In this chapter
A revolution is going on now, and it compares to the one Johannes Gutenberg started in 1456 when he pioneered the use of movable type. The ability to print in quantity made it possible for the first time for the common man to gain knowledge by himself. This new revolution is based on global connectivity, and its impact is on our ability to disseminate information by ourselves. We now take it for granted that we can share information, preach, publish, talk, and touch the rest of the world through our computers. Networks have radically changed the way the world communicates.
Networks aren't limited to just the work environment anymore. Many homes with a computer quickly end up with two or more, and it's not long before it seems sensible to tie them together with a network. So, whether or not you have one now, a network is probably in your future. In this chapter, you'll learn how networking works and how Windows XP provides the tools to help you become part of the connected world.
NOTE
This chapter is designed to provide some basic networking concepts. If you have been networking computers for some time, feel free to skip ahead. If you are new to networking, read on. This chapter will help get you pointed in the right direction.
I probably don't have to convince you of the value of tying your computers together with a network, even if you have only two. With a network, you can do the following:
Use any printer attached to any computer.
Share files, that is, get at files stored on one computer from another. At home, having this capability might mean you can finish that letter you were writing yesterday using your kids' computer because they're now using yours to manage their stock portfolios. In the office, a network lets workers share information quickly and facilitates the creation of a centralized documentation system.
Share CD-ROMs.
Back up networked computers with one common backup system—for example, a tape drive.
Use network-enabled application software, such as databases, workgroup scheduling and calendar programs, and email. Network-enabled software is designed to give multiple users simultaneous access to information that is updated in real-time.
Share a single Internet connection among several computers, saving on telephone lines and connection costs.
Play multi-user games within your home or office, or across the Internet.
A network can justify its cost with printer or Internet connection sharing alone. But how hard is it to put together?
It doesn't seem possible that it's now nearly 15 years since I installed my first network in a client's office. It was a nerve-wracking experience because it had cost my client thousands of dollars in hardware and software above the cost of the computers alone, and although he didn't know, I had never installed networking software or a file server before. Networking was reputed to be a costly, mystical, and dark art, and I soon found that this reputation was well-deserved. The network eventually worked. For several thousand dollars, my client got 10 computers that could read and write to the same database file.
Now a network card can cost half the price of a movie ticket, you can buy network cables at the corner hardware store, and first-class networking software is, well, nearly free—it's free if you were going to buy Windows anyway. And you can probably take it for granted that you should be able to just plug and play.
In the next few chapters, you'll learn how to use Windows networking to connect to the computer in your basement, to the rest of your office workgroup, or to a worldwide corporate enterprise. You may still need to learn an incantation or two, but fear not, they're no longer in Latin.
One other point: I'll be using the word resource frequently in this chapter. By resource, I mean a shared folder or printer on someone else's computer, which you can access through the LAN.
Windows XP has, right out of the box, all the software you need to communicate and share information with other computers. Windows XP Professional can fill several roles, depending on the way it's connected to other computers. It can be any of the following:
A standalone computer working in complete isolation. An example might be a simple home computer.
A standalone computer connected to others via a modem. An example is a laptop computer with a modem used to connect to an office or to the Internet. This computer works in isolation some of the time but can socialize when needed. You can think of this type as a remote workstation.
A member of a small workgroup of computers with no central “server.” An example might be a computer in a small office or home office, one of say 2 to 10. The computers share resources with each other but are essentially independent. This computer is a peer in what is called a peer-to-peer network; no one computer has an intrinsically special role in making the network work. All the participants are on equal footing; they are peers. Not all the computers need to use Windows XP either; Windows XP can peer with older versions of Windows and other operating systems such as Mac OS and Linux.
A member of a group of computers working under the stewardship of a central server. This computer is probably one of a group of a dozen or more. The designated master computer or server contains, at least, centralized username and password information, which it passes out as a service to the other computers on the network. These other computers are the clients in a client/server network. Windows XP Professional can be the client of a server run by Windows Server 2003, Windows 2000 Server, or Novell NetWare.
A member of a client/server network that is in turn connected to other networks. An example is a computer in a branch office of a large company. This computer is participating in an enterprise network, where special consideration has to be made to management, security, and the allocation of resources of many, many computers and people spread out over a wide geographical area.
Windows XP Professional has all the stuff to participate in any of these network environments. The one thing it can't do is take the central, or server, role of a client/server or enterprise network. The reason for this is that Windows XP Pro doesn't have the ability to act as a centralized user/password database. For that, you need at least one computer running one of the Windows Server versions or one of its more upscale varieties: Advanced Server, Enterprise Server, or Data Center.
NOTE
Microsoft cleverly named the successor to Windows 2000 Server “Windows Server 2003.” Why they had to move the number around, we don't know. But, to keep things simpler in our text, we're going to use the name “Windows 200x Server” when our discussion doesn't have to make a distinction between the two.
Windows XP Professional file sharing service can make a network connection with at most 10 other computers. If you need to share a network resource (such a printer or file folder) with more than 10 computers, you'll need one of the Windows Server versions.
In the next few chapters, you'll learn how to configure and tune up Windows XP in each of these environments. If you already understand how networks work, you can skip ahead to “The Many Faces of Windows XP” later in this chapter. If not, check out the following sections for an introduction to the concepts and terms you should know.
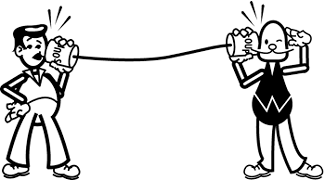
What makes a network tick? Let's start by looking at Figure 15.1, the first sort of network you probably built.
Don't laugh! A tin can telephone has many of the attributes of a computer network. The basis of a network is a physical transport medium: a means of carrying raw information (for example, words) over a medium (string) between hardware interfaces (cans). When you first used a tin can phone, you found out right away that you couldn't speak at the same time as the person on the other end, so you had to work out a protocol to coordinate your conversation: You probably said “over” after you spoke, like the astronauts and pilots you saw in the movies. Finally, you found that there's a limit to how long the string could be for the phone to work. If the string was too long, you couldn't hear.
Computer networks have these components and limitations, too. The raw information in a network is digital data (bits), carried over a physical medium (usually wires or optical fibers, but sometimes radio waves) between hardware interfaces (network adapters plugged into your computer), according to a mutually agreed-upon protocol that coordinates the computers' conversations.
A computer network is often called a local area network, or LAN. A LAN is a group of computers connected by a physical medium that supports a relatively high rate of data transmission, say 1 million bits per second (Mbps) or more, in relatively close proximity, say within one building, all able to communicate directly with each other. (Imagine 10 cans on strings, all tied together in the center!) Most home and small office LANs transmit data at 10 or 100Mbps (million bits per second). This is fast enough that loading and saving large word processing documents to a remote computer isn't noticeably slower than using your own hard drive. Hot-rod networks can run as fast as 1000Mbps. This kind of blazing speed is used mostly in corporate settings and by digital-media mavens.
The electrical nature of LAN communication limits the physical distance allowed between computers to at most a few hundred yards. LANs can be extended much farther using optical fiber cables, which carry data as pulses of light, to connect groups of computers sharing a more traditional (and inexpensive) electrical connection. You might hear this arrangement called a campus network or metropolitan area network.
A wide area network, or WAN, is a group of two or more LANs tied together over even longer distances. Historically, these connections were much slower, between 56 thousand bits per second (Kbps) and 1Mbps because long-distance connections were extremely expensive. (A 56Kbps connection between San Francisco and Chicago with a guaranteed throughput of only 16Kbps cost about $2,500 per month in 1996.) Now that the telecommunications companies have installed optical fiber cables all over the world, even WAN connections can be as fast as LAN connections these days. Using the Internet, a 400Kbps connection between any two points in the U.S. can be made for as little as $300 per month.
In addition to your data, LANs carry quite a bit of “chatter” as the member computers broadcast questions, asking for the location of needed resources, and as servers broadcast announcements of the services they provide. This communications overhead could use up most of the carrying capacity of a slow WAN connection, so special devices called routers examine and make decisions about what data to send back and forth between the disparate geographical areas.
