INTERNAL CONTROLS FOR THE INTERNET, INTRANETS, AND EXTRANETS (STUDY OBJECTIVE 9)
The Internet, intranets, and extranets are all networks that are intended for the sharing of information and the conducting of transactions. In all three networks, controls must be in place to limit access and prevent hackers and other network break-ins. As illustrated in Exhibit 14-7, extranets must have more limited access than the Internet, and intranets must limit access to those inside the company. For all three network levels, a company must establish the correct level of controlled access. In the case of intranets, only internal employees are given access to the network and information. Extranet access should be limited to those parties in the supply chain who will be sharing information or engaging in exchanges with the company. The general public must be prevented from gaining access to these intranet and extranet networks. The Internet connections of a company must also be controlled. When a company uses the Internet for exchanges such as B2C transactions, it must by default give access to all potential customers. However, controls must still exist to limit those customers' access. For example, a potential customer of Amazon.com would need to know whether a particular book was in stock and available for immediate shipment, but would not need to know the number of units in stock of that book. On the other hand, a supplier in the supply chain of Amazon.com would probably need access to inventory levels by virtue of being a part of the extranet of Amazon.com. The point of this illustration is that a company must establish and maintain controls that limit access to the appropriate level for related parties. Customers, suppliers, and employees need different levels of access, as well as access to different types of data. Therefore, a company must carefully implement and maintain proper controls over Internet, extranet, and intranet network connections.
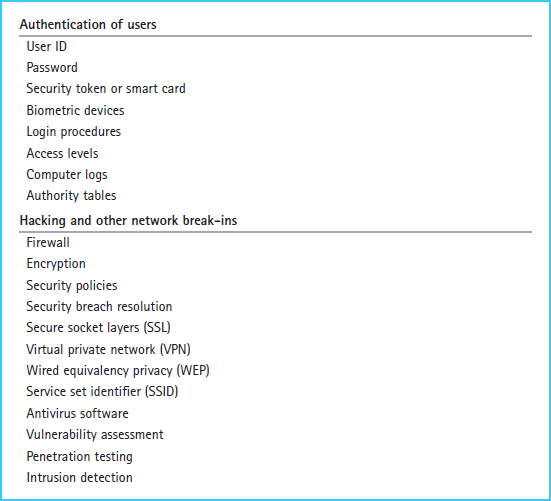
Access is limited by establishing appropriate internal controls such as firewalls and user authentication. The establishment and use of user authentication is intended to prevent log-in to the intranet or extranet by unauthorized users. Firewalls prevent external users from accessing the network and data on the extranet or intranet. Chapter 4 described in detail risks and controls for IT systems. Two of the categories of risks and controls that can limit access to intranets and extranets are reproduced in Exhibit 14-8.
Exhibit 14-8 Controls to Limit Access to Intranets and Extranets