GENERAL CONTROLS FROM AN AICPA TRUST SERVICES PRINCIPLES PERSPECTIVE (STUDY OBJECTIVE 3)
A reference list for the general controls described in the previous section appears at the end of this chapter as Exhibit 4-11 (page 177). Each of the general controls is intended to prevent, detect, or correct risks and exposures in IT systems. A company may choose not to use all of the controls described previously. Each organization should decide which combination of IT controls is most suitable for its IT systems, making sure that the benefits of each control outweigh its costs. As an example, you probably would not spend money to install an extensive car burglar alarm system in your 1988 Honda Civic. The cost of the burglar alarm would outweigh the benefits.
When considering IT risks, organizations should implement those IT controls which are cost beneficial. As a framework to discuss these IT risks, the AICPA Trust Services Principles categorizes IT controls and risks into five categories:4
- Security. The system is protected against unauthorized (physical and logical) access.
- Availability. The system is available for operation and use as committed or agreed.
- Processing integrity. System processing is complete, accurate, timely, and authorized.
- Online privacy. Personal information obtained as a result of e-commerce is collected, used, disclosed, and retained as committed or agreed.
- Confidentiality. Information designated as confidential is protected as committed or agreed.
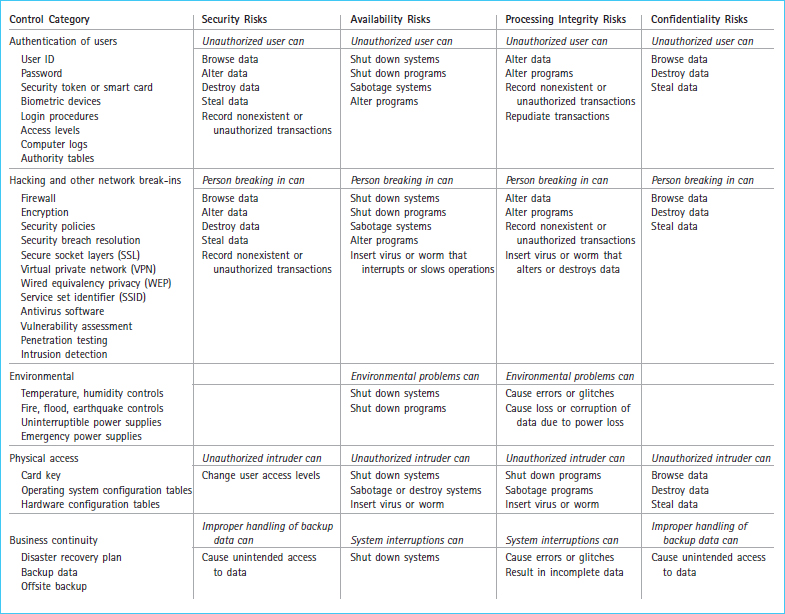
The fourth category, online privacy, applies only to e-business (discussed in a later chapter on e-business). The other four risk categories are used in this section to describe the concepts of controls and risks in IT systems. For each of these four categories, this section describes some of the risks and the corresponding controls, which are summarized in Exhibit 4-5. This is not a comprehensive list of risks, but a summary of some common risks along the four categories of security, availability, processing integrity, and confidentiality.
Perhaps the best way to understand these risks and the corresponding need for IT controls is to consider the absence of any IT controls. As an analogy, consider the likely negative consequences that could occur if your car doors did not have locks. Car door locks exists to prevent the specific risks of break-in and theft. Car door locks lessen these risks, but do not completely eliminate them. The sections that follow describe some of the potential risks in IT systems and controls that can reduce them. Much like car door locks, controls reduce risks; but it is impossible to completely eliminate risks.
RISKS IN NOT LIMITING UNAUTHORIZED USERS
The top section of Exhibit 4-5 lists eight IT controls related to authentication of users. These were described in the previous section as controls that can lessen the risk of unauthorized users gaining access to the IT system: user ID, password, security token, biometric devices, log-in procedures, access levels, computer logs, and authority tables. Consider the likely results if these controls were completely missing from an IT system: An unauthorized user could easily access data and programs he should not have access to, change data, record transactions, and perhaps even have a company check written directly to himself. Unauthorized users could be from inside or outside the organization. In addition, the lack of a user ID and password would mean that the company would be unable to determine which users accomplish which tasks. There would be no computer log of tasks accomplished by individual users.