As I mentioned earlier, one of the main distinctions of a server-based network is a centralized username/password database. To let users continue working if the long-distance connection fails, and to provide speedier logon checks, builders of WAN networks usually install a server at each geographic location. Windows 200x Server lets administrators add or alter user information at any one location, and the server automatically copies the changes to all the other servers. For large enterprises, this one feature alone makes it worth the extra bucks.
As you know, a LAN consists of a group of computers connected together using some sort of electrical medium. You can choose from several different electrical media. They differ in the way they format and electrically represent the data sent between computers.
Network devices have to use some standardized way of organizing the data signals they transmit between computers. You might have heard of some of these already:
Ethernet was developed by Xerox, Intel, and Digital Equipment Corporation. Ethernet has grown so popular and common that you hardly need to use the word anymore: Most networks are Ethernet networks.
Asynchronous Transfer Mode, or ATM, is a networking technology widely used in the telecommunications and Internet industries for very high-speed backbone networks. Backbone is a term for an ultra-fast connection between the separate parts or sites of a large network. For example, it might refer to the set of links between major network sites of a corporation, the national network of a telephone carrier, or the high-speed Internet links between major ISPs. ATM is often used behind-the-scenes by Internet service providers to route data to DSL (Digital Subscriber Line) modems. However, ATM is only rarely used to connect directly to individual user's computers, except for some very specialized graphics workstations and other ultra-high-tech situations.
Other technologies are waning in popularity and you won't be hearing of them again, so don't feel any need to memorize:
ARCnet, AppleTalk, and StarLan were early network technologies but are hardly used now because they are so much slower than modern technologies. AppleTalk is still occasionally used to connect older Macintoshes to printers. ARCNet is still used in some industrial settings, for example, to control factory equipment.
Token ring was developed by IBM and is still used in businesses that are “blue” to the core, but nobody else in his right mind would install it now because it's slower and much more expensive than Ethernet.
If you're constructing your own network, you'll likely use Ethernet in one form or another. The choice you'll have to make is which kind of physical medium to use.
The signals transmitted across a LAN are generated and interpreted by electronics in each computer. Some computers have built-in network interfaces; otherwise, each computer in a LAN needs a network interface card, or NIC. I may also refer to them as network cards.
These electrical signals have to be carried from computer to computer somehow. The original design for Ethernet used a very expensive 1/2-inch thick cable that could carry a 10Mbps Ethernet signal up to 500 meters. (It was named 10BASE5 for reasons that only make sense to an engineer.)
Today's network interface cards are designed to use one of several inexpensive varieties of network cabling, or use radio waves to avoid the need for wiring altogether. In the following sections, I'll list the various types of media you're likely to encounter.
Thin Ethernet used a coaxial cable similar to television cable to connect each computer—I say “used” because it's an old, cumbersome technology that has virtually disappeared. It was also called 10BASE2 Ethernet; the 10 indicated that the network ran at 10Mbps, and the 2 indicated that it had a maximum wiring length of 200 meters or 660 feet. Thin Ethernet cables ended in distinctive twist-on connectors called bayonet connectors, or BNC.
Thin Ethernet wiring ran from computer to computer in a daisy-chain fashion called a bus network, as shown in Figure 15.2.

Figure 15.2. Thin Ethernet network cabling ran from computer to computer in a single unbroken line called a bus.
Some coaxial cable may still be around, but it's been almost completely supplanted by the much faster, much less expensive, and much easier to use twisted-pair system.
Unshielded Twisted-Pair, or UTP, has become the most common network carrier, and is so called because like-colored pairs of wires inside the cable are gently twisted together for better immunity to electrical interference from fluorescent lights, radio signals, and so on. This inexpensive type of cable is also used for telephone connections, although the network variety is of a higher quality and is certified for its capability to carry high data rates. UTP cables are terminated with eight-wire RJ45 connectors, which are wider versions of the ubiquitous modular telephone connectors.
UTP cable quality is categorized by the highest data rate it's been designed and certified to carry reliably. The most common cable types are shown in Table 15.1.
Table 15.1. UTP Cable Categories
Designation | Highest Data Rate | Application |
|---|---|---|
CAT-1 | Less than 1Mbps | Telephone (voice) |
CAT-2 | 4Mbps | IBM Token Ring |
CAT-3 | 16Mbps | 10Mbps Ethernet (10BASE-T) |
CAT-4 | 20Mbps | 16Mbps Token Ring |
CAT-5 | 100Mbps | 100Mbps Ethernet (100BASE-T), ATM, others |
CAT-5E or -5X | 250Mbps | Gigabit Ethernet[*] (1000BASE-T) |
CAT-6 | 250Mbps | Gigabit Ethernet[*] |
[*] Gigabit Ethernet uses four pairs of wire each carrying 250Mbps, providing an aggregate speed of 1000Mbps | ||
The thing to remember here is that you can't use just any old wiring you find in your walls to carry a network signal: You have to look for the appropriate “CAT-something” designation, which will be printed on the cable jacket every foot or so.
UTP cabling can carry token ring signals but is most commonly used for Ethernet networking. UTP Ethernet devices are connected to a central device called a hub in what is called a star network, as shown in Figure 15.3. Star networks are reliable: If any cable in a bus network broke, the whole network failed. If a cable in a star network fails, only the computer connected by that cable goes offline.
You can buy three varieties of UTP-based Ethernet hardware, denoted 10BASE-T, 10/100BASE-T, and 1000BASE-T in order of increasing speed. I'll discuss the 10BASE-T variety first.
If you've been paying attention, you might guess that the 10BASE part means 10Mbps, but T? The T stands for twisted pair, and you just have to know that the maximum permitted cable length is 100 meters, or 330 feet.
This is usually an ample distance in a home or small office environment, but it limits 10BASE-T's usefulness in a large building or campus LAN. Hubs can solve this problem by serving to connect several close-by computers. The hubs can then be connected to each other with fiber-optic cable, which forms a “backbone” connecting groups of computers, as shown in Figure 15.4.
Fast Ethernet is a 100Mbps version of Ethernet over UTP cable. It is also called 100BASE-T or 100BASE-Tx. Most current hardware can actually work at either speed, and is labeled 10/100BASE-T or -Tx. (The x stands for full-duplex, which is standard with 100BASE-T networking hardware, with or without the x.)
This hardware is 10 times faster than 10BASE-T hardware. The CAT-5 cable and connectors required to carry this high-speed signal are a tiny bit more expensive than CAT-3 and require more care in their installation, but the cost has fallen so much in recent years that it's really no longer a consideration. 100BASE-T hubs and network cards used to be more expensive as well, but again, they're manufactured in such enormous volumes now that the price differential has disappeared. In fact, most new computers have a 10/100BASE-T adapter built right into the motherboard. The wiring is cheap, so, for a home or small office, Ethernet networking is virtually free.
Gigabit Ethernet, 100Mbps version of Ethernet over UTP cable. It is also as you might guess, sends data at 1000Mbps. It's several times more expensive than 100Mbps Ethernet, but the tenfold increase in speed is worth it if your server is trying to feed files to several hundred people at once, or if you're involved in medical imaging, digital video editing, or other applications that involve transferring huge amounts of data. It's also used for the backbones of large networks and for fast server-to-server and server-to-switch connections.
Gigabit networking is overkill in the home and small office environment, as most desktop computers can't transfer data to or from their hard disks fast enough to take advantage of such a fast network. Still, some higher-end workstations, like Mac G5s and most server-class machines, now come with a 10/100/1000BASE-T adapter built-in. This adapter will work at any of these three speeds, depending on the abilities of the hub or switch to which it's connected. The price of Gigabit switches and hubs has fallen to less than $15 per port. For example, a 5-port switch costs about $60. So, if your computers came with Gigabit adapters, have ultra-fast hard drives or RAID arrays, and you expect to be moving lots and lots of data around, it might be worth your while to pay just a bit more for the switch and CAT-6 cabling. Gigabit Ethernet requires CAT-5E or CAT-6 quality cable and connectors throughout, with all four wire pairs connected.
It always seemed silly to me to have a portable computer tied down by network and power wires. Now, it doesn't have to be. Ethernet-over-the-proverbial-ether—that is, wireless networking—has become amazingly inexpensive and ubiquitous. Using wireless network adapters, you can connect computers in a small area (such as a home or office) via radio, as illustrated in Figure 15.5. With modern equipment, the data rate can reach a respectable 54Mbps.
