HARDWARE AND SOFTWARE EXPOSURES IN IT SYSTEMS (STUDY OBJECTIVE 4)
The previous sections described and linked risk areas to corresponding controls. To properly understand these risks, we must also understand their possible sources. Consider a burglar alarm analogy. One risk in owning a building is the possibility of break-in and theft of assets from the building. A control to help prevent that risk is a burglar alarm. But to know how to install the sensors for a burglar alarm, the installer must know the potential points of entry, which would be any door or window in the building. Doors and windows serve useful purposes and make the building more efficient, but each one is a risk area and the sensors for the burglar alarm must be placed at each of the windows and doors. In a similar manner, components of an IT system can be thought of as areas that open risks for an organization, or “entry points.” In an IT system, there are security, availability, processing integrity, and confidentiality risks. General controls (described earlier) can help limit those risks, but the “entry points” over which these controls should be placed must be identified. This section describes the typical IT system components that represent “entry points” where the risks must be controlled.
There are so many different types of hardware and software that can be used in an IT-based accounting system that no two organizations are likely to have identical hardware and software configurations. Each organization selects and implements hardware and software according to its specific needs. Since this chapter cannot possibly cover all possible hardware and software configurations, it describes typical components in generic terms. The exhibits depicting IT systems are not intended to be literal pictures of exact systems, but are simplified depictions of those systems. Exhibit 4-6 depicts several of the hardware and software components described in this chapter.
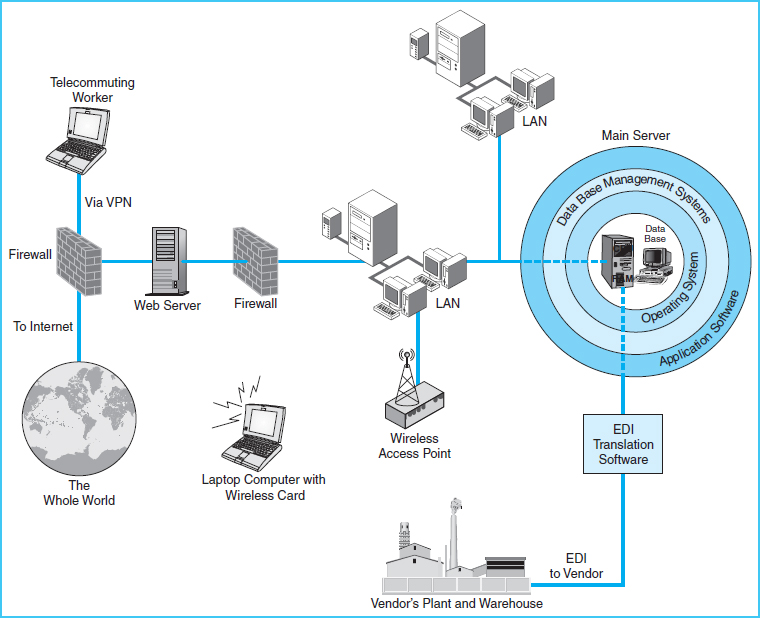
Exhibit 4-6 Exposure Areas in an IT System
The components illustrated in Exhibit 4-6 can increase the efficiency, effectiveness, and economy of conducting business. They can improve sales, performance, and customer service and reduce costs. The existence of each of these components represents an exposure that should be controlled. These IT system exposures are entry points that make the organization susceptible to the IT risks described earlier. The exposure areas shown in Exhibit 4-6 are as follows:
- The operating system
- The database
- The database management system (DBMS)
- Local area networks (LANs)
- Wireless networks
- E-business conducted via the Internet
- Telecommuting workers and mobile workers
- Electronic data interchange (EDI)
- Application software
The first eight of these exposure areas can be controlled by the use of appropriate general controls such as those described in previous sections. The next eight sections give a brief description of each of the eight exposure areas. Some of these hardware or software components are described in more detail in other chapters. The ninth exposure area, application software, requires application controls. The description of application controls within application software is presented in the last section of this chapter. The purpose of the descriptions in this chapter is to provide only enough detail to allow an understanding of these exposures.
