8.1. Introduction
Protection and restoration are two methods whereby traffic affected by network failures is automatically rerouted over alternate resources. As per the definitions in Chapter 4, the term protection denotes the paradigm whereby a dedicated backup resource is used to recover the services provided by a failed resource. In contrast, the term restoration is used to denote the paradigm whereby backup resources are not dedicated to specific primary resources, but allocated dynamically based on availability. This may result in longer recovery times as compared with the protection case, but with possible improvements in network utilization.
Protection is a well-established feature in SONET/SDH networks. In Chapter 4, the details of Linear Automatic Protection Switching (LAPS) and ring protection schemes were described. These protection schemes utilized certain SONET/SDH overhead bytes (K1 and K2) for communication between network elements (NEs). The resulting protocols are said to be bit-oriented, since the communication does not rely on any additional framing procedure or transport protocol. With the advent of mesh networking, the existing LAPS schemes, which work between adjacent NEs, have been augmented with new mesh protection schemes. These are end-to-end protection schemes and include both dedicated protection (e.g., 1 + 1), as well as shared protection. Furthermore, newer LAPS-like link protection schemes have also been proposed. Like LAPS, these new protection schemes require signaling between NEs.
A question is whether the signaling for the new protection schemes should be bit-oriented (i.e., directly using SONET/SDH overhead bytes) or based on a higher-level protocol (e.g., RSVP-TE). Bit-oriented protocols are generally fast and can be optimized to the internal architecture of NEs. On the other hand, signaling based on a higher-level protocol allows the development of new protection schemes rather quickly due to the richer set of messaging constructs available. The use of higher-level protocols also facilitates interoperability when multiple subnetworks are interconnected to form a larger optical network (Figure 8-1). Finally, higher-level protocols are required in networks with OOO switches (i.e., PXCs) where bit-oriented protocols are not usable.
Figure 8-1. Segmented Protection
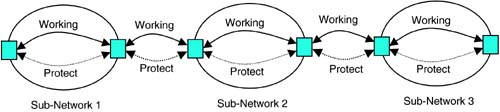
Now, restoration was briefly considered in Chapter 4, with emphasis on the efficiency aspects of restoration procedures. Aside from efficiency, restoration must be considered when end-to-end protection does not succeed or cannot be provided. For instance, shared mesh protection is designed to protect against single failure events (see section 8.4). If more than one failure occurs concurrently, mesh protection may not succeed for some connections. In this case, the failed connections could be subject to restoration procedures. As an example of the case where end-to-end protection is not possible, consider an optical network consisting of multiple, interconnected subnetworks (Figure 8-1). Suppose that standard NNI signaling (see Chapter 7) is implemented between the subnetworks, but the routing scheme used does not provide adequate information to determine end-to-end diverse paths (see Chapter 12). In this case, end-to-end path protection for a connection may be realized as shown in Figure 8-1. Here, the connection segment within each subnetwork is protected using end-to-end protection within that subnetwork, and the segment between two subnetworks is protected using LAPS. In this scenario, it is clear that the border nodes through which both the working and protection paths are routed are points of vulnerability. Failure of one of these nodes will render the connection unprotected. In this case, restoration may be used as a method of last resort to recover from node failures.
From a signaling point of view, restoration is tantamount to reprovisioning a connection after a failure. In Chapter 7, we saw that provisioning can be through a management system or signaling based. Since restoration needs to be completed as quickly as possible, the common wisdom is that restoration must be based on signaling. Thus, while connection provisioning may or may not need a distributed control plane, protection and restoration do.
In the rest of this chapter, we describe the new mesh protection schemes, their signaling requirements, and the various options for realizing the signaling. As mentioned earlier, we consider two broad categories of new protection schemes in mesh networks: span or link protection, and end-to-end or path protection. Span protection refers to the protection of a link (and hence all the connection segments routed over the link) between two neighboring NEs. End-to-end protection refers to the protection of an entire connection path from the ingress to the egress points in a network. A connection may be subject to both span protection (for each of its segments) and end-to-end protection (when span protection does not succeed or is not desired). In this context, the link and the connection are typically bidirectional consisting of a pair of unidirectional entities (see Chapter 6). Under span and end-to-end protection schemes, it may be required that when a failure affects any one direction of the connection, both directions of the connection are switched to a new link or path, respectively.
In the next section, we examine the new span protection scheme and the signaling protocol mechanisms suitable for implementing it. Following this, in section 8.3, we describe dedicated end-to-end mesh protection schemes and the associated signaling mechanisms. In section 8.4, shared mesh protection is described. It should be noted that mesh protection is still implemented in a proprietary manner by different equipment vendors. As of this writing, standards are evolving on protection and restoration protocols [Papadimitriou+02, Lang+03b]. Thus, our descriptions in sections 8.2–8.4 are based on work in progress. Now, questions are often raised as to the relationship between the signaling procedures used in optical networks for protection and restoration versus those used in MPLS networks for the same functions. We discuss this in section 8.5.