Wireless access is especially handy for users of laptop computers, Palm Pilots, and other mobile users who visit several offices in the course of a day. A device called an access point can be installed at each location to make the connection between wireless devices and a standard wired network or the Internet. Then, to quote Buckaroo Banzai, “wherever you go, there you are.”
Hot spots—sites with Wireless access to the Internet—are springing up everywhere. In fact, a certain big coffee chain from Seattle is rolling this out nationwide—they'll connect you to the Internet for a small hourly fee while you sip a latte! (Your humble authors would never set foot in one of these places, of course, preferring to patronize locally owned establishments and the original Peet's Coffee & Tea. But I digress.)
NOTE
The wireless network manufacturer's organization is called the “Wi-Fi Alliance.” Wi-Fi stands for Wireless Fidelity, and in a loose way, “Wi-Fi” is used to refer to Wireless networking.
One thing you have to watch out for is that there are currently three Wireless standards, named 802.11a, 802.11b, and 802.11g. The “standard” part refers to the fact that the technology is governed by an international standards committee, and equipment made by one manufacturer should work correctly with equipment made by another. (This didn't actually hold true a few years ago, but today it largely does.)
However, equipment designed for one standard won't necessarily work with equipment designed for a different standard, as shown in Table 15.2. 802.11a equipment can only communicate with other 802.11a devices. 802.11b and 802.11g equipment can interoperate, but only at the lowest-common-denominator speed.
Table 15.2. Wireless Networking Standards
Wireless Standard | Data Rate[*] | Compatible with |
|---|---|---|
802.11a | up to 54Mbps | 802.11a only |
802.11b | up to 11Mbps | 802.11b at 11Mbps 802.11g at 11Mbps |
802.11g | up to 54Mbps | 802.11g at 54Mbps 801.11b at 11Mbps |
[*] Some manufacturers have tweaked their wireless devices to let them communicate at twice the standard's maximum speed, but only when connected to equipment by the same manufacturer. | ||
If you're considering wireless, 801.11g (also called “wireless-g”) is the stuff to get for home and small office networks. Wireless-a equipment tends to be expensive. The price differential between -b and -g is miniscule, but -g can go five times faster and it's compatible with -b adapters.
Given the complexity of the stuff, and knowing that just a few years ago it cost about $400 per computer to go wireless, I think today's prices for wireless gear are insanely low: about $20–40 per computer for adapters, and $20–100 for an access point, the wireless network's hub. While it isn't quite as fast as 100Mbps Ethernet, wireless is so much easier to install that it's competitive with wired networks even in the home and office.
However, there are two things that you must keep in mind. First, a wireless network is not as reliable as a wired network. In my experience and that of many friends, it simply stops working at random intervals; sometimes once a day, sometimes once a week. It may start working again by itself after a few seconds or minutes or hours, or you may have to restart your computers and wireless router to get it back on the air. In contrast, unless someone trips over a cable and yanks the connector off, a wired Ethernet network should run for years without a single glitch.
Second, unless you take explicit steps to secure it, a wireless network is “open to the public,” and it's a trivial matter for random passers-by to browse through your shared files and borrow your Internet connection. Making a wireless network secure takes some effort, and to be frank, it can be difficult and confusing even for networking pros, let alone for the technologically challenged. As a result, many people skip the security step just to get their network working, and end up getting their computers hacked-into. A wired network has neither the setup headaches nor the security risks.
Network data can also be transmitted as radio signals through your existing telephone lines or electrical wiring. Meant primarily for home use, powerline networking equipment (called HomePlug by its manufacturers' association) and phoneline networking (called HomePNA) send data at up to 10Mbps. It has the advantage of being very easy to install—an adapter plugs into your wall jack or phone jack, and connects to your computer. No other wiring or setup is involved.
I rather soundly derided this equipment in the first two editions of this book, but the technology has improved, and the prices have fallen to the point where it makes perfect sense to use it in the average home.
Optical fiber is capable of gigabit (1000Mbps) and higher speeds and can also carry data over runs of several miles, quite a bit farther than standard Ethernet. Optical fiber is not generally run directly to individual computers, but between hubs and routers between buildings, to form the “backbone” of a campus network, as shown in Figure 15.6. Optical fiber cables can carry multiple 10 or 100Mbps Ethernet data signals, as well as more advanced, even higher-speed data formats called Fiber Distributed Date Interface (FDDI) and Asynchronous Transfer Mode (ATM).

Figure 15.6. Optical fiber cable linking two 100BASE-T hubs via a fiber “uplink” port. Cables contain pairs of fibers because each fiber can carry information in only one direction.
In summary, there are several different network technologies involved in any network: data transmission format standards like Ethernet and Token Ring, and electrical wiring standards like 10BASE-T and ThinNet. Networks depend on an agreement to use several specific technologies, each of which relies on another to help it do its job. For example, a file-sharing standard relies on a network protocol, which depends on a data transmission format, which requires a wiring standard.
In fact, there's even a standardized way of talking about the way these standards interrelate. In case you haven't guessed already, engineers like nothing more than forming committees to create standards.
If you've read about networks in any other computer book, you've probably seen a diagram similar to the one in Figure 15.7, the OSI Standard Network Model. The International Organization for Standardization (ISO) and Institute of Electrical and Electronic Engineers (IEEE) developed this model—I think to help computer book authors fill lots of pages trying to explain it. It's in every computer book I've ever seen.

Figure 15.7. The OSI Standard Model for Computer Networks—a required figure in every computer book. Networks are built from components, each of which performs a job for a higher-level component in the “stack.”
I will spare you the usual long explanation of this diagram because I don't think it's very helpful as an introduction to networking. But I do think it helps illustrate that networks are composed of modular components, conceptually “stacked” one on top of the other, each performing a job for the component above it, using the components below. The parts are interchangeable in that you may often choose one of several available technologies to do the job of a given layer. As long as the job is done correctly, the higher layers don't really care how it's done.
The components in this “stack” communicate with their corresponding components in the other computers on the network. As you go down in these stacks, the layers are less concerned with interpreting the data they handle and more with simply moving it somewhere. The higher level components interpret and communicate with each other to reassure each other that the data they have sent was correctly received, and they rely on the lower levels to actually transport that data from one computer to another.
That's the OSI network model in two paragraphs.
In the real world—at least in the Windows world—the “stack” of components that make up Windows networking isn't just a concept, it really does exist. Figure 15.8 shows the Windows network model. When you want to access a remote network resource somewhere inside the operating system, the following actions occur:
A network client composes data messages to communicate these desires to the remote computer, using an agreed-upon file sharing protocol.
These messages are packaged according to a transport protocol, which specifies how messages are to be broken into manageable pieces, how the pieces are to be addressed to member computers, and how to re-request missing or garbled pieces as they are received.
The packaged message pieces are called packets and are physically carried by a data link or framing protocol that determines how to arrange the bits of information in each packet for transmission.
The bits are converted into electrical pulses, radio signals or flashes of light and carried from one computer to another through a physical medium that carries the pulses or flashes to another computer.
The pulses or flashes are received at the other end; the data work their way up the network components on the other side and are finally delivered to a server component. The server sends a response back through the same path to the client.
The data link level is handled entirely by the hardware in a network interface card (NIC). When you buy a network card, you're buying a data link protocol and the attachment to the physical medium. Because the card is what you'll actually see and have to describe to Windows, from this point on, I'll talk about adapters rather than data link protocols.
A network client is one of the most important top-level parts of Windows networking. The client is responsible for making remote files, folders, and printers available to your computer. To do this, it communicates with a corresponding server component on another computer, whose job it is to deliver file and printer information to client computers. Your Windows XP computer actually has both components built in, because it can both share files and printers and use shared files and printers.
Microsoft provides two network clients with Windows XP Professional: the Client for Microsoft Networks and a Client for Novell NetWare networks. Novell supplies its own version of the NetWare client, downloadable from their Web site, so you actually have a choice of three.
These client components, at the top of their network stacks, communicate with their corresponding top-level server components in other computers to read and write files, queue printer data, read the contents of folders for display in Explorer, and so on. The Client for Microsoft Networks uses the Server Message Block (SMB) and NetBT (NetBIOS over TCP/IP) protocols to speak to other Windows computers, Windows 2000 Servers, and IBM OS/2 LAN Manager Servers. You won't ever encounter SMB or NetBIOS directly in your dealings with Windows Networking; they're part of the client and server software.