THE OPERATING SYSTEM
The operating system is the software that controls the basic input and output activities of the computer. The operating system provides the instructions that enable the CPU to read and write to disk, read keyboard input, control output to the monitor, manage computer memory, and communicate between the CPU, memory, and disk storage. In large computer systems, the operating system manages memory and CPU functions so that multiple users or multiple applications do not interfere with each other. The operating system handles computer data in binary form, which means that data are in sets of 0 or 1 data bits. That is, data such as dollar balances or passwords are being transmitted or stored in the operating system in binary form—sets of 0 and 1 values. Any knowledgeable person who understands binary data and who gains access to the operating system may be able to scan memory for things such as passwords, employee data, and other sensitive data. Such a person could also manipulate or destroy data. The operating system can be an entry point for unauthorized users or hackers.
Operating system access allows a user access to all the important aspects of the IT system. Since all application and database software works through the operating system, access to the operating system also allows access to applications and the database. In addition, all read/write data functions are controlled by the operating system, and any person who has access to the operating system can have full access to data. Essentially, access to the operating system opens access to any data or program in the IT system. Therefore, controlling access to the operating system is critical. If a knowledgeable person is able to access and manipulate the operating system, that person potentially has access to all data passing through the operating system, all processes, and all programs. Thus, the operating system poses security risks, availability risks, processing integrity risks, and confidentiality risks.
THE REAL WORLD
As an example of the dangers of threats to operating system software, in 2003 Microsoft Corp. announced a critical security flaw in several versions of the Windows operating system for personal computers and servers. An excerpt of an article5 related to that flaw is as follows:
“It should be emphasized that this vulnerability poses an enormous threat, and appropriate patches provided by Microsoft should be immediately applied,” the group said in an advisory posted to its Web site. The group said that programs designed to exploit the vulnerability will likely be available on the Internet soon.
By sending too much data to other computers that use its operating system, an attacker can cause the system to grant full access to the system.
“This would give the attacker the ability to take any action on the server that they want,” Microsoft stated in its advisory. “For example, an attacker could change Web pages, reformat the hard disk, or add new users to the local administrators group.”
Jeff Jones, senior director for Microsoft's Trustworthy Computing group, said that, in addition to applying the patch, users and systems administrators should close down any unused communications channels, or ports.
“Customers should protect their network with a firewall,” he said. “Individual users should use the Internet Connection Firewall or some other personal firewall.” The Internet Connection Firewall is a Windows feature that limits the ways that a potential intruder could attack from the network.
The operating system software is much different from application software. Application software, such as accounting software, usually has programmed controls that limit the types of data a person can see or manipulate. For example, employees in the purchasing department who log in to the accounting system will be able to access vendor information, but not payroll information. Application accounting software is written to limit data access and also accept only a limited type of data to be input. For example, if an employee is entering pay rates, it is not likely that the payroll software would allow her to enter letters in that blank box, or enter a pay rate of $500 per hour. Although software is written to limit data access and input, any knowledgeable person who has access to an operating system can manipulate data without being hindered by these types of input or data limitations.
The risks to the operating system related to accounting data include security, availability, processing integrity, and confidentiality risks. Unauthorized access to the operating system would allow the unauthorized user to do the following:
- Browse disk files or memory for sensitive data or passwords
- Alter data through the operating system
- Alter access tables to change access levels of users
- Alter application programs
- Destroy data or programs
As summarized in Exhibit 4-5, these risks are present in all four categories. Many of the general controls mentioned earlier and shown in Exhibit 4-5 should be in place to help reduce these risks. Since an organization must determine which controls are most cost-beneficial, it is not possible to list a complete, inclusive set of general controls recommended for every operating system. At the least, an organization should use user IDs, passwords, log-in procedures, computer logs, and authority tables.
