RISKS AND CONTROLS IN GENERAL LEDGER PROCESSES (STUDY OBJECTIVE 6)
In terms of the five internal control activities described in Chapter 3, following are common procedures associated with the general ledger.
AUTHORIZATION OF TRANSACTIONS
The general ledger accumulates subtotal data from the previous processes within the company. For example, sales subtotals are posted to the general ledger sales account. Each of those individual sales was authorized when the sale occurred. Chapter 8 describes the authorization of sales. However, there must also be proper authorization to begin the process of posting from the sales journal to the general ledger.
In the case of a manual accounting system, a journal voucher is prepared by a manager in the sales department, and that approved journal voucher is forwarded to the general ledger department. The journal voucher includes the dollar amounts, the accounts affected, and an authorized signature. Posting to the general ledger should not occur without a signed, authorized journal voucher from the department that accounted for the process. For example, wages and deductions are not posted to the general ledger until the payroll department forwards a signed journal voucher. The signed journal voucher serves as authorization to post the payroll data to the general ledger.
In a computerized accounting system, paper journal voucher documents may not exist. In these systems, individual transactions may be entered into special modules, but not posted to the general ledger until the batch of transactions is completely entered and errors are corrected. For example, sales for an entire day may be entered in the “Sales” module, but not posted to the general ledger until the end of the day.
Approvals for each journal voucher are general authorizations rather than a specific authorization. Through the assignment of limited access to the general ledger module, management can limit the capability of general ledger posting to selected employees. One set of employees would have a user ID and password that would allow them to enter individual sales in the “Sales” module. Another employee or set of employees has access that allows her or them to post to the general ledger. Employees who have not been given access to general ledger posting will be unable to post to the general ledger. This assignment of separate duties enables management to give authority to general ledger employees to post to the general ledger.
Computerized accounting systems have different levels of automation. As the computerized accounting systems become more complex and integrated, there are usually fewer manual processes. With more automation and fewer manual steps, responsibility for authorization gets moved to lower and lower levels of employees. For example, if a computerized accounting system automatically updates the general ledger as individual transactions are entered, there is no need for a separate posting step. Thus, the employee who enters the details of the sale has, in effect, authorized the general ledger posting. In many IT systems today, the accounting systems are extremely complex, automated, and integrated, and they place the authorization at the lower-level employees.
THE REAL WORLD
Consider the checkout lanes at a department store such as Walmart. Around the world, there are employees working checkout lanes who are scanning products by passing them over the bar code scanner and accepting payment. In a large company such as Walmart, it would be tremendously inefficient for the system to delay the general ledger posting until a specific employee logs in to conduct the posting. Rather, when the checkout lane employee completes a sale by accepting payment and printing a sales receipt, he or she has authorized an event that will automatically update sales, inventory, and cash balances.
Many large corporations that sell to other companies have even more complex IT accounting systems, often connected to vendor and customer IT systems. In these systems, a sale might actually be authorized by the customer. Therefore, these systems require preexisting and negotiated relationships between buyer and seller companies. Both parties must have already approved these processes and established IT systems that execute the processes.
THE REAL WORLD
Walmart and Procter & Gamble (P&G) have interconnected IT systems. P&G sells consumer products such as soap, shampoo, and diapers to Walmart. A sale by P&G to Walmart is actually triggered by the Walmart IT inventory system. As Walmart inventory levels of certain products fall below established reorder points, the systems interact and authorize a transfer of products from P&G to Walmart. This means that P&G's sale and the subsequent update of its sales and receivable accounts are activated by its customer's computer system. Similarly, Walmart's purchase and update of its inventory and payables accounts are triggered by this system.
Whether the system is manual or computerized, posting to general ledger accounts should occur only when proper authorization exists. In manual systems and less complex computerized systems, the authorization to post is vested in the journal voucher. In more complex accounting systems, certain employees are authorized to record specific events that automatically post transactions to the general ledger. Whether the authority is vested in employees or in connected IT systems, management must establish the method of authorization it desires in its accounting system.