The Novell client can communicate with Novell NetWare-based file servers using the built-in NetWare Core Protocol (NCP), or with a Windows XP or Windows 2000 Server network service called File Services for Novell Networks.
NOTE
File Services for Novell and File Services for Macintosh are available only with Windows 200x Server and their more advanced versions. These services allow a Windows Server to share files and printers with Novell workstations and Apple Macintosh computers, respectively.
Each of these client packages uses a transport protocol to carry messages between your workstation and a remote computer's sharing service.
As you learned previously, transport protocols define how data is arranged and sent in a coordinated fashion between computers. There are three transport protocols commonly used on Windows-based computers:
TCP/IP (Transport Control Protocol/Internet Protocol) is the transport protocol that forms the basis of the Internet. TCP/IP is actually a set of many protocols that are used to provide the services that higher-level network components need: resolving computer names into network card and IP addresses, guaranteed transmission, and internetwork routing. The TCP part, or Transmission Control Protocol, is the method an IP-based network uses to guarantee that data is sent end-to-end without errors. I'll go into more detail about TCP/IP in a little bit.
IPX/SPX (Internetwork Packet Exchange/Sequenced Packet Exchange) was developed by Novell for its NetWare network software. Windows can use IPX/SPX for its file sharing services as well. Like TCP/IP, IPX/SPX is really a set of protocols that provide many services, including name resolution, guaranteed transport, and Internetwork routing.
NetBEUI (NetBIOS Enhanced User Interface) was developed by IBM for its original IBM PC Network; it provides similar services to TCP/IP and IPX/SPX, except that it doesn't have a mechanism to route data to remote networks. NetBEUI can transport data between computers only on the same physical LAN. NetBEUI was supported by previous versions of Windows, but has been dropped in Windows XP. (Well, almost dropped—it's on the Windows XP installation CD in case you have to use it, but it's not easy to find.)
The Client for Microsoft Network can use either TCP/IP or IPX/SPX to send its messages to a file server; all that's required is that both the client computer and server computer have at least one installed protocol in common.
Similarly, Novell's client package communicates with Novell NetWare-based file servers using IPX/SPX, or for recent versions of NetWare, TCP/IP.
The following are some other protocols and acronyms you might run across:
AppleTalk and its Ethernet-based counterpart LocalTalk are used in Apple Macintosh networking. Windows 2000 Professional provided LocalTalk to facilitate using LAN-connected Apple printers, but it's been dropped from Windows XP.
DLC (Data Link Control) is an IBM networking protocol, but you won't run into it directly unless you're working on a corporate network with IBM mainframes. In that case, if it's used, your company's network management staff will install and manage it for you. DLC is also used by some network-connected printers. Like AppleTalk, support for DLC has been dropped by Microsoft.
Point-to-Point Protocol, or PPP, is used to carry Internet Protocol data packets across a dial-up modem connection. This protocol is used to establish almost all modem connections to Internet service providers. PPP is part of the TCP/IP suite and a standard part of Windows's Dial-Up Networking support.
Point-to-Point Protocol over Ethernet, or PPPoE, is used by some DSL and cable modem Internet service providers to link your computer to the ISP's routing equipment. Its purpose is to limit the number of computers connected to the Internet to just those being actually used. For previous versions of Windows, ISPs provided their own PPPoE software. PPPoE is now built into Windows XP as part of its Broadband Connection support.
Wired Equivalent Privacy or WEP is an encryption protocol used by wireless networks to protect data from being intercepted by eavesdroppers, and to prevent random passersby from being able to connect to and use your network without permission. In urban areas, it's now common to find that your computer can pick up a half-dozen or more wireless network signals. That means that a half-dozen or more random other people can pick up your wireless signal, and you don't want them poking into your files. WEP helps prevent that. It's unfortunately not completely unbreakable—a hacker with a laptop can park him- or herself in front of your house or office for a few hours and eventually be able to get on your network, so another encryption standard was developed, and is becoming more common:
Wi-Fi Protected Access, or WPA, is an improved encryption scheme for wireless networking. Windows XP Service Pack 2 includes WPA support. Most wireless equipment vendors now support it as well, however, if you have existing equipment, you may have to download upgraded software to get it.
Universal Plug and Play, or UPnP, lets networked computers and networked devices such as network routers, printers, and household appliances automatically configure themselves to join whatever network they find themselves plugged into. It can, for example, automatically configure your computer to use an Internet connection shared by another computer on the LAN. UPnP also lets these “smart” appliances tell your computer what they do, and can let you configure them from your Windows PC.
Point-to-Point Tunneling Protocol, or PPTP, is used to create Virtual Private Networks, or VPNs. PPTP takes data destined for a private, remote network, repackages the data for transmission across the Internet, and at the other end unpackages the data to be released into the private, protected network. I'll go into greater detail explaining VPNs in Chapter 18, “Windows Unplugged: Remote and Mobile Networking.”
Layer 2 Tunneling Protocol (L2TP) is another protocol used to create Virtual Private network connections. Windows XP comes with built-in support for both PPTP and L2TC. It is always used along with IPSEC for encryption.
IPSEC, which stands for Internet Protocol Security, is a protocol that provides very strong encryption of data sent through a TCP/IP network.
IPV6, for Internet Protocol Version 6, is a new version of TCP/IP. It's sort of TCP/IP on steroids. (Today's ubiquitous TCP/IP protocol is actually version 4. Versions 1 through 3 came and went before the Internet as we know it today existed.) IPV6 is designed primary to get around the most serious limitation of IPV4, which is the limited number of unique IP addresses—the Internet's equivalent of the telephone number—that can be assigned, about four billion. IPV6 will allow us to assign a network address to every computer, person, insect, microbe, and particle of gravel[*] on the planet and still have plenty left over. It will also greatly ease the job of routing Internet data around the globe.
Windows XP supports IPV6, although it's not widely used at present.
Earlier in the chapter, when I described UTP and coaxial cable media, I described the popular physical media and data link protocols used in LANs, and mentioned the Ethernet and Token Ring data link protocols. When you buy a network adapter, they come lumped together: You're buying a piece of hardware that performs both data-link and physical transport functions.
At the physical level, network cards send packets of data through their physical medium from one card to another. Network cards have two ways of sending data: unicast, which sends data directly from one card to another specific card, and multicast or broadcast, which sends the same data packet to every card on the network. Each network card has an address (like a phone number) that is actually built right into the hardware of the network card. It is called the physical network address or media access control (MAC) address.
When a unicast data packet is addressed directly to a MAC address, only the one intended computer receives and examines the data. When a broadcast is made, every computer receives the packet. When a packet arrives by either means, the network adapter uses a hardware interrupt to inform Windows that data has arrived. Windows reads the data out of the network card and passes it up to the next higher layer in the protocol stack to be examined and acted upon.
The preceding sections pretty much cover the technology for sending data from computer to computer. Next, let's look at how networks find computers by name. (I'll describe the process for TCP/IP. Networks based on the IPX/SPX protocol work in a similar fashion.)
My server's physical network (MAC) address is 00-C0-CA-14-09-2F, but I certainly don't want to know that, let alone type it very often. I just want to view files on the computer named Java. So, it's up to the network software to resolve the name Java into its MAC address 00-C0-CA-14-09-2F so that my computer can send requests to it. How this is accomplished depends on the transport protocol in use: the now-retired NetBEUI, or TCP/IP. The difference between the two is significant.
I'm sure you've tried to find a friend in a crowded airport lobby. The quickest way to find him or her is to stand up on a chair and shout out his or her name. Works like a charm, even though it momentarily interrupts everyone around you. The old NetBEUI protocol resolved names this way. It broadcast a request to every computer on the network: “Will the computer named Java please send me a message with your MAC address!”
This approach is fine when the desired computer is on the same physical LAN wire; in fact, it's great because it works without any configuration at all. But when two LANs are separated by a WAN link, NetBEUI's technique would require that the broadcast message be sent across the WAN. The WAN link would have to transmit every broadcast on every connected LAN to every other connected LAN to be sure that every computer could be found. Remember that WAN links were historically slow, on the order of 64Kbps, and with a few hundred computers sending a broadcast every minute or so, the WAN link would be fully occupied, carrying only broadcast messages and no useful data.