THE DATABASE
In an IT system, all or most accounting records and data are stored in electronic form in the database. There are many different types of databases, but for the purpose of examining the risks to a database, we can assume that the database is a large disk storage for accounting and operating data. The existence of a database offers many operational advantages such as the increased efficiency of IT and easy retrieval of the data. However, the database also is an exposure area. It is a part of the IT system that is susceptible to security, availability, processing integrity, and confidentiality risks. This is true because any unauthorized access to the data can compromise their security and confidentiality and potentially interfere with the availability and normal processing of the IT system. Two examples illustrate these risk areas. An unauthorized user who gains access to the database can browse through the data, compromising the security and confidentiality of the data in the database. The unauthorized user could also destroy or erase data, thereby affecting the accuracy of processing and perhaps making processing unavailable, since some data has been erased.
The exposure of the database may be easier to understand if you compare an IT system with a paper-based system of some 50 years ago. If a person wanted to browse through payroll records back then, he would have to go to the filing cabinet, where the paper payroll records were kept, and use a key to open the file drawer. This means that the only possible unauthorized use of the data could have been by someone with physical access to the file cabinet and the key. However, a sophisticated IT system has data stored in a large database and usually has many computers networked to that database. Hence, it may be possible for someone, including a hacker who might be 3000 miles from the office, to read payroll data from any computer connected to the network. Therefore, the database may be more open to unauthorized access than the physical, paper records, because the database has so many more access points.
General controls such as those outlined in Exhibit 4-5 can help limit the exposure of the database. The use of these controls to authenticate users and limit hacking and network break-ins can reduce the chance of unauthorized access to the data. Again, the organization must determine which specific general controls are best suited to its IT system and may decide not to employ all of the general controls listed in Exhibit 4-5. Controls such as user IDs, passwords, authority tables, firewalls, and encryption are examples of controls that can limit exposures of the database.
THE DATABASE MANAGEMENT SYSTEM
The database management system (DBMS) is a software system that manages the interface between many users and the database. Exhibit 4-7 shows a diagram of multiple user groups accessing and sharing the database through the DBMS.
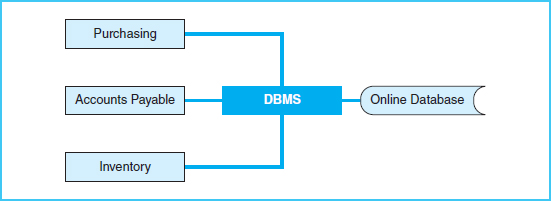
Exhibit 4-7 The Database Management System
Users in all three application areas—purchasing, inventory, and accounts payable—must be able to access records of inventory items, cost, and other data related to inventory. The inventory data can be stored in the database and shared by all three user groups. Each individual user group may have a different level of access. For example, a purchasing user might need to add a new record when a purchase is placed. However, accounts payable users should not be able to add purchases, but should be able to read the records to determine which items should be paid. In addition, there are other users, such as accounts receivable users, who need access to customer and sales data, but have no need to access purchase records. The database management system manages this interface between users and data. It is the controller of access levels for different users.
As is true of the data, the DBMS poses security, confidentiality, availability, and processing integrity risk exposures. Since the database management system reads from and writes to the database, unauthorized access to the DBMS is another exposure area. An unauthorized user who is able to access the DBMS may browse, alter, or steal data. Authentication controls and controls over hacking and network break-ins can limit the chance of unauthorized access to the DBMS.
Both the data and the database management system are critical components that must be adequately guarded to protect business continuity. Loss of the data or alteration to the DBMS can halt operations. Therefore, the physical access, environmental, and business continuity controls are very important for these two components.
LANS AND WANS
A local area network, or LAN, is a computer network covering a small geographic area. In most cases, LANs are within a single building or a local group of buildings. Most LANs are sets of personal computers or workstations that are connected in order to share data and devices such as printers. Typically, the LAN is connected to a larger computer, the server, where data and some programs reside and are shared over the LAN. A group of LANs connected to each other to cover a wider geographic area is called a wide area network, or WAN.