SEGREGATION OF DUTIES
In manual accounting systems, segregation of duties is a desirable internal control. Employees who post journal vouchers have responsibility for record keeping. For proper segregation, those employees should never have authorization or custody functions. General ledger employees should only record journal vouchers from other operational departments that have been authorized by managers in those departments. The general ledger employees should never be given responsibility for authorizing any journal vouchers. Also, general ledger employees should never have custody of any assets that they record in the general ledger. If these employees have both custody and record keeping functions, they have a capability to steal assets and alter the records.
A third segregation in a manual general ledger system is that general ledger functions should be segregated from special journal and subsidiary ledger tasks. The special journals, subsidiary ledgers, and general ledger serve important, but separate, record keeping and control functions. Special journals and subsidiary ledgers have details of many subaccounts, such as sales revenues and an account balance for each customer in the accounts receivable subsidiary ledger. The general ledger sales and accounts receivable accounts maintain overall increases, decreases, and a balance in those accounts. At all times and for each special journal and subsidiary ledger, total balances should equal the balance in the corresponding general ledger account. As examples, the total of the sales in the sales journal should equal the balance of sales in the general ledger, and the total of the accounts in the accounts receivable subsidiary ledger should equal the balance of accounts receivable in the general ledger. By separating the record keeping function for these two types of records, control is enhanced. Two separate parties are keeping independent, but related records. If there are problems with the reconciliation of the two records, it may be the case that errors or fraudulent acts have occurred. Separating general ledger from special journal and subsidiary ledger functions increases the likelihood that errors or fraud will be prevented or detected.
In summary, three important segregations should be in place in a manual general ledger system. General ledger employees should record journal vouchers, but they should not
- authorize journal vouchers
- have custody of assets
- have recording responsibility for any special journals or subsidiary ledgers
Computerized accounting systems may not have the same types of segregation. Segregation of functions may not be possible in IT systems if manual functions have been computerized. Whether segregation of functions is possible depends on the complexity of the IT accounting system. Simple accounting systems may still have some segregation of functions for general ledger record keeping, while more complex systems will not. Microsoft Dynamics GP® software is an example of a relatively less complex accounting software system for small and mid-size businesses. In such an accounting system, segregation is achieved by allowing different levels of access for different employees. This concept was described in the previous section on authorization. Essentially, general ledger functions and posting can be assigned to certain employees by the limiting of access to the general ledger functions on the basis of log-in IDs. Exhibit 12-9 shows a general ledger posting window in Microsoft Dynamics GP® accounting software. User IDs and passwords can limit access to this window to only selected employees. The employee who is given access to this window would choose which batch entries to post, place a checkmark in the box next to the batch, and select the Post option.
More complex accounting software may post to the general ledger system automatically as transactions are processed. In this case, segregation of general ledger functions is not likely, because there are no employee functions within the general ledger system. However, incompatible duties in processes that eventually post to the general ledger can still be segregated.
THE REAL WORLD
In an ERP system with potentially thousands of users and processes that automatically trigger other processes, how is segregation of duties managed? A typical ERP system has many automated triggering processes. Following is an example of automatic triggering and the effect on segregation of duties:
Customer orders for goods may automatically trigger production runs, which in turn trigger inventory purchases communicated by electronic data interchange to specified suppliers. When the warehouse clerk receives inventory from the supplier, he or she makes an entry to the system from the receiving dock, changing the status of the purchase order from “open” to “received.” When accounts payable receives the invoice, which may occur electronically, the system matches goods received to invoices received, automatically creating a payable and scheduling payment.2
Exhibit 12-9 General Ledger Posting in Microsoft Dynamics GP®
Notice in this ERP example that if one person's user ID and password allowed the authorization of both the purchase and receiving entry, he or she could execute processes that automatically match goods to invoices and prepare a payment. Therefore, as user IDs and passwords are assigned, proper segregation must be considered. A user should not be able to process incompatible duties, such as those cited in the foregoing purchase and receiving example. In addition, an ERP system should segregate authorizing a transaction from updating the related master file. As an example, a user's profile should not allow the initiation of a purchase and the maintenance of the approved vendor list (the master file). Since incompatible duties may allow one person to process potentially fictitious or fraudulent transactions that would eventually be posted to the general ledger, these transactions would automatically be included in the company's financial statements. Therefore, in order to promote accurate financial reporting, ERP systems must control access so that incompatible duties cannot be performed by any employee. Chapter 15 discusses more details of segregation of duties in ERP systems.