So, NetBEUI was a bad choice for networks with wide area links, and in fact, Microsoft has dropped support for NetBEUI in Windows XP as better ways have been developed.
An Internet Protocol, or IP, based network takes a more sophisticated approach to finding computers by name. To avoid relying completely on broadcasts for name lookups, IP networks rely on a directory service much like the 411 Directory Assistance service for telephones. IP-based protocols send requests for name-to-number lookups to a specific computer, which replies with the required address information. Microsoft supports two name-lookup services: WINS and DNS, which I'll discuss in more detail later on in this chapter.
But this just raises the question of how an IP-based computer can reach the computer hosting the naming service, which might be on a remote network far away. The MAC addresses built into network adapters are essentially random numbers, so knowing a remote computer's MAC address doesn't help you find it—you'd have to broadcast to every computer in the world to locate the destination!
The solution to this problem is that each computer in an IP network is given an IP address, which I'm sure you've seen before; it's a number like 63.69.110.193. These are like street addresses, and can be interpreted by routers all over the world to get data packets where they need to go. As the postal service first sends mail to a given state, then a city, then a street, then your house, so a router only has to know where to deliver data for all IP addresses starting with 63. Once it gets there, the 63 router sends the packet to the router responsible for all addresses starting with 63.69, which sends it to the router for 63.69.110, which finally sends it to computer 63.69.110.193. (I'm way oversimplifying this, but it should give you the picture.)
When data is sent using IP, the sending computer first determines whether the destination computer is on the same physical LAN. If the destination computer is on the same physical LAN, the sending computer uses the old stand-up-and-shout approach: it broadcasts a request for computer number 63.69.110.193 to please identify itself (in IP lingo, it ARPs). The other computer responds with its MAC address, and with that information the network adapter can deliver the packet to its destination.
When the IP address is not a local address, the sending computer forwards the packet to a router, which forwards the packet out across the WAN or the Internet, which is just a very large IP WAN. Routers along the way relay the packet from one router to the next by examining the IP address. The backbone routers of an IP WAN or the Internet know exactly where to send every IP packet, based on its IP address. Eventually, the packet finds its way to a router on the destination LAN, where the router ARPs and sends the packet to its intended computer.
How does a router or computer tell whether an IP address is local? The answer is in the subnet mask, that mysterious 255.255.255.something number that you've probably entered into at least one home computer to connect to the Internet.
An IP address is a series of four numbers between 0 and 255. It can be written in binary as a 32-bit binary number, as in this example:
11000110 01000110 10010010 01000110
A network mask can also be written in binary; for example, 255.255.255.240 is
11111111 11111111 11111111 11110000
The part of an IP address that lines up with the ones in its subnet mask is called the subnet number, and the remainder is the node number or node address.
IP address |
|
subnet mask |
|
subnet number |
|
node number |
|
Every computer on an IP LAN must have the same subnet number. If the subnet number of a destination IP address matches the sender's subnet number, the address is local: shout, get the MAC address, send directly. If the subnet number differs, the computer simply punts: It sends the packet to a designated gateway, a router whose job it is to ultimately deliver the packet.
TIP
You probably suspect that this description is an oversimplification. It's not, actually, for the simple case I've described. What I've left out are details about how routers decide which of several possible directions to send a given packet and how they communicate new routes and traffic reports to each other. For a detailed look at the IP protocol and network technology, you might check out the following books:
Practical Cisco Routers, ISBN: 0-7987-2103-1, Que
Upgrading and Repairing Networks, Fourth Edition, ISBN 0-7897-2817-6, Que
NOTE
If you're interested in the nitty-gritty details of Microsoft's implementation of network protocols, including TCP/IP timing, tuning, and Registry entry details, you might want to dig into the technical whitepapers at http://www.microsoft.com/Windows2000/techinfo.
As I mentioned earlier, a network card's MAC address is physically “burned in” to the adapter's hardware. But IP addressing must somehow be set up in software. We can't just pull a number out of a hat, because each computer on a LAN must use a number with the same subnet number and network mask, but a different node number than others on its local network. Also, it needs to know the address of its local gateway router, and the addresses of any name-resolving servers.
There's no simple automatic way for a computer to reliably determine this information. It can be assigned and entered manually, but on large networks, this is a cumbersome and difficult task.
To solve this problem the Internet community developed a protocol called BootP. Microsoft “embraced and extended” the BootP protocol and called the result DHCP (Dynamic Host Configuration Protocol). DHCP service can be provided by Windows 200x Server (as well as NT Server), the Internet Connection Sharing service, as well as virtually all routers and hardware Internet connection sharing devices.
When a computer using DHCP is started (booted) up, it broadcasts a request for an IP address on its local network. A computer running a DHCP server responds to this request with a reply packet that specifies an appropriate IP address, network mask, and other setup information. Since broadcasts aren't passed by routers to other connected networks, only the local DHCP server hears the request and responds with an appropriate local network address. Each DHCP server keeps track of which IP addresses it has assigned to local computers, to avoid handing out the same number twice. It's also responsible for recycling addresses when a computer leaves the network and stops using an address it's been given. So, it places a time limit on which a computer can use a given IP address—it's called a lease. Before the time limit runs out, the computer must contact the DHCP server to either renew its lease, or obtain a new number.
NOTE
Just when you thought things couldn't get more complex… they do. Small IP-based LANs with only Windows computers don't even really need a DHCP server. If Windows is set up for automatic (DHCP) IP configuration, and no DHCP server responds to the request for configuration information within 30 seconds or so, it does pull an IP address out of a hat. It picks a random IP address in the range 169.254.0.0 through 169.254.255.255.
Windows continues to ask for DHCP service every three minutes, and if a DHCP response does eventually arrive, Windows reconfigures itself accordingly.
Although this works, it's ugly: The boot process is delayed a while, and every three minutes the network will seem to “lock up,” over and over. The fix is to manually assign IP addresses in each computer.
Some people move their computers between networks with DHCP and static setups. This is especially common with laptop computers that commute between home and office. Office networks usually use DHCP, while home networks can be set up either way. Older versions of Windows had to be configured for one network and then had to be completely reconfigured (manually) for the other every time they were moved. If you're a commuter, you'll be happy to know that Windows XP Professional has a feature called Alternate Configuration, which lets you set up static IP information to be used when DHCP isn't present. This lets you more easily move between multiple networks, as long as only one has a static IP setup.
To return the discussion to name resolution, let me describe how a TCP/IP network turns names into addresses. Two name resolution systems can be involved: WINS and DNS.
The Windows Internet Naming Service, or WINS, was introduced with Windows NT, which was the first Microsoft operating system that allowed Microsoft File Sharing to operate over the TCP/IP protocol. Windows users are used to using one-word names to identify computers, and networks can contain computers using NetBIOS and IPX/SPX as well as the TCP/IP protocol. Microsoft developed WINS as an integrated address resolution system. It learns the names of all the computers connected to each network connected to the server running WINS and makes these names available to TCP/IP-based computers on those networks. When a new computer appears on the network, the computer registers itself with the WINS server so that other computers can find it by name.
More importantly, WINS servers trade information across a WAN or the Internet, making name service available out of the reach of NetBEUI-based computers. The addition of WINS and TCP/IP to Microsoft networking made file sharing across a WAN a much more efficient operation, as it removed the requirement for bridging NetBEUI packets across a WAN link.
It works like this: A WINS server can respond to broadcasts (“Will a WINS server please tell me the address of the computer named Java?”), but on a large network, you can also tell Windows to direct its request to a specific WINS server at a particular IP address. This way, a TCP/IP-based client can find computers across a WAN link, through TCP/IP's capability to efficiently route directly addressed packets from network to network, without the need to send broadcast packets across the link as well.
Domain name service, or DNS, is the name resolution system used by all Internet-based software, and now on most Windows 200x Server networks as well. The domain name service is a sort of distributed database system that looks up names like www.quepublishing.com and returns IP addresses like 198.70.146.70. It also provides Inverse DNS information, which tells you that IP address 63.69.110.193 is named www.quepublishing.com.
You can use DNS-based naming with Microsoft Networking, too. For example, you can tell Windows Explorer to view \server.mycompany.com. Windows tries WINS first, if it's set up, and then attempts to resolve the name using DNS. If DNS fails, Windows broadcasts a request to the local LAN. If one of these methods succeeds, Windows can go ahead and use Microsoft File Sharing to connect to the computer.