Since LANs and WANs are connected into the larger network of servers and computers within a company, the LANs represent risk exposure areas. Anyone with access to a workstation on the LAN can access data and devices on the entire network within the organization. LANs represent an entry point where an unauthorized user may gain access to the network. LANs pose security, confidentiality, availability, and processing integrity risks. An unauthorized user on the LAN may browse, alter, or steal data and thereby compromise the security and confidentiality of data. Any unauthorized manipulation of data or programs through the LAN can affect the availability and processing integrity of the IT system.
In addition to the workstations, the network cabling also poses risks. Any of the network cables or connections represents a spot where an intruder could tap into the network for unauthorized access. The workstations on the LAN and all network connections should be protected by general controls that limit unauthorized users. Firewalls, encryption, and virtual private networks are important controls when the local area network is connected to networks outside the organization, such as the World Wide Web.
WIRELESS NETWORKS
Wireless networks have become very popular in organizations because they allow workers to connect to the network without being tethered to a network cable. A wireless network can save much time, cost, and effort in running network cables. In addition, it allows workers to roam and continue working via the network.
THE REAL WORLD
Boeing Co. uses wireless networks on the floor of the large shop where it manufactures airplanes. This wireless network with notebook computers allows Boeing workers to move around the plane while they are working and view engineering drawings or parts availability during the manufacturing processes. The employees do not have to walk to a desk or workstation, away from the manufacturing flow, to access these things. Wireless networks can make employees more efficient by allowing them to roam.
The wireless network represents another potential entry point of unauthorized access and therefore poses the four risk exposures of security, confidentiality, availability, and processing integrity. The wireless network has the same kind of exposures as described in the previous section about local area networks. In fact, a wireless network is simply a special case of a LAN. In the wireless network, signals are transmitted through the air rather than over cables. These network signals are similar to radio signals; therefore, anyone who can receive those radio signals may gain access to the network. In fact, there are those who specifically take notebook computers and travel around or near company buildings, hoping to gain access to the company's wireless network. If they can intercept the network signals, they may be able to use the network to gain free Internet access at the least and hack into the company's network at worst. A popular activity is to find a company whose network signal bleeds outside the building to the sidewalk around it. Potential abusers of this network make identifiable chalk marks on the sidewalks so that others can find the network access. This activity has become known as “warchalking.” A double curve symbol on the sidewalk indicates that you can access an open wireless network at that point. The legality and ethics of warchalking are debatable, but a company might avoid it by instituting proper controls, such as wired equivalency privacy (WEP) or wireless protected access (WPA), station set identifiers (SSID), and encrypted data.
THE INTERNET AND WORLD WIDE WEB
Many companies use the Internet to buy or sell via a website or to better serve customers and/or employees. A later chapter on e-business will focus on the specifics of Web-based commerce. This section provides only basics about business use of the Internet so that risk exposures and controls can be examined. While there are many advantages for companies, using the Internet poses security, confidentiality, availability, and processing integrity risks. In addition, the existence of e-commerce in an organization poses online privacy risks, which are described in a later chapter.
The Internet connection required to conduct Web-based business can open the company network to unauthorized users, hackers, and other network break-in artists. The sheer volume of users of the World Wide Web dramatically increases the potential number of hackers or unauthorized users who may attempt to access an organization's network of computers. An unauthorized user can compromise security and confidentiality, and affect availability and processing integrity by altering data or software or by inserting virus or worm programs.
A typical network configuration for Internet connection to a company's network was presented in Exhibit 4-6. Notice in the figure that there is a separate computer serving as the Web server. This computer Web server is isolated from the company network via a firewall. The exhibit shows a dual firewall system, with a firewall between the Internet and the Web server, and a firewall between the Web server and the organization's network. The use of dual firewalls can help prevent hackers or unauthorized users from accessing the organization's internal network of computers.
TELECOMMUTING WORKERS AND MOBILE WORKERS
A significant number of employees in the United States work from home, using some type of network connection to the office. This work arrangement is commonly called telecommuting or teleworking. The Telework Advisory Group of WorldatWork6 reports that telecommuting work arrangements are used by nearly 20 percent of workers over the age of 18. Telecommuting can offer benefits to both employer and employee. The employee gains flexibility and other advantages of being at home, while the employer may save office space and overhead expenses for the worker. The potential disadvantages of telecommuting are that the tele-worker loses daily face-to-face interaction and may miss meetings with other employees or supervisors.
Telecommuting workers cause two sources of risk exposures for their organizations. First, the necessary network equipment and cabling can be an entry point for hackers and unauthorized users. Second, the teleworker's computer is also an entry point for potential unauthorized users; it is not under the direct control of the organization, because it is located in the teleworker's home. Therefore, the organization must rely on the teleworker to maintain appropriate security over that computer and to correctly use firewalls and virus software updates to keep security current. These two entry points pose security, confidentiality, availability, and processing integrity risks. The organization's security policy should address the security expectations of workers who telecommute, and such workers should connect to the company network via a virtual private network.
In addition to working in fixed locations, many employees access company networks and systems using mobile devices such as smart phones and tablets. Examples of smart phones are iPhones and Android phones; tablets include iPads and Android tablets. Using e-mail servers and applications that access company systems, employees may read and process or change company data. They also tend to use these mobile devices at lunchtime, while traveling, while visiting customers or vendors, and from home during off hours. These mobile devices cause the same types of security, availability, processing integrity, and confidentiality risks. Therefore, companies have developed unique methods to protect security and confidentiality. For example, companies that provide mobile devices for employees establish “remote wipe” capability. A remote wipe allows the company's IT professionals to remove company data and applications from the device. If an employee's smart phone or tablet is lost or stolen, it can be remotely wiped of data and applications.
ELECTRONIC DATA INTERCHANGE
Electronic data interchange (EDI) is the company-to-company transfer of standard business documents in electronic form. EDI is widely used by businesses to buy and sell goods and materials. Rather than mailing copies of purchase orders and invoices, companies send these kinds of standard business documents back and forth electronically. To conduct EDI with business partners, a company must use a dedicated network, a value added network, or the Internet. The specific details and advantages of EDI are explained in a later chapter on e-business.
Regardless of the type of network used, the EDI network entails security, confidentiality, availability, and processing integrity risks, as it is another “entry point” for unauthorized users or hackers. EDI transactions must be properly guarded and controlled by general controls including authentication, computer logs, and network break-in controls. Exhibit 4-5 lists these controls and the corresponding risks.
CLOUD COMPUTING
As introduced in chapter 2, many companies use a public cloud computing model for software, data storage, or both. The advantages of public cloud computing, as described in the following list, are repeated from chapter 2:
- Scalability. As a company grows, it can easily purchase new capacity from the cloud provider. It need not buy servers or new data storage as the cloud provider already has the capacity. This scalability is also a tremendous advantage for spikes in business activity. If a company has a large increase in business volume during certain seasons, it can easily scale up the capacity purchased from the cloud provider. When the seasonal volume declines, it then easily scales down the services it buys from the cloud provider.
- Expanded access. Once the software and data are stored in the cloud, it can be accessed by multiple devices from many different locations. This gives the company much more flexibility for those who use or enter the accounting data. It also makes it easier for users to startup new computing capabilities.
- Infrastructure is reduced. The company has a reduced need for servers and data storage since most of these resources are provided by the cloud provider. This also means that the cloud provider handles data security and backup of data.
- Cost savings. Because of the advantages mentioned above, there are usually significant cost savings recognized from cloud computing. Cloud computing is usually a pay-for-service model. In other words, a company pays the cloud provider only for the level of services it actually uses. The scalability of the cloud means that the company no longer needs to maintain an IT system large enough for the peak demand periods. Cloud computing also allows a company to reduce its investment in IT hardware and the personnel needed to support IT hardware. This eliminates the financial risk because the user company avoids making a significant up-front financial investment in technology-related resources that may have uncertain returns.
A company must recognize the risks associated with cloud computing. When examined from its simplest perspective, cloud computing is the outsourcing of IT infrastructure (the hardware), data, and software to a third party. Although the advantages are noteworthy, control of the company's data and software is transferred to the third-party cloud provider, thus introducing additional security, availability, processing integrity, and confidentiality risks. The user company must trust that the provider will keep the data secure and confidential. Similarly, the user must also trust that the provider will not have interruptions in service (downtime or breakdowns). A brief summary of the risks follows:
- Security. All processing, storing data, and reading data occur over the Internet; therefore, the third-party provider must have good user authentication, firewalls, encryption, and virtual private network connections. If a company had its own IT, software, and data storage, it would design and maintain these controls. Under the cloud computing model, it depends on the third-party provider to maintain security controls.
- Availability. Any interruptions in service cause the software and data to be unavailable. Again, a company is placing full control of availability in a third-party provider. The third-party cloud provider must have backup facilities, backup servers, data backups, and proper business continuity plans and disaster recovery plans. Most service level agreements indicate that a high level of uptime, even 100 percent, is guaranteed. However, these agreements also provide for credit or reduced payments if service is interrupted. It can be difficult to successfully recover funds paid to the provider or get concessions in future payments when interruptions occur. Even if the third-party provider has no downtime, an interruption in the company's Internet access can prevent it from accessing cloud services. Therefore, Internet access must be available at all times for the company and the third-party provider.
- Processing integrity. All control of software installation, testing, and upgrading is transferred to the third-party provider of cloud computing services. Thus a company has less control over ensuring that processing is accurate and complete. A company that outsources via cloud computing is trusting the third-party provider to maintain processing integrity.
- Confidentiality. As is true of the previous three items, the control of maintaining confidentiality is transferred to the third-party provider. This includes an extra risk that employees of the third-party provider can possibly browse and misuse company data.
THE REAL WORLD
SalesForce.com, a cloud provider of customer relationship management software, experienced a sudden outage of service around noon on January 6, 2009. For about one hour, the service interruption prevented 900,000 subscribers from accessing or using the service. This outage prevented sales people and managers of the client companies from gaining any access to customer data. They were unable to engage in normal sales and promotional activities during the outage.
A more severe availability problem occurred at Coghead, a cloud computing vendor that offered database services in the cloud to paying customers. Coghead stored client databases and database applications on its servers. In February 2009, Coghead announced it was to be purchased by SAP, and customers would have to find alternative places to store data. Customers were given about two months to move their data off the servers at Coghead. This illustrates the loss of control of data if you store your data and applications in the cloud. You have less control over the data and applications, and if the provider happens to cease operations (such as going out of business), there is a significant risk of losing data and applications.
To avoid these extra risks inherent in a public cloud, many companies establish their own computing cloud structure. This is called a private cloud. The private cloud is developed, owned, maintained, and used by the user company. There is no involvement of a third-party provider. This private cloud offers many, but not all, of the advantages of a public cloud. A private cloud provides the majority of benefits in the areas of scalability and expanded access; however, it does not reduce infrastructure or reduce costs. The greatest advantage of a private cloud is that it does not transfer control of data and software to a third-party provider. Thus, the company maintains the ability to control the security, availability, processing integrity, and confidentiality risks.
THE REAL WORLD
Starbucks uses a combination of public clouds, private clouds, and traditional corporate IT systems. In its stores, Starbucks uses Office 365 for e-mail and productivity applications such as Microsoft Word. Office 365 is the public cloud version of the Microsoft Office Suite. For e-mail and productivity applications at the corporate offices, Starbucks uses its own traditional IT systems on premises. For its customer relationship management software, Starbucks uses SalesForce.com, a public cloud application. For other accounting and Oracle ERP applications, Starbucks uses a private cloud based on virtualized servers that they maintain. This example of using various IT approaches is quite common.
In each of these risk areas, a company places its trust in the third-party provider to have proper IT controls as described in the earlier parts of this chapter. A company must carefully examine and review cloud providers before entering into a cloud computing service agreement. A provider must be trustworthy, reliable, and large enough to scale up operations if necessary. User companies must continually monitor and assess whether the cloud provider is appropriately meeting their needs.