There are several security risks resulting from unauthorized access. However, it is important first to understand the nature of unauthorized access. While the most popular type of unauthorized access is probably by a person unknown to the organization, employees of the organization also may try to access data to which they do not need access to perform their job duties. For example, a person who works in an accounts receivable department has no need to access payroll data. Data within the organization should be protected from internal unauthorized access as well as from external access. Unauthorized access to the IT system can allow persons to browse through data that is beyond the scope of their job duties, alter data in an unauthorized manner, destroy data, copy the data with the intent to steal and perhaps sell to competitors, or record unauthorized transactions. Establishing log-in procedures that include user IDs, passwords, security tokens, access levels, biometric devices, and authority logs can help prevent or lessen these security risks. These are preventive controls. The computer log of attempted log-ins can be periodically reviewed to determine whether unauthorized access or any attempt to gain unauthorized access has occurred. The organization can then change policies or practices if necessary to prevent further unauthorized access. The computer log serves as a detective control to assist in the discovery of unusual log-in attempts.
Exhibit 4-5 Control and Risk Matrix in IT Systems
Availability risks must be assessed and controlled by authentication of user controls. Once a person gains unauthorized access, it is conceivable that he may tamper with the IT system in a manner that may shut down systems and/or programs. These interruptions would obviously make the system or program temporarily unavailable for its intended use. An unauthorized user could also sabotage an IT system by inserting malicious program code to be triggered later. For example, suppose Company XYZ fires a disgruntled programmer, but fails to revoke the user ID and password immediately. Before that programmer cleans out his office and leaves, he may insert into the system some malicious instructions that erase the accounts receivable files during its next regularly scheduled run. Many years ago, this happened to a company; It was unable to recover the files and eventually filed for bankruptcy. This type of malicious code can be triggered by a particular date, a scheduled run, or another set of system circumstances. In addition, the unauthorized user may simply change the program itself. Lessening the chance of unauthorized access through authentication controls can help prevent these availability risks. The computer log would assist in tracing the person responsible for shutting down systems and programs, sabotaging systems, or altering programs.
Processing integrity can be compromised without adequate authentication controls. Processing integrity refers to the accuracy, completeness, and timeliness of the processing in IT systems. If unauthorized users access the IT system, they could alter data to change the results of processing. This could occur prior to the transaction being processed, during processing, or after the processing is complete. In all three cases, the accuracy or completeness of processing would be affected. For example, after a sale has been processed, an unauthorized user could delete the amount due to the company in the accounts receivable record. The unauthorized user could also alter programs to affect the results of processing. An unauthorized user might change program instructions to automatically double the hours worked for a particular person every time a payroll check is written for that person. Unauthorized users are sometimes able to circumvent other controls and insert transactions that are fictitious or unauthorized.
Another processing integrity risk is repudiation of real transactions. After a sales transaction has been processed, it may be possible for an unauthorized user to erase traces of the transaction and claim that they do not owe money to the company. Attempting to limit unauthorized users through log-in and authentication controls helps reduce the chances of these risks occurring. Computer logs may facilitate tracing of the alteration of data or unauthorized transactions to the responsible person.
Confidentiality risk, or the risk of confidential data being available to unauthorized users, can occur if authentication controls are weak. An unauthorized user who gains access can browse, steal, or destroy confidential data. Improving authentication and log-in controls helps limit the chances of confidentiality risks. Computer logs can assist in detecting such compromises of data and in tracing them to the responsible person.
Proper use of authentication controls and computer logs can help limit all four categories of these risks. As is always true, these risks cannot be eliminated, but they can be reduced by the use of appropriate controls. Each organization should assess the level of these risks and apply the controls that are cost beneficial for their system.
