostic features of their operating system.
Another application of screen sharing is for a trainer to share screens with students so that students can learn by watching as the instructor explains the settings needed for an app, a document, or another use.
File Share
File sharing is also a major benefit of third-party remote access apps. Although current e-mail systems can handle much larger file sizes than they could a few years ago, there are still occasions when e-mailing files just won’t do. With built-in drag-and-drop file transfers included in some remote access apps, file transfers are as easy as moving files between folders in Windows.
Security Considerations of Each Access Method
The best remote access method is the one that provides the best balance of speed, power, ease of use—and security. Here’s how the major methods stack up:
• RDP is relatively secure because it uses encryption, but its default settings make it vulnerable to unwanted connections. Changing the RDP port, using a VPN, and adjusting firewall settings make an RDP setting more secure.
• Telnet is insecure and sends passwords and user names as clear text, so you should use it only within your own LAN.
• SSH is very secure, using encryption for the entire connection and supporting tunneling (VPN) connections.
• Third-party remote access apps are typically very secure because they offer advanced encryption and (some) support for one-time passwords. The latter feature generates a list of passwords, each of which can be used just once. Use the list if you need to connect remotely from public network connections to prevent shoulder surfers or keyboard loggers from gaining access to the remote computer. Check the specifications for the specific third-party app to determine its security features and how to improve them.
REVIEW
Objective 4.9: Given a scenario, use remote access technologies Major types of remote access technologies include
• RDP (Remote Desktop Connection and Windows Remote Assistance, Microsoft)
• Telnet (Linux, macOS, and Windows—command line)
• SSH (Linux, macOS, and Windows—command line)
• Third-party tools (PuTTY, GoToMyPC, TeamViewer, and others)
• Screen sharing, offered by third-party tools and RDP
• File sharing, offered by third-party tools
Telnet is the least secure, with third-party apps being the most secure.
4.9 QUESTIONS
1. You are preparing to run Remote Desktop Connection to perform remote troubleshooting. From the command line or Search bar, which of the following commands would you use to start it?
A. RDC
B. DeskConn
C. mstsc
D. WRA
2. You are helping a client configure her system for Remote Assistance. Which Windows configuration option is used to make these changes?
A. Remote Access in Settings
B. Remote tab in System Properties
C. Remote Assistance in Computer Management
D. Connections tab in Internet Explorer
3. You need to use Telnet to remotely access another computer on the company network, but you cannot locate Telnet on your Windows 10 system. How do you get access to Telnet?
A. Install it from the Microsoft website
B. Open Settings | Apps and click Manage optional features
C. Set up a Linux VM and run Telnet from there
D. Click Turn Windows features on and off in the Programs and Features Control Panel applet
4. A new tech is attempting to use SSH to connect to IP address 192.168.4.19 as user newbie. Which of the following commands is the appropriate syntax?
A. ssh [email protected]
B. ssh 192.168.4.19@newbie
C. https://192.168.4.19 ssh-newbie
D. None of the above; run SSH from a GUI by clicking the remote computer
5. Your organization is looking for a remote access application that can be used securely from public Internet terminals. What security feature should this app include?
A. Cross-platform support
B. One-time passwords
C. Screen sharing
D. File sharing
4.9 ANSWERS
1. C mstsc is the command to launch Remote Desktop Connection.
2. B System properties, Remote (tab) is the correct answer.
3. D Enable Telnet with the Add and Remove Windows Features dialog.
4. A The correct syntax is ssh username@ipaddress, as shown in choice A.
5. B One-time passwords are used only once, so although a shoulder surfer or keystroke app might see the login, the password cannot be used again.