ADEQUATE RECORDS AND DOCUMENTS
To maintain adequate records and documents in a manual general ledger system, there are two important requirements. First, the organization must have a well-defined chart of accounts. To reduce the chance of misclassified transactions that are posted to an incorrect account, the chart of accounts must be designed in a way that minimizes confusion about the types of transactions that belong in each individual account. The chart of accounts should have a sufficient number and type of accounts that facilitate the accurate classification of transactions. For example, if there is no “Rent Expense” ledger account, users will be uncertain where to post a payment for rent. Different users could post it to different accounts. This nonconsistency would make the balances in those accounts less useful, since no one could easily tell whether rent is included.
Second, there must be an adequate audit trail to allow tracing transactions back to the source. All transactions of the organization should have an audit trail that allows the transaction to be tracked from its initiation through its recording in the general ledger. In a manual system, the source documents, special journals, subsidiary ledgers, journal vouchers, and general ledger make up the audit trail. Using this documentation, a transaction can be traced from the source document to the general ledger. Transaction tracing can also occur in the opposite direction, starting with the general ledger and tracing the amounts back to the original source documents.
In computerized IT accounting systems, the audit trail may be made up of electronic images in files, with no supporting paper documents or records. Thus, the audit trail could be either of these extremes—paper documents or computer files—or the audit trail could be partially paper based and partially electronic images. For example, the audit trail would be made up of paper source documents, transaction logs, transaction files, and master files.
SECURITY OF THE GENERAL LEDGER AND DOCUMENTS
In manual systems, the general ledger and supporting documents must be protected from unauthorized access that might allow records to be fraudulently altered. The paper documents and records of manual systems can be protected by limiting the number of people who have access to these documents.
IT accounting systems protect record access in a different way. For electronic file images, access can be limited through the proper use of user IDs, passwords, and resource authority tables. These general controls establish which employees have access to specific records or files.
INDEPENDENT CHECKS AND RECONCILIATION
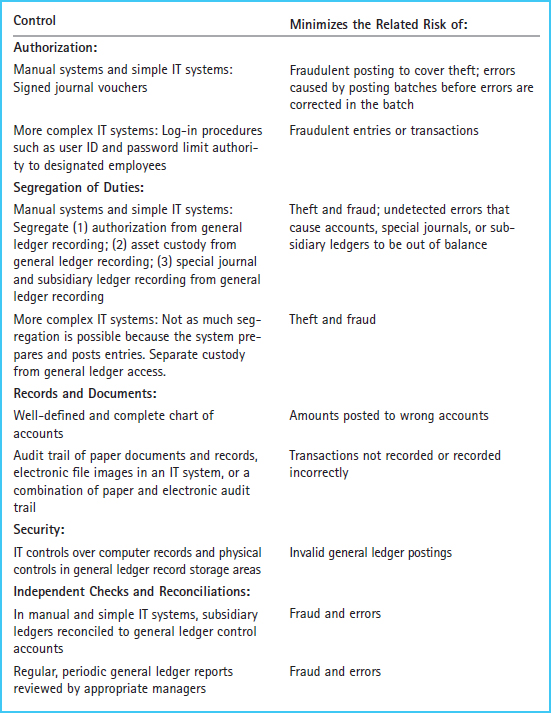
In a manual general ledger system, the reconciliation of special journals and subsidiary accounts to the general ledger control accounts is an independent check on the accuracy of recording regular, recurring transactions. In addition, appropriate managers should regularly review general ledger reports for accuracy and completeness. In an IT system, reports are checked for correctness by printing and cross-checking the reports against each other to ensure their accuracy. Exhibit 12-10 summarizes the controls and risks in general ledger processes.
Exhibit 12-10 General Ledger Controls and Risks