RISKS FROM HACKING OR OTHER NETWORK BREAK-INS
Hackers or others who break into computer networks are usually thought of as being outside the company. While this is often true, a hacker could be an employee of the organization who hacks in from home or at work. In fact, employees can sometimes be more dangerous because of their knowledge of company operations and potential access to company information or assets. Whether the threat is from an insider or outsider, efforts should be made to reduce the risk of hacking or network break-ins and to limit the harm that can result. The controls that may be applied are firewalls, encryption of data, security policies, security breach resolution, secure socket layers (SSL), virtual private network (VPN), wired equivalency privacy (WEP), wireless protected access (WPA), service set identifier (SSID), antivirus software, vulnerability assessment, penetration testing, and intrusion detection. Intrusion detection is a detective control, while the others are preventive.
The security risks related to hacking and network break-ins are the same as those identified in the previous section on unauthorized users. Those who break into a computer network have obviously breached security and could browse, alter, or destroy data. The use of the controls listed in the previous paragraph and in the second group in Exhibit 4-5 can help reduce the security risks of network break-ins, as well as reduce the potential damage if break-ins do occur.
The availability risks are that the network break-in can allow systems or programs to be shut down, altered, or sabotaged. The person who breaks in may also plant a virus or worm into the system. The processing integrity risks are that the person breaking in can alter the data or programs to compromise the accuracy or completeness of the data. Recording nonexistent or unauthorized transactions will also compromise data accuracy or completeness, as could planting a virus or worm. Again, there is a confidentiality risk, since the person breaking in may access, browse, steal, or change confidential data.
RISKS FROM ENVIRONMENTAL FACTORS
IT systems can be negatively affected by the environment in which they operate. Extremes of temperature or humidity can cause operating problems, especially to large mainframe computers, which are sensitive to heat and high humidity and therefore must be placed in rooms in which the climate is tightly controlled. Interruptions to the electrical power can cause systems to go down. It is not possible to prevent power outages caused by thunderstorms, fire, flood, or earthquake, but building location and construction can reduce the effects of these natural disasters. For example, a computer system should not be located in an area that frequently floods. Uninterruptible and emergency power supplies can be used to continue operations during power outages caused by natural events, because, for example, a thunderstorm can cause a lengthy power outage without actually being as disastrous as people commonly think, in terms of death and destruction.
Any environmental changes that affect the IT system can cause availability risks and processing integrity risks—the risks that systems can be shut down or errors and glitches in processing can occur which cause lost or corrupted data. Backup power supply systems allow IT systems to be gradually shut down without the loss or corruption of data.
PHYSICAL ACCESS RISKS
Physical access to computer systems and computer rooms should be limited to those who must have access in order to carry out their job assignments. Others who gain access (intruders) pose risks to the IT systems. The security risk is that an intruder who gains physical access may change user access levels so that she can later access data or systems through any network attached system. The availability risks are that unauthorized physical access would allow an intruder to physically shut down, sabotage, or destroy hardware or software. In addition, physical access may make it possible for an intruder to insert viruses or worms from diskette, CD, or other media. An intruder may interrupt processing and thereby affect the accuracy or completeness of processing. Thus, processing integrity risks are that systems or programs may be shut down or sabotaged. Viruses and worms can also affect the accuracy and completeness of processing. An intruder poses confidentiality risks in that she may be able to gain access to confidential data to browse, alter, or steal.
BUSINESS CONTINUITY RISKS
Many things can interrupt business continuity, including natural disasters. Due to the critical importance of IT systems to business continuity, there must be controls to limit IT risks related to business continuity and natural disasters. However, as part of continuity planning, an organization must still keep backup copies of data on-site and off-site. The existence of backup data poses a risk in that it affords another opportunity for unauthorized access. The security risk is that an unauthorized person may gain access to the backup data. Without proper business continuity planning, disaster recovery planning, and backup data, adverse events can interrupt IT system operation. The availability risk is that as events interrupt operations, the system becomes unavailable for regular processing. The processing integrity risk is that business interruptions can lead to incomplete or inaccurate data. The confidentiality risk is that unauthorized persons may gain access to confidential data if they access backup data. A coordinated effort regarding business continuity planning, disaster recovery planning, control over backup data, and correct use of these procedures can limit the risks.