Because corporate networks are growing so large, the old “one word name” scheme for Windows networks is no longer adequate. On Windows 200x Server-based networks, Microsoft is encouraging the use of DNS-like names (such as host.region.company.com) even inside a company's network. Microsoft is making this use easier by tying the Windows 200x Server DNS service into the Active Directory, which identifies all of the network's computers, networks, users, and resources.
DNS was designed for the original 1970s' Internet with its fairly static database; entering new computers and domains was time-consuming. The DNS server provided with Windows 200x Server, however, interacts with the Microsoft networking system on a dynamic basis to learn the names of computers as they plug into and leave the network.
Now you know what the basics of what makes a network work. I've described how a network is composed of layers of software and hardware whose purpose is to let high-level client and server software provide useful services to you and the operating system. Security is a major concern in networks: after all, we can't have the mailroom staff looking up the executives' salaries.
The Windows approach to network security varies, depending on the type of network community to which it's connected. The following sections describe what these different network types are and how Windows XP changes with each one.
On a peer-to-peer or workgroup network, Windows XP Professional is a terrific member workstation, and you can set up shared folders with just the click of a mouse. XP Professional is also quite friendly with Windows 2000, NT, and 9x, and treats them as peers, too. It can attach to Novell NetWare and UNIX/Linux servers as well, if they're part of your network.
The downside of the peer-to-peer network is that each Windows workstation manages its own separate username/password database. Because there's no centralized control over user privileges, obtaining access to shared folders and printers on your LAN can be hit or miss. If you haven't been added as a user of the computer whose shared resources you want to use, you're out of luck.
Because networks are becoming so common even in the home, Microsoft introduced a feature with Windows XP called Simple File Sharing. With Simple File Sharing, passwords are dispensed with across the network. That is, files made available across the network are available to one and all. This is a fair compromise between simplicity and security for homes and small offices. The feature is optional on Windows XP Professional in a workgroup network, and is always enabled on Windows XP Home Edition.
Note
→ To learn more about shared folder security, see “Specific Configuration Steps for Windows XP,” p. 835.
Administration of the computers on a peer-to-peer network is handled on an individual basis also. Each computer has its own privileged “Administrator” account, so anyone with his or her computer's administrator password can have at the Windows setup and configuration, and a network manager has to know each computer's individual Administrator password.
Finally, to locate resources on a peer-to-peer network, you might have to hunt around a bit. Either you must know the name of the computer whose resources you want to use, or you have to poke around My Network Places (called Network Neighborhood in earlier versions of Windows). Poking around is fine on small networks but can be cumbersome on large networks with more than a few dozen computers.
When a Windows XP Professional computer is part of a network managed by Windows Server 2003, Windows 2000 Server, or Windows NT Server, something different happens: Windows XP Pro relinquishes the job of identifying users and their passwords to the server.
This is a good thing. This is called a domain network. A domain is a group of computers under the control of a central set of one or more domain servers. As part of a domain, when you log in on any member computer, your identity is actually verified by the server, and you are then automatically recognized by every other Windows XP, 2000, and NT computer on the whole network. Permission to view files, of course, can be granted or taken away by the owner of each computer; I'll explain how to manage permissions in Chapter 27, “System Utilities.” The point is that with a common user database you can better maintain good security practices, because you can manage access to resources in a much more coherent manner.
When you're part of a domain (or group of domains), locating shared resources is not necessarily any easier than it is on a peer-to-peer network. Either you need to know the name of the workstation or server you want to use, or you have to burrow through the domains and computers displayed in domain-sized groups on My Network Places.
Finally, as part of a server-based network, the “domain administrator”—that is, the administrator of the server computer—can exercise some serious control over what users of each computer can see and do, thanks to the Windows profile and policy systems. These features have two effects:
They provide a way to deliver the same desktop, Control Panel, and software settings to a user no matter which computer he or she uses.
They let the domain administrator individually remove or “lock down” Windows features and Control Panel options that change network, display, hardware, and network settings for individuals or groups of users. Maintenance and support costs are reduced by removing the users' ability to customize (in management's view: mess up) their own computers. Joking aside, this feature can save big companies serious money.
They let the network manager instruct Windows to store your “My Documents” folder and your preference settings on a central server, so that your personal files and settings will be available no matter which computer you log on to; you should be able to use any computer in the organization. This not only makes your job easier, it makes it easier for the network administrators to back up everybody's files at once, so that they can be recovered in the event of a hardware crash.
Quite a personality change, isn't it? Of course, exercising this kind of control is completely up to the domain administrator—use of each of these features is optional.
Finally, when Windows XP Professional is a member of a Windows 200x Server network with Active Directory, an even more comprehensive management structure comes into play. With Active Directory, the network administrators can do everything I mentioned in the preceding sections plus delegate management responsibilities to lower levels in the chain of command, at just about any level of detail they desire. This makes it possible for people in a big company's far-flung areas to manage computer resources for their local region, yet keep management privileges compartmentalized.
For example, a large company with many small branch offices could let branch managers assign users at their branches to departmental groups but not change their passwords. The network administrator could let the San Francisco network manager change network settings but not the Winnemucka manager, and so on. The level of what Microsoft calls granularity in control and delegation is nearly unlimited.
This capability could mean one of two things to you, the Windows XP Professional user:
Nothing at all because you're not part of an Active-Directory based network
Nothing at all because you are locked out of all this fun stuff by your network manager
I'm only partly kidding. If you're a Windows XP Professional user on an Active Directory network, these management features affect you only when they prevent you from doing something. The only new thing you have to learn is the telephone number of the network manager who's responsible for your computer. (This manager, on the other hand, has so much new to learn that he or she is probably in a class somewhere right now, on the verge of tears.)
Active Directory services also let network managers assign application software to users or groups, so your desktop automatically picks up icons for software you haven't even installed but your organization thinks you need. When you go to use it, Boom, it installs itself (in theory anyway).
Active Directory also lets you search for network resources and organizational information in a very useful, unified way. The Active Directory is designed to contain all kinds of information about the resources on a network, the network's users, and the structure of the organization itself. We're all used to the searching power on the World Wide Web, and Active Directory brings us the same power to search on a company's worldwide network. Want to find the email address of your pal Sal in the Sonoma Sales Center? No problem, Active Directory can find it in a flash. Need to find a printer in your building that can print on both sides in color? One click, and you'll have it.
I'll talk about Active Directory in more detail later in this chapter.
NOTE
Active Directory is based on the LDAP (Lightweight Directory Access Protocol) protocol, an Internet standard for querying hierarchical databases. Windows 200x Server runs an LDAP server on every Active Directory-enabled server computer. Administrative changes to the directory can occur on any member server, and the changes are replicated to all of the other servers. The location of the nearest Active Directory server is found using the standard DNS system. This makes it possible for a computer to join an Active Directory network and find its place in the world without any manual configuration: DHCP gives the computer its IP address and DNS servers, DNS locates Active Directory, and Active Directory delivers the rest of the information the computer needs to deliver any other appropriate services.
Windows XP Professional can also exhibit multiple personality disorder: Meet the remote workstation. Windows can behave like a standalone computer when you're toting your laptop around in the field, a workgroup computer when you're networked at home, and then it can act like a domain member when connected to the server-based network by modem or broadband connection from home or at a network cable or docking port at work.
An additional feature Windows XP Pro offers to the remote user is the “offline” file. Windows lets you mark files or folders for offline use and copies them from the network to your hard drive. When you're disconnected from the network, you'll have access to this copy, even though it still appears to be in a folder on another networked computer. When you reconnect, by modem or by plugging into the office network, Windows automatically synchronizes the offline files, copying anything you changed back to the network and retrieving any updated files from the network to your hard disk.
TIP
Offline files are similar to the My Briefcase function offered by Windows 9x. The advantage to offline files, however, is that they appear to stay in their original locations. Windows invisibly keeps track of the offline copies, so you don't have to worry about dragging files to and from the briefcase folder.
So, to My Briefcase: Good riddance! I have to admit I never understood or got My Briefcase to work anyway, and I suspect few people did.
Besides file and printer sharing, Windows XP provides many other network services. You might never interact with some of these services directly, but their presence makes Windows the amazing application platform it is.
Let's take a tour of Windows network services. I'll describe what each service is, why it's useful, perhaps a bit about how it works, and I'll tell you where to find out how to install, configure, or use it, if appropriate.
Networking software was originally developed in order to share and transfer files between computers. (America Online Buddy Chat came later, if you can believe that!) Windows XP comes with the following features:
Client for Microsoft Networks, which gives access to files and printers shared by other Windows computers as well as OS/2, UNIX, Linux, and so on.
File and Printer Sharing for Microsoft Networks, which lets Windows XP Professional share files and printers with users of those same operating systems. Windows XP Pro is limited to 10 simultaneous connections from other computers; the Server version is required for larger LANs.
Web Sharing, which is a new technology that provides secure file copying to and from shared folders over the Internet, using the Web's Hypertext Transfer Protocol. The “new” part is that it uses full Windows security and the Windows Explorer user interface, while the underlying technology is based on the World Wide Web and Microsoft's Internet Information Server.
Client for Novell Networks, which gives access to files and printers shared by Novell NetWare file servers.
Print Services for UNIX, which lets you use and share printers with computers using the UNIX operating system's LPR protocol.
Unlike Windows 200x Server, however, Pro has no tools to share files with Apple Macintosh computers or to use Macintosh shared folders.
Note
→ For information about installing, configuring, and using Microsoft network software, see Chapters 15 through 18.
Note
→ For information about interacting with Novell and UNIX servers, see Chapter 20, “Networking Mix and Match.”
When Windows XP Professional is connected to a Windows Server domain, besides simply validating usernames and passwords, Server can supply Pro computers with a profile for each user as he or she logs in.
A profile contains information that helps Windows XP Professional make its desktop and folders look the same no matter which physical computer you use. User profiles contain the following:
Desktop icons and shortcuts
The contents of your My Files and Documents folder
Your configuration and preference settings for all the software you use, from your Word preferences to your choice of screen savers
Management settings that control, for example, whether you are allowed to change Control Panel entries
Roaming user profiles are covered in more depth in Chapter 28, “Managing Users.”
Windows XP provides network protocols that let software application developers write programs that interact across a network. You will probably never have to install, configure, or even know such protocols exist; you'll just use the programs that use them and happily go about your business. But someone may mention them, so you should be familiar with their names: RPC and COM+.
Microsoft's remote procedure call (RPC) network protocol allows software to be split into pieces that run on different computers and interact across a network. The RPC mechanism is used, for instance, when a user on one Windows computer pauses print spooling on another. It's the basis of most of Windows's remote management capabilities; these are more sophisticated things than the authors of the basic file sharing protocols made allowances for.
The former Component Object Model (COM) and Distributed COM (DCOM) services have been combined in Windows 2000 and XP to the upgraded COM+ service. COM+ provides software developers tools to build highly modular software in a variety of languages. The “+” and “Distributed” parts refer to the service's ability to let software communicate across the network with software running on other computers. For example, Windows Management Instrumentation (WMI) uses COM+ to provide a means of remotely of monitoring and managing networked computers.
NOTE
If you read about the security improvements provided by Windows XP Service Pack 2, you may notice RPC and DCOM are mentioned. Before Service Pack 2, applications that used RPC and DCOM could receive “anonymous” connections from remote computers by default. After SP2, the default is for remote connections to require authentication. Also, by default, Windows Firewall blocks incoming RPC and DCOM requests, all of which initially use TCP Port 135. This port must be opened to allow remote computers to access RPC/DCOM services on your computer. In addition, Windows Firewall must be told which applications are allowed to receive the incoming connections. If you or your company has developed RPC or DCOM applications, configuration or programming changes will probably be necessary to make them work after installing SP2. (On a corporate network, this will be done through Group Policy.)
To learn more about COM and DCOM, pick up a copy of COM/DCOM Unleashed, published by Sams Publishing. For information about SP2 changes to RPC and DCOM, visit www.microsoft.com/technet and search for the words “dcom rpc developer sp2”.
Windows has a built-in network service called the Messenger service. This Messenger has nothing to do with the Windows Messenger instant messaging program discussed in Chapter 12. Rather, it's a very primitive system that lets computers on a network send short pop-up messages to each other. These services were designed to send simple notices, for example, to let Administrators notify users of an impending network shutdown and for print servers to notify users that their print job has completed.
The Messenger service displays received messages in a pop-up dialog. The related Alerter service can be set up to watch System Monitor parameters and send a message to an administrator if it detects an abnormal condition like a filled hard drive. Unfortunately, the services were widely abused by spammers and unscrupulous Web site operators to display advertisements. Therefore, after installing Service Pack 2, the Alerter and Messenger services will be disabled by default. (They can be restored by changing their startup setting to “Automatic” in the Computer Management “Services” list.)
With an unfortunate and confusing name, since this relatively new networking addition has nothing to do with the peer-to-peer networking we've been discussing so far in this chapter, Windows Peer-to-Peer Networking is a new service that lets software developers write applications that run on multiple computers. The potential applications include number-crunching tools that can take advantage of unused processing power on other people's computers, file and media sharing tools (think Napster), and discussion/collaboration/communication tools.
The .NET (pronounced “dot net”) initiative is Microsoft's most recent replacement for COM, DCOM, and RPC. .NET is an entire software framework for Internet-enabled software application development. Again, it's something that you will probably never interact with directly, but it will make possible a whole new generation of software applications.
Windows XP Professional can connect to remote LANs through the Internet using Virtual Private Networking (VPN). This very secure technology makes it safe to use Microsoft networking over the Internet.
Note
→ If you're interested in learning more about Virtual Private Networking, see “Virtual Private Networking,” p. 708.
If you travel with a laptop or often work from a location outside your physical LAN, you can still use RAS (Remote Access Service, also called dial-up networking) to interact with people and files on your network.
Note
→ For more detailed information about RAS, see “Dial-Up Networking,” p. 674.
Windows XP Professional allows you to configure a modem for incoming connections as well as outgoing. You can provide access to your LAN via modem, for example, to retrieve files from your office while you are at home or in the field. At most, two incoming connections are permitted with Pro.
Note
→ To configure Remote Access, see “Setting Up Dial-Up Networking,” p. 675.
Windows XP Professional also allows you to connect to your LAN via the Point-to-Point Tunneling Protocol (PPTP); that is, it lets you create a Virtual Private Network. If your LAN has a full-time Internet connection, it will (or it should) have a firewall installed, thus preventing you from using file sharing directly from the outside world. A VPN connection lets you safely penetrate the firewall to gain access to your LAN over the Internet.
Windows XP Professional and Windows 2000 Server/Windows 2003 Server provide a sort of remote-control system called, variously, Windows Terminal Services, Remote Desktop, and Remote Assistance. Terminal Services let you use a computer remotely. Your applications run on the remote computer, while you use your local computer's display, keyboard, and mouse. There are three names for what is basically the same piece of software, because it's used three different ways:
Terminal Services—. A Windows 2000 Server/Windows 2003 Server can be set up to host applications used by remote clients. For example, one beefy computer can run complex software, while the remote computers, which only need to provide a display and keyboard, can be relative lightweights. Terminal services is also great for remote administration of a server—a manager can sit in front of one computer, but can control and configure servers anywhere in the world.
Although the service is provided only by Windows 2000 Server/Windows 2003 Server, the client software is available for Windows XP, 2000, 9x, and NT.
Remote Desktop—. Windows XP Professional has a Remote Desktop feature, which is a copy of the Terminal Services server limited to one incoming connection. It's intended, for example, to enable an employee to access his or her Windows XP Pro computer at the office from home. When a remote user is connected, the XP computer's screen blanks out, so only one person at a time can use the computer.
Remote Assistance—. Windows XP Professional and Home Editions' Remote Assistance feature is based on—you guessed it—Terminal Services again, also limited to one connection. In this case, however, the desktop is not blanked out when the remote user attaches: It's intended for the remote and local user to work together to resolve a problem. Also, the remote connection can only occur when the computer owner emails the remote user an electronic invitation, which is good for one connection only. This makes the service useless for general remote-employee-type work, but handy for one-time assistance.
Windows XP Professional has a handy feature that first appeared in the Windows 98 Second Edition: Internet Connection Sharing. This feature lets one XP Pro computer with a modem or high-speed Internet connection provide Internet access to all users of a LAN.
This access is somewhat limited, however. It requires that the LAN use the Windows built-in automatic IP address configuration system, so it's incompatible with WAN configurations. It also requires that the computer with the modem or high-speed connection be left turned on all the time.
Connection sharing is described in more detail in Chapter 19, “Connecting Your LAN to the Internet.”
With Service Pack 2, Microsoft significantly beefed up the Internet security features of Windows XP. Windows Firewall replaced the earlier Internet Connection Firewall. Among other things, Windows Firewall addresses one of the more stunning deficiencies in the older firewall, which left computers unprotected for 10 to 30 seconds during the bootup process. You might not think that 10 to 30 seconds is much, but with millions of Windows-based computers connected to the Internet, thousands of computers got infected by computer viruses and worse through that window of opportunity.
Windows Firewall is discussed in Chapter 19, “Connecting Your LAN to the Internet,” and in Chapter 21, “Network Security.”
Windows XP includes support for Universal Plug and Play (UPnP), a network protocol that lets “smart” networked devices advertise their presence on the network. For instance, many of the inexpensive Internet connection sharing routers on the market are UPnP-enabled. Windows XP will automatically detect their presence and can to a limited extent let you configure them through the Windows interface. More importantly, UPnP lets network-dependent application software like Microsoft Messenger function correctly across an Internet router; UPnP provides a means for the application and the router to talk to each other.
There is some discussion of UPnP in Chapter 12, “Chatting and Conferencing with Windows Messenger,” and more in Chapters 19 and 21.
As discussed earlier in this chapter, Windows 2000 and Windows XP can take advantage of a service called the Active Directory (AD). Active Directory combines a name/address directory, management and security services, and wide-area replicated database technologies to provide a foundation for all of Windows' networking functions. If your network is managed by a Windows 200x Server with AD installed, this service is automatically and transparently made available to you. AD is entirely based on TCP/IP technology, and for this reason, all Windows XP computers should use TCP/IP as their primary, if not only, network protocol.
Note
→ To learn how to use Active Directory services, see “Exploring and Searching the Network,” p. 619.
Active Directory is a distributed database. Distributed means that information about separate parts of a geographically dispersed network are automatically copied from region to region, from server to server, so that the same information is available at all locations. Any of the information can be managed from any location, and the changes made automatically propagate throughout the network. This might not matter or make sense to the user of an eight-person network, but to the manager of a corporate network that spans several continents, the ability to manage a given computer just as easily from Canada as from Canberra is very appealing indeed.
Active Directory is a true database: It can store any sort of information. Out of the box, it's used to store usernames, passwords, group membership, privileges and other security information, and feature-limiting controls called Group Policies, as well as the names and locations of computers and network printers. But it can also be used by software developers to store arbitrary information about software applications, such as the location and names of the nearest database servers—anything that would be useful to have spread throughout an organization's network.
The most significant part of AD is that it's hierarchical: It arranges information in user-defined groups called containers, which can be nested to any depth. The purpose of this hierarchy is to let AD represent the real structure of an organization. AD lets a network manager define groups by geographical region, department, workgroup, function, or whatever categories make sense to the organization. Each grouping can contain other groups, until finally actual users and/or their computers, printers, and other resources are entered.
The purpose of this feature is to enable network managers to assign usage and management privileges like the right to access certain files or the right to manage user accounts to these containers at appropriate levels, rather than to individuals. A network manager therefore can grant access to users based on the organization's own structure rather than on a user-by-user basis or through “flat” enterprise-wide groups.
For example, let's say a company has East Coast and West Coast divisions and an accounting department in each (see Figure 15.9).

Figure 15.9. Active Directory lets network managers define groups based on actual organizational structure. These groupings model the organization's chains of command. The resulting structure can then be used to sensibly control access privileges and to delegate management rights.
If the network manager grants read and write privileges to a shared network folder to the East Coast container, then all users anywhere in the East Coast structure (Jose, Sue, Bob, and Mary) get access rights to the folder. If Jose is granted “manager” rights to the East Coast Accounting group, then he can control the user accounts for Sue and himself.
Management of all East Coast printers could be granted to a network manager by granting him management rights to the East Coast container. He then would get the right to manage any printers within the entire container, across all its subdivisions.
Active Directory can be integrated into the domain name system for a company's network so that, for example, a computer in the East Coast accounting division could be named bigbox.accounting.eastcost.mycompany.com.
Active Directory is used internally by Windows tools such as Explorer, My Network Places, and the Printer Manager. User-written programs can get access to the directory's contents through a programming interface called Active Directory Services Interface (ADSI) or more generally through an Internet protocol called Lightweight Directory Access Protocol (LDAP), which is an industry standard for directory queries and responses. Email programs, for example, can be designed to use LDAP to search for email addresses, regardless of the underlying network system, whether it's based on Windows, Novell NetWare, or other networking systems.
You might hear the term IntelliMirror and wonder what sort of network feature it is. IntelliMirror actually is just Microsoft's name for several features and services provided by its domain networks based on Active Directory. These are
Remote Installation—. Windows XP can be installed from scratch onto an empty hard drive over a network.
Roaming User Profiles—. Your My Documents folder and your preferences settings are stored on the network servers and copied to the computers you use, so they're available anywhere on your enterprise network.
Group Policy—. Windows's capability to “force” preferences settings and restrict access to system configuration dialog boxes is based on Registry entries defined by the network administrators and copied to your computer when you log in.
Application Publication—. Application software such as Word and Excel can be installed automatically across the network, based again on Group policy settings.
Together, these features let network administrators give you the experience of walking up to any computer in your organization and having it be “your” computer with all your files, settings, and applications. You should, in theory, even be able to log off, throw your computer out the window, and replace it with a brand new, empty one, and in short order pick up your work where you left off. In theory, anyway.
Finally, Windows XP comes with a full complement of applications and tools that Internet and UNIX users expect on a TCP/IP-based computer. They're not part of Windows Networking, technically speaking, because they don't use the Networking Clients. They communicate with other computers using TCP/IP directly. These tools include the following:
Internet Explorer (Web browser)
SNMP Agents
Telnet
Ping
FTP
NetMeeting
nslookup
pathping
tracert
Outlook Express (SMTP/POP mail client)
Internet Information Server (Web server)
These programs are discussed in Part III of this book, “Windows XP and the Internet.”
Finally, Windows XP Professional, when it's part of a Windows Server-based network, supports the use of two very sophisticated network security systems to encrypt network traffic and to communicate passwords and information about user rights between computers.
Windows XP Professional supports the IPSec TCP/IP data encryption standard. IPSec provides a means for each of the data packets sent across a network to be encrypted—scrambled—so that an eavesdropper with a wiretapping device can't glean passwords or other sensitive information from your data while it flows through the wires of your building, through airwaves in a wireless network, or across the Internet.
Windows XP also supports the Kerberos network authentication protocol, which was developed at to the Massachusetts Institute of Technology (MIT) and is now widely used in secure distributed network operating systems. Kerberos manages the identification of computer users on a network to eliminate many network security risks, such as the recording and playback of passwords.
I've found that modern network software works perfectly the first time about 99 percent of the time. When things go wrong, however, you quickly find that the diagnostic tools are nowhere near as sophisticated, automated, or helpful as the installation tools. You need a more complete understanding of network technology and structure to diagnose a broken network than you do to install one, and more to the point, a more complete understanding than I can give you in a general-purpose book like this.
So, the big tip for this chapter is this: If you're planning to set up a network for more than a few computers, or you're setting up a network in a business situation, you should have some pretty solid expertise at hand for the times when problems arise. You might have a consultant install and maintain your network, or you might at least establish a relationship with a consultant or technician whom you can call if you run into trouble.
If you want to become a networking professional yourself, I recommend the following books as places to continue your training:
Upgrading and Repairing Networks, Fourth Edition, ISBN: 0-7897-2817-6, Que
Practical Network Cabling, ISBN: 0-7897-2233-X, Que
Practical Network Peer Networking, ISBN: 0-7897-2247-X, Que
Practical Firewalls, ISBN: 0-7897-2416-2, Que
[*] I'm exaggerating a bit. There actually aren't enough IPV6 addresses to include all of the gravel.