Common Security Technology
Modern software architectures make use of several technologies for supporting system security. This section is a quick summary of the key technologies that are used and how then can help support the different aspects of secure systems.
Symmetric Encryption
Data encryption means converting the data so that it can only be decrypted and read by authorized users. Data encryption requires an algorithm that is applied to the data to encrypt it.
Symmetric encryption is so called because it uses the same key to both encrypt and decrypt the data.
One of the simplest cryptographic techniques is the Caesar cipher (named because Julius Caesar was reported to have used it). The Caesar cipher simply replaces each letter of the alphabet by the letter three positions further on, so that A is replaced by D, B by E, and so on, with the last three letters replaced by the start of the alphabet. Figure 15.1 shows the Caesar cipher.
Figure 15.1. The Caesar cipher.
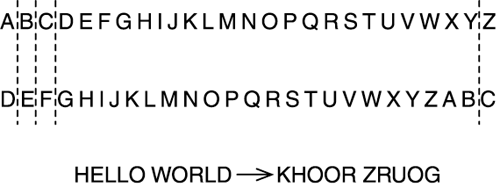
The Caesar cipher is a specific example of a simple shift substitution cipher when one letter replaces another. A different cipher is obtained by shifting the alphabet by more or less than three letters, as shown in Figure 15.2.
Figure 15.2. A Shift cipher.

The number of letters the enciphering alphabet is shifted by is called the cipher key. Given an encrypted message, anyone with the key can decipher the message. Because the same key is used to encrypt and decrypt the message, this is know as a symmetric encryption algorithm.
In programming terms, each letter is represented by a number, and the substitution cipher simply adds the key number to the value of each letter to get the encrypted form. The resultant number must be adjusted to map the last few letters (X, Y, and Z) onto the first few (A, B, and C) letters. This is a very simple algorithm.
In real applications, symmetric algorithms use sophisticated algorithms with number keys of 56 or 128 bits (approximately 45 decimal digits). The algorithms used are usually well known but, due to the size of the keys used, they cannot be easily reversed. In other words, without the key, the original plain text message can only be recovered by applying each possible key in turn. As long as the key is a large one and the encryption algorithm is sufficiently robust, the time taken to crack the cipher with a brute-force method attack, such as applying every possible key, can be hundreds of years.
One of the most widely used symmetric encryption algorithms is called DES (Data Encryption Standard).
Symmetric encryption is used to ensure data confidentiality. Symmetric encryption ensures that only the intended recipients who know the decryption key can recover the original data.
Asymmetric Encryption
Asymmetric encryption uses different algorithms than symmetric encryption and requires the use of two keys. One key is used to encrypt the data, and the other is used to decrypt the data. The two keys can be very large numbers, with modern systems using numbers of 1024 bits (approximately 140 decimal digits). Asymmetric encryption is called public key encryption due to the way the two keys are used.
Of the two keys used in asymmetric encryption, one is made public, while the other is kept private to the owner. The keys are known, respectively, as the public key and the private key.
If data is encrypted with the public key, only the owner of the private key can decrypt it. This approach is used to ensure data confidentiality but is restricted to supporting only one recipient per message.
In contrast, using symmetric key encryption allows one message to be distributed to several recipients, as long as each recipient knows the key used to encrypt the message. If the private key was known by more than one person, it would undermine the other benefits of using asymmetric encryption (such as non-repudiation) and avoid the need to distribute the cipher key. Distributing the keys used in symmetric encryption is a major problem, because the keys have to be distributed in a secure manner. An attacker obtaining the keys can decrypt the message to recover the original data.
Another use of asymmetric encryption is to support non-repudiation. If a message is encrypted with the private key, it can only have originated from the key owner. Anyone can decrypt the data using the public key with the knowledge that it can only have originated from the owner of the private key. This use of asymmetric encryption is the basis of digital signatures.
Asymmetric encryption is slow compared to symmetric encryption. To improve performance, it may be desirable to use symmetric encryption. The problem here is how to distribute the encryption key to the recipient securely.
A common approach is to use symmetric encryption for the data and to pass the encryption key with the data. To make this approach secure, the recipient's public key is used to encrypt the symmetric key passed with the encrypted data. The recipient can use his or her private key to recover the key and then decrypt the actual data.
This technique enables large volumes of data to be encrypted quickly and, at the same time, distributing the encryption key in a secure manner.
SSL and HTTPS
The Secure Sockets Layer (SSL) is an implementation of public key encryption in TCP/IP networking. TCP/IP communication uses a technology called sockets (sometimes called service or port numbers). All standard TCP/IP services advertise themselves on a fixed socket or port—FTP on 21, TCP/IP on 23, HTTP on 80, and so on. You have seen socket numbers when using the J2EE RI Web server that runs on port 8000.
http://localhost:8000
Ordinary socket communication uses plain (unencrypted) data. Any user that can monitor network traffic can read any usernames, passwords, credit card details, bank account information, or anything else passed over the network. This is obviously an unacceptable situation from a security point of view.
One solution to securing confidential data over a network is to encrypt the data within the application. This is an inconsistent solution because some applications will be secure while others are not.
Another solution is to always encrypt all network traffic. Because encryption adds an overhead to the network communication, this will affect overall performance and is unnecessary when data does not need to be encrypted.
The workable solution is to seamlessly provide network encryption only for applications that require secure data transmission. Using this approach, any application can encrypt confidential data simply by using the encrypted network communications instead of the usual plain text data transfer. Each application decides if encryption is needed but does not have to implement the encryption algorithms.
SSL is a network encryption layer than can be used by any TCP/IP application. The application has to connect by using a secure socket rather than a plain socket, but otherwise, the application remains unchanged.
Hypertext Transfer Protocol Secure (HTTPS) is the name given to the HTTP protocol when it uses a secure socket. The default port used by an HTTPS is 443. When a URL specifies the HTTPS service, the Web browser connects to an HTTP server but uses SSL to encrypt the data. All the popular Web browsers indicate on the status line when SSL communication is taking place. Typically, an open and closed padlock is used to shown whether data is encrypted.
Online credit card verification services and banking systems use SSL communication.
Checksums and Digests
Data integrity is usually achieved by providing checksums or digests of the data. The data in a message is subjected to a numerical algorithm that calculates one or more validation numbers that are transmitted with the data. The recipient receives the data and applies the same algorithms to the data. As long as the recipient's calculations yield the same numbers as those transmitted with the data, the recipient is reasonably confident that the data is unchanged.
Checksums use simple algorithms and are primarily intended to detect accidental corruption of data. Message digests use sophisticated algorithms that are designed to prevent deliberate changes to data. The algorithms used in a message digest generate many digits and are chosen so that it is virtually impossible to change the original data without changing at least one of the digest numbers.
There are several digest algorithms in use, with Message Digest version 5 (MD5) currently one of the most popular. The MD5 specification can be found at http://www.ietf.org/rfc/rfc1321.txt.
Many applications that can be downloaded from the Web also have an associated signature file. A signature file is used to validate the contents of the associated file (the one it signs). Signature files usually contain one or more digests (typically MD5) of the file they are signing. After downloading the file, a conscientious user can also download the signature file and check the integrity of the download file by calculating the digest of the file and comparing it to the value in the signature file. Programs to calculate digests are widely available on the Internet.
Digital Certificates
Digital certificates are specified by the X509 international standard and define a format for representing public keys and other information about an entity (it could be a user, a program, a company, or anything that has a public key).
The official specification for the X.500 Directory Service is available from the International Telecommunications Union (ITU) web site at http://www.itu.int/rec/recommendation.asp?type=folders&lang=e&parent=TREC-X.509.
Digital certificates are often sent with a request for data so that the server can encrypt the data with the recipient's public key.
Digital certificates must be signed by a Certification Authority (CA) to prove their validity. A signed digital certificate contains a message digest of the certificate encrypted using the CA's private key. Any recipient of the certificate can decrypt the digest using the CA's public key and verify that the rest of the certificate has not been corrupted or modified.
Digital certificates can be used to ensure authentication, confidentiality, and non-repudiation.
Caution
Valid Digital Certificates have been erroneously issued to individuals spoofing the credentials of trusted companies. A Digital Certificate is only as trustworthy as its Certification Authority